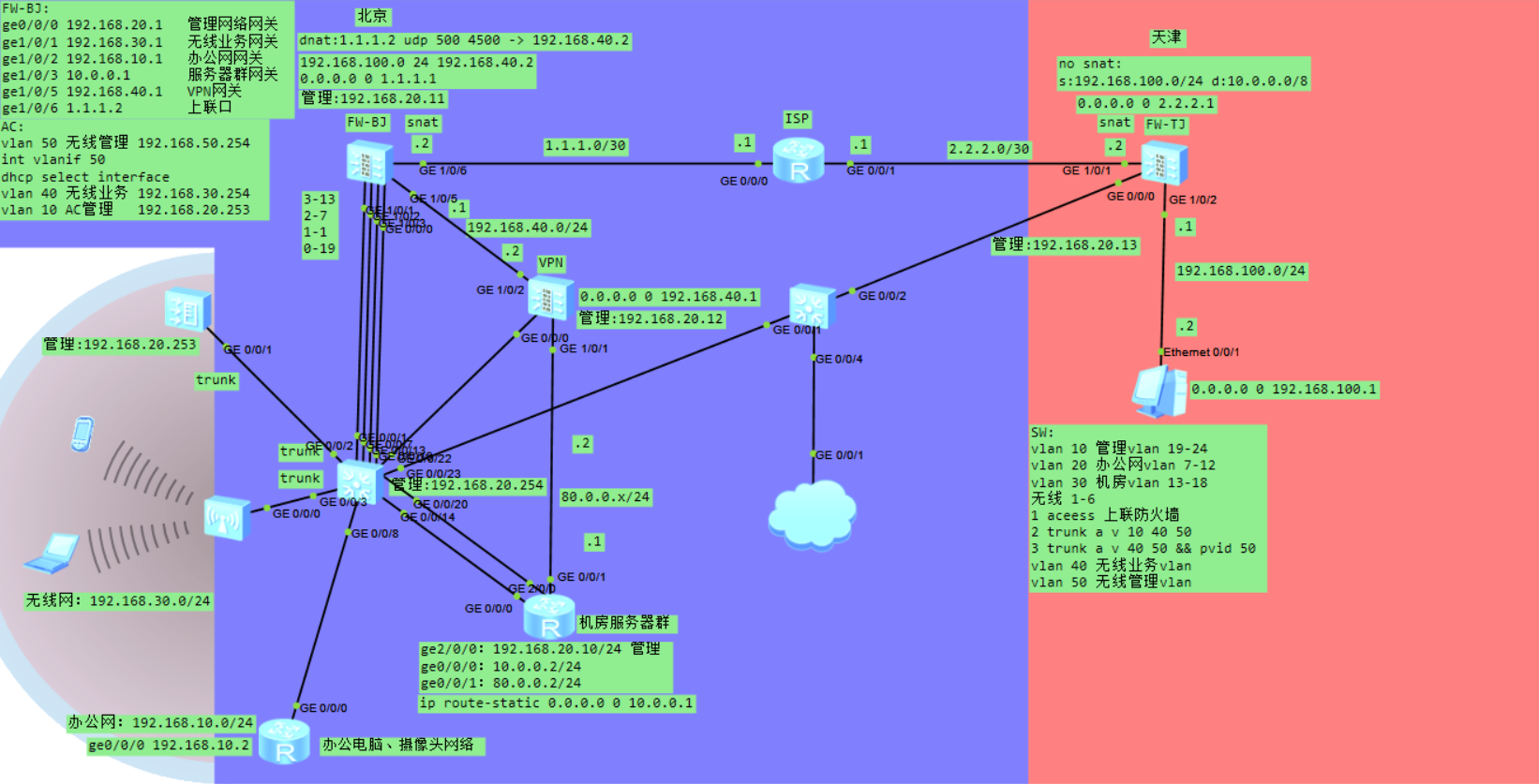
都是一些基础的东西,该标的图中差不多都标注出来了。详细的各个机器的配置放在附页中了。正文简单说下图中没有展现的。
路由(静态,策略)
ENSP策略路由对于设备本身发出的包是不生效的。刚开始在FW-BJ做了[s:192.168.100.0/24 d:10.0.0.0/24 --> 192.168.40.2]这样一条策略路由。FW-BJ和FW-TJ两边建立IPSec后,由192.168.100.2 ping 10.0.0.1,此时ping reply包通过VPN解密后直接通过默认路由发往了1.1.1.1。
NAT(SNAT,DNAT)
ENSP里面是先做SNAT,再匹配IPSec感兴趣流的。
VPN(IPSec VPN,PPTP VPN)
站点到站点这种使用IPSec,出差这种点到站点的使用PPTP VPN。下面是PPTP VPN的教程。上面链接是服务端配置,下面链接是win10客户端的配置。
使用PPTP VPN有弊端。linux客户端拨号的号,是不能更改分配给的IP的。多个linux客户端接入PPTP VPN服务器是会起冲突的。
-
Windows 10系统自带Virtual Private Network客户端配置连接PPTP 服务器_1 https://blog.51cto.com/u_15266039/2896864
交换(VLAN(TRUNK,ACCESS),STP,堆叠)
这里说下堆叠。实验用的24口交换机。实际使用这么个交换机往往捉襟见肘。堆叠可以使两个交换机合二为一。ENSP无法堆叠实验,我用HCL搭建了一下,具体可以参考这个链接:
HCL配置 IRF 堆叠实验 https://blog.csdn.net/long_up/article/details/107471388
WALN(AP,AC)
无线信号这个圈会被调色板盖住的。刚开始一直没出现这个圈,我以为是我哪里配的有问题,重搭了3遍,哈哈哈哈哈哈。无线部分的搭建可以参考这个链接:
eNSP-无线技术原理 https://blog.csdn.net/weixin_51491005/article/details/119514373
IP-MAC绑定
这里说的是DHCP的预留地址。需要分配固定IP的主机。服务器或者前端的主机。
延申一下,说一下局域网IP冲突问题,如果都是DHCP不会有冲突,但显然是不可能的。非法的机器先开机抢走了IP,正常的机器无法上网。 关键的服务器部分和办公区分开。冲突主要集中在有线网办公区,办公区比较大,人比较多的话再划vlan,再细分几个网段,将排错环境调小点。使用静态IP时,有意识地先ping一下,确定没人用再用。网络问题,规划和管理很重要。
DHCP
ENSP图形化界面开启DHCP Server保存时,还要命令行到接口下打DHCP select interface。
DDNS
ISP大多为我们提供动态IP,DDNS捕获用户每次变化的IP,然后将其与域名相对应。方便实惠的内网穿透解决办法。
FTP
带宽不够用,网关限速。局域网内经常传大文件可以搭建个FTP服务器。
补充内容
这里说一下状态防火墙为什么能快速转发。防火墙会对数据流的第一个包的五元组做一个hash,后续的包五元组hash值相同,不再检测,直接转发。
常用命令
# windows
# tracert
# nslookup
# arp查看和清空
arp -a/d
# ipconfig
# 清空DNS缓存
ipconfig /flushdns
# 所有DHCP网卡重新获取地址
ipconfig /release_all
ipconfig /renew_all
# 查看端口号是否被占用
netstat -ano | findstr <端口号>
# 查看路由表
route print
# 添加路由
route add 192.168.1.2 mask 255.255.255.0 192.168.1.1 -p
# 添加主机路由
route add -host 192.168.1.2 192.168.1.1 -p
# 删除路由
route delete 192.168.1.2 mask 255.255.255.0 192.168.1.1
# linux
# 查看路由表
route -n
# 添加静态路由
route add -net 10.20.30.40 netmask 255.255.255.0 gw 192.168.0.1
# 添加默认路由
route add default gw 192.168.0.1
# 添加主机路由
route add -host 10.20.30.40 gw 192.168.0.1
# huawei switch/router
# 查看内存配置文件/当前窗口配置
dis cu/th
# 查看路由表
dis ip routing-table
# 查看各个接口的IP
dis ip int b
# 查看vlan
dis vlan b
# 配置端口类型(trunk为例)
p l t
# 配置允许通过vlan(trunk为例)
p t a v xx xx
# 保存
CTRL+Z save
附页
FW-BJ.cfg
!Software Version V500R005C10SPC300
!Last configuration was saved at 2023-03-21 10:17:14 UTC
#
sysname FW-BJ
#
l2tp domain suffix-separator @
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
update schedule location-sdb weekly Sun 23:18
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
dhcp enable
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 22:40
update schedule av-sdb daily 22:40
update schedule sa-sdb daily 22:40
update schedule cnc daily 22:40
update schedule file-reputation daily 22:40
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%5bIr:B4|[9sEFC&]CoG&<L1%u.[F;n"k'Tgazf.:GXpAL1(<@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%9gL|,]3)i7UN:@+0{o@)zfYuW93fLW<#6I;<NASML~*RfYxz@%@%
level 15
manager-user admin
password cipher @%@%s2$z4ztu0~~g#&8^{d[X4%nefKeM<il4L$b5$8SQ*pz/%nh4@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip address 192.168.20.1 255.255.255.0
alias GE0/METH
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 192.168.30.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
dhcp select interface
dhcp server ip-range 192.168.30.100 192.168.30.200
dhcp server gateway-list 192.168.30.1
dhcp server dns-list 114.114.114.114
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 192.168.10.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.0.0.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
ip address 192.168.40.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/6
undo shutdown
ip address