inconsistencies vulnerabilities differential
CVE-2023-34050 Spring AMQP Deserialization Vulnerability
CVE-2023-34050 Spring AMQP Deserialization Vulnerability MEDIUM | OCTOBER 18, 2023 | CVE-2023-34050 Description In 2016, allowed list patterns for des ......
Understanding q-value and FDR in Differential Expression Analysis
Understanding q-value and FDR in Differential Expression Analysis Daqian Introduction to q-value and FDR In differential gene expression analysis, res ......
差分约束(Differential constraint)
test definition 差分约束系统 是一种特殊的 \(n\) 元一次不等式组,它包含 \(n\) 个变量 \(x_1,x_2\),\(\dots,x_n\) 以及 \(m\) 个约束条件,每个约束条件是由两个其中的变量做差构成的,形如 \(x_i-x_j\leq c_k\),其中 \(1 ......
Detremine center or focus for plane differential system
Distinguish center and focus for plane differential system 背景 对于一个平面光滑微分系统 \[\begin{equation} \dot{x}=f(x,y),~~~ \dot{y}=g(x,y). \end{equation} \]假设 \ ......
SciTech-BigDataAIML-Tensorflow-Introduction to Gradients and Automatic Differentiation
In this guide, you will explore ways to compute gradients with TensorFlow, especially in eager execution. Automatic Differentiation and Gradients Auto ......
【五期李伟平】CCF-A(S&P'20)The Value of Collaboration in Convex Machine Learning with Differential Privacy
Nan W., et al. “The Value of Collaboration in Convex Machine Learning with Differential Privacy.” 2020 IEEE Symposium on Security and Privacy. 304-317 ......
Django报错UnorderedObjectListWarning: Pagination may yield inconsistent results with an unordered object_list
Django报错UnorderedObjectListWarning: Pagination may yield inconsistent results with an unordered object_list 报错 报错信息如下: Django报错Django报错UnorderedObject ......
google chrome remote debbuging vulnerability
Form of expression The first is linpeas.sh in the process of detection found that there is a remote debugging of google chrome.the phenotype and analy ......
什么是计算机安全领域的 Vulnerability Exploit
漏洞是指软件或系统中的安全弱点,它可能允许攻击者以某种方式访问系统、绕过安全控制或获取未经授权的信息。利用漏洞指的是利用这些软件或系统中存在的漏洞、弱点或错误来实施攻击的行为。这个过程通常包括利用已知的漏洞或错误,开发相应的代码或脚本来获取对系统的未授权访问或执行未授权操作。 在计算机安全领域,利用 ......
Apache Shiro Authentication Bypass Vulnerability (CVE-2010-3863)
Apache Shiro Authentication Bypass Vulnerability (CVE-2010-3863) 漏洞简介 Apache Shiro是一款开源安全框架,提供身份验证、授权、密码学和会话管理。shiro框架直观、易用,同时也能提供健壮的安全性。 在Apache Shir ......
Proj. Unknown: Deciding Differential Privacy of Online Algorithms with Multiple Variables
Paper https://arxiv.org/abs/2309.06615 Abstract 背景: 自动机A被称作查分隐私自动机:当对某些D,对任何隐私预算ε>0,该自动机是Dε-differentially private( A DiP automaton is a parametric au ......
论文阅读笔记——LAVA: Large-scale Automated Vulnerability Addition
LAVA: Large-scale Automated Vulnerability Addition Brendan Dolan-Gavitt∗, Patrick Hulin†, Engin Kirda‡, Tim Leek†, Andrea Mambretti‡, Wil Robertson‡, ......
Secure Code Warrior C# Basic OWASP Web Top 10 2017 8: Insecure deserialization, 9: Using Components with Known Vulnerabilities, 10: Insufficient Logging and Monitoring
Last but not least. These set challenges consist of 8: Insecure deserialization, 9: Using Components with Known Vulnerabilities, 10: Insufficient Logg ......
Secure Code Warrior C# Basic OWASP Web Top 10 2017 5: Broken Access Control, 6: Security Misconfiguration and 7: XSS vulnerabilities
Learn the ropes or hone your skills in secure programming here. These challenges will give you an understanding of 5: Broken Access Control, 6: Securi ......
Secure Code Warrior C# Basic OWASP Web Top 10 2017 1: Injection Flaws and 2: Broken Authentication vulnerabilities 3: Sensitive Data Exposure and 4: XXE vulnerabilities
Let's continue with some other very common application weaknesses. This set of levels will focus on 3: Sensitive Data Exposure and 4: XXE vulnerabilit ......
Secure Code Warrior C# Basic OWASP Web Top 10 2017 1: Injection Flaws and 2: Broken Authentication vulnerabilities
Let's start with the most critical application weaknesses. These challenges get you the foundations of 1: Injection Flaws and 2: Broken Authentication ......
Django-SQL Injection Vulnerability (CVE-2019-14234)
> 复现环境:Vulhub 环境启动后,访问`http://192.168.80.141:8000`即可看到Django默认首页 #### 漏洞复现 首先登陆后台`http://192.168.80.141:8000/admin/`,用户名密码为`admin`、`a123123123`。 登陆后台后 ......
Proj CDeepFuzz Paper Reading: IvySyn: Automated Vulnerability Discovery in Deep Learning Frameworks
## Abstract 本文:IvySyn Task: discover memory error vulnerabilities in DL frameworks BugType: memory safety errors, fatal runtime errors Method: 1. 利用na ......
org.apache.hadoop.hive.metastore.HiveMetaException: Schema initialization FAILED! Metastore state would be inconsistent !!问题的解决
# 问题描述 hive进行初始化时,出现这样的问题; # 问题解决 只要进入到我们的虚拟机安装配置的mysql里面,将我们hive-site.xml里面提及到的数据库删除,然后再进行初始化即可; 这次出错是因为,我之前已经初始化过,才出现了这个问题; ......
Proj CDeepFuzz Paper Reading: Differential Testing of Cross Deep Learning Framework APIs: Revealing Inconsistencies and Vulnerabilities
## Abstract 背景:目前对cross-framework conversion中的inconsistencies和security bugs的研究少有 本文:TensorScope Task: test cross-frame APIs in Machine Learning Librar ......
微分平坦(differential flatness)的简易理解
对于运动控制下的系统建模,如果规划控制的变量太多,产生的维度就太多,如无人机变量为12个,即12维空间,同时规划12个变量不现实,所以考虑使用少数几个变量及其有限阶导数代表其他变量,这样一来只需要对少数几个变量进行规划则可以达到对所有变量规划。 参考:https://zhuanlan.zhihu.c ......
Proj CDeepFuzz Paper Reading: Automatic differentiation in PyTorch
## Abstract 本文:描述automatic differentiation module of PyTorch 包括:Lua Torch, Chainer, HIPS Autograd Task: Provides a high-performance environment on dif ......
什么是 NVD(National Vulnerability Database)
当谈到网络安全和漏洞管理时,"NVD",或者全称"National Vulnerability Database",是一个不可或缺的概念。NVD是一个由美国国家标准与技术研究院(NIST)维护的综合性漏洞数据库,旨在收集、共享和分发关于计算机软件和硬件中存在的安全漏洞的信息。NVD的存在对于保护信息 ......
org.apache.hadoop.hive.metastore.HiveMetaException: Schema initialization FAILED! Metastore state would be inconsistent !!问题的解决
# 问题描述 上次还是初始化很快,这次直接出错,我觉得可能是已经初始化一次的原因; 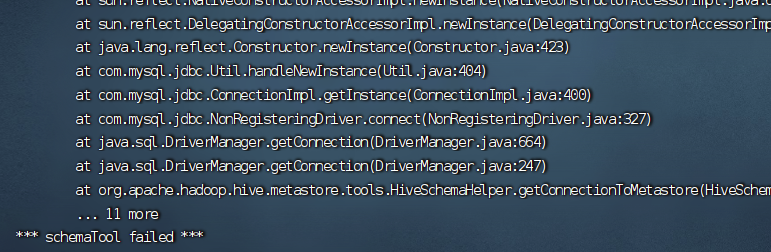 # 问题解决 进入到mysql ......
论文解读(WIND)《WIND: Weighting Instances Differentially for Model-Agnostic Domain Adaptation》
Note:[ wechat:Y466551 | 可加勿骚扰,付费咨询 ] 论文信息 论文标题:WIND: Weighting Instances Differentially for Model-Agnostic Domain Adaptation论文作者:论文来源:2021 ACL论文地址:dow ......
ceph分布式存储软件pgs inconsistent
Ceph是一个开源的分布式存储系统,它提供了高性能、高可靠性以及高扩展性。Ceph的设计理念是基于对象存储模型,通过将数据分割成多个对象并存储在不同的节点上,实现数据的分布式存储和访问 ......
npm - 报错:found XXX vulnerabilities (XXX low, X moderate),run `npm audit fix` to fix them, or `npm au
完整报错 我正准备 npm 装包,结果失败了,并提示如下报错信息: found 808 vulnerabilities (804 low, 4 moderate) run `npm audit fix` to fix them, or `npm audit` for details 解决 直接按照后 ......
apache apache_parsing_vulnerability
Apache两个解析漏洞复现及防御方法 - FreeBuf网络安全行业门户 1、介绍 名称:apache apache_parsing_vulnerability 编号: 原理: 应用:apache 版本: 2、测试 2.1 靶场搭建 2.2 测试过程 (1)上传b.php.jpg <?php ev ......
TabError: inconsistent use of tabs and spaces in indentation
001、python程序报错如下: 002、报错原因(看着缩进是一样的,实际上是不一样的) 003、解决方法 将缩进统一调整为tab键, 对齐即可。 参考:https://blog.51cto.com/yunyaniu/4724938 。 ......
Fourier Analysis and Nonlinear Partial Differential Equations 阅读笔记 (第一章)
# 实分析基础 ## Holder与卷积不等式 首先从经典的Holder不等式入手. **命题: 经典情况下的Holder不等式** >设$(X,\mu)$是测度空间, $(p,q,r)\in[1,\infty]^3$满足 >$$\frac{1}{p}+\frac{1}{q}=\frac{1}{r} ......