网络拓扑图
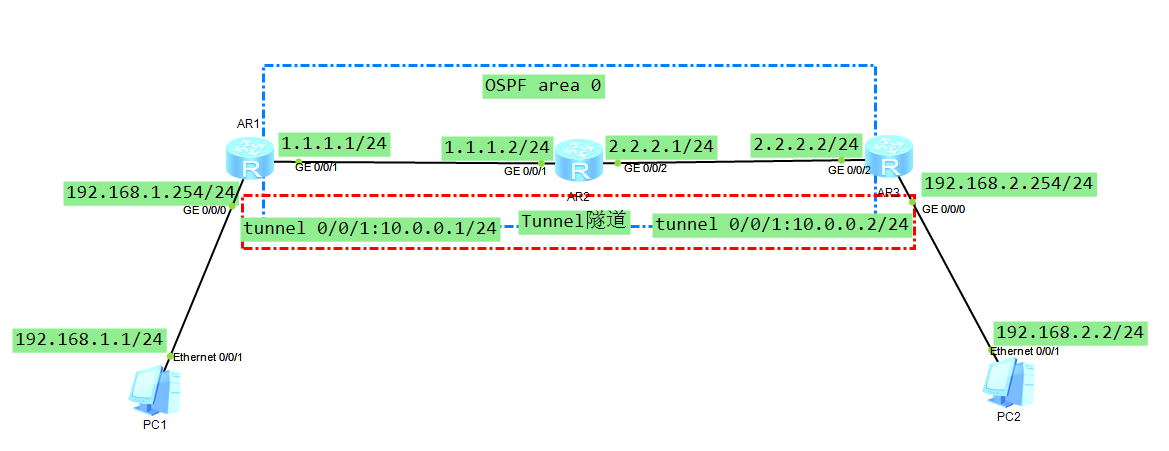
解释:pc1和pc2分别属于一个公司的两个地区的不同私网,pc1所属的区域出口为静态公网地址1.1.1.1,pc2所属的区域出口为静态公网地址2.2.2.2。
需求:
1.实现pc1所在网段可以访问外网;
2.实现pc2所在网段可以访问外网;
3.实现pc1所在网段可以直接通过内网地址访问pc2所在网络。
4.实现pc2所在网段可以直接通过内网地址访问pc1所在网络。
配置步骤:
1.配置路由器和pc机的端口IP。
2.AR1、AR2、AR3直接通过ospf实现路由互通。
3.分别在AR1的ge0/0/1和AR3的ge0/0/2做nat,实现内网访问互联网。
3.分别在AR1和AR3配置GRE。
4.分别在AR1和AR3上配置两个私网到对端内网的路由,使其走gre隧道。
路由器和pc配置如下。
PC1:

AR1:
[AR1]display current-configuration [V200R003C00] # sysname AR1 # snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00 # portal local-server load flash:/portalpage.zip # drop illegal-mac alarm # wlan ac-global carrier id other ac id 0 # set cpu-usage threshold 80 restore 75 # acl number 2000 rule 5 permit # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http # firewall zone Local priority 15 # interface GigabitEthernet0/0/0 ip address 192.168.1.254 255.255.255.0 # interface GigabitEthernet0/0/1 ip address 1.1.1.1 255.255.255.0 nat outbound 2000 # interface GigabitEthernet0/0/2 # interface NULL0 # interface Tunnel0/0/1 ip address 10.0.0.1 255.255.255.0 tunnel-protocol gre source 1.1.1.1 destination 2.2.2.2 # ospf 1 router-id 1.1.1.1 area 0.0.0.0 network 1.1.1.1 0.0.0.0 # ip route-static 192.168.2.0 255.255.255.0 Tunnel0/0/1 # user-interface con 0 authentication-mode password user-interface vty 0 4 user-interface vty 16 20 # wlan ac # return
AR2:
[AR2]display current-configuration [V200R003C00] # sysname AR2 # snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00 # portal local-server load flash:/portalpage.zip # drop illegal-mac alarm # wlan ac-global carrier id other ac id 0 # set cpu-usage threshold 80 restore 75 # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http # firewall zone Local priority 15 # interface GigabitEthernet0/0/0 # interface GigabitEthernet0/0/1 ip address 1.1.1.2 255.255.255.0 # interface GigabitEthernet0/0/2 ip address 2.2.2.1 255.255.255.0 # interface NULL0 # ospf 1 router-id 2.2.2.2 area 0.0.0.0 network 1.1.1.2 0.0.0.0 network 2.2.2.1 0.0.0.0 # user-interface con 0 authentication-mode password user-interface vty 0 4 user-interface vty 16 20 # wlan ac # return
AR3:
[AR3]display current-configuration [V200R003C00] # sysname AR3 # snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00 # portal local-server load flash:/portalpage.zip # drop illegal-mac alarm # wlan ac-global carrier id other ac id 0 # set cpu-usage threshold 80 restore 75 # acl number 2000 rule 5 permit # aaa authentication-scheme default authorization-scheme default accounting-scheme default domain default domain default_admin local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$ local-user admin service-type http # firewall zone Local priority 15 # interface GigabitEthernet0/0/0 ip address 192.168.2.254 255.255.255.0 # interface GigabitEthernet0/0/1 # interface GigabitEthernet0/0/2 ip address 2.2.2.2 255.255.255.0 nat outbound 2000 # interface NULL0 # interface Tunnel0/0/1 description 1.1.1.1 ip address 10.0.0.2 255.255.255.0 tunnel-protocol gre source 2.2.2.2 destination 1.1.1.1 # ospf 1 router-id 3.3.3.3 area 0.0.0.0 network 2.2.2.2 0.0.0.0 # ip route-static 192.168.1.0 255.255.255.0 Tunnel0/0/1 # user-interface con 0 authentication-mode password user-interface vty 0 4 user-interface vty 16 20 # wlan ac # return
PC2:
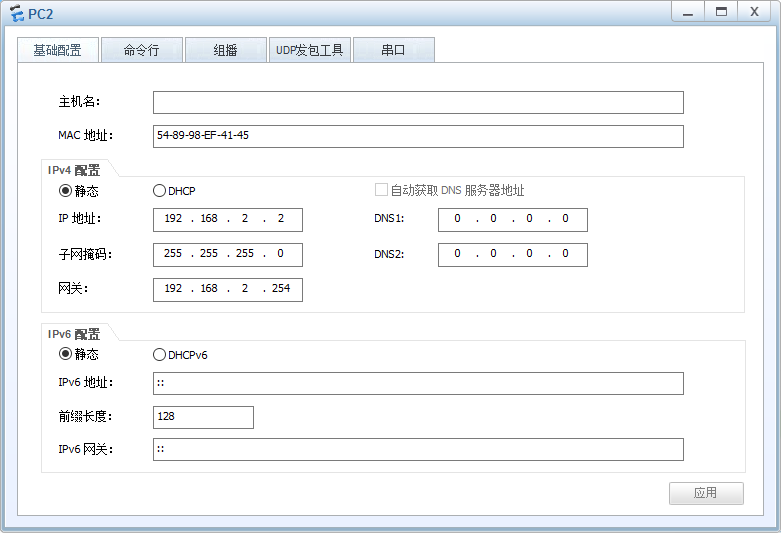
实验结果:
