第十二周
信息搜集
arp-scan -l
nmap -p- 192.168.56.14
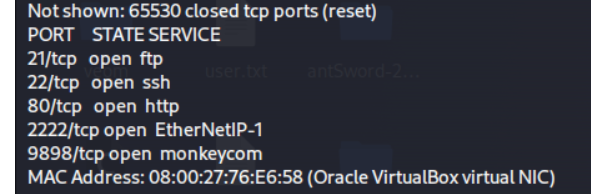
nmap -sV -p21,22,80,2222,9898 192.168.56.14
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http Apache httpd 2.4.38 ((Debian))
2222/tcp open ssh OpenSSH 8.4 (protocol 2.0)
9898/tcp open monkeycom?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9898-TCP:V=7.93%I=7%D=4/12%Time=6436A73A%P=x86_64-pc-linux-gnu%r(NU
SF:LL,DE,"Welcome\x20to\x20Hogwart's\x20magic\x20portal\nTell\x20your\x20s
SF:pell\x20and\x20ELDER\x20WAND\x20will\x20perform\x20the\x20magic\n\nHere
SF:\x20is\x20list\x20of\x20some\x20common\x20spells:\n1\.\x20Wingardium\x2
SF:0Leviosa\n2\.\x20Lumos\n3\.\x20Expelliarmus\n4\.\x20Alohomora\n5\.\x20A
SF:vada\x20Kedavra\x20\n\nEnter\x20your\x20spell:\x20")%r(GenericLines,125
SF:,"Welcome\x20to\x20Hogwart's\x20magic\x20portal\nTell\x20your\x20spell\
SF:x20and\x20ELDER\x20WAND\x20will\x20perform\x20the\x20magic\n\nHere\x20i
SF:s\x20list\x20of\x20some\x20common\x20spells:\n1\.\x20Wingardium\x20Levi
SF:osa\n2\.\x20Lumos\n3\.\x20Expelliarmus\n4\.\x20Alohomora\n5\.\x20Avada\
SF:x20Kedavra\x20\n\nEnter\x20your\x20spell:\x20Magic\x20Output:\x20Oops!!
SF:\x20you\x20have\x20given\x20the\x20wrong\x20spell\n\nEnter\x20your\x20s
SF:pell:\x20")%r(GetRequest,125,"Welcome\x20to\x20Hogwart's\x20magic\x20po
SF:rtal\nTell\x20your\x20spell\x20and\x20ELDER\x20WAND\x20will\x20perform\
SF:x20the\x20magic\n\nHere\x20is\x20list\x20of\x20some\x20common\x20spells
SF::\n1\.\x20Wingardium\x20Leviosa\n2\.\x20Lumos\n3\.\x20Expelliarmus\n4\.
SF:\x20Alohomora\n5\.\x20Avada\x20Kedavra\x20\n\nEnter\x20your\x20spell:\x
SF:20Magic\x20Output:\x20Oops!!\x20you\x20have\x20given\x20the\x20wrong\x2
SF:0spell\n\nEnter\x20your\x20spell:\x20")%r(HTTPOptions,125,"Welcome\x20t
SF:o\x20Hogwart's\x20magic\x20portal\nTell\x20your\x20spell\x20and\x20ELDE
SF:R\x20WAND\x20will\x20perform\x20the\x20magic\n\nHere\x20is\x20list\x20o
SF:f\x20some\x20common\x20spells:\n1\.\x20Wingardium\x20Leviosa\n2\.\x20Lu
SF:mos\n3\.\x20Expelliarmus\n4\.\x20Alohomora\n5\.\x20Avada\x20Kedavra\x20
SF:\n\nEnter\x20your\x20spell:\x20Magic\x20Output:\x20Oops!!\x20you\x20hav
SF:e\x20given\x20the\x20wrong\x20spell\n\nEnter\x20your\x20spell:\x20")%r(
SF:RTSPRequest,125,"Welcome\x20to\x20Hogwart's\x20magic\x20portal\nTell\x2
SF:0your\x20spell\x20and\x20ELDER\x20WAND\x20will\x20perform\x20the\x20mag
SF:ic\n\nHere\x20is\x20list\x20of\x20some\x20common\x20spells:\n1\.\x20Win
SF:gardium\x20Leviosa\n2\.\x20Lumos\n3\.\x20Expelliarmus\n4\.\x20Alohomora
SF:\n5\.\x20Avada\x20Kedavra\x20\n\nEnter\x20your\x20spell:\x20Magic\x20Ou
SF:tput:\x20Oops!!\x20you\x20have\x20given\x20the\x20wrong\x20spell\n\nEnt
SF:er\x20your\x20spell:\x20");
MAC Address: 08:00:27:76:E6:58 (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
访问一下80端口
扫描一下目录
dirsearch -u 192.168.56.14
发现没有什么东西
使用gobuster测试一下
gobuster dir -r -u http://192.168.56.14 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x txt,php,html,md
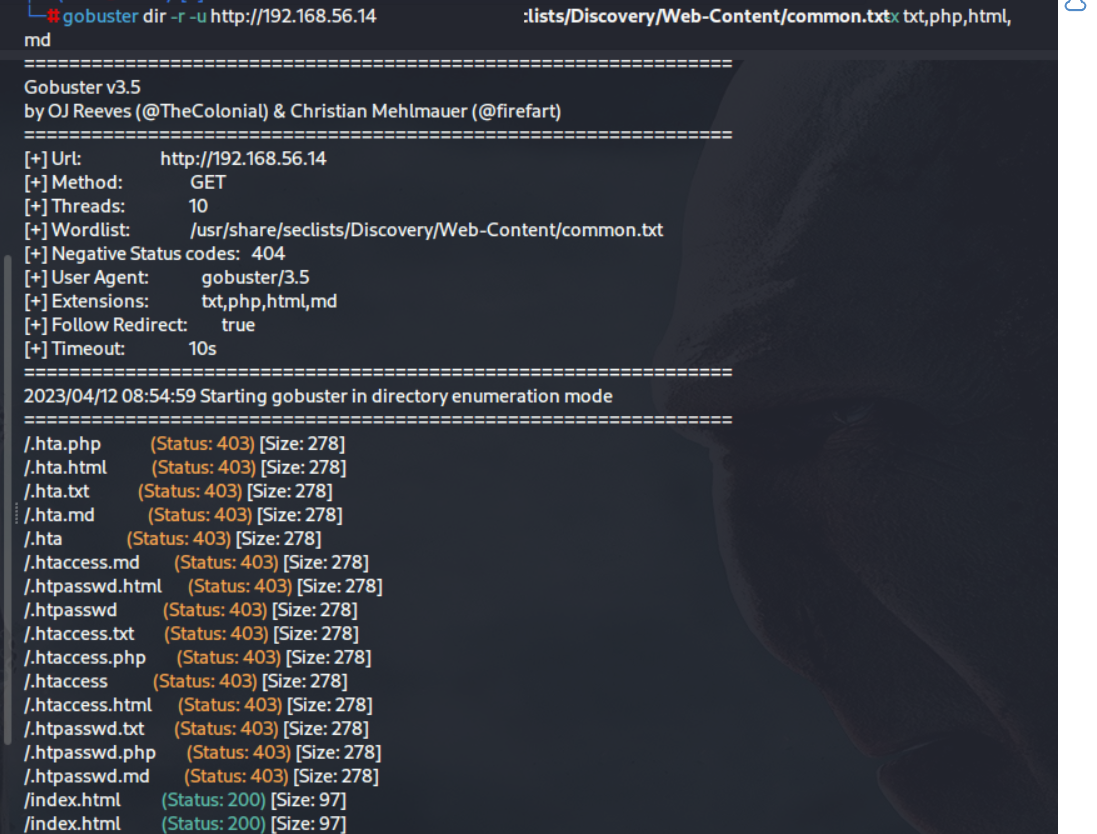
依旧没有什么东西
打点
ftp
ftp 192.168.56.14
anonymous
密码为空
一个文件下载下来
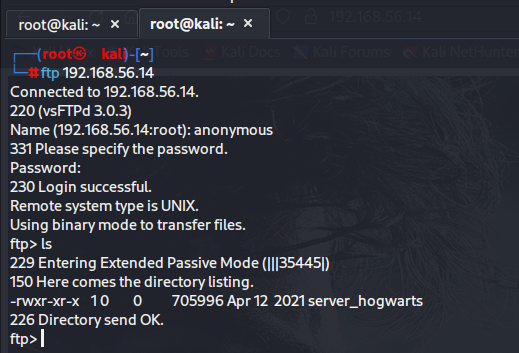
get server_hogwarts

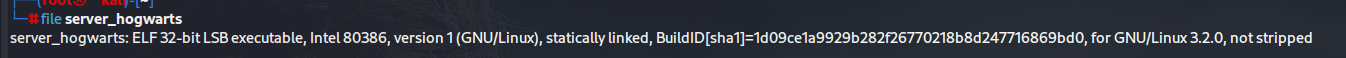
查看文件是什么:linux的可执行程序,那就执行。
chmod +x server_hogwarts
./server_hogwarts

然后就没返回东西,既然在执行,那看下进程有什么
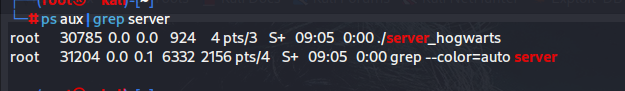
ps aux | grep server
发现了进程,那么看看进程有没有开放别的端口服务
ss -pantu | grep server
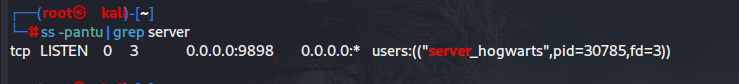
看到开放了9898端口,和靶机上的一样
看看自己这个端口有什么:什么也没有。
nc 127.0.0.1 9898
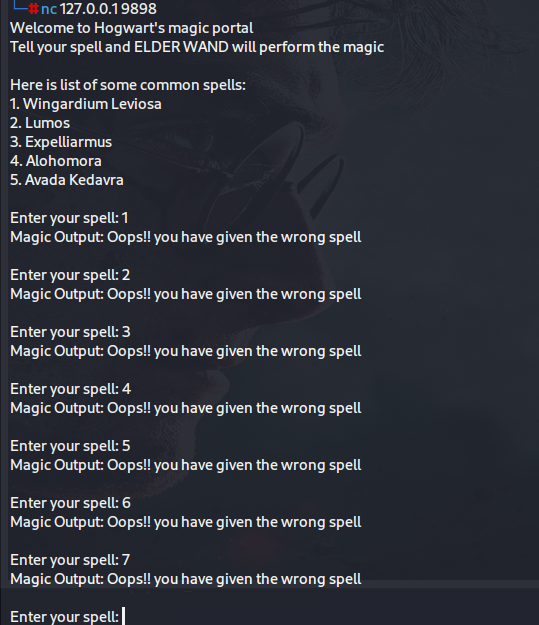
再看看靶机的端口会有什么:
nc 192.168.56.14 9898
和本地一样的,没有收获

缓冲区溢出
使用edb调试server_hogwarts
kali本机存在ALSR安全技术,地址空间随机化,会造成内存地址的随机化,导致我们无法确定缓冲区溢出的位置。所以要关闭。
cd /proc/sys/kernel
echo 0 > randomize_va_space 默认是 2
apt install edb-debugger
调试工具有gdb→命令行的工具,使用edb-debugger工具,更有利于使用
执行输入edb就可以了。
启动测试的服务。打开工具,找到服务,点击run