实验一(基本ACL的应用)
学会配置基础的ACL
拓扑
在AR1对应位置配置ACL,使PC1禁止访问PC2

配置
PC1配置,PC2参考PC1
AR1配置
<Huawei>sys
[Huawei]sys AR1
[AR1]inte gi 0/0/0
[AR1-GigabitEthernet0/0/0]ip addr 192.168.1.254 255.255.255.0
[AR1-GigabitEthernet0/0/0]inte gi 0/0/1
[AR1-GigabitEthernet0/0/1]ip addr 192.168.2.254 255.255.255.0
[AR1-GigabitEthernet0/0/1]q
[AR1]acl 2000 //创建一个基本的ACL
[AR1-acl-basic-2000]rule deny source 192.168.1.1 0.0.0.0 //添加一条规则拒绝来自192.168.1.1的流量
[AR1-acl-basic-2000]q
[AR1]inte gi 0/0/0
[AR1-GigabitEthernet0/0/0]traffic-filter inbound acl 2000 //给GE0/0/0的入流量设置ACL规则
测试
PC1 ping PC2(无法通信)
PC>ping 192.168.2.1
Ping 192.168.2.1: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
--- 192.168.2.1 ping statistics ---
3 packet(s) transmitted
0 packet(s) received
100.00% packet loss
查看ACL规则匹配次数
[AR1]dis acl 2000
Basic ACL 2000, 1 rule
Acl's step is 5
rule 5 deny source 192.168.1.1 0 (3 matches) \\规则匹配了三次,成功阻拦了PC1 和 PC2的通信
PC1和网关的通信(无法通信)
因为ACL规则应用在GE0/0/0的入流量中,所以流量无法进入到接口到达路由器,所以网关也无法通信,接下来更改规则的应用位置,在GE0/0/1的出流量中应用此规则
PC>ping 192.168.1.254
Ping 192.168.1.254: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
--- 192.168.1.254 ping statistics ---
2 packet(s) transmitted
0 packet(s) received
100.00% packet loss
AR1配置
[AR1-GigabitEthernet0/0/0]undo traffic-filter inbound
[AR1-GigabitEthernet0/0/0]inte gi 0/0/1
[AR1-GigabitEthernet0/0/1]traffic-filter outbound acl 2000
此时再测试PC1和网关的通信(通信成功),PC1和PC2的通信(无法通信)
PC>ping 192.168.2.1
Ping 192.168.2.1: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
--- 192.168.2.1 ping statistics ---
2 packet(s) transmitted
0 packet(s) received
100.00% packet loss
PC>ping 192.168.1.254
Ping 192.168.1.254: 32 data bytes, Press Ctrl_C to break
From 192.168.1.254: bytes=32 seq=1 ttl=255 time=16 ms
From 192.168.1.254: bytes=32 seq=2 ttl=255 time=15 ms
--- 192.168.1.254 ping statistics ---
2 packet(s) transmitted
2 packet(s) received
0.00% packet loss
round-trip min/avg/max = 15/15/16 ms
实验2
学会配置高级ACL
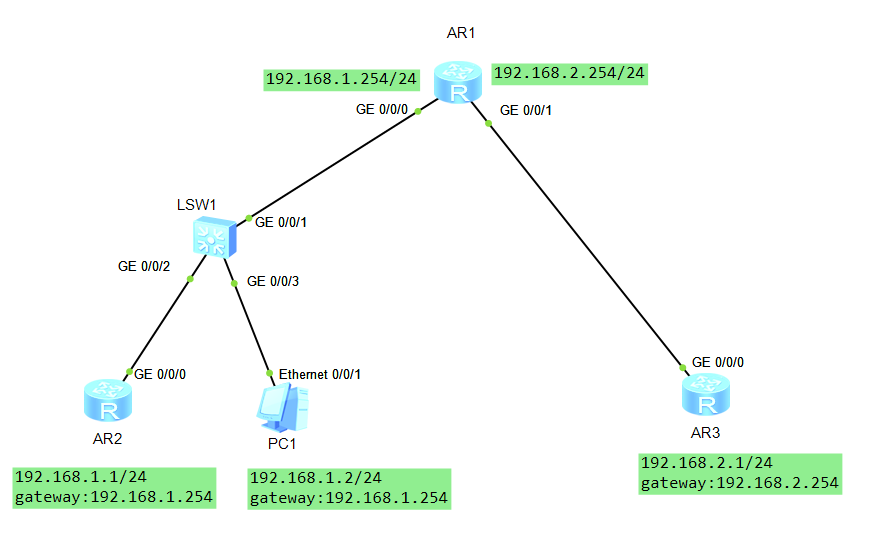
拓扑
配置AR3为telnet服务器
配置ACL规则禁止AR2使用telnet远程控制AR3,但可以ping通AR3
配置
PC1配置
AR2配置
<Huawei>sys
[Huawei]sys AR2
[AR2]inte gi 0/0/0
[AR2-GigabitEthernet0/0/0]ip addr 192.168.1.1 255.255.255.0
[AR2-GigabitEthernet0/0/0]q
[AR2]ip route-static 0.0.0.0 0 192.168.1.254
AR3配置
<Huawei>sys
[Huawei]sys AR3
[AR3]inte gi 0/0/0
[AR3-GigabitEthernet0/0/0]ip addr 192.168.2.1 255.255.255.0
[AR3-GigabitEthernet0/0/0]q
[AR3]ip route-static 0.0.0.0 0 192.168.2.254
[AR3]user-interface vty 0 4
[AR3-ui-vty0-4]authentication-mode password
Please configure the login password (maximum length 16):abc.123
[AR3-ui-vty0-4]protocol inbound telnet
[AR3-ui-vty0-4]user privilege level 15
AR1配置
<Huawei>sys
[Huawei]sys AR1
[AR1]inte gi 0/0/0
[AR1-GigabitEthernet0/0/0]ip addr 192.168.1.254 255.255.255.0
[AR1-GigabitEthernet0/0/0]inte gi 0/0/1
[AR1-GigabitEthernet0/0/1]ip addr 192.168.2.254 255.255.255.0
[AR1]acl name telnent_deny 3000 //创建高级ACL,名为telnet_deny
[AR1-acl-adv-telnent_deny]rule deny tcp source 192.168.1.1 0 destination 192.168
.2.1 0 destination-port eq 23 //设置规则,禁止192.168.1.1访问192.168.2.1的23端口(telnet服务)
[AR1-acl-adv-telnent_deny]q
[AR1]inte gi 0/0/0
[AR1-GigabitEthernet0/0/0]traffic-filter inbound acl 3000
测试
AR1 ping AR3
<AR2>ping 192.168.2.1
PING 192.168.2.1: 56 data bytes, press CTRL_C to break
Reply from 192.168.2.1: bytes=56 Sequence=1 ttl=254 time=40 ms
Reply from 192.168.2.1: bytes=56 Sequence=2 ttl=254 time=40 ms
Reply from 192.168.2.1: bytes=56 Sequence=3 ttl=254 time=50 ms
--- 192.168.2.1 ping statistics ---
3 packet(s) transmitted
3 packet(s) received
0.00% packet loss
round-trip min/avg/max = 40/43/50 ms
AR1 远程连接AR3
<AR2>telnet 192.168.2.1
Press CTRL_] to quit telnet mode
Trying 192.168.2.1 ...
Error: Can't connect to the remote host
由于AR1做了在GE0/0/0的入流量的规则,限制了AR2访问AR3 telnet的流量,但没有限制ICMP,所以可以正常ping通,接下来去除ACL规则检测AR2远程连接AR3
AR1配置
[AR1]inte gi 0/0/0
[AR1-GigabitEthernet0/0/0]undo traffic-filter inbound
再测试AR2 远程连接 AR3
<AR2>telnet 192.168.2.1
Press CTRL_] to quit telnet mode
Trying 192.168.2.1 ...
Connected to 192.168.2.1 ...
Login authentication
Password:
<AR3>