FIT5037
Week 1: Overview
Type of Network Attacks
- Interruption
- Availability
- Interception
- Confidentiality
- Modification
- Integrity
- Fabrication
- Authentication
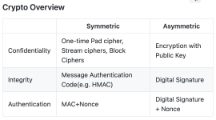
Security Goals
- Secrecy/ Confidentiality(CONF)
- Encryption
- Integrity
- Message Authentication Code(MAC)
- Digital Signature
- Authentication
- The digital signature, biometrics, password
- Non-repudiation(NR)
- The digital signature, biometrics
- Availability
Week2 Cryptography Foundations for Network Security
OUTLINE
Confidentiality in Network:
Symmetric and Asymmetric Encryption
Adversarial Capabilities
IND-CPA and IND-CCA Security Model
Integrity and Authentication in Network
Digital Signatures and MAC
Block cipher:
- process one input block at a time
- produce one output block for each input block
- common block sizes: 64, 128 and 256 bits
Stream cipher:
-
process input elements continuously
-
produces one element at a time
-
common element size: 1 bit or 1 byte
-
operation is generally exclusive OR (XOR) between input elements and stream cipher
key
ECB, CBC,CFB, OFB, CTR
RSA is not indistinguishable under chosen-cipher text attack
Why are attacks in the IND-CPA model effective against RSA?
Encryption can be performed by anyone.
RSA encryption is deterministic.
Probabilistic PKE
AUTHentication + INTegrity:
Diffie Hellman Key Exchange
Digital Signature and MAC (Message Authentication Code) and Hash
Digital signatures reproduce the electronic version of the normal signatures
- proof of identity (authenticity of the message origin)
- proof of message integrity
- non-repudiation
MAC
- Provides message integrity and authenticity
- MAC does not distinguish between two participants
Hash
- One way function collision resistance
- Provides integrity check
MAC Replay Attack and Countermeasure
Nonce + Challenge Response Protocol
Countermeasure: Nonce
- Every time Bob wants to communicate, Alice sends a nonce (a challenge) to Bob.
- Then Bob calculates: Hash(key, "I'm Bob" || nonce).
- Alice receives the above hash value and recalculates it for verification.
Since the hash value is different for each nonce, replay attacks are mitigated.
Week3A: Public Key Infrastructure
OUTLINE
Man-in-the-middle attacks on Public-key encryption
Public Key Infrastructure
Digital Certificate, i.e., X.509 Certificate Certificate Authority
How PKl Defeats the MITM Attack
Attacks on Pkl
- Authentication
- Confidentiality
- Integrity
- Non-repudiation
- Trust
Digital Signatures
Encrypt message with private key -> Generate digital signature
Decrypt digital signature with public key -> Verify digital signature -> Check if M == M'
How PKI Defeats the MITM Attack
Alice needs to obtain a certificate from a trusted entity (Certificate Authority - CA).
After verifying Alice's identity, the trusted entity issues a certificate containing Alice's name and public key.
Alice sends the entire certificate to Bob.
Bob uses Alice's public key to verify the certificate - ensuring it is from Alice and not someone else.
The certificate cannot be forged or tampered with.
Core Functions of a CA
Subject Verification
Ensure that the entity applying for a certificate possesses or represents the identity in the subject field.
Signing Digital Certificates
The CA uses its private key to generate two digital signatures for the certificate.
Once the signatures are applied, the certificate cannot be modified.
Anyone with the CA's public key can verify the signatures.
Get a Certificate from CA:
Step 1: Generate a public/private key pair
Step 2: Generate a certificate signing request (CSR);
Attack Scenario: Genuine Certificate
The attacker forwards a genuine certificate to Alice.
Alice recognizes the certificate as genuine, so she encrypts secret with the certificate's public key and sends it to the "server."
The attacker intercepts the request but cannot decrypt the secret because they do not possess the private key.
Attack Scenario: Fake Certificate
The attacker forges a certificate for the domain example.com using their own public key.
The CA does not sign the certificate as the attacker is not associated with example.com.
The attacker attempts to self-sign the certificate and sends it to Alice.
Alice's browser raises a warning as it cannot find any trusted certificate to validate the received certificate.
Attack Scenario: Attacker's Certificate
The attacker possesses a valid certificate of their own.
The attacker sends their certificate to Alice.
Alice's browser checks if the subject field of the certificate matches Alice's intent.
The received certificate's validity is checked.
The certificate's subject (common name) is verified to match the server's hostname.
Attacks Against PKI
Man-in-the-Middle Proxy
The proxy creates a self-signed CA certificate installed on the user's browser.
The proxy intercepts communications.
Attacks on CA Verification Process
Attack on CA Signing Process: Private key compromise.
- How to protect private keys: Use a hardware security model.
Attacks on Algorithms: Digital certificates rely on one-way hash and digital signatures.
- Use stronger algorithms.
User Confirmation Attacks: Certain software does not compare the information within the certificate (common name field) with the user-provided or approved information: Security vulnerability in Common Name.
Week 3B: Email Security
OUTLINE
Internet Email Architecture and Protocols SMTP, MIME
Email Security
PGP
S/MIME
Domain Keys Identified Mail (DKIM)
Privacy-preserving email services with provider-supplied functions (case study)
- What are the main services provided by PGP?
- Key management, confidentiality, integrity, authenticity.
- What is the purpose of detached signatures?
- Signatures are sent separately. Two files: the original data and the signature.
- Why is R64 encoding used for email applications?
- Some email servers do not accept binary emails and require printable characters. R64 uses ASCII characters, all of which are printable.
- What is S/MIME? What encryption functions does S/MIME use?
- S/MIME = Secure MIME
- 3DES/AES for encryption, Elgamal for key exchange, SHA for signing
- What is DKIM? How does DKIM email authentication service differ from S/MIME or PGP?
- The sender's email server signs the email.
- DKIM is used for email server to email server communication, while PGP and S/MIME are end-to-end encryption.
Why is Transport Layer Security (TLS) not sufficient to protect email?
Answer: TLS protects communication between two hops; all intermediate hops see plaintext.
Simple Mail Transfer Protocol (SMTP)
- Text-only
- Limited to ASCII characters
- Size limitations
- Command-only
- Issues
- No security - plaintext messages
PGP (Pretty Good Privacy)
-
Key management
-
Authentication (AUTH) + Integrity (INT)
Digital signatures (No-Repudiation)
-
Confidentiality (CONF)
Encryption:
- Symmetric encryption
IDEA, 3DES-EDE, AES
- Public-key encryption
RSA, Elgamal, Digital Signature Algorithm
- Hash
MD5, SHA-1, SHA-2, SHA-512
-
Encryption steps:
- HASH(M) => digest
- RSA(digest, private key) => digital signature sig
- RSA is a public-key encryption method used for signing.
- digital signature sig || M => certificate
- Compress(certificate) => compressed certificate
- AES(session key, compressed certificate) => encrypted compressed certificate (using symmetric encryption)
- RSA(session key, recipient's public key) => encrypt session key for non-peer-to-peer encryption of the session key
- Another user can retrieve the session key of 128 bits using their private key
- Sent to the recipient: encrypted compressed certificate || encrypted session key
-
Decryption steps:
- Retrieve the decryption session key using the private key => session key
- Decrypt the compressed certificate using the session key => compressed certificate
- Obtain M || digital signature by decompressing the data => M || digital signature = DeCompress(compressed certificate)
- Verify Hash(M) and Hash(M')
- Hash(M') = Decrypt the digital signature using the sender's public key.
-
Compression:
- PGP uses ZIP compression algorithm after applying the signature and before encryption.
-
Why is this order important?
- Signing: It is best to sign the original message before compression to ensure the signature is based on the original message.
- Transmission: Compression saves on email transmission and file storage space.
- Encryption: Encrypting after compression can enhance encryption because compression reduces redundancy in the message.
Radix-64 Encoding
- Used for compatibility with email protocols
- Text => Binary => ASCII characters (every 6 bits = 1 ASCII character)
Key Management
- Send Key Identifiers (KeyID) instead of the full public key for bandwidth efficiency.
- Users can have multiple key pairs.
- Two types of keyrings need to be maintained:
- User's own public/private key pairs
- Store the encrypted private key instead of the plaintext private key.
- Public keys of other communication partners
- Store the public keys of other users indexed by their KeyID.
- User's own public/private key pairs
Trust Model
- Does not rely on Certificate Authorities (CAs).
- Each user is their own CA.
- Users sign the keys of users they trust, forming a web of trust.
- If there is a chain of signatures leading to a trusted key, the trusted key is signed by other trusted keys.
Restrictions
- Misuse
- Leakage
- No forward secrecy
- Public key exchange is required.
- Targeted attacks against PGP KeyID.
- May hinder useful functionalities such as search, spam filtering, and subject extraction.
- Lack of non-repudiation and authentication in compromised scenarios.
What is S/MIME? What encryption functions are used in S/MIME?
- S/MIME stands for Secure/Multipurpose Internet Mail Extensions.
Digital Signatures
RSA
Hash Functions
MD5, SHA-1, SHA-2
Session Key Encryption
Key Transport: RSA, ElGamal (asymmetric)
Key Agreement: Diffie-Hellman (DH)
Message Encryption (Symmetric)
AES-128
Triple DES (T3-DES)
MAC (Message Authentication Code)
HMAC with SHA-1
Cipher Modes
AES-GCM (Galois Counter Mode)
AES-CCM (Counter with CBC-MAC)
Multipurpose Internet Mail Extensions (MIME)
- MIME supports different types of content. X.509 v3 certificates
- Each client has a trusted CA certificate list.
- Own key pairs and certificates signed by trusted CAs.
DomainKeys Identified Mail (DKIM)
- Outgoing emails from the sender's domain must be signed using the sender domain's secret key before leaving the domain.
- Transparent to the user
- Mail Submission Agent (MSA) signs
- Mail Delivery Agent (MDA) verifies
- The recipient can verify the signature using the domain's public key.
- The public key is stored in DNS servers, and the signature is attached.
What is DKIM? How does DKIM email authentication service differ from S/MIME or PGP?
- DKIM stands for DomainKeys Identified Mail.
- The sender's email server signs the email.
- DKIM is used for authentication between email servers, whereas PGP and S/MIME provide end-to-end encryption.
Q: Why don't email service providers deploy end-to-end (user-to-user) email encryption?
Encryption prohibits email systems from providing useful functionalities such as filtering, topic extraction, targeting ads, and search.
Week4:IPSec
OUTLINE
Network Layer, IP
IPSec
VPN
Anonymisation in Network (Tor)
Understand IPSec architecture, protocols, and applications
Understand Encapsulating Security Payload (ESP), transport and tunnel modes of operations in IPSec
Virtual Private Network (VPN)
- Isolation
- Tunneling
- Multiple logical overlay networks coexist on the same physical network, each network providing its own private services.
Answer
Placing the VPN server in front of the firewall is better. VPN also has the functionality of a firewall. After the VPN gateway, the messages will be decrypted, allowing the firewall to inspect the details of the packets.
IPsec: Internet Protocol Security
IPSec is a security protocol used to protect network layer data. It provides security processing at the Internet layer for IP datagrams, protecting them according to the security policies of the communicating IP nodes before forwarding them to the network interface layer.
The receiving IP node verifies the datagrams based on established security parameters and rejects those that are not protected according to the defined policies.
The services provided by IPSec include: Authentication, Integrity, Confidentiality, No-Repudiation (but does not hide identity).
- Authentication: Verifies the claimed identity of the data source, ensuring the authenticity of the sender.
- Integrity:
- Data Integrity
- Anti-Replay: It can detect tampering with and duplicate arrival of individual IP datagrams.
- Confidentiality: Protects data from unauthorized disclosure and provides limited traffic confidentiality. It hides the source IP address, destination IP address, size of IP datagrams, and communication frequency.
The entire process of IPsec consists of five steps:
- Initiation: Something needs to trigger the creation of our tunnel. For example, when we configure IPsec on a router, we use an access list to tell the router which data to protect. When the router receives content that matches the access list, it initiates the IKE process. The tunnel can also be initiated manually.
- IKE Phase 1: We negotiate a security association to build the IKE Phase 1 tunnel (ISAKMP tunnel).
- IKE Phase 2: In the IKE Phase 1 tunnel, we build the IKE Phase 2 tunnel (IPsec tunnel).
- Data Transfer: We send user data through the IKE Phase 2 tunnel to protect the user data.
- Termination: The IPsec tunnel will terminate after a period of time when there is no user data to be protected.
IPSec has two main protocols:
- Authentication Header (AH):
- Integrity
- Data-Origin Authentication
- Anti-Replay
- Access Control
- No Confidentiality
- Encapsulating Security Payload (ESP):
- Integrity
- Data-Origin Authentication
- Anti-Replay
- Confidentiality
- ESP can provide only confidentiality (CONF), only authentication (AUTH), or both.
IPSec has two modes: Encapsulation Mode
- Transport Mode:
- Inserts the IPsec header into the IP packet to protect the data. Host-to-host
- Tunnel Mode:
- Keeps the original packet and adds a new header. The ESP/AH header follows the new IP header, while the original IP packet remains unchanged. Gateway-to-gateway

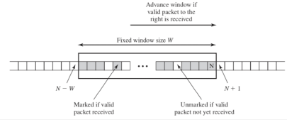
Anti-replay Services
Replay: AUTH packet
Case
If the received sequence number is smaller than the size of the current window's leftmost edge, discard the packet.
If the received sequence number is within the range of the current window, check if the packet has been received.
If the received sequence number is greater than the maximum size of the current window, set the received sequence number as the maximum edge and calculate the minimum edge using N-W+1.
If the recipient sets N=60 and window size W=64, the range should be 0-60.
The IPSec policy file contains a list of entries:
3 IPSec Policies:
- DISCARD
- Discard the packet.
- PROTECT
- Protect the packet using AH and ESP security protocols.
- BYPASS
- Bypass IPSec processing.
Security Association (SA)
SA is a contract between two entities that specifies how they will communicate using security services.
Security Association Database (SAD)
- AH information
- ESP information
- SA lifecycle
- IPSec protocol mode (Transport/Tunnel)
IPSec Architecture
- Authentication Header (AH): Extended header for message authentication.
- Encapsulating Security Payload (ESP): Provides encryption with combined confidentiality and message integrity.
- Internet Key Exchange (IKE): Key management scheme for IPSec.
- SA establishment: Participants of the IKE protocol first establish security associations to define the security parameters for the IPSec session, such as encryption algorithms, authentication algorithms, key lengths, etc. These parameters will be used for encrypting and authenticating IP packets.
- Key exchange: IKE uses the Diffie-Hellman key exchange algorithm to negotiate and generate shared keys. Through Diffie-Hellman key exchange, communicating parties can securely generate shared keys without directly transmitting the keys.
- Authentication: The IKE protocol supports various authentication methods such as pre-shared keys, digital certificates, Public Key Infrastructure (PKI), etc. Authentication ensures that communicating parties can mutually verify each other's identities and prevent man-in-the-middle attacks.
- Key negotiation and establishment: Through the negotiation process, IKE parties use the Diffie-Hellman key exchange algorithm to generate shared keys and use these keys to establish various keys required for the IPsec session, such as symmetric keys and asymmetric keys.
Anonymising Network
C. IPsec does not provide anonymity on the Internet. It is primarily used for encrypting and securing the transmission of data, rather than hiding or anonymizing the identities of senders or receivers.
Solution: decentralized, anonymous network
A. When using Encapsulating Security Payload (ESP), it provides confidentiality. ESP is part of the IPsec protocol suite and is used to provide encryption and authentication of data over IP networks.
B. IPsec provides anti-replay properties, meaning it can prevent attackers from replaying captured packets, thus protecting the integrity and security of the communication.
D. When using Authentication Header (AH), IPsec provides integrity. AH is also part of the IPsec protocol suite, and it provides integrity and authentication of data but does not provide encryption. No CONF
TOR Distributed Anonymous Communication Service
The sender must negotiate an encryption key with each router.
Components of Tor
- Client
- Server
- Tor (Onion) router: Special proxy relays application data.
- Directory server: Provides Tor router information.
Process
- The last router sees the plaintext data but doesn't know where the message originated from.
- Each router only knows its predecessor and successor.
Process of a client sending a message:
- The client retrieves the Tor node list from the directory server.
- The client randomly selects a path to the destination server.
- The client negotiates an AES key with each router (each router has its own encryption key).
- The client encrypts the message:
- C3 = Encrypt(K3, data||IP_Server)
- C2 = Encrypt(K2, C3 || IP_OR3)
- C1 = Encrypt(K1, C2 || IP_OR2)
- The client sends an IP packet: IP_Client || IP_OR1 || C1
Packet processing at each router:
- Packet arrives at OR1:
- C2 || IP_OR2 = DEC(K1, C1)
- Cache IP_Client, IP_OR2
- Send an IP packet: IP_OR1 || IP_OR2 || C2
- Packet arrives at OR2:
- C3 || IP_OR3 = DEC(K2, C2)
- Cache IP_OR1 || IP_OR3
- Send an IP packet: IP_OR2 || IP_OR3 || C3
- Packet arrives at OR3:
- IP_Server || data = DEC(K3, C3)
- Cache IP_OR2, IP_Server
- Send an IP packet: IP_OR3 || IP_SERVER || data
Week5A:Firewall
OUTLINE
Firewalls
Understand Transport Layer Security (TLS)
- TLS Handshake
- TLS Record
Understand Attacks on TLS, SSL(deprecated)
- Padding Oracle Attack
Requirements of a firewall
- All the traffic between trust zones should pass through the firewall.
- Only authorized traffic, as defined by the security policy, should be allowed to pass through.
- The firewall itself must be immune to penetration, which implies using a hardened system with secured Operating Systems.
- Determines the direction in which requests may be initiated and are allowed to flow through the firewall. It tells whether the traffic is “inbound” (From the network to the firewall) or vice-versa “outbound”
Firewall Policy
• User control:
Controls access to the data based on the role of the user who is attempting to access it. Applied to users inside the firewall perimeter.
• Service control:
Controls access by the type of service offered by the host. Applied on the basis of network address, the protocol of connection and port numbers.
• Direction control:
Determines the direction in which requests may be initiated and are allowed to flow through the firewall. It tells whether the traffic is “inbound” (From the network to firewall) or vice-versa “outbound”
Firewall actions
• Accepted: Allowed to enter the connected network/host through the firewall.
• Denied: Not permitted to enter the other side of firewall.
• Rejected: Similar to “Denied”, but tells the source about this decision through ICMP packet.
three types of firewalls:
• Packet Filter Firewall
• Stateful Firewall
• Application/Proxy Firewall
Overview of TLS
Transport Layer Security (TLS) provides a secure channel between two communicating applications.
- Integrity: Channel can detect any changes made to the data during transmission
- Authentication: At least one end of the channel needs to be authenticated, so the other end knows who it is talking to.
- Confidentiality: Nobody other than the two ends of the channel can see the actual content of the data transmitted.
TLS Layer

• TLS sits between the Transport & Application layer
• Unprotected data is given to TLS by the Application layer
• TLS handles encryption, decryption, and integrity check
• TLS gives protected data to the Transport layer
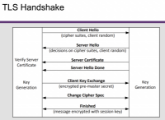
TLS Handshake
Before a client and server can communicate securely, several things need to be set up first:
- Encryption algorithm and key
- MAC algorithm
- Algorithm for key exchange
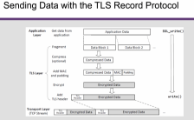
Data is transferred using records:fragmentation: ≤ 16KB
Each record contains a header and a payload.
Padding Oracle Attack

The goal of a padding oracle attack is to compromise the confidentiality of encrypted data, especially in cases where block cipher modes (such as CBC mode) are used for encryption.
In this mode, the plaintext data is divided into fixed-sized blocks and transmitted after encryption using a key. Each encrypted block is encrypted using the ciphertext of the previous block as the initialization vector (IV).
The steps of a padding oracle attack are as follows:
- The attacker intercepts the encrypted ciphertext and selects a specific encrypted block to attack.
- The attacker modifies the last byte of that encrypted block and sends the modified ciphertext back to the decrypting entity.
- When the decrypting entity attempts to decrypt the modified ciphertext, if the padding verification step fails (for example, if the format of the padding bytes is incorrect), the decrypting entity will return an error, indicating a padding verification failure.
- The attacker leverages the result of the padding verification failure to infer the true value of the last byte of the modified ciphertext block. This is because the padding verification step provides information about the correctness of the padding bytes' format. By continuously modifying the padding bytes until the padding verification succeeds, the attacker can deduce the correct value of the padding bytes.
- By repeating the above steps byte by byte, the attacker can deduce the value of each byte in the encrypted block in sequence.
Countermeasures
- Remove server responses
- Use AES GCM model - authenticated encryption
- Ensure that the ciphertext is not modified during the transmission
Week 5:Wireless Network
Wireless Network Security Overview and Countermeasures
Wireless networks face various security threats, but there are countermeasures to mitigate these risks.
The basic elements of the IEEE 802.11 wireless security standard include WEP (insecure), WPA, and WPA2.
Understanding the vulnerabilities in the implementation of WPA2 and analyzing the unique threats posed by physical layer interference attacks.
Wireless Security: The Problem
- Channel:
- Broadcast nature makes it easier for eavesdropping and interference.
- Mobility and Accessibility:
- Mobile devices are more susceptible to threats.
- Resources:
- Limited memory/power makes it challenging to implement robust security systems.
The MAC address (Media Access Control Address) is a unique identifier for network interfaces used to identify devices on a local network. However, MAC address-based authentication can be bypassed because MAC addresses can be spoofed or forged.
Attackers can use specific software or tools to modify their device's MAC address, masquerading as a trusted device. This deception allows attackers to bypass MAC address-based authentication measures and gain unauthorized network access.
Therefore, although the MAC address serves as a unique identifier for a device, it is not a reliable authentication mechanism as it can be tampered with or forged. In wireless networks, higher-level authentication methods such as WPA/WPA2 passwords, enterprise-level 802.1X authentication, etc., are typically required for stronger security.
Threat:
- Man-in-the-Middle attack
- Identity theft, media access control(MAC) address spoofing
- Ad hoc networks
- Denial of Service(DoS)
- Network injection
Wireless Security Measures
-
Securing transmissions:
signal-hiding: to protect the location of access points
encryption
-
Securing access points
authentication
Jamming
The adversary interferes with the reception of messages by transmitting a continuous jamming signal, or several short jamming pulses.
cause DoS
Detection:
monitor signal strength
monitor carrier sensing time
Week6:Network Attacks
OUTLINE
TCP Protocols
SYN flooding attack
TCP reset attack
TCP session hijacking attack
DNS protocols
Local DN'S cache poisoning attack
Remote DNS cache poisoning attack
DoS attack
Security of WEP in IEEE 802.11b:
- Encryption Algorithm: WEP uses RC4 to encrypt data. RC4 is a stream cipher algorithm used to generate ciphertext by XORing plaintext with a key.
- Key Management: WEP uses a fixed key for encryption, typically a 40-bit or 104-bit key. The key needs to be shared between the wireless access point and wireless clients.
Insecurity
- Improved IV Management:
- Detection of IV reuse
- IV collisions
- WEP Recommendations:
- Changing IV for each data packet
- Some weak implementations of WEP
- Message modification without knowledge of the key
Insecurity INT
- CRC32 is not a MAC:
- It is linear
- CRC32 used with stream cipher:
- Stream ciphers are linear
- Modification of ciphertext possible without disclosing m
Insecurity of WEP in IEEE 802.11b:
- Key Weakness: WEP uses a relatively small key space of 40 bits or 104 bits, making it vulnerable to exhaustive attacks. Attackers can attempt all possible key combinations to break WEP encryption.
- Initialization Vector (IV) Reuse: WEP uses a 24-bit IV to increase encryption strength. However, WEP repeats the same IV in practical use, leading to repetitiveness in encrypted traffic, allowing attackers to retrieve the encryption key.
- Weaknesses in the RC4 Algorithm: The RC4 algorithm used by WEP has certain weaknesses that enable attackers to recover the key by analyzing the encrypted data stream. This type of attack is known as WEP key recovery attack.
- Data Integrity Issues: WEP does not provide a mechanism for data integrity checks, which means attackers can tamper with the data without being detected.
- Key Management and Authentication Issues: WEP employs weak key management and authentication mechanisms, making it susceptible to dictionary attacks and forged authentication attacks.
Security of WPA TKIP in IEEE 802.11g
Temporal Key Integrity Protocol (TKIP)
- Key Mixing: IV and key are mixed before RC4 encryption for each packet.
- Protection against replay attacks using sequence counter.
- Message Integrity Check (MIC) instead of CRC32 for data integrity.
Rekeying: Unique key for each packet.
Security of WPA2 CCMP in IEEE 802.11i
- Authentication: Verifying the identity of users or devices.
- Confidentiality: Protecting data from being intercepted during transmission by encrypting it.
- Integrity: Ensuring that data is not tampered with during transmission using checksums and Message Authentication Codes (MAC).
Difference between TKIP and CCMP:
- TKIP was introduced to enhance the security of WEP (Wired Equivalent Privacy). It provides encryption, integrity, and message authentication but is relatively weaker.
- CCMP is the encryption protocol used in WPA2, providing authentication, integrity, and confidentiality. It is more secure than TKIP.
WPA2 (PSK): Password Cracking Attack
- The attacker starts by monitoring the wireless network (using tools like Wireshark).
- The attacker identifies connected users on the WiFi (can be discovered using Wireshark).
- The attacker forges a de-auth packet and forces the victim user to disconnect from the WiFi.
- When the user reconnects to the WiFi, the attacker captures the handshake containing the PSK hash value.
- The attacker offline cracks the hash and recovers the password.
WPA2: Security Best Practices
- Avoid WPA2 PSK.
- Use EAP-TLS certificate-based authentication.
- Implement rogue access point detection.
- Use the latest operating system.
Network Layer: Lower Layers
- VPN (Virtual Private Network) and IPSEC (Internet Protocol Security):
- VPN and IPSEC are excellent when you want to encrypt all network traffic.
Transport Layer:
- TLS (Transport Layer Security):
- Services provided:
- Confidentiality: Protects data from being intercepted during transmission through encryption.
- Encryption: Data is encrypted using cryptographic algorithms, ensuring only authorized parties can decrypt it.
- Integrity: Ensures data is not tampered with during transmission through checksums and Message Authentication Codes (MAC).
- Message Authentication Code (MAC): Used to verify the integrity and authenticity of messages.
- Authentication: Verifies the identity of communicating parties through methods like digital certificates.
- Confidentiality: Protects data from being intercepted during transmission through encryption.
- Services provided:
Application Layer:
-
SYN Flood Attack:
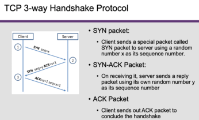
- SYN flood attacks exploit vulnerabilities in the TCP three-way handshake process. Attackers continuously send a large number of forged SYN packets to servers, depleting the server's Transmission Control Block (TCB) queue resources.
Countermeasure: SYN Cookie
- Upon receiving a SYN packet, the server calculates a keyed hash using a key derived from the SYN packet.
- The hash value (H), known as the SYN cookie, is sent to the client (IP address) as the initial sequence number.
- The server does not store half-open connections in its queue.
- Since the attacker receives a fake IP address, they won't receive H.
- Legitimate clients send H+1 to the server, which the server verifies.
-
TCP RST Attack:
- TCP RST attacks involve immediately terminating a connection between two hosts by sending RST packets.
- TLS cannot prevent TCP RST attacks since TLS operates above TCP and cannot protect the TCP header, allowing the RST flag to be set.
- Solution: Use Intrusion Detection Systems (IDS) to detect and prevent TCP RST attacks.
-
TCP Session Hijacking Attack:
- Hackers can execute TCP session hijacking attacks by capturing packets and manipulating the next sequence number and acknowledgement number.
- Solution:
- Make it difficult to spoof packets by randomizing initial sequence numbers and source port numbers.
- Encrypt the TCP payload.
DNS Protocol:
- Authoritative Name Server (Domain Name System):
- Each DNS zone has at least one authoritative name server responsible for publishing information about that zone and providing authoritative and deterministic responses to DNS queries.
- Local DNS Cache Poisoning Attack:
- Attack against user machines: Attackers send forged DNS responses with malicious IP addresses to user machines that send DNS queries.
- Attack against local DNS servers (cache poisoning attack): Attackers send forged responses to local DNS servers while they perform iterative queries to DNS servers on the Internet, as long as they arrive before the actual responses.
- Remote DNS Cache Poisoning Attack:
- Remote DNS cache poisoning attack requires guessing port numbers, transaction IDs, etc.
- Cache impact: If no attempts fail, the actual response will be cached by the local DNS server, and the attacker needs to wait for cache timeout to make the next attempt.
Countermeasures:
- DNSSEC (DNS Security Extensions):
- DNSSEC provides authentication and integrity checks for DNS data but does not provide confidentiality protection.
- All answers from DNSSEC-protected zones are digitally signed.
- TLS/SSL:
- Client and server negotiate encryption algorithms and session keys.
- Relies on trust and decisions regarding certificate authorities for key issuance.
- HTTPS is built on top of TLS/SSL, defeating DNS cache poisoning attacks.
Countermeasure for Kaminsky DNS Cache Poisoning Attack:
b. Use DNSSEC
c. Randomize source port numbers
Week7A:IDS
OUTLINE
Intrusion Detection
Background and Concept
Intrusion Detection Systems (IDS)
Detection Model
System Architecture
Real-world Tools
Incident Response
Intruders:
- Impersonator: Typically refers to someone who attacks a system from the outside.
- Insider: Typically refers to someone who attacks a system from within.
- Covert Operator: Can be either an external or internal attacker.
Design Objectives:
- Detect various types of intrusion behavior.
- Including known and unknown attacks.
- Adapt to new attacks or changes in behavior.
- Real-time detection of intrusion behavior.
- Efficient analysis of user activity.
- Timely reporting of suspicious incidents.
- Ensure accuracy.
- Minimize false positives and false negatives.
IDS Models:
Signature-based:
- Unusual behavior is known.
- Alerts are generated when activity matches a signature.
Anomaly-based:
- Normal behavior is known.
- Alerts are generated when activity deviates from normal behavior.
- Requires more time and processing power.
- Can produce false positives (normal activity identified as malicious) and false negatives (malicious activity considered normal).
- Threshold Anomaly Detection
- Statistical Anomaly Detection
Heuristic-based:
- Uses machine learning models of normal behavior.
- Alerts are generated when the model identifies activity as anomalous.
IDS Architecture:
- Auditor: Records all security-related activities for analysis.
- Analyzer: Analyzes data from the auditor automatically and updates settings as needed.
- Notifier: Reports detected anomalies and updates settings as needed, triggers appropriate countermeasures.
IDS Types:
- Host-based IDS (HIDS):
- Deployed on individual systems to detect malicious activity on a single device. Can also be used in a distributed system within a network.
- Pros: Lower cost, as most HIDS are software-based; visibility into low-level activities; lower false positive rates for local threats.
- Cons: Limited view of the network; potential for system tampering by malicious insiders.
- Network-based IDS (NIDS):
- Monitors network traffic to detect intrusion behavior across the entire network.
- Pros: Can see attacks in network traffic, particularly at the transport or IP layer; difficult to tamper with.
- Cons: May require dedicated hardware; challenging to inspect encrypted traffic.
Week7B:Denial of service attack
OUTLINE
Understand the goal of DoS attacks
Describe different DoS attacks on different layers
Explain the basic countermeasures against Dos attacks
Understand the concept and methodology of DDos attacks
Goals
- Target on availability
- take out a large site with little computing work
- How: amplification
- DoS bug -> design flaw
- DoS flood -> command bot-net to generate a flood of requests
- Will bypass SYN flood protection proxy
Mitigation
- Client puzzles
- given challenges
- for TCP connection floods, the first data must contain a puzzle solution, otherwise, the TCP connection is closed.
- for SSL handshake DoS
- Challenge C based on TLS session ID
- Server: check puzzle solution before RSA decryption
- Limitations
- Requires changes to both clients and servers
- Hurts low-power legitimate clients during an attack
- CAPTCHAs
- Applies to application layer DDoS
- Source identification Ingress filtering
- identify packet source
- block the attack at the source
- ISP only forwards packets with legitimate source IP
- Source identification Traceback
- DDoS involves many packets on thes ame path
- Store one link in each packet
- Path can be long
Countermeasures
- Prevent initial hack
- Use of firewalls
- Check ingress/egress packets
- Use a server farm and load balancer to offset the effects of a DDoS attack
- Change the IP address of the attacked system
Week8:Penetration Testing in Practice
OUTLINE
Understanding Key Concepts
Test Preparation - What needs to be prepared before testing.
Penetration Testing - Steps to conduct a successful test.
Common Traps
DevSecOps
Sample Pentest - A story of a real penetration test, objectives, and results!
Skills Enhancement for Penetration Testing
A penetration test involves the use of a variety of manual and automated techniques to simulate an attack on an organization's information security arrangements - either from malicious outsiders or your own staff.
Types of tests:
- Application penetration testing (typically web applications), which finds technical vulnerabilities
- Infrastructure penetration testing, which examines servers, firewalls and other hardware for security vulnerabilities.
TIPS
MAC Only
- Authenticity
- Integrity
IEEE 802.11i Security of WPA2 CCMP
- Authentication: Verifying the identity of users or devices.
- Confidentiality: Protecting data from being intercepted during transmission by encrypting it.
- Integrity: Ensuring that data is not tampered with during transmission using checksums and Message Authentication Codes (MAC).
Transport Layer Security (TLS):
- Confidentiality: Protecting data from being intercepted during transmission by encrypting it.
- Integrity: Ensuring that data is not tampered with during transmission using checksums and Message Authentication Codes (MAC).
- Authentication: Verifying the identity of communication parties through methods like digital certificates.