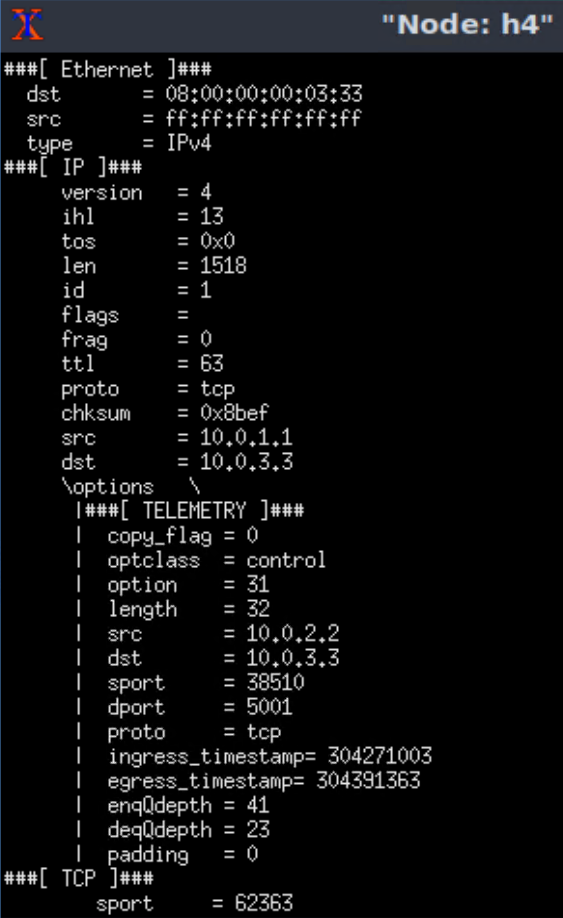
使用p4_16复现Burstradar
github链接:Burstradar的bmv2源码
实验过程
根据教程的提示,直接运行sudo make run可能会出现报错error: clone3: unknown extern function,其中,提示信息建议使用clone_preserving_field_list进行代替。我们可以找到,原始代码的写法为:
clone3(CloneType.E2E,E2E_CLONE_SESSION_ID,meta);
如果只是将clone3直接替换成clone_preserving_field_list,则还会出现meta参数的报错,如下图所示:
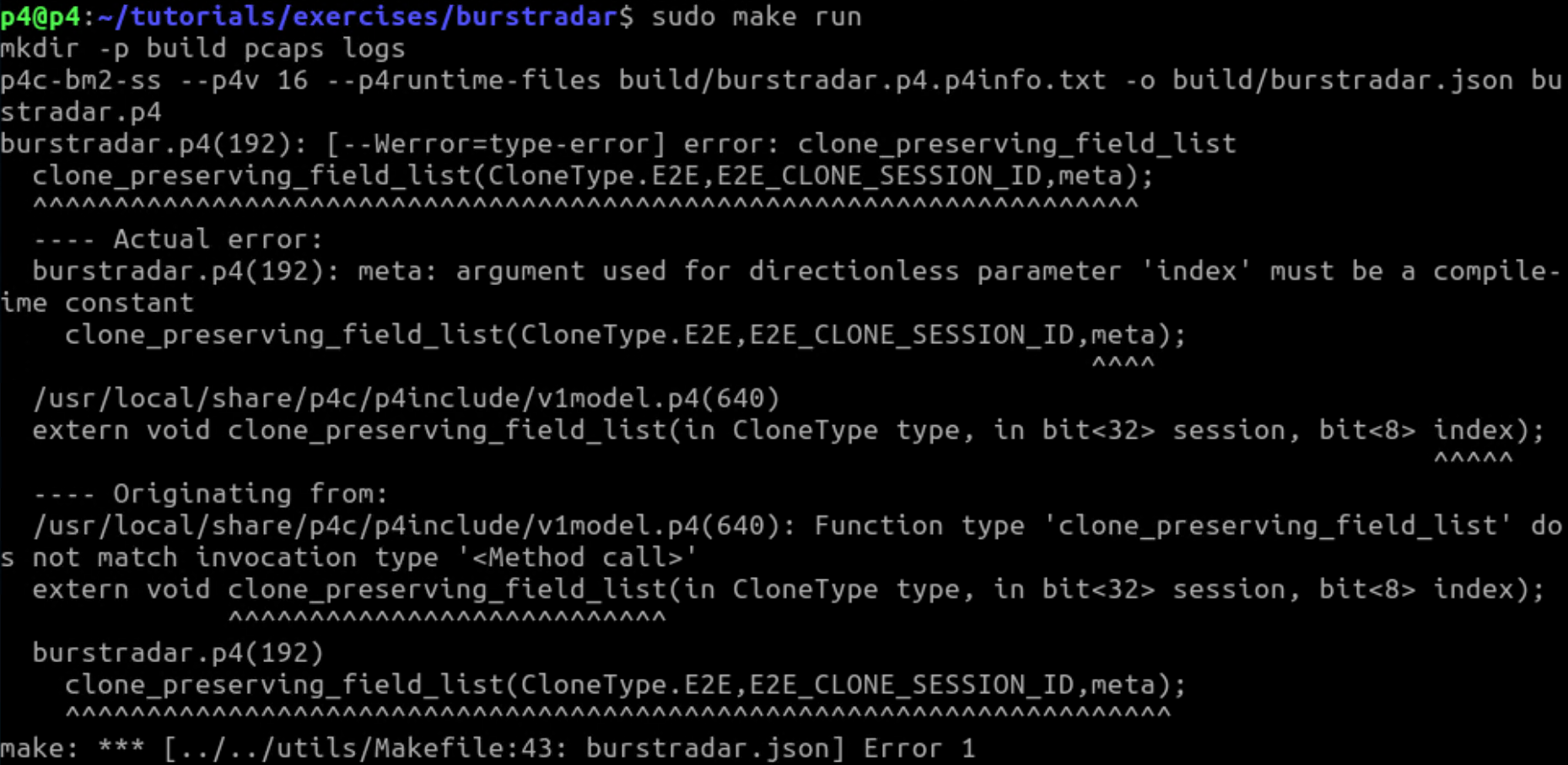
可以看到报错的meta参数是metadata类型的,根据参考链接中的例子,我们对代码进行了修改:
struct metadata {
@field_list(1)
bit<1> flag; // metadata for each packet
@field_list(1,2)
bit<7> index;
}
action do_clone_e2e(){
clone_preserving_field_list(CloneType.E2E,E2E_CLONE_SESSION_ID,1);
}
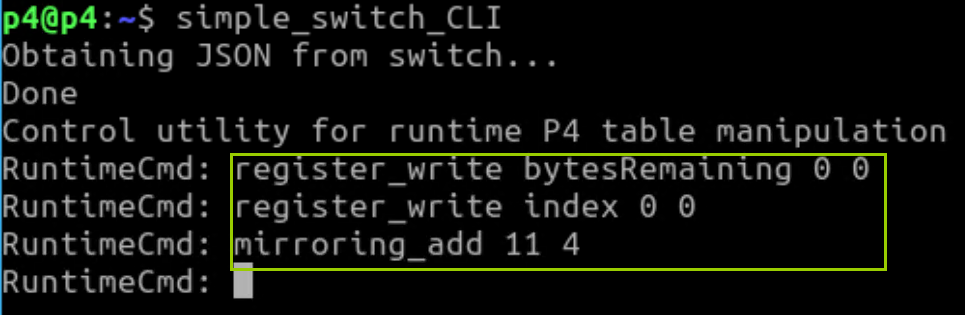
在simple_switch_CLI中,方框内的配置需要自己输入:
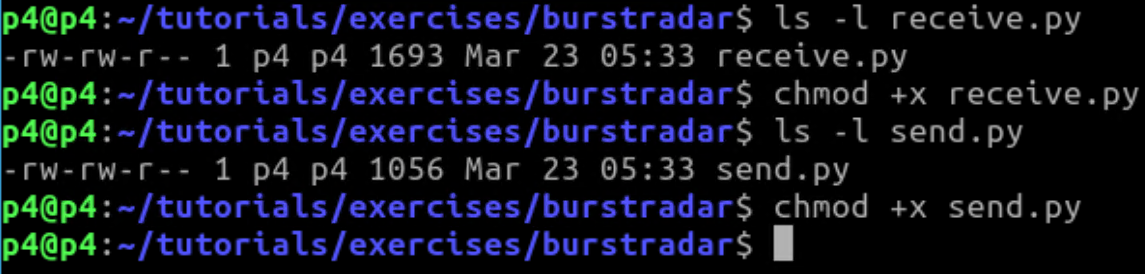
如果直接在xterm终端中运行./receive.py,会出现permission denied报错,使用ls -l命令查看receive.py文件的权限,可以看到缺少执行权限,需要用chmod +x命令添加,send.py同理,如下图所示:
如果系统中只存在python3,则需要对receive.py以及send.py进行修改,receive.py修改后的代码如下所示,send.py同理修改,只需要改第一行的python类型以及print的输出格式即可
#!/usr/bin/env python3
import sys
import struct
import os
from scapy.all import sniff, sendp, hexdump, get_if_list, get_if_hwaddr
from scapy.all import Packet, IPOption
from scapy.fields import ShortField, IntField, LongField, BitField, FieldListField, FieldLenField, SourceIPField, Emph, ShortEnumField, ByteEnumField, ByteField
from scapy.all import IP, TCP, UDP, Raw
from scapy.layers.inet import _IPOption_HDR, DestIPField
from scapy.data import IP_PROTOS, TCP_SERVICES
def get_if():
ifs=get_if_list()
iface=None
for i in get_if_list():
if "eth0" in i:
iface=i
break;
if not iface:
print("Cannot find eth0 interface")
exit(1)
return iface
class IPOption_TELEMETRY(IPOption):
name = "TELEMETRY"
option = 31
fields_desc = [ _IPOption_HDR,
ByteField("length", 2),
Emph(SourceIPField("src", "dst")),
Emph(DestIPField("dst", "127.0.0.1")),
ShortEnumField("sport", 20, TCP_SERVICES),
ShortEnumField("dport", 80, TCP_SERVICES),
ByteEnumField("proto", 0, IP_PROTOS),
BitField("ingress_timestamp", 0, 48),
BitField("egress_timestamp", 0, 48),
BitField("enqQdepth", 0, 19),
BitField("deqQdepth", 0, 19),
BitField("padding", 0, 2) ]
def handle_pkt(pkt):
if TCP in pkt and pkt[TCP].dport == 1234:
print("got a packet")
pkt.show2()
# hexdump(pkt)
sys.stdout.flush()
def main():
ifaces = list(filter(lambda i: 'eth' in i, os.listdir('/sys/class/net/')))
iface = ifaces[0]
print("sniffing on %s" % iface)
sys.stdout.flush()
sniff(iface = iface,
prn = lambda x: handle_pkt(x))
if __name__ == '__main__':
main()
实验效果
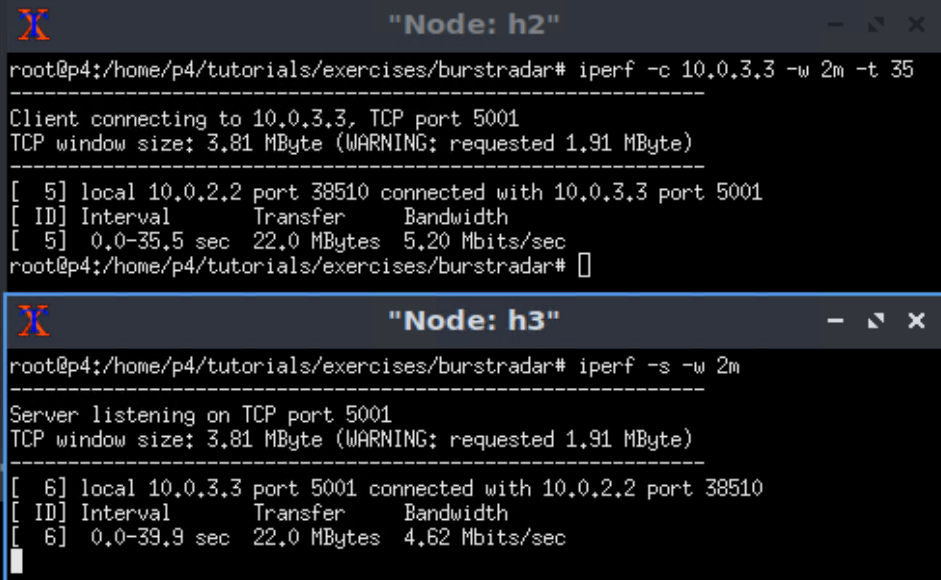
h1与h3:
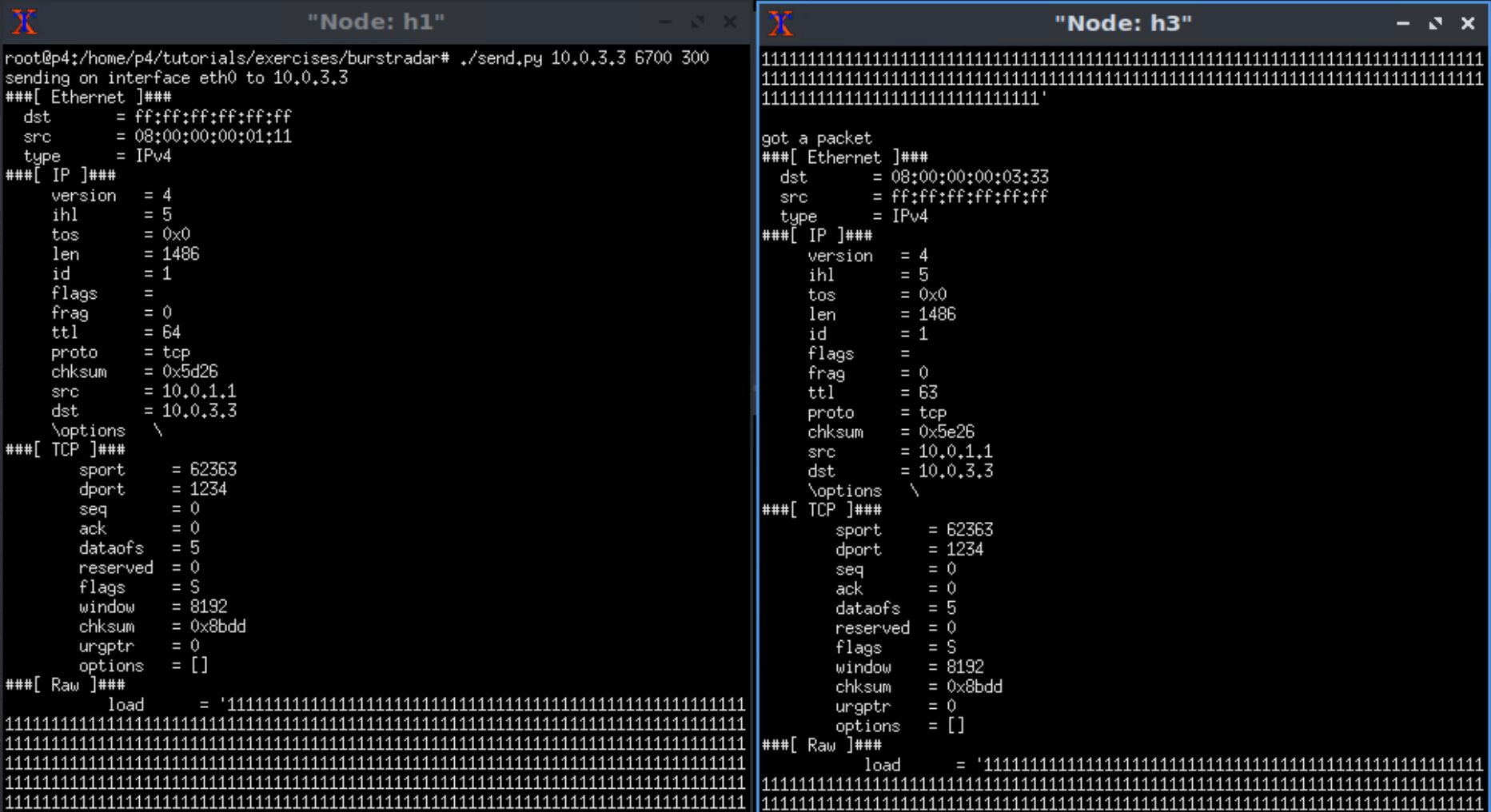
监控器端: