之前一直没啥时间,假期做了一下D3的安卓题目D3Tetris。
总的来说如果能够动调来做这道题会好很多。
-
首先是它的Java层整体做了混淆,不是很好看,在MainActivity部分大致都是些界面相关,无关痛痒。
-
主要是有一个com.jetgame.tetris.logic下的GameViewModel类,其中有两个native函数格外亮眼,这样归功于解析so时发现了这样两个导出函数。oO0OooOo0oO是类构造时候就会调用的方法,而另一个是在发送网络请求时调用的。


-
然后就是so没有JNI_OnLoad,在.init_array有两个函数,其中第一个是进行了一系列检查,第二个则是写了一个base64表

-
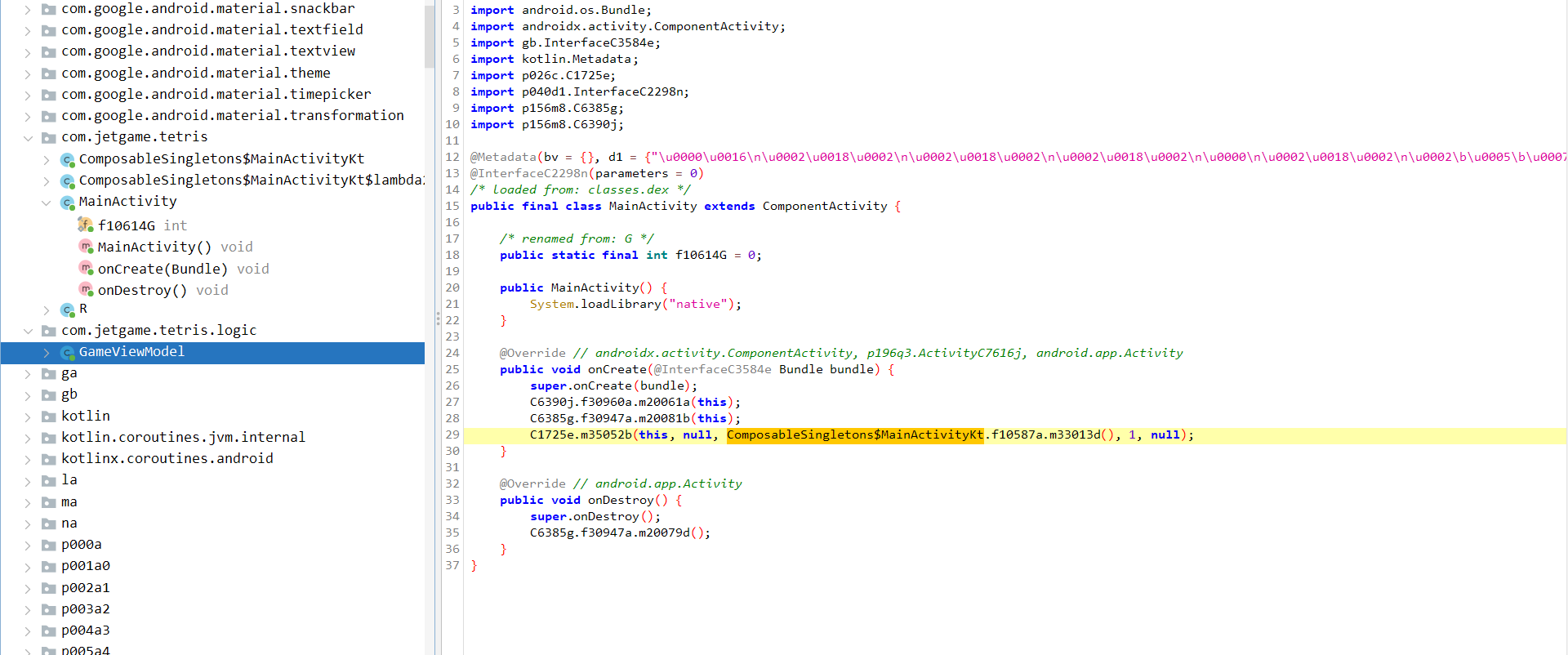
将IDA断点下在两个导出函数开头,同时下断到init_array段第一个函数开头,并且设置开头等自动断点,因为只有断在开头才能绕过Frida检查,否则在Frida环境中闪退
-
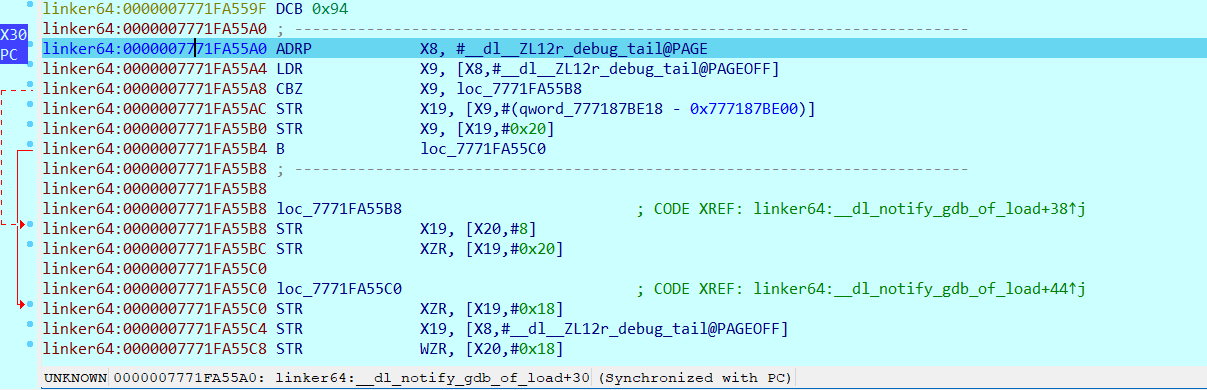
使用调试模式启动APP,并且使用IDA进行附加,然后JDWP继续运行APP,点几下运行然后IDA会断在linker位置说明已经可以动调了。
-
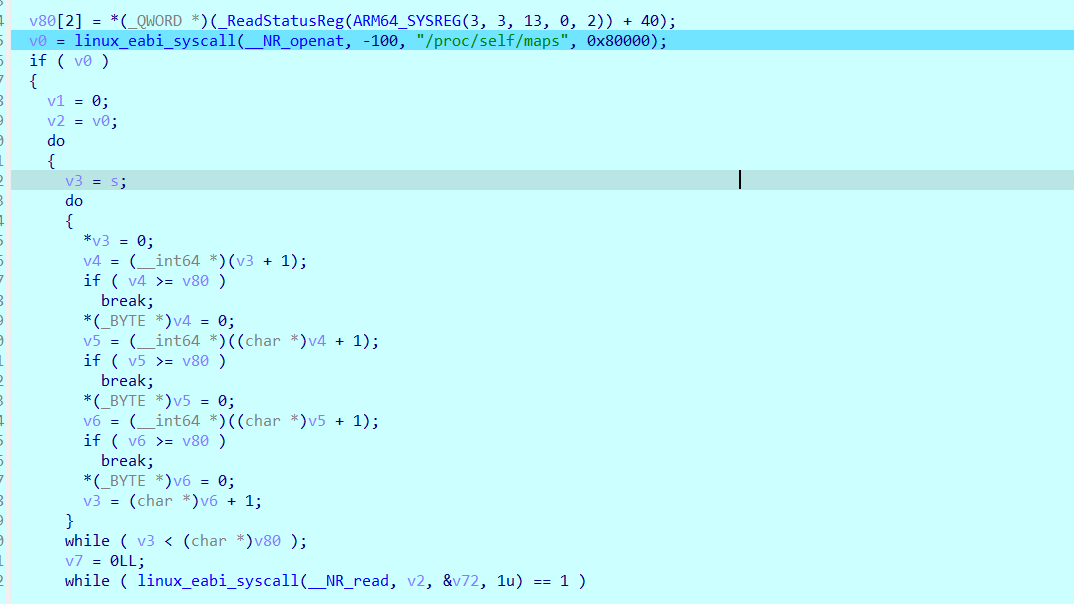
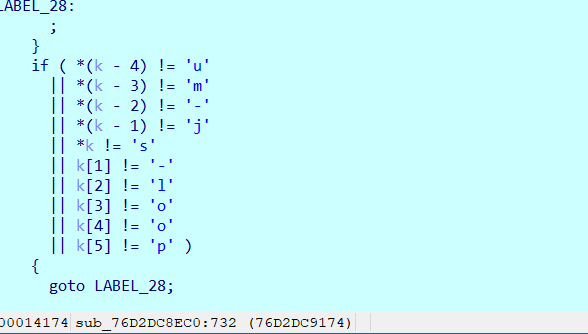
继续运行,直到断在刚刚下的断点位置处,然后直接断在最后一行c,因为这里起了一个线程,这个函数显然实在判断一些特征字符串,官方WP给出了具体实现,对照so反汇编也可以发现其中检查gum-js-loop等字符串
https://github.com/darvincisec/DetectFrida/blob/master/app/src/main/c/native-lib.c

-
执行到线程的创建时直接改PC指针,跳过检查线程的创建

-
绕过后点击继续运行直到断在刚刚的第一个导出函数
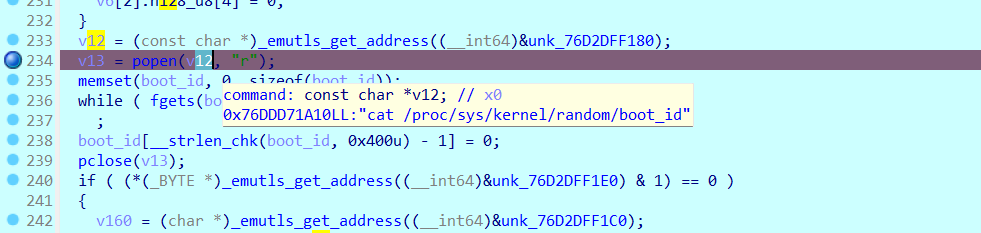
Java_com_jetgame_tetris_logic_GameViewModel_oO0OooOo0oO开头位置,然后往下找就会找到一个popen。读了/proc/sys/kernel/random/boot_id,这是一个特征值它在每次系统启动时生成并保持不变,直到下一次重新启动,共36位5267126b-49a3-4473-9e5c-xxxxxxxxxxxx
-
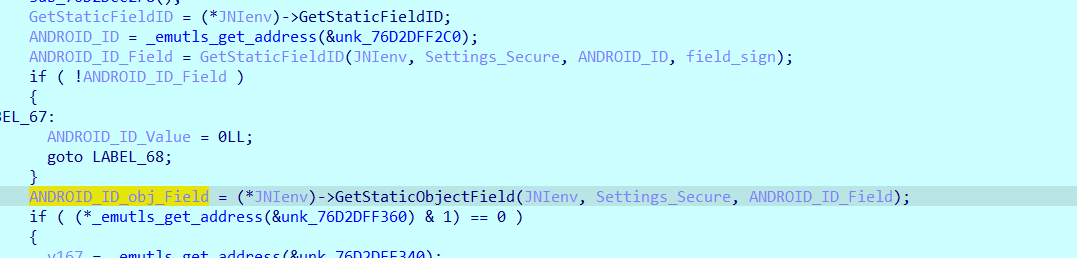
之后凡是遇到JNI函数就下一个断点,因为要看具体的参数进行分析,so里面的字符串均为加密后的结果,断到这些位置能够很好的进行分析。先是获取到
android/provider/Settings$Secure这个类,然后拿到android/content/Context这个类,然后拿到android/content/Context下getContentResolver这个方法的ID,然后通过Secure获取到里面的ANDROID_ID字段的ID,该字段为设备唯一标识符,但是会随着刷机而改变。然后拿到android/app/ActivityThread这个类,通过其获得currentActivityThread这个方法的ID并随之进行了调用,然后拿到了getContentResolver的返回对象,然后使用getString拿ANDROID_ID,就是String androidId = Secure.getString(context.getContentResolver(), Secure.ANDROID_ID);的意思

-
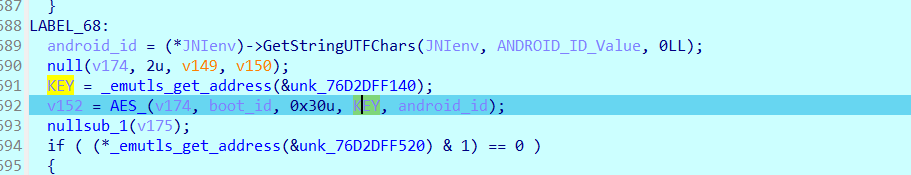
拿到的ANDROID_ID应当为16位。类似
1d3570xxxxe67c30,然后就是一个魔改的AES,并且可以观测其参数有boot_id和ANDROID_ID以及一个KEY:A SIMPLE KEY!!!!!!!!!!!!!!!!!!!!
-
之后进行了RC4,密钥为
SKJ<HANIOSHDLJKa
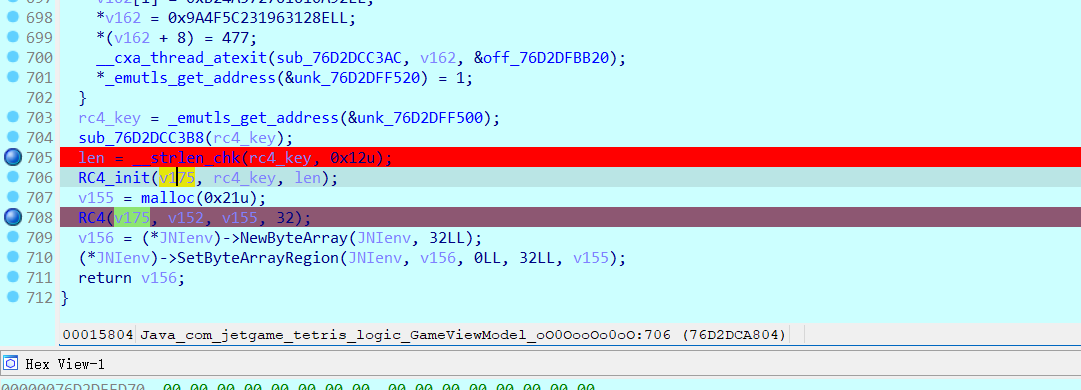
-
到这里还有一个流量包没用,将流量里面的protobuf数据提取出来base64编码,然后解就可以了
import blackboxprotobuf
import base64
data = base64.b64decode('CAESIKZiLmL3esNca/V0RG2K9rKkhETw946h0N0JxmInCHTpGhAzZDM1NGU5ODk2M2E2OWIyIDwoqpWa/fUwMAI=')
message,typedef = blackboxprotobuf.protobuf_to_json(data)
print(message)
print(typedef)
- 得到
{
"1": "1",
"2": "\\xa6b.b\\xf7z\\xc3\\k\\xf5tDm\\x8a\\xf6\\xb2\\xa4\\x84D\\xf0\\xf7\\x8e\\xa1\\xd0\\xdd\t\\xc6b'\bt\\xe9",
"3": "3d354e98963a69b2",
"4": "60",
"5": "1680936962730",
"6": "2"
}
- 最后借用V0id?的脚本一用拿到flag前32位,后四位比赛官方hint给出
class RC4:
def __init__(self, key) -> None:
self.key = key
self.S = 0
self.__rc4_init__()
def __rc4_init__(self):
S = [i for i in range(256)]
j = 0
for i in range(256):
j = (j + S[i] + self.key[i % len(self.key)]) % 256
S[i], S[j] = S[j], S[i]
self.S = S
def rc4_encrypt(self, plain) -> list:
i = 0
j = 0
cipher = []
for p in plain:
i = (i + 1) % 256
j = (j + self.S[i]) % 256
self.S[i], self.S[j] = self.S[j], self.S[i]
k = p ^ self.S[(self.S[i] + self.S[j]) % 256]
cipher.append(k)
return cipher
s_box = (
0x90, 0x7A, 0x50, 0xEF, 0xF0, 0x9C, 0x2F, 0x7D, 0xA0, 0x34,
0x23, 0xCA, 0x4F, 0x21, 0x66, 0x6B, 0x3D, 0xE0, 0xC2, 0xB3,
0xFC, 0x69, 0x08, 0xFF, 0x7F, 0x16, 0x48, 0xD5, 0xEB, 0x59,
0xD8, 0x0C, 0xF3, 0xE4, 0xA8, 0xEA, 0xB9, 0x81, 0x01, 0x28,
0x13, 0xB8, 0x6C, 0xCB, 0xDC, 0x8A, 0x27, 0x19, 0xD2, 0xA4,
0xD3, 0x99, 0x49, 0x57, 0x87, 0xDF, 0x2D, 0x4A, 0xC1, 0x58,
0xB4, 0x68, 0xDE, 0xC7, 0x94, 0x7B, 0xAA, 0xE2, 0x8C, 0x53,
0xAD, 0x1E, 0x04, 0xC5, 0x18, 0x00, 0xED, 0xF1, 0x79, 0x43,
0x51, 0xB0, 0x84, 0x5A, 0xEE, 0x97, 0x88, 0x26, 0xB6, 0x73,
0x9D, 0x5B, 0xFE, 0xE5, 0x54, 0xF4, 0xB1, 0x06, 0x3F, 0xBC,
0x31, 0x60, 0xA1, 0x85, 0xC9, 0xF8, 0xC6, 0xE7, 0xAE, 0xC3,
0x82, 0x9F, 0xFB, 0xCE, 0xFD, 0x32, 0x8D, 0x2E, 0x41, 0xBF,
0x37, 0xB7, 0xEC, 0x77, 0x02, 0x80, 0x3B, 0x76, 0x92, 0x14,
0xD0, 0x4C, 0x38, 0x89, 0x1C, 0x46, 0x2B, 0x0B, 0xC4, 0x72,
0x0E, 0xCD, 0x62, 0x10, 0x6F, 0x09, 0x8F, 0x7C, 0xD4, 0xD7,
0x6D, 0xF7, 0x9B, 0xAC, 0x20, 0x12, 0x64, 0xDD, 0xCC, 0xFA,
0x70, 0xF9, 0x35, 0x1D, 0x9A, 0x52, 0xF5, 0x0D, 0xAF, 0xBA,
0xA6, 0x30, 0x29, 0x8B, 0x7E, 0xC0, 0x83, 0x95, 0x61, 0x44,
0xA3, 0x22, 0x75, 0x5E, 0xA7, 0x55, 0x2A, 0x91, 0xF2, 0x42,
0xA2, 0x56, 0xB5, 0x5F, 0xDB, 0x36, 0x47, 0xBE, 0x86, 0xA5,
0x40, 0x15, 0x5D, 0x8E, 0xBD, 0xC8, 0x1A, 0xD1, 0x3C, 0x07,
0x11, 0x33, 0xBB, 0x6E, 0x9E, 0x96, 0x3A, 0xDA, 0x39, 0x5C,
0x2C, 0x1F, 0x17, 0xE6, 0x25, 0x6A, 0x0A, 0x3E, 0x93, 0xE9,
0x74, 0x65, 0xAB, 0x4D, 0xCF, 0xE8, 0x78, 0x0F, 0xB2, 0xE1,
0xF6, 0x71, 0x03, 0xA9, 0x1B, 0xD6, 0x63, 0x4E, 0xD9, 0x24,
0x98, 0x67, 0x45, 0x05, 0xE3, 0x4B
)
inv_s_box = (
75, 38, 124, 242, 72, 253, 97, 209, 22, 145, 226, 137, 31, 167, 140, 237, 143, 210, 155, 40, 129, 201, 25, 222, 74, 47, 206, 244, 134, 163, 71, 221, 154, 13, 181, 10, 249, 224, 87, 46, 39, 172, 186, 136, 220, 56, 117, 6, 171, 100, 115, 211, 9, 162, 195, 120, 132, 218, 216, 126, 208, 16, 227, 98, 200, 118, 189, 79, 179, 252, 135, 196, 26, 52, 57, 255, 131, 233, 247, 12, 2, 80, 165, 69, 94, 185, 191, 53, 59, 29, 83, 91, 219, 202, 183, 193, 101, 178, 142, 246, 156, 231, 14, 251, 61, 21, 225, 15, 42, 150, 213, 144, 160, 241, 139, 89, 230, 182, 127, 123, 236, 78, 1, 65, 147, 7, 174, 24, 125, 37, 110, 176, 82, 103, 198, 54, 86, 133, 45, 173, 68, 116, 203, 146, 0, 187, 128, 228, 64, 177, 215, 85, 250, 51, 164, 152, 5, 90, 214, 111, 8, 102, 190, 180, 49, 199, 170, 184, 34, 243, 66, 232, 153, 70, 108, 168, 81, 96, 238, 19, 60, 192, 88, 121, 41, 36, 169, 212, 99, 204, 197, 119, 175, 58, 18, 109, 138, 73, 106, 63, 205, 104, 11, 43, 158, 141, 113, 234, 130, 207, 48, 50, 148, 27, 245, 149, 30, 248, 217, 194, 44, 157, 62, 55, 17, 239, 67, 254, 33, 93, 223, 107, 235, 229, 35, 28, 122, 76, 84, 3, 4, 77, 188, 32, 95, 166, 240, 151, 105, 161, 159, 112, 20, 114, 92, 23
)
def sub_bytes(s):
for i in range(4):
for j in range(4):
s[i][j] = s_box[s[i][j]]
def inv_sub_bytes(s):
for i in range(4):
for j in range(4):
s[i][j] = inv_s_box[s[i][j]]
def shift_rows(s):
s[0][1], s[1][1], s[2][1], s[3][1] = s[1][1], s[2][1], s[3][1], s[0][1]
s[0][2], s[1][2], s[2][2], s[3][2] = s[2][2], s[3][2], s[0][2], s[1][2]
s[0][3], s[1][3], s[2][3], s[3][3] = s[3][3], s[0][3], s[1][3], s[2][3]
def inv_shift_rows(s):
s[0][1], s[1][1], s[2][1], s[3][1] = s[3][1], s[0][1], s[1][1], s[2][1]
s[0][2], s[1][2], s[2][2], s[3][2] = s[2][2], s[3][2], s[0][2], s[1][2]
s[0][3], s[1][3], s[2][3], s[3][3] = s[1][3], s[2][3], s[3][3], s[0][3]
def add_round_key(s, k):
for i in range(4):
for j in range(4):
s[i][j] ^= k[i][j]
# learned from https://web.archive.org/web/20100626212235/http://cs.ucsb.edu/~koc/cs178/projects/JT/aes.c
xtime = lambda a: (((a << 1) ^ 0x1B) & 0xFF) if (a & 0x80) else (a << 1)
def mix_single_column(a):
# see Sec 4.1.2 in The Design of Rijndael
t = a[0] ^ a[1] ^ a[2] ^ a[3]
u = a[0]
a[0] ^= t ^ xtime(a[0] ^ a[1])
a[1] ^= t ^ xtime(a[1] ^ a[2])
a[2] ^= t ^ xtime(a[2] ^ a[3])
a[3] ^= t ^ xtime(a[3] ^ u)
def mix_columns(s):
for i in range(4):
mix_single_column(s[i])
def inv_mix_columns(s):
# see Sec 4.1.3 in The Design of Rijndael
for i in range(4):
u = xtime(xtime(s[i][0] ^ s[i][2]))
v = xtime(xtime(s[i][1] ^ s[i][3]))
s[i][0] ^= u
s[i][1] ^= v
s[i][2] ^= u
s[i][3] ^= v
mix_columns(s)
r_con = (
0x00, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40,
0x80, 0x1B, 0x36, 0x6C, 0xD8, 0xAB, 0x4D, 0x9A,
0x2F, 0x5E, 0xBC, 0x63, 0xC6, 0x97, 0x35, 0x6A,
0xD4, 0xB3, 0x7D, 0xFA, 0xEF, 0xC5, 0x91, 0x39,
)
def bytes2matrix(text):
""" Converts a 16-byte array into a 4x4 matrix. """
return [list(text[i:i+4]) for i in range(0, len(text), 4)]
def matrix2bytes(matrix):
""" Converts a 4x4 matrix into a 16-byte array. """
return bytes(sum(matrix, []))
def xor_bytes(a, b):
""" Returns a new byte array with the elements xor'ed. """
return bytes(i^j for i, j in zip(a, b))
def inc_bytes(a):
""" Returns a new byte array with the value increment by 1 """
out = list(a)
for i in reversed(range(len(out))):
if out[i] == 0xFF:
out[i] = 0
else:
out[i] += 1
break
return bytes(out)
def pad(plaintext):
"""
Pads the given plaintext with PKCS#7 padding to a multiple of 16 bytes.
Note that if the plaintext size is a multiple of 16,
a whole block will be added.
"""
padding_len = 16 - (len(plaintext) % 16)
padding = bytes([padding_len] * padding_len)
return plaintext + padding
def unpad(plaintext):
"""
Removes a PKCS#7 padding, returning the unpadded text and ensuring the
padding was correct.
"""
padding_len = plaintext[-1]
assert padding_len > 0
message, padding = plaintext[:-padding_len], plaintext[-padding_len:]
assert all(p == padding_len for p in padding)
return message
def split_blocks(message, block_size=16, require_padding=True):
assert len(message) % block_size == 0 or not require_padding
return [message[i:i+16] for i in range(0, len(message), block_size)]
class AES:
"""
Class for AES-128 encryption with CBC mode and PKCS#7.
This is a raw implementation of AES, without key stretching or IV
management. Unless you need that, please use `encrypt` and `decrypt`.
"""
rounds_by_key_size = {16: 10, 24: 12, 32: 14}
def __init__(self, master_key):
"""
Initializes the object with a given key.
"""
assert len(master_key) in AES.rounds_by_key_size
self.n_rounds = AES.rounds_by_key_size[len(master_key)]
self._key_matrices = self._expand_key(master_key)
def _expand_key(self, master_key):
"""
Expands and returns a list of key matrices for the given master_key.
"""
# Initialize round keys with raw key material.
key_columns = bytes2matrix(master_key)
iteration_size = len(master_key) // 4
i = 1
while len(key_columns) < (self.n_rounds + 1) * 4:
# Copy previous word.
word = list(key_columns[-1])
# Perform schedule_core once every "row".
if len(key_columns) % iteration_size == 0:
# Circular shift.
word.append(word.pop(0))
# Map to S-BOX.
word = [s_box[b] for b in word]
# XOR with first byte of R-CON, since the others bytes of R-CON are 0.
word[0] ^= r_con[i]
i += 1
elif len(master_key) == 32 and len(key_columns) % iteration_size == 4:
# Run word through S-box in the fourth iteration when using a
# 256-bit key.
word = [s_box[b] for b in word]
# XOR with equivalent word from previous iteration.
word = xor_bytes(word, key_columns[-iteration_size])
key_columns.append(word)
# Group key words in 4x4 byte matrices.
return [key_columns[4*i : 4*(i+1)] for i in range(len(key_columns) // 4)]
def encrypt_block(self, plaintext):
"""
Encrypts a single block of 16 byte long plaintext.
"""
assert len(plaintext) == 16
plain_state = bytes2matrix(plaintext)
add_round_key(plain_state, self._key_matrices[0])
for i in range(1, self.n_rounds):
sub_bytes(plain_state)
mix_columns(plain_state)
shift_rows(plain_state)
add_round_key(plain_state, self._key_matrices[i])
sub_bytes(plain_state)
shift_rows(plain_state)
add_round_key(plain_state, self._key_matrices[-1])
return matrix2bytes(plain_state)
def decrypt_block(self, ciphertext):
"""
Decrypts a single block of 16 byte long ciphertext.
"""
assert len(ciphertext) == 16
cipher_state = bytes2matrix(ciphertext)
add_round_key(cipher_state, self._key_matrices[-1])
inv_shift_rows(cipher_state)
inv_sub_bytes(cipher_state)
for i in range(self.n_rounds - 1, 0, -1):
add_round_key(cipher_state, self._key_matrices[i])
inv_shift_rows(cipher_state)
inv_mix_columns(cipher_state)
inv_sub_bytes(cipher_state)
add_round_key(cipher_state, self._key_matrices[0])
return matrix2bytes(cipher_state)
def encrypt_cbc(self, plaintext, iv):
"""
Encrypts `plaintext` using CBC mode and PKCS#7 padding, with the given
initialization vector (iv).
"""
assert len(iv) == 16
plaintext = pad(plaintext)
blocks = []
previous = iv
for plaintext_block in split_blocks(plaintext):
# CBC mode encrypt: encrypt(plaintext_block XOR previous)
block = self.encrypt_block(xor_bytes(plaintext_block, previous))
blocks.append(block)
previous = block
return b''.join(blocks)
def decrypt_cbc(self, ciphertext, iv):
"""
Decrypts `ciphertext` using CBC mode and PKCS#7 padding, with the given
initialization vector (iv).
"""
assert len(iv) == 16
blocks = []
previous = iv
for ciphertext_block in split_blocks(ciphertext):
# CBC mode decrypt: previous XOR decrypt(ciphertext)
blocks.append(xor_bytes(previous, self.decrypt_block(ciphertext_block)))
previous = ciphertext_block
# return unpad(b''.join(blocks))
return b''.join(blocks)
iv = b'3d354e98963a69b2'
aeskey = b'A SIMPLE KEY!!!!!!!!!!!!!!!!!!!!'
aes = AES(aeskey)
enc = [0xa6,0x62,0x2e,0x62,0xf7,0x7a,0xc3,0x5c,0x6b,0xf5,0x74,0x44,0x6d,0x8a,0xf6,0xb2,0xa4,0x84,0x44,0xf0,0xf7,0x8e,0xa1,0xd0,0xdd,0x9,0xc6,0x62,0x27,0x8,0x74,0xe9]
r = RC4(b'SKJ<HANIOSHDLJKa')
ciphertext = r.rc4_encrypt(enc)
print(len(ciphertext))
plaintext = aes.decrypt_cbc(ciphertext,iv)
print(plaintext)